4.6 Mapping Security Attributes to Organizations and Users
Security attributes can be mapped to User groups using a Security mapper. This is done using the Mapper Maintenance window. Attributes mapped to User groups in the mapper, are mapped against each user in that user group, after running the Security batch.
- User groups
- Organization
- Jurisdiction
- Business Domain
- Case Type
Prerequisites for Mapper Maintenance
The following are the prerequisites for Mapper Maintenance:- Loading Security Attributes Data
- Configuring Function
- Resaving Metadata
- Loading User Configuration Data
To load security attribute data, Load the security attribute data into the following table:
Table 4-13 Security Attribute Table
| Security Attribute | Table Name |
|---|---|
| Organization | KDD_ORG |
| Jurisdiction | KDD_JRSDCN |
| Business Domain | KDD_BUS_DMN |
| Organization Locale specification | KDD_JRSDCN_TL |
| Jurisdiction Locale specification | KDD_BUS_DMN_TL |
| Business Domain Locale specification | KDD_ORG_TL |
For more information, see the Loading Data.
Configuring FunctionYou can configure the Usergroups to display them in the Mapper window.
To configure the function, Provide the Function code in the KDD_INSTALL_PARAM table for param_name=’ECMSecurity Function’. By default, the CMACCESS function is provided.
Note:
The owner role should be updated in ATTR_1_VALUE_TX column. Update the owner name as mentioned in DEFAULT_CASE_OWN- ER_1 to ATTR_1_VALUE_TX column of the KDD_INSTALL_PARAM table.
Update the column ATTR_3_VALUE_TX for PARAM_ID=7 with the RRS URL in the KDD_INSTALL_PARAM table where you want to post the case.
Data modifications to the Master, Reference, Base tables reflect in the Hierarchy/Derived Entity values.
To enable this, Metadata re-save is required after data load into those Master/Reference/Setup table on which the hierarchy/ Derived Entity is defined.
You can re-save Hierarchy/Derived Entity using the Save Metadata screen.
Hierarchy Re-save- Log in as an ECM Admin user.
- Navigate to Financial Services Enterprise Case Management and select CommonTasks.
- Select Utilities and click Save Metadata.
- Select the Hierarchy and select the below-mentioned Hierarchy. To
select them, use >>button and click Save
- ECM_UserGroup
- ECM_Organization
- ECM_Jurisdiction
- ECM_BusinessDomain
- ECM_Case Type
- Log in as an ECM Admin user.
- Navigate to Financial Services Enterprise Case Management and select CommonTasks.
- Select Utilities and click Save Metadata
- Select Derived Entity and select the below mentioned Derived
Entities. To select them, use >> button and click Save.
- DE_GRPMAST
- DE_GROUP
- DE_ROLE
- DE_ROLE_FUNCTION_MAP
- Derived Entity on Usergroup Dataset
Load the User configuration data into the CSSMS_ATTRIB_MAST table using Excel Upload if not done during before User creation. For more information, see the Oracle Financial Services Analytical Applications Infrastructure User Guide.
Create or Edit the user for which you must map the Security Attributes. For more information, see the Managing Identity and Authorization section.
Using Mapper Maintenance
- Login as an ECM Admin user.
- Navigate to Financial Services Enterprise Case Management and go to Common Tasks.
- Select Unified Metadata Manager and click Business Metadata Management, and click Map Maintenance.
- Select ECM User Group Security Mapper from the Mapper List.
Click Map Maintenance.
Figure 4-3 Map Maintenance
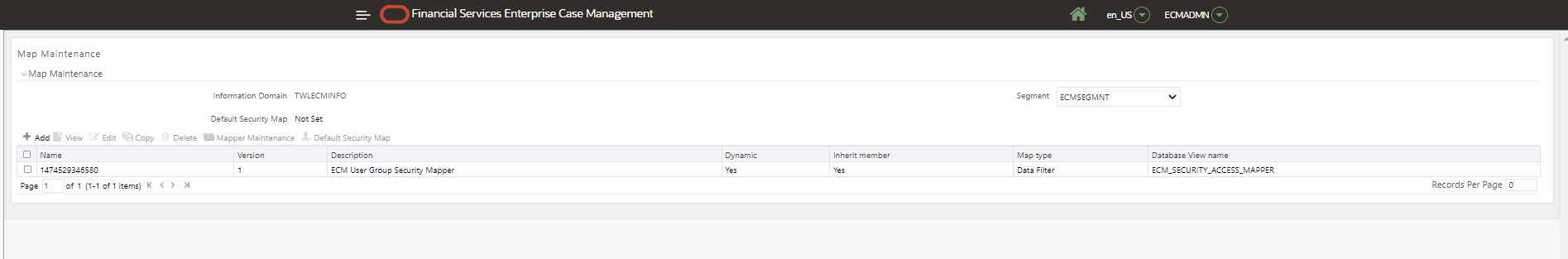
- User Group Security mapper window is displayed. Click
Add.
Figure 4-4 User Group Security Mapper window
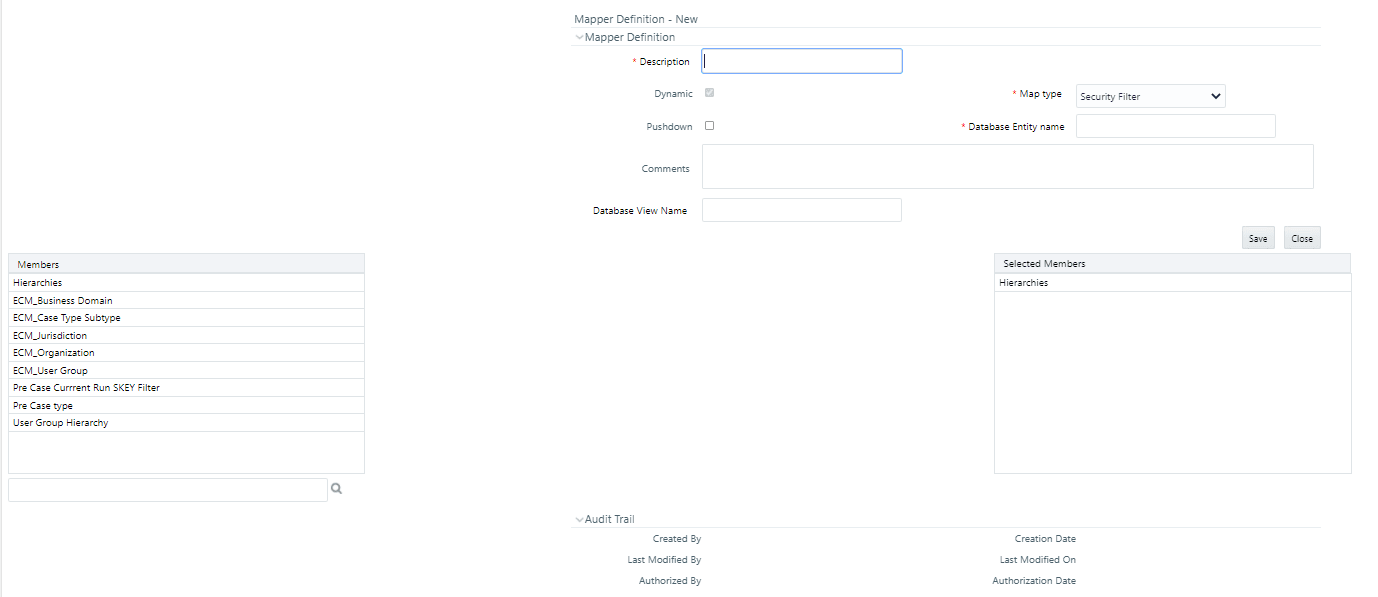
- The Add Mapping Screen is displayed with all the Hierarchies.
- User groups of the users for the Security Attributes are mapped. Lists all User groups which are mapped to the Function code mentioned in KDD_INSTALL_PARAM. For more information, see Configuring ECM Security Function.
- Organization: A User or Organization's access to other Organizations depends on the selection(s) made for this organization parameter. For example, if a user is mapped to Org1 and Org2, then the user can access these two organizations, but other security attributes are also should match.
- Jurisdiction: Mapping of one or more jurisdictions to a user group, gives the privilege of accessing cases that belong to the mapped jurisdiction.
- Business Domain: Mapping of one or more business domains to a user group gives the privilege of accessing cases that belong to the mapped business domains.
- Case Type: Mapping of one or more Case Types to a user group gives them the privilege of accessing cases that belong to the mapped Case Type.
- Select the required values from each hierarchy and click Go. Click Save.
- Click Save. You are directed to the previous screen,
where the Member combinations can be viewed. All the changes get saved in
the ECM_SECURITY_ACCESS_MAPPER table and respective view
ECM_SECURITY_ACCESS_MAPPER_VW.
Note:
Member Combinations will show you the mappings you made in the Add Mapping Screen. Mapped Members section will show you all the actual members participating in the selection (same as the content stored in ecm_security_access_mapper/ecm_security_access_mapper_vw).
All the exploded mappings can be seen in this section. You can navigate to all the pages of the same section to see the mappings.
If you want to remove the mapping from the mapper. Select a mapping from the first panel and click Remove. You should click Pushdown to effect these changes in the system.
For more information on Mapper, see the Oracle Financial Services Analytical Applications Infrastructure User Guide.
Note:
If you are creating a new user, then perform the security mapping for that user and again execute the ECM_SECURITY_BATCH.- Batch Maintenance
- Batch Execution
- Batch Monitor/Checking the Execution Status
All updates made to all the user profiles through User Maintenance UI, and Mapping done using Map Maintenance are imported from the CSSMS_USER_PROFILE table of OFSSAAI configuration schema to KDD_REVIEW_OWNER table with the help of ICC Batch.
By default, the ICC Batch used for ECM Security Batch is automatically assigned to SYSADMN user during Installation.
begin
AAI_OBJECT_ADMIN.TRANSFER_BATCH_OWNERSHIP ('fromUser','toUser','infodom'); end;OR
begin
AAI_OBJECT_ADMIN.TRANSFER_BATCH_OWNERSHIP ('fromuser','touser');
end;Here,
- from User indicates the user who currently owns the batch
- to User indicated the user to which the ownership has to be transferred
- Infodom is an optional parameter if specified the ownership of batches pertaining to that Infodom will be changed.
begin
AAI_OBJECT_ADMIN.TRANSFER_BATCH_OWNERSHIP('SYS- ADMN','ECMADMN','ECMINFO');
end;The seeded Batches are viewed from the Batch Maintenance operation.
- Navigate to Common Tasks and select Operations and click Batch
Maintenance.
Note:
If it is not visible to the Admin User, then you have to execute the steps mentioned in Changing ICC Batch Ownership to ECM Admin from SYSADMN user. - Select the <Infodom>_ECM_SECURITY_BATCHand select the Task1. Click Edit from the Task Details section.
- Modify the Parameter List. Seeded values are p_create_id.
- For the Parameter List-Syntax is‘p_create_id’,’p_user_id’.
- op_create_id: Current Admin User who is going to execute theBatch.
- op_user_id: User(s) for which the Security Attribute
Mapping changed through theSecurity
Mapper.
This can be changed in the following two ways:
- Use Case 1: If ‘Parameter List’, values are given as 'ECMADMN','' then Batch populates kdd_review_ownerand its mapping tables for all the Users which are mapped through the Security Mapper where ECMADMN is the current logged in Admin User.
- Use Case 1: If ‘Parameter List’, values are given as 'ECMADMN','USER1,USER2', then Batch populateskdd_review_ownerandits mapping tables for only the Users USER1 and USER2 which are mapped through the Security Mapper where ECMADMN is the current logged in Admin User.
- Define the ‘Parameter List’ values, clickSave.
- Navigate to Common Task and select Operations and then click
Batch Execution. The Batch Execution window is displayed.
Figure 4-5 Batch Execution
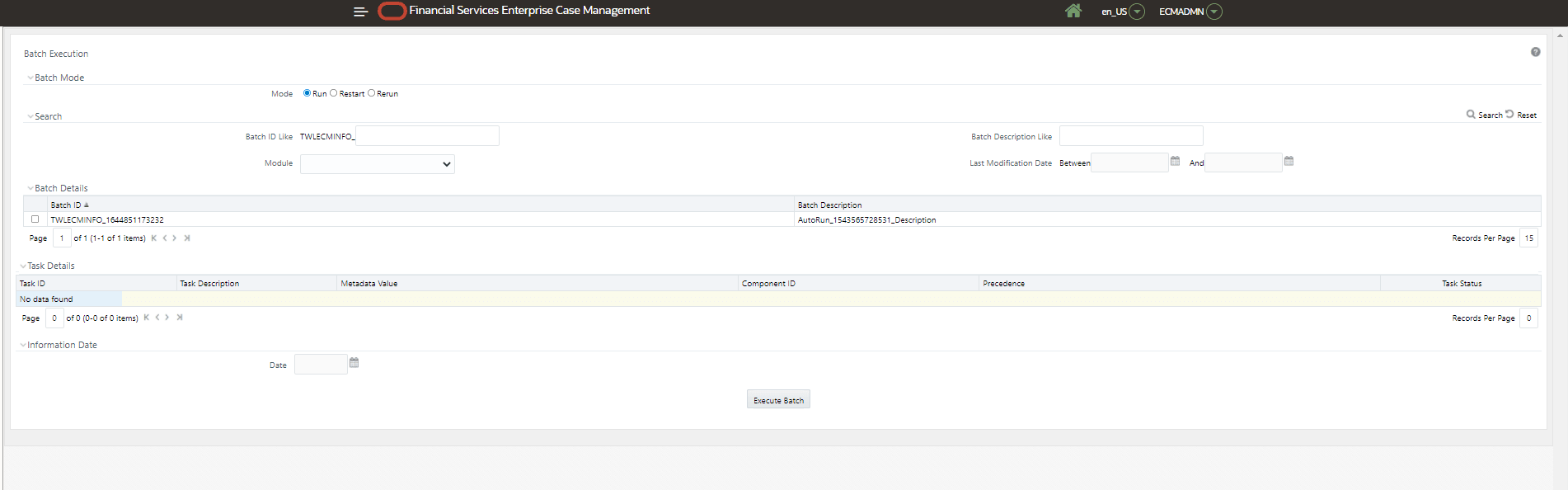
- Before executing a Batch, check if the following services are
running on the application server:
- ICCserver
- Router
- AMServer
- MessageServer
For more information, see the Oracle Financial Services Analytical Applications Infrastructure Guide.
- Thes eeded batch (<Infodom>_ECM_SECURITY_BATCH) must be executed for the required MIS Date on this screen.
- Select <Infodom>_ECM_SECURITY_BATCH and provide the Current Date in the Information Date section.
- Click Execute Batch.
- Navigate to Common Task and select Operations and then click
Batch Monitor. The Batch Monitor window is displayed.
For more information on the configuration and execution of a batch, see the Oracle Financial Services Analytical Applications Infrastructure Guide.
Following are the status messages in Batch Monitor:
- N: Not Started
- O: On Going
- F:Failure
- S:Success
- The execution log is accessed on the application server from the following directory: $FIC_D- B_HOME/log/date.
The file name has the batch execution ID. After the Batch is successful, the mappings for the User(s) is reflected in KDD_REVIEW_OWNER and its mapping tables. The Audit is recorded in the respective Audit Tables.
Mapping Read-Only Case typeIf you need Read-Only access to certain Case types, then add an entry in KDD_REVIEW_OWNER_CSE- TYP_RDONLY table against the Case type.