Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Export Oracle Database Audit Logs from Oracle Data Safe to OCI Logging
Introduction
Oracle Data Safe is a fully-integrated cloud service focused on the security of your data. It provides a complete and integrated set of features for protecting sensitive and regulated data in Oracle Database. Features include Security Assessment, User Assessment, Data Discovery, Data Masking, and Activity Auditing.
The Oracle Cloud Infrastructure (OCI) Logging service provides a highly scalable and fully managed single interface for all the logs in your tenancy. Use logging to access logs from all your OCI resources and enable, manage, and search them.
OCI Functions is a fully managed, multi-tenant, highly scalable, on-demand, Functions-as-a-Service platform. It is built on enterprise grade OCI and powered by the Fn project open source engine.
Objective
-
Export Oracle Database unified audit logs from Oracle Data Safe to OCI Logging using a scalable and automated architecture.
The architecture to be deployed is shown below.
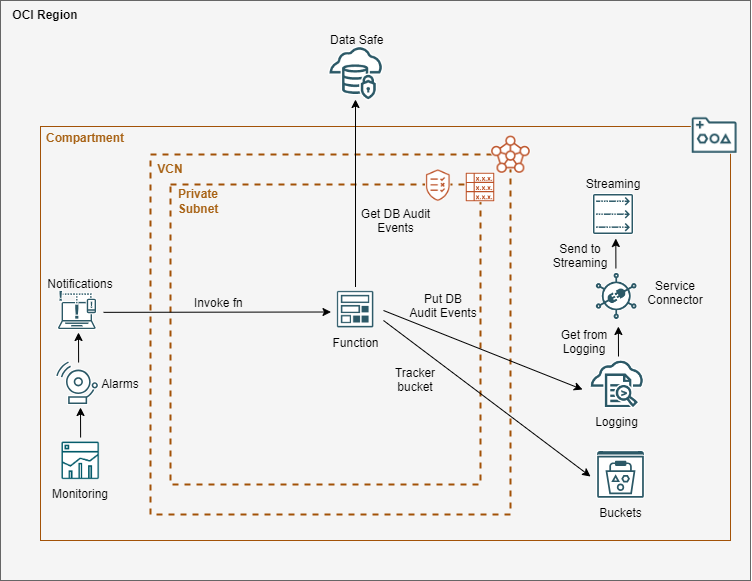
Prerequisites
The following requirements are necessary prior to deploying the environment.
-
Configure Oracle Data Safe to obtain database audit events from Oracle Database.
-
Configure the OCI Registry user (OCI username) and OCI Registry user password (OCI user authentication token).
-
Create and verify Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) policies to allow the OCI Registry user to push the image of the Python function that will be used.
-
Permission to manage the following types of resources in your OCI tenancy: IAM policies, Dynamic Groups, VCNs, Service Gateways, Route Tables, Security Lists, Subnets, Functions, Monitoring Alarms, and Notifications.
Note: In order to simplify the deployment, we suggest that the deployment be done via OCI Resource Manager using the Terraform scripts available here.
Prerequisite 1: Register and Configure the database in Oracle Data Safe
Before creating the reference architecture, it is necessary to configure Oracle Data Safe to receive audit events from the Oracle Databases to be monitored.
In this tutorial, we will configure Oracle Data Safe in an Oracle Autonomous Database, in a previously created OCI tenant. However, it is possible to configure the audit of Oracle Databases in several different environments (on-premises, in instances, and so on). For more information on possible scenarios for configuring Oracle Data Safe, see Data Safe.
You can configure Oracle Autonomous Database audit directly on the database services page or via the OCI Console. We will do it via OCI Console.
-
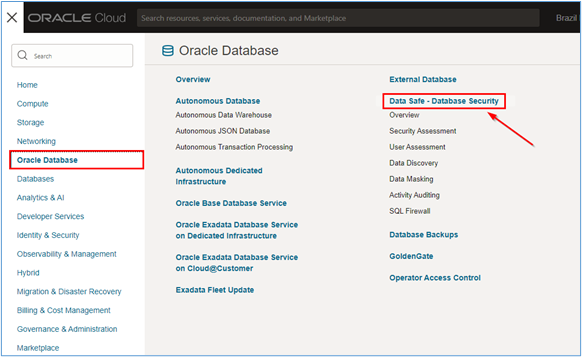
Go to the OCI Console, click Oracle Database and then click Data Safe – Database Security.
-
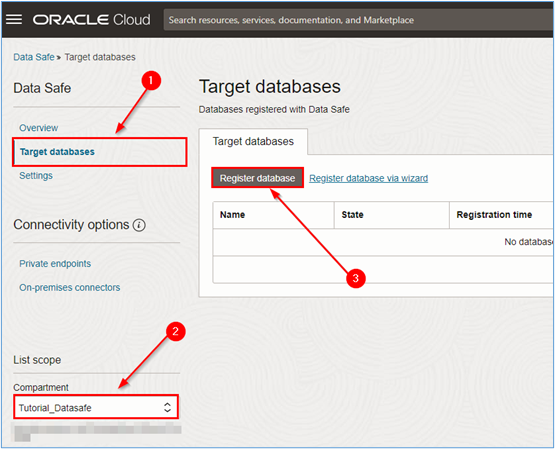
To register the database, click Target databases and select the compartment where the database is to be registered and then click Register database.
-
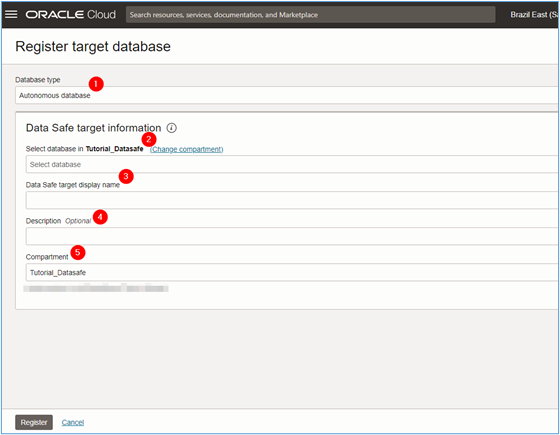
In Data Safe configuration page, enter the following details and click Register, then wait for the configuration to complete.
-
Database type: Select the type of database that will be configured. In this tutorial, the type is Autonomous Database. For more information about supported Oracle Database types, see Supported Target Databases.
-
Select database in < Compartment >: Select the database that will be monitored by Oracle Data Safe.
-
Description: Optionally, it is possible to enter a description for registering the database in Oracle Data Safe.
-
Compartment: Select the compartment where the Oracle Data Safe registration will be made.
For more information about configuring Oracle Data Safe, follow the step-by-step instructions available in Get Started with Oracle Data Safe Fundamentals on the Oracle Live Labs portal.
-
Prerequisite 2: Configure the OCI Registry user
For the environment to be created as needed, an OCI IAM user must be authorized to push images within the OCI Registry. This user will provide the image of the function to be used to automate the collection of Data Safe logs and therefore, needs the correct permissions to the OCI Registry. According to the requirements for building the environment, configure the OCI IAM user’s access credentials to the OCI Registry.
-
Log in to the OCI Console with the user who will access the OCI Registry and click My profile.

-
In the user details window, click Auth Tokens and then click Generate token.

-
Enter the description for the created token and click the Generate token.
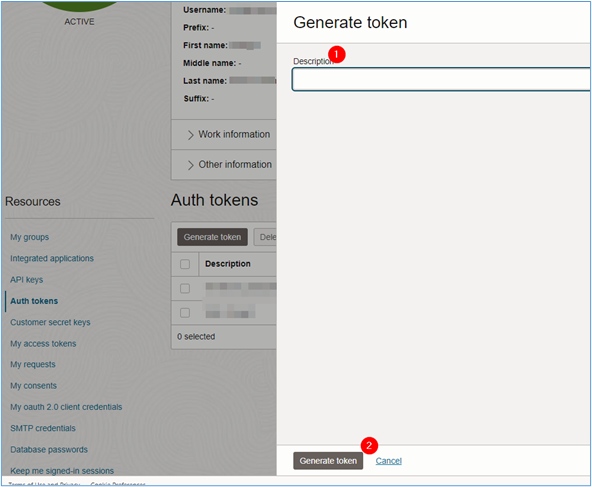
Your auth token will be generated. Note the auth token as it will be used as a parameter for configuring the stack within OCI Resource Manager.
Note: The user who will be used to create and consume the OCI Registry does not necessarily need to be the same user who will deploy the infrastructure via OCI Resource Manager. During deployment, the username and auth token information of the user who will access the registry is requested.
Prerequisite 3: Create OCI IAM Policies to access the OCI Registry
For the OCI IAM user to have access to OCI Registry service, it is necessary to allow the user to manage repositories in the compartment where the environment will be created, or using the least-privilege policy, it is necessary to allow the user to update the compartment’s repositories. Therefore, apply one of the two options below to configure access to the OCI Registry.
-
Manage policy for repositories
Allow group <group_name> to manage repos in compartment <compartment_name> -
Update policy for repositories
Allow group <group_name> to manage repos in compartment <compartment_name> where ANY {request.permission = 'REPOSITORY_READ', request.permission = 'REPOSITORY_UPDATE', request.permission = 'REPOSITORY_CREATE'}-
REPOSITORY_READ: User permission to read the repository, that is, pull images.
-
REPOSITORY_UPDATE: User permission to send images to the repository, that is, push images.
-
Prerequisite 4: OCI IAM policies for architecture deployment
According to the available documentation, the user who will deploy this infrastructure must have manage permission for the following OCI services: IAM policies, Dynamic Groups, VCNs, Service Gateways, Route Tables, Security Lists, Subnets, Functions, Monitoring Alarms, and Notifications.
Approach 1: Deploy via Terraform using OCI Resource Manager
To implement the reference architecture for the scalable collection of database audit logs via Oracle Data Safe, run the Terraform available at the fn-datasafe-dbaudit-to-oci-logging GitHub repository using an OCI IAM user with access to the OCI Console and whose group has the required permissions as previously informed. According to the documentation available in the repository, it is possible to install the solution via OCI Resource Manager or Terraform CLI.
Note: To simplify the deployment of the environment, we suggest that the deployment be done via OCI Resource Manager.
-
To automatically install and configure the reference architecture for log collection, log in to tenant OCI Console with the user that will be used for deployment and select the region where you will install the environment.
In another tab, access the repository page on GitHub available here: fn-datasafe-dbaudit-to-oci-logging.
-
Once the tenant OCI Console and the GitHub repository page open, scroll down the repository page to the Deploy Using OCI Resource Manager section, and to begin the installation, click Deploy to Oracle Cloud.

-
An OCI Resource Manager page will open within the OCI Console. Enter the following information and then click Next.
- Oracle Terms of Use: Read and select the box I have reviewed and accept the Oracle Terms of Use.
- Name: Optional, give a name that identifies the environment installation.
- Create in compartment: Select the compartment where the environment will be created.

-
In the next window, enter the following information and then click Next.
- OCIR Username: Enter the username of the user used to deploy the infrastructure (user must have permission to create and upload an image to the repository).
- OCIR user password: Enter the auth token created previously in prerequisites.
- Deployment mode: Enter the way in which the environment will be created. In this case we will use
test. - VCN CIDR: Enter the CIDR of the VCN to be created for deploying the environment. This item is optional and can be changed as necessary.

-
On the next page, click Create to create the architecture and wait for the OCI Resource Manager to create the environment.

Approach 2: Deploy via Terraform using the OCI Console
A specific and orderly step-by-step procedure must be followed to perform manual deployment via the OCI Console. To start, select a compartment where the environment will be created. In this compartment, create a new VCN (or use an existing VCN).
Task 1: Create VCN and Subnets
-
To create the environment’s VCN, go to the OCI Console and navigate to Networking and Virtual Cloud Networks.

-
Select the compartment where the VCN will be created and then click the Start VCN Wizard.

-
In the wizard page, select Create VCN with Internet Connectivity and click Start VCN Wizard.

-
In Create a VCN with internet connectivity page, enter the following information to create the VCN.
- VCN Name: Fill in the name of the VCN to be created.
- Compartment: Select the compartment where the VCN will be created.
- VCN IPv4 CIDR block: Enter the desired CIDR for the VCN or use the CIDR already filled in by the tool.
- Public Subnet IPv4 CIDR block: Enter the desired CIDR for the public subnet or use the CIDR already filled in automatically.
- Private Subnet IPv4 CIDR block: Enter the desired CIDR for the private subnet or use the CIDR already filled in automatically.


-
Click Next and wait for the VCN to be created.

Task 2: Create OCI Registry Repository
This service will host the image of the Python function that will collect Data Safe audit logs.
-
Go to the OCI Console and navigate to Developer Services and Container Registry.

-
In the Container Registry services page, select the compartment where the container registry will be created and click Create repository.

-
Enter the necessary information to create the repository and click Create.
- Create in compartment: Select the compartment where the repository will be created.
- Access: Select
private, so that this is a private repository (not accessible via the Internet). - Repository name: Enter the name to be assigned to the repository.

After creation is complete, the repository will be available to view its details.

Note: Note the Namespace created for the repository. This Namespace will be used in a later task.
Task 3: Create an OCI Bucket to Control Signaling
As shown in the topology of the proposed environment, it is necessary to create an OCI Bucket to receive a text file that is used to control the execution of the function code. The name of this bucket will be used in the configuration of the OCI Functions and also in the policies to be configured for the environment.
-
To create the bucket, go to the OCI Console and click Storage, Bucket.

-
Select the compartment and click Create Bucket.

-
Enter the Bucket Name and click Create.

Note: Note the name of the bucket, it will be used when building policies and configuring the OCI Functions.
Task 4: Create a Custom Log
The destination of the logs collected from Oracle Data Safe must be an OCI Logging group that will contain a custom log created specifically to receive the audit records captured from the monitored databases.
-
Go to the OCI Console, navigate to Observability & Management and click Log Groups.

-
A log group will be created to house the custom log used by the OCI Functions. Select the compartment where the log group will be created and click Create Log Group.

-
Enter the following information and click Create to create the log group.
- Name: Enter a name for the log group.
- Description: Enter a description for the log group.

-
Click Logs and then click Create Custom Log.

-
Enter the following information to create the custom log that will receive the audit logs from the databases monitored by Oracle Data Safe and click Create custom log.
- Custom log name: Enter a name for the custom log.
- Compartment: Select the compartment where the custom log will be created.
- Log group: Select the log group just created in the above step.

Note: We will not create the agent config.
-
The custom log creation page is a workflow that will also allow to create agent config. In this case, we will not create the agent config. So, click Cancel

The log group page will be loaded again and contains the custom log created.
Note: Note the Oracle Cloud Identifier (OCID) of the custom log created as it will be used when configuring the OCI Functions.

Task 5: Create the OCI Functions
After creation of the repository where the OCI Functions image should be stored, the OCI Functions must then be created to collect the Data Safe audit logs.
-
Go to the OCI Console, navigate to Developer Services and Applications.

-
Select the compartment where the application will be created and click Create application.

-
Enter the following information to create the application and click Create.
- Name: Enter a name for application.
- VCN in < Compartment >: Select the VCN where the application will be created.
- Subnets in < Compartment >: Select the subnet where the application will be created.
- Shape: Select the architecture on which the application will be created. In this example we will use
GENERIC_X86.

Task 6: Configure the OCI Functions
Once the application has been created, the page will load automatically. On this page, there is a recommended step-by-step guide via OCI Cloud Shell or local setup to be followed so that OCI Functions can be created. In this tutorial, the suggested step-by-step instructions via OCI Cloud Shell will be used.
-
Select the Cloud Shell setup.

Note: The example given in Cloud Shell setup refers to simple Java code. As we will use Python code in this lab, below is a reference for OCI Functions startup in Python.
-
Click Cloud Shell and enter the details according to the desired configuration for your OCI Functions.

fn list context fn use context <REGION> fn update context oracle.compartment-id <OCID_Compartment> fn update context registry <REPO_URL>/<namespace>/[repo-name-prefix]- < REGION >: Enter the region where the OCI Functions will be created. In this case, we use
sa-saopaulo-1. The list of OCI regions can be found here: Regions and Availability Domains. - < OCID Compartment >: Enter the OCID of the compartment where the function will be created.
- < REPO_URL >/< Namespace >/[ repo-name-prefix]: The repository URL is made up of the key of the region where the repository was created and the name of this created repository. Therefore, for this tutorial, the full URL will be:
- REPO_URL: String formed by
< region-key >.ocir.io. we use thesa-saopaulo-1region, and therefore the URL will be:gru.ocir.io(the region-key for your region can be found here: Regions and Availability Domains). - Namespace:
axyxxqi24xxx(Noted at Task 2.4). - repo-name-prefix: Name of the created repository.
- REPO_URL: String formed by
- < REGION >: Enter the region where the OCI Functions will be created. In this case, we use
Task 7: Create the Auth Token for Log in to OCI Registry
It is necessary to create an auth token so that the user used to carry out this procedure can log in to the created OCI Registry. For more information, see Getting an Auth Token.
Task 8: Create and Deploy the OCI Functions
-
Once the auth token is created, you will need to log in to the repository via Docker command. For more information about log in, see Logging in to Oracle Cloud Infrastructure Registry.
docker login -u '<namespace>/<username>' <repo-domain-url> -
Once logged in to the repository, it is possible to initialize the function and edit the Python code for deployment. Run the following commands.
fn list apps fn init --runtime python fndatasafelogs cd fndatasafelogs >> Edit function.py to insert the function code >> Edit requirements.txt to insert requirements as needed for the role >> Edit function.yaml to make it as needed fn -v deploy --app <app_name>Note: There are steps where it will be necessary to edit the files. The contents of the
function.py,requirements.txtandfunction.yamlfiles can be found here.
Task 9: Configure the OCI Functions Operating Parameters
Once the OCI Functions have been created, they must be configured to collect Data Safe logs correctly.
-
Go to the OCI Console and navigate to Developer Services and Applications.

-
Select the compartment where the application for this project was created and click on the application.

-
In the Function, click on the function created to configure it.

-
Click Configuration and enter the following information for the function to work.
- ociOSTrackerBucketName: Enter the name of the control bucket created in Task 3.3.
- ociDataSafeCompartmentOCID: Enter the OCID of the OCI tenant (root tenant) used.
- ociLoggingLogOCID: Enter the OCID of the custom log created in Task 4.6.

Now, finalize the policies to configure the Oracle Data Safe log collection function.
Task 10: Create a Dynamic Group
Create a dynamic group in order to grant the OCI Functions access to the services necessary to collect Data Safe logs.
-
In the OCI Console, go to Identity, Domains,
<Your_Domain>, Dynamic Groups and click Create dynamic group.
Note: In this example, we use the Identity Domain Default. Check the identity domain used in your environment and access it correctly.
-
Enter the following information and click Create dynamic group.
-
Name: Enter the name of the dynamic group.
-
Description: Enter a description for the dynamic group.
-
Rule 1: Enter the dynamic group matching rule that will identify the created OCI Functions.
The matching rule used will be as follows:
ALL {resource.type = 'fnfunc', resource.compartment.id = '<Compartment_ID>'}- Compartment_ID: Enter the OCID of the compartment where the function was created.

Note: Note the name of the dynamic group created. It will be used during the construction of OCI IAM policies.
-
Task 11: Create the OCI IAM Policies for the operation of the OCI Functions
For the function that will collect Data Safe logs to work correctly, it is necessary to create all necessary access permissions.
-
In the OCI Console, go to Identity & Security and Policies.

The creation of policies must be done both at the compartment level where the environment is being created and at the tenancy level. At the tenancy level, it will be necessary to create a single policy. This policy will allow the created function to read all Oracle Data Safe events wherever they occur.
-
To create policies in the compartment, click Create policy.

-
Enter the following information and click Create.

-
Name: Enter the name of policy.
-
Description: Enter the description of policy.
-
Compartment: Select the compartment where the policy will be created. This first policy can be created in the compartment where the environment was created.
-
Policy Builder: Click on the key to activate the advanced policy filling mode.
-
Policies: Enter the policies in text format.
The policies necessary for the environment to function are as follows:
Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to manage buckets in compartment <Compartment_Name> where target.bucket.name='<Bucket_Name>' Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to manage objects in compartment <Compartment_Name> where target.bucket.name='<Bucket_Name>' Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to use log-content in compartment <Compartment_Name> Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to manage objects in compartment <Compartment_Name> Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to read objectstorage-namespaces in compartment <Compartment_Name> Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to read buckets in compartment <Compartment_Name> -
At the Tenant level, it will only be necessary to create the policy that will allow the function to read Data Safe events.
Allow dynamic-group 'Default'/'<Dynamic_Group_Name>' to read data-safe-audit-events in tenancy- Dynamic_Group_Name: Enter the name of the dynamic group created for the OCI Functions.
- Compartment_Name: Enter the name of the compartment where the environment for this procedure was created.
- Bucket_Name: Enter the name of the created OCI Bucket.
Note: These policies and the entire environment for this procedure were created in the Default identity domain of the environment. For more information about identity domains, see Identity Domain.
Once the policies have been created, it will be possible to execute the function so that its namespace is identified. This namespace will be used to create an alarm in OCI Monitoring.
-
-
To execute the function, open the Cloud Shell and run the following commands.
fn list appsCopy the name of the app created for this lab and run the following command.
fn invoke <app_name> <function_name>
Note: Check the execution status is ok. This shows that the function can run perfectly in the environment.
Now that we have the function operational, create the OCI Notifications topic and OCI Monitoring alarm to finalize the configuration.
Task 12: Create the OCI Notifications Topic
Once the OCI Functions has been deployed, it will be possible to configure the OCI Notifications service to invoke the execution of the Python code that will collect Data Safe logs on a recurring basis.
-
In the OCI Console, go to Developer Services and Notifications.

-
Click Create Topic to create the notification topic.

-
Enter the following information to create the notification topic and click Create.
- Name: Enter a name for the topic to be created.
- Description: Optional Enter a description for the topic.

-
It is possible to subscribe to the function on the topic, that is, when the topic is triggered by the temporal alarm, the topic will execute the Python code to collect the Data Safe logs. To configure the OCI Functions subscription on the topic, click on the name of the newly created topic.

-
Once inside the topic page, click Create Subscription to perform the configuration.

-
On the configuration page, enter the following information and click Create.
- Protocol: Select Function.
- Function compartment: Select the compartment where the OCI Functions was created.
- Oracle Functions application: Select the application created in Task 5.
- Function: Select the function created in Task 6.

The topic will be updated with the successful function subscription.

Task 13: Create an Alarm with OCI Monitoring
Once the topic has been configured and the function has been added, the alarm must be created, which will be responsible for triggering the notification and consequently the function.
-
In the OCI Console, go to Observability & Management and Alarm Definitions.

-
To create an alarm, click Create Alarm.

-
Enter the following information to create an alarm.
-
In the Define Alarm field, enter the following information.
- Alarm name: Enter the name for the alarm.
- Alarm severity: Select “info” for the alarm severity.

-
In the Metric description field, enter the following information.
- Compartment: Select the compartment where the alarm will be created.
- Metric namespace:
oci_faas. - Metric name:
FunctionInvocationCount. - Interval:
1 day. - Statistic:
Count.

-
In the Trigger rule field, enter the following information.
- Operator:
greater then. - Value:
0. - Trigger delay minutes:
1.

- Operator:
-
In the Define Alarm Notifications field, enter the following information.
- Destination service:
Notifications. - Compartment: Select the compartment where the OCI Notifications topic was created.
- Topic: Select the name of the created topic.
- Repeat notification?: Select this box so that OCI Notifications can be triggered multiple times.
- Notifications frequency:
1. - Notifications frequency:
minutes.

- Destination service:
-
Select Enable this alarm? and click Save alarm.

-
Once this is done, the environment will be ready to collect Data Safe logs. Wait a few moments until the Data Safe logs start to appear in the custom log created.

Related Links
Acknowledgments
- Author - Rodrigo Pace de Barros
- Contributor - Fabrizio Zarri
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Export Oracle Database Audit Logs from Oracle Data Safe to OCI Logging
F92056-01
February 2024
Copyright © 2024, Oracle and/or its affiliates.