Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Migrate a Red Hat Enterprise Linux Virtual Machine from Amazon Web Services to Oracle Cloud Infrastructure
Introduction
Migration from Amazon Web Services (AWS) to Oracle Cloud Infrastructure (OCI) is an increasingly frequent endeavour for many organizations, as OCI is a next-generation cloud that allows applications to run faster and more securely, for less.
Virtual Machine (VM) migration is often a core part of such an endeavour, leading customers to look for appropriate guidance on how to migrate them from AWS to OCI. Additionally, for many organizations, Linux constitutes the bulk of their infrastructure. This tutorial, therefore, is focused on the migration of Virtual Machines running one of the most widely used Linux distribution in the world (Red Hat Enterprise Linux) from AWS to OCI.
This tutorial provides customers with guidance on the requirements for virtual machine migration to OCI and how to prepare and migrate a Red Hat Enterprise Linux VM from AWS to OCI, so that it can be launched in OCI in Paravirtualized mode. OCI also allows instances to be launched in Emulated mode, but VMs using Paravirtualized devices provide much faster performance compared to running in emulated mode, with at least six times faster disk I/O performance.
The overall process consists of preparing the VM in AWS, exporting it to Amazon Simple Storage Service (Amazon S3), transferring it to OCI Object Storage, creation of a custom image in OCI and launching an instance from it. Image transfer between Amazon S3 and OCI Object Storage is performed using the open source tool rclone, if you are just experimenting with small size images, you can do it manually. We recommend using rclone, though, as it makes transferring images a much faster and simpler process.
Objectives
-
Prepare a Red Hat Enterprise Linux VM in AWS for migration to OCI.
-
Export the prepared VM as an image to Amazon S3.
-
Transfer the image to OCI and create an instance from it.
Prerequisites
-
Access to an AWS account that can create or already has API keys and has access to Amazon S3 and Amazon Elastic Compute Cloud (Amazon EC2).
-
Access to an OCI tenancy and compartment for the image migration and instance launch.
-
Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) policies to:
-
Allow access to OCI Object Storage.
-
Provision a VM in OCI (for the rclone VM and the custom image based VMs).
-
Allow creation of OCI API keys.
-
Assumptions
-
AWS VM provisioned with
pempublic key. -
The AWS RHEL VM has only 1 volume: boot volume.
-
AWS image is exportable; the Amazon Machine Image (AMI) used in this tutorial is the AWS platform image for RHEL
9.3.0as of March 2024. -
SSH connectivity with user provided by default by AWS:
ec2-user. -
AWS command line operations performed on AWS CloudShell. You can, alternatively, use AWS CLI tool.
-
Oracle Linux VM provisioned in OCI and with SSH connectivity to Amazon S3. This is the VM where you will install and configure rclone for transferring images between Amazon S3 and OCI Object Storage.
Task 1: Prepare Data Transfer Infrastructure
This tutorial uses the following data transfer architecture:
-
Image transfer via the Internet between Amazon S3 and OCI Object Storage performed by rclone. For a production grade deployment, the use of Oracle Cloud Infrastructure site-to-site VPN or FastConnect is recommended. For more information, see VPN Connection to AWS and FastConnect.
-
Rclone configured with user principal authentication for secure access to Amazon S3 and OCI Object Storage.
Task 1.1: Prepare Amazon S3 and OCI Object Storage Buckets
In this task, we will create a bucket in:
- Amazon S3 for images to be exported to.
- OCI Object Storage to store VM disk images transferred from Amazon S3.
Create a bucket in Amazon S3 with the following properties:
- Access control lists (ACLs) enabled. We will need to attach a custom ACL to allow an image to be exported to Amazon S3.
- Block all public access.
In the Amazon S3 bucket permissions, attach an ACL to the bucket, using the grant that matches the AWS region you are working on, as shown in the following image. Consult the grantee region-specific canonical account IDs here: Exporting an instance as a VM using VM Import/Export.
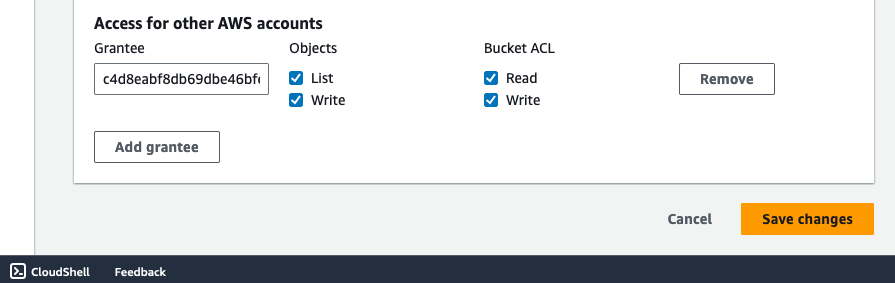
Finish this task by creating a bucket in OCI Object Storage on the standard storage tier. This is the bucket to which you will later transfer the VM image from Amazon S3.
Task 1.2: Install and Configure Rclone
In this task, we will install rclone in a VM running on OCI. You can install rclone on your local machine if you are experimenting with small size VMs and configure rclone with 2 remotes: Amazon S3 and OCI Object Storage.
-
Install rclone and SSH into the Oracle Linux VM in OCI.
sudo -v ; curl https://rclone.org/install.sh | sudo bash -
Perform the remotes configuration in rclone. This is done by starting a rclone configuration session. Run the following command in the command line.
rclone config -
For Amazon S3 remote configuration, enter the following information.
- Remote Name: Enter a remote name.
- Remote Type: Select S3 type.
- Provider: Select AWS.
- access_key_id: Enter the access key id associated with the AWS user you have decided to use.
- secret_access_key: Enter the secret access key matching the access key id.
- Region: Select the AWS region you are working on.
- location_constraint: Select the location constraint that matches the Amazon web region you are working on. For some regions (such as Frankfurt), this could be empty.
- acl: Select private to make sure you are creating the more restricted canned ACL. For more information, see Canned ACL.
-
For rclone access to OCI Object Storage, this tutorial uses an OCI user and API signing keys. Alternatively, you can use dynamic groups. For more information, see Calling Services from an Instance.
Before configuring the OCI Object Storage remote, we will:
-
Create OCI API signing keys for rclone to authenticate into OCI Object Storage and perform the image data transfer. To create the API signing keys and take note of the directory where you store the keys on the VM because you will need to provide it in the OCI configuration file, see How to Generate an API Signing Key.
-
Create an OCI configuration file. This configuration file requires the OCI API signing keys. For more information, see SDK and CLI Configuration File.
To understand authentication options for rclone with the OCI provider, see Announcing native OCI Object Storage provider backend support in rclone.
-
-
The OCI configuration file is typically stored as a
confignamed file in the directory.~/.oci/ -
Once you have created OCI API signing keys and the OCI configuration file, you can configure the OCI remote in rclone. Run the following command to start the configuration session.
rclone config -
Enter the following information for OCI Object Storage remote configuration.
- Remote Name: Enter a remote name.
- Type: Select Oracle Object Storage.
- Provider: Select
user_principal_auth(as you will be using an OCI user and API signing keys), if you use a dynamic group, selectinstance_principal_auth. - Namespace: Enter the tenancy namespace.
- Compartment: Enter the OCI bucket compartment Oracle Cloud Identifier (OCID).
- Region: Enter the region where you are working in OCI.
- Endpoint: Leave blank or enter the endpoint in this format:
https://<namespace>.objectstorage.<region-code>.oci.customer-oci.com/n/<namespace>.
-
Check the rclone remote configuration file using the following command.
cat ~/.config/rclone/rclone.conf
Task 2: Prepare Source VM Boot Volume
Task 2.1: Perform a Mandatory Snapshot of the AWS VM Boot Volume
Perform a snapshot of the AWS VM boot volume. This is mandatory before starting any boot volume configuration activity.
Task 2.2: Enable Serial Console
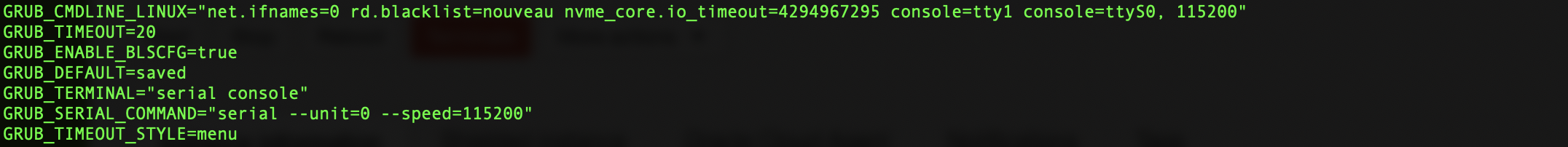
Serial console connections allow a user to troubleshoot a VM, performing activities such as system configuration files editing and password resets. Typically, to prepare a VM for serial console, the GRUB boot loader file needs to be configured. This file resides in /etc/default/grub.
The most important GRUB configuration parameters are:
- GRUB_TIMEOUT_STYLE: make sure it is commented if its value is "hidden"; alternatively, change it to "menu"
- GRUB_TIMEOUT: make sure it is higher than 0 to allow boot mode selection without skipping directly to the default option. Specify this value in both files.
- GRUB_CMDLINE_LINUX: make sure "console=tty1 console=ttyS0, 115200" is appended to it
- GRUB_TERMINAL: make sure its value is "serial console"
- GRUB_SERIAL_COMMAND: make sure its value is "serial -- unit=0 --speed=115200"
-
Open
/etc/default/grub.sudo vi /etc/default/grubEdit the file so that it looks like the file shown in the following image.
-
After editing the file, run the following command to make sure the GRUB boot loader is adequately updated.
sudo grub2-mkconfig -o /boot/grub2/grub.cfg
Task 2.3: Check Paravirtualization Drivers
To import a VM to OCI so that it can launch in Paravirtualized mode, Paravirtualization VirtIO drivers need to be present in the image. In this task, we will check both the kernel and the initramfs temporary filesystem to confirm the presence of the drivers. Note that Linux-based operating systems running the kernel version 3.4 or later support paravirtualized drivers; therefore, often you just need to check and confirm they are present.
The minimum set of VirtIO drivers needed includes pci, scsi. These drivers should be present in the kernel or in initramfs.
-
Check the kernel of the AWS VM by using the following command.
sudo grep -i virtio /boot/config-$(uname -r)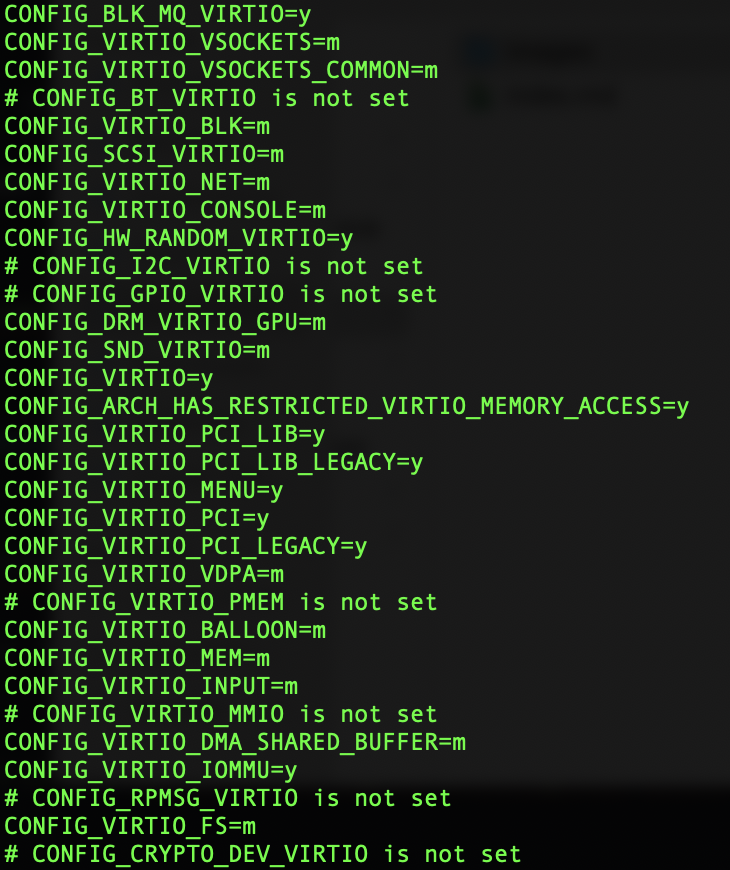
Note: The
pciVirtIO driver is present in the kernel. -
Check the kernel of the AWS VM by using the following command.
sudo lsinitrd /boot/initramfs-$(uname -r).img | grep virtio
Note: The
scsiVirtIO driver is present in initramfs. -
If the boot volume of your VM does not have the drivers, you will need to rebuild the initramfs with
dracut.sudo dracut -v -f --add-drivers “virtio virtio_pci virtio_scsi” /boot/initramfs-$(uname -r).img $(uname -r)
Task 2.4: Configure Networking settings
For the networking configuration, ensure:
- The VM is using DHCP.
- Any MAC Address hardcoded references in the networking configuration are removed.
There are several ways of performing networking configuration on Linux. Specifically in RHEL, ethernet connections configuration can be performed either by editing networking configuration files in /etc/sysconfig/network-scripts/ifcfg-eth0 or by using NetworkManager. This tutorial uses the latter to perform the necessary networking configuration. For more information, see Configuring an Ethernet connection.
-
Run NetworkManager command line tool (
nmcli) to see a summary of the networking configuration of the VM.
-
To list the connections available in the VM, run the following command.
nmcli connection showYou will find a list of connections. The VM used in this tutorial has the following connections.
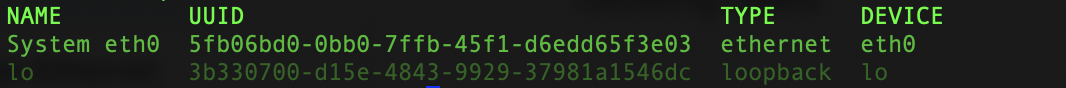
-
Confirm the ethernet connection associated with
eth0using Dynamic Host Configuration Protocol (DHCP).nmcli connection show <connection UUID>Scroll until you find the
ipv4.methodparameter. It should have the valueauto.
-
Edit the connection associated with interface
eth0. You will remove the MAC address from the interface configuration by using the following command.sudo nmcli connection modify <connection UUID> 802-3-ethernet.mac-address '' -
Apply these changes by using the following command.
sudo nmcli con up <connection UUID> -
Additionally, check the
/etc/udev/rulesdirectory to see if there are any udev rules files containing MAC address hardcoded rules and delete them. The AWS image used in this tutorial has one such file70-persistent-net.rules. Run the following command to delete this file.sudo rm /etc/udev/rules.d/70-persistent-net.rules
The networking configuration is now complete. You can confirm by checking the file /etc/sysconfig/network-scripts/ifcfg-eth0.
Task 3: Export Virtual Machine Image to Amazon S3
This task requires the use of AWS CLI. This tutorial uses the AWS CloudShell, because it skips AWS CLI configuration tasks.
-
Stop the VM. Open the AWS CloudShell and run the following command to export the image.
aws ec2 create-instance-export-task --instance-id <instance-id> --target-environment vmware --export-to-s3-task DiskImageFormat=vmdk,ContainerFormat=ova,S3Bucket=<bucket name> -
Enter the following information.
- Disk Image Format: Enter VMDK, as it is the only AWS export format supported by OCI.
- Container Format: Enter OVA, to combine the disk image with metadata about the VM. Alternatively, you can export this parameter.
- Target environment: Enter vmware, as it is the only target environment supported in OCI.
-
You can monitor the state of the export task by running the following command in the AWS CloudShell.
aws ec2 describe-export-tasks --export-task-ids <export task id>sWhen you first launch the task, you will find it in the active state. Once it finishes, you will find it in the completed state.
Task 4: Transfer Image to OCI Object Storage
SSH into the OCI VM in which rclone was configured in Task 1.2. Perform the copy of the exported image from the AWS S3 bucket to the OCI Object Storage bucket.
rclone copy <aws-remote>:<bucket>/<imagefile> <oci-remote>:<bucket> -vv
Task 5: Create Custom Image in OCI and Launch Instance
-
In the OCI Console, go to Custom Images on the Compute Service and select Import Image
-
Enter the following information.
- Compartment: Select compartment, where you want to create the custom image.
- Name: Enter the name for the custom image.
- Operating System: Select RHEL.
- Source: Import from an Object Storage bucket. Select the bucket you configured in Task 1.1.
- Object Name: Select the image you transferred from Amazon S3.
- Launch Mode: Select Paravirtualized mode.
-
Click Import image to start the image import.
-
Once the image is created, you are ready to launch an instance from it. In the custom image details page, select Create instance and enter the following information.
- Name: Enter the name for instance.
- Compartment: Select compartment, where you want to launch the instance.
- Availability Domain.
- VCN and Subnet. For the purposes of this tutorial you can use a public subnet to skip VPN connectivity.
- SSH Keys: You have two options: either generate new SSH keys or use the same set of keys you used in AWS. If you want to keep using the same set of keys, upload the same public key you used in AWS for the source VM. Assuming your AWS public key is in the
.pemkey format, change it to.pem.pubin order to upload it to the OCI instance. This will allow you to keep using the same private key to SSH into the VM.
-
Launch the virtual machine. Once provisioning finishes, you can connect to it. Notice that the user you connect with is ec2-user, not opc.
ssh -i pathToKey/keyfile ec2-user@<publicIp>
Related Links
-
Troubleshooting Instances Using Instance Console Connections
-
Announcing native OCI Object Storage provider backend support in rclone
-
Migrate Data to Oracle Cloud Infrastructure Object Storage Using Rclone
Acknowledgments
- Author - Ricardo Malhado (Principal Cloud Solution Architect)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Migrate a Red Hat Enterprise Linux Virtual Machine from Amazon Web Services to Oracle Cloud Infrastructure
F95983-01
April 2024