Network Security in OHI Environment
When deploying OHI Components applications onto a network there are many security issues to take into consideration, especially the use of firewall and VPN technologies. A firewall will permit or deny network permissions based on configured rules, to protect the internal network from malicious actions while permitting legitimate communications.
Firewalls perform the following functions in a typical OHI environment:
-
Guard the company Intranet from unauthorized outside access.
-
Separate Intranet users accessing the OHI system from internal subnetworks where critical corporate information and services reside.
-
Protect from IP spoofing and routing threats.
-
Prohibit unauthorized users from accessing protected networks and control access to restricted services.
-
Throttle requests / apply rate limiting.
-
Act as Web Application Firewall protecting against malicious requests.
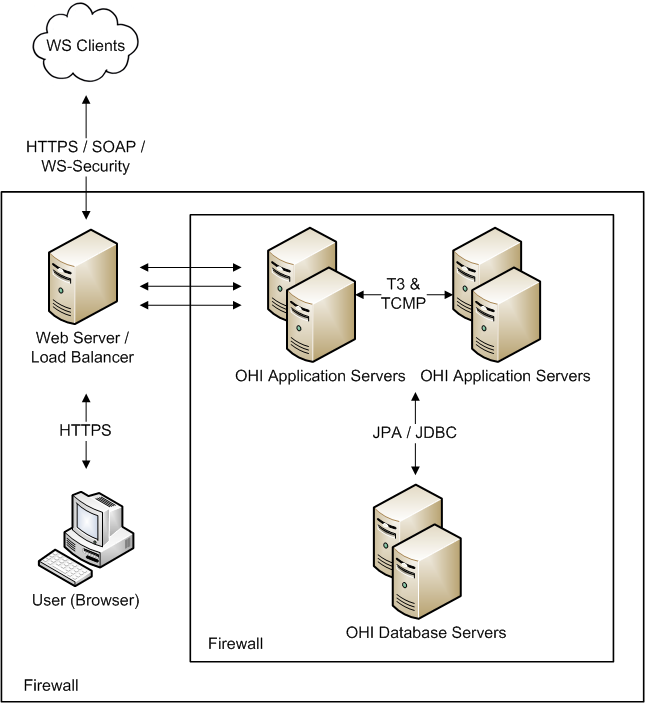
A typical OHI Components environment usually has the following security zones:
-
Internet - External web service clients may come from outside of the company network.
-
Intranet - A company network separated by the external firewall that gives remote workers access to the OHI user interface. This is also where OHI web servers and / or load balancers may be placed. Alternatively, for additional protection, web and load balancing servers may be placed in a separate demilitarized zone (DMZ) where external and internal clients first interact with the OHI environment.
-
OHI application server and database zone - OHI application servers, database servers and possibly authentication servers (for example, if a customer chooses to delegate authentication using LDAP servers) typically reside in this zone.
Ensure that the firewalls used to secure an OHI environment support the HTTP 1.1 protocol; it enables browser cookies and inline data compression for improved performance.