Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Integrate Zed Attack Proxy with Oracle Cloud Infrastructure DevOps Build Pipeline
Introduction
Oracle Cloud Infrastructure (OCI) DevOps service is a complete Continuous Integration/Continuous Delivery (CI/CD) platform for developers to simplify and automate their software development lifecycle. The OCI DevOps service enables developers and operators to collaboratively develop, build, test, and deploy software. DevSecOps is the practice in which security testing is added in the automation process of Software development and deployment.
Zed Attack Proxy (ZAP), formerly known as Open Web Application Security Project Zed Attack Proxy (OWASP ZAP), is an open source web application security scanner. It helps developers and security professionals detect and find vulnerabilities in web applications. ZAP will provide a report which tells about the vulnerabilities and warnings found during vulnerability scan.
Objectives
- Integrate ZAP with OCI DevOps Build Pipeline.
Prerequisites
- Create and set up a pipeline to build and deploy an application. For more information, see Deploy your application using OCI DevOps CI/CD pipeline on Kubernetes.
Task 1: Set up build stage for ZAP scan
-
Create Build spec file using the below configuration for the ZAP integration stage named
zap_build_spec.yaml. Replace theapplication-urlin build spec command with the deployed application URL. You can also use the Build Parameters to make it more dynamic. Upload the build spec file to the repository.version: 0.1 component: build timeoutInSeconds: 10000 runAs: root shell: bash steps: - type: Command timeoutInSeconds: 1200 name: "Zap Scan" command: | docker run -v /docker-vol/agent-dir/ext/${OCI_PRIMARY_SOURCE_NAME}:/zap/wrk/:rw --user root ghcr.io/zaproxy/zaproxy:stable zap-baseline.py -t <application-url> -g gen.conf -d -r report.xml outputArtifacts: - name: zap-report type: BINARY location: ${OCI_PRIMARY_SOURCE_DIR}/report.xml -
Add Build stage for ZAP integration.
-
Click Add a stage under the build pipeline and choose Manage build stage.
-
Enter
zap_build_spec.yamlin Build Spec file path. -
Enter the stage name and add primary code repository.
-
Select Connection type as OCI code repository and select code repo in which
zap_build_spec.yamlis present.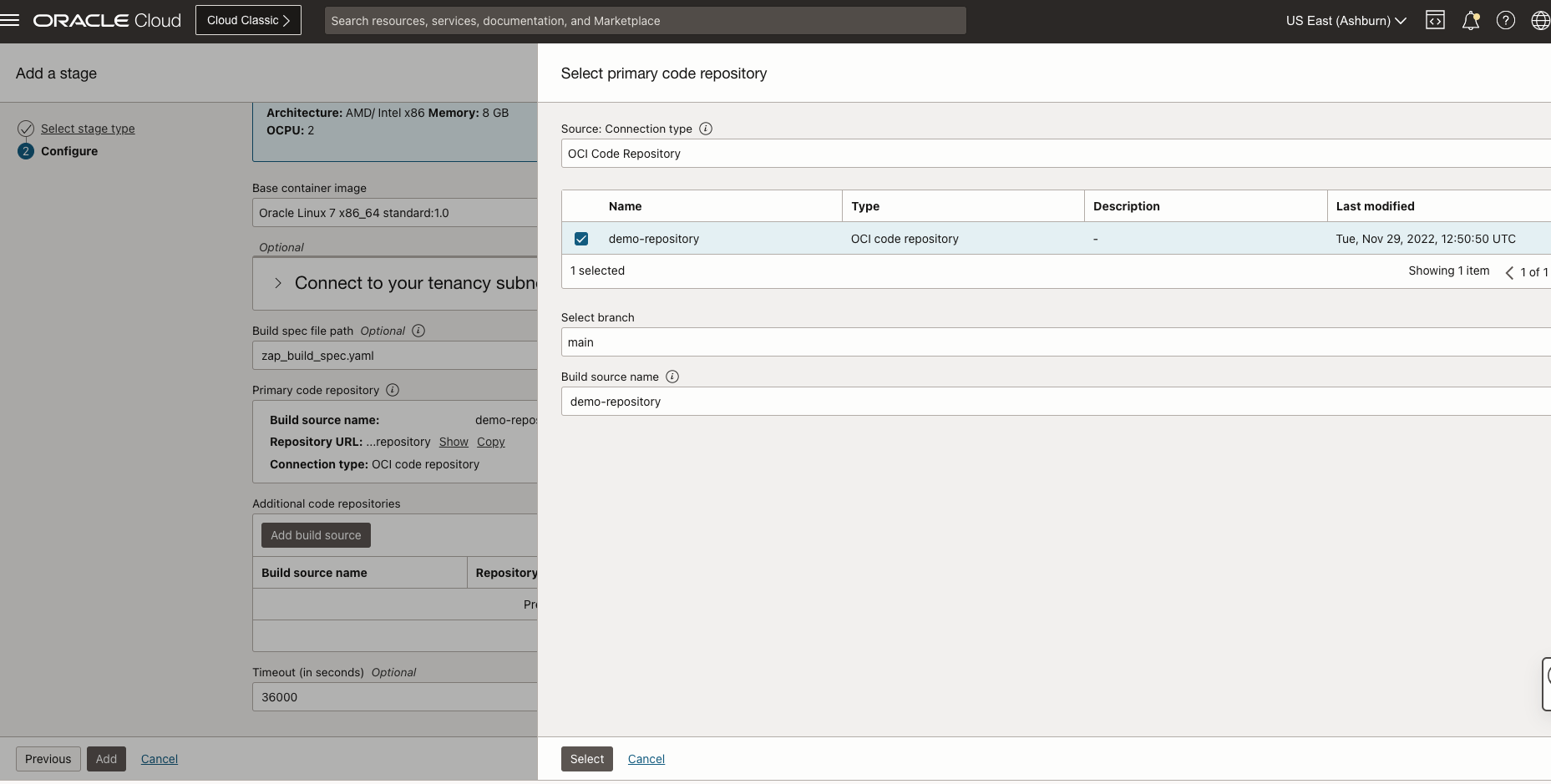
-
-
Add Artifact.
-
Click Add Artifact.
-
Specify type as General artifact.
-
Select the artifact registry repository where ZAP report will be stored.
-
Select Artifact from the repository.
-
Click Add.
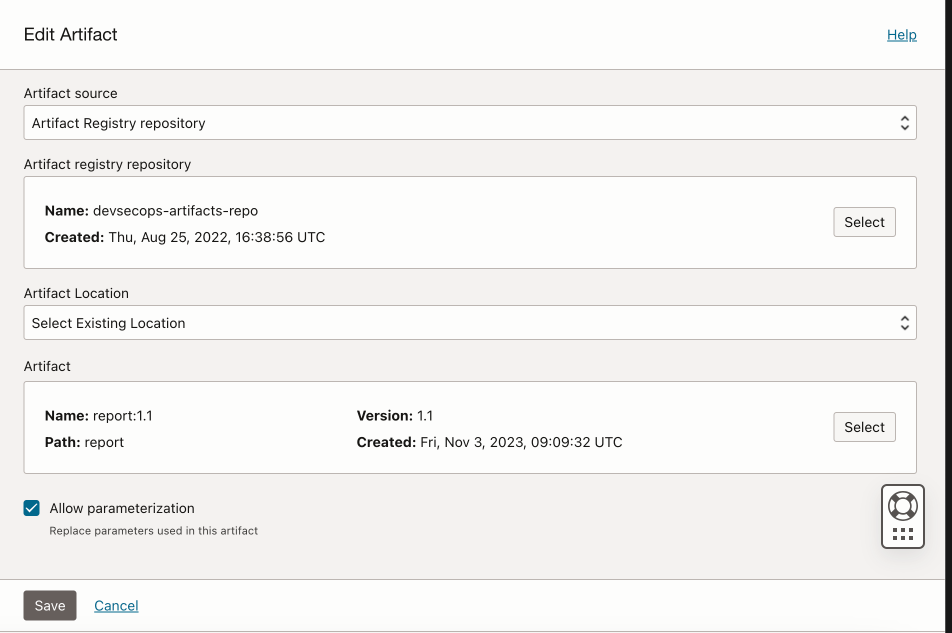
-
-
This stage will push the ZAP report to artifact registry. In the previously created build pipeline, add another stage of type Deliver Artifacts.
-
Click Select artifact(s) and select the artifact created.
-
Give Build config/result artifact name as zap-report, because we mentioned this artifact name in our
zap_build_spec.yamlfile. -
Click Add.
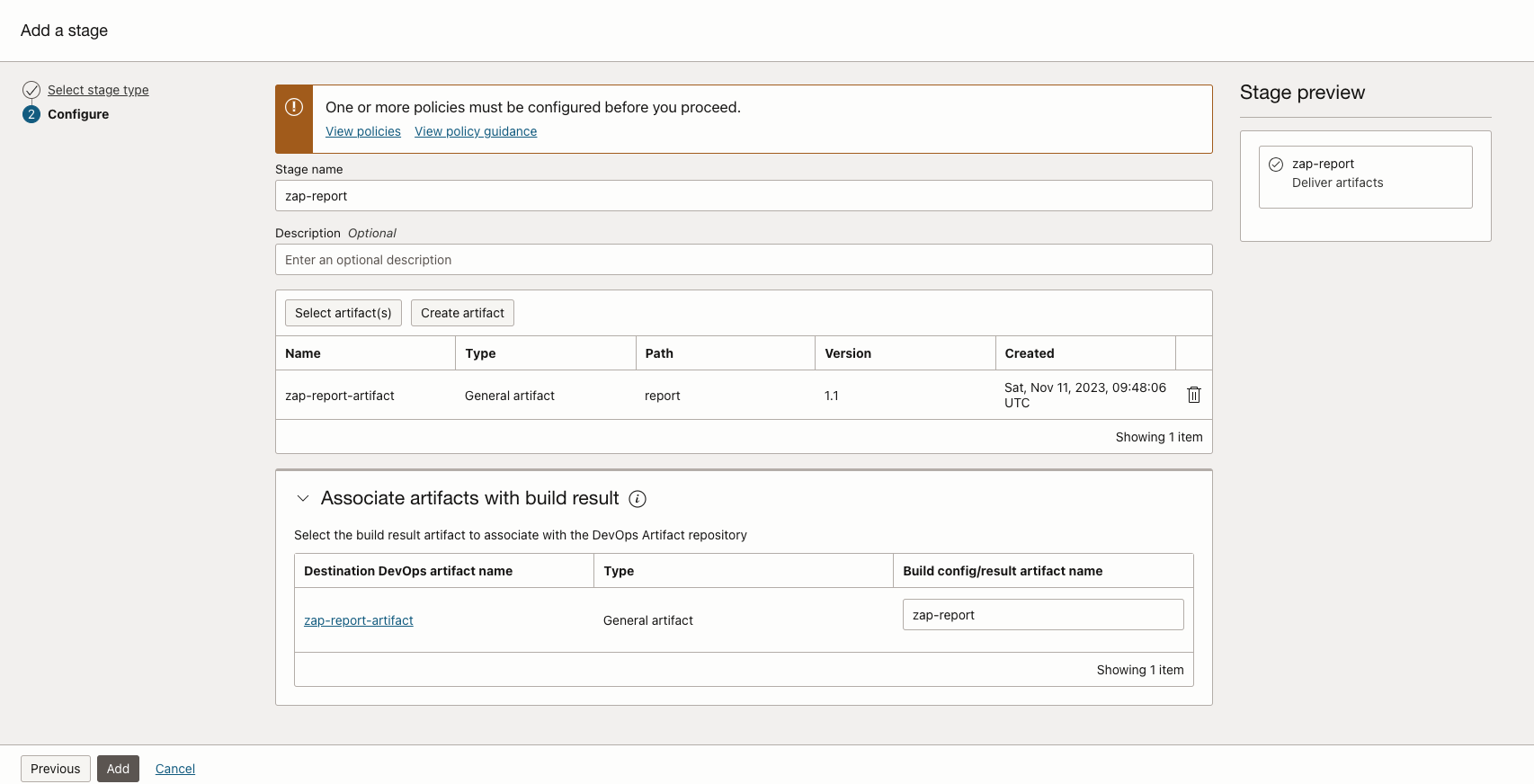
-
-
The build pipeline is shown in the following image. Click Start manual run to run the pipeline.

-
After the pipeline runs successfully, you can download ZAP report from the artifact registry.

Next steps
The generated ZAP report will help in understanding the Vulnerabilities and Warnings that are found during the ZAP Scan. This build spec configuration is performing a baseline-scan. You can also perform the ZAP - Full Scan, which performs actual ‘attacks’ and can potentially run for a long period of time.
ZAP scan can be done first on a test environment. If there are no vulnerabilities found in the test environment, the application can be rolled out to Production.
Related Links
Acknowledgments
- Author: Nikhil Khandelwal (Enterprise Cloud Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Integrate Zed Attack Proxy with Oracle Cloud Infrastructure DevOps Build Pipeline
F89773-01
November 2023
Copyright © 2023, Oracle and/or its affiliates.