Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Update the authentication flow for Oracle Essbase users to a different Identity Cloud Service
Introduction
Oracle Essbase is a business solution that uses a proven, flexible, best-in-class architecture for analysis, reporting, and collaboration. Oracle Essbase delivers instant value and greater productivity for your business users, analysts, modelers, and decision-makers, across all lines of business within your organization. When you deploy Oracle Essbase from the Marketplace it is a stack deployment and you as an administrator need to pass the Identity Cloud Service parameters to the stack.
Prerequisites
- Identity Cloud Service administration access for both the Identity Cloud Service instances.
- SSH instance access to the compute instance where Oracle Essbase is deployed.
- User migration of the existing Oracle Essbase users from old Identity Cloud Service to the new Identity Cloud Service.
- Migration of any policy/configuration related to Oracle Essbase from old Identity Cloud Service to the new Identity Cloud Service.
Objectives
This tutorial describes how you can update the Identity Cloud Service references and link Oracle Essbase to another Identity Cloud Service for authentication and authorization.
Note: You must make these changes on the test instance first to check for any possible impact to a working piece and/ or any impact with respect to the access/role of the Oracle Essbase user.
Task 1: Register a Confidential Application in Identity Cloud Service
We will register a Confidential Application in the new Identity Cloud Service where you want to route the authentication flow for your Oracle Essbase users.
- Register the confidential application by following the steps mentioned HERE.
Task 2: SSH to the compute instance where Oracle Essbase is deployed
- SSH into the compute instance where you have installed Oracle Essbase.
Note This tutorial considers that the compute instance with Oracle Essbase has public SSH access. If your compute instance does not have public SSH access, create a Bastion session to access the instance privately. The steps are mentioned HERE.

Task 3: Locate and update the files with Identity Cloud Service references
-
Update the
99_essbase.conffile. Before you make any changes to the file, you must create a backup copy of the file.-
Location of the File -
cd /etc/httpd/conf.d -
Linux Command -
sudo cp -p /etc/httpd/conf.d/99_essbase.conf /etc/httpd/conf.d/99_essbase.conf.original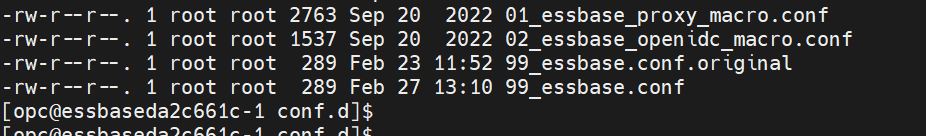
-
-
Edit the
99_essbase.conf fileand modify the old Identity Cloud Service details with the new Identity Cloud Service details.-
Linux Command -
sudo vi /etc/httpd/conf.d/99_essbase.conf -
Update the below mentioned highlighted details and Save.
``` Change: # Create OIDC configuration Use EssbaseOIDC <<OLD-Identity Cloud Service-GUID>>> identity.oraclecloud.com <<OLD-Identity Cloud Service-Client ID>> <<OLD_IDCS-Client Secret>> <<Encrypted-Field>> to # Create OIDC configuration Use EssbaseOIDC <<NEW-Identity Cloud Service-GUID>>> identity.oraclecloud.com <<NEW-Identity Cloud Service-Client ID>> <<New_IDCS-Client Secret>> <<Encrypted-Field>> ```Note: The Encrypted-Field should be left as is and we will update it later in the process.

-
-
Restart the httpd service:
sudo systemctl restart httpd -
Encrypt the new Identity Cloud Service client secret and update it.
-
Switch to Oracle user:
sudo su oracle -
Encrypt the new Identity Cloud Service Client secret:
/u01/vmtools/bin/run-encrypt.sh <<New_IDCS-Client Secret>>. Note down the output of this command as «New_Encrypted_IDCS-Client Secret».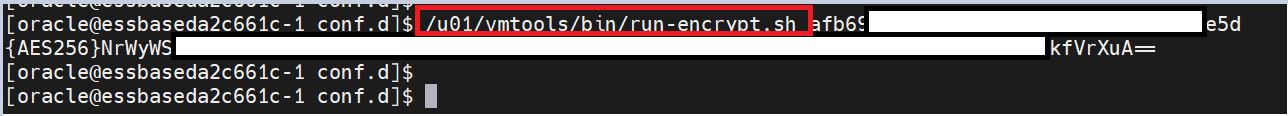
-
Back up the
config.xmlfile.-
Location of the file -
cd /u01/config/domains/essbase_domain/config** -
Linux Command-
cp -p /u01/config/domains/essbase_domain/config/config.xml /u01/config/domains/essbase_domain/config/config.xml.original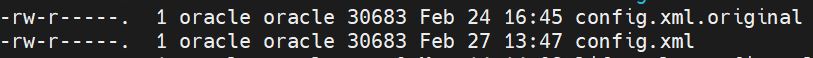
-
-
Update the
config.xmlfile with the new Identity Cloud Service Details.-
Linux Command -
vi /u01/config/domains/essbase_domain/config/config.xml. -
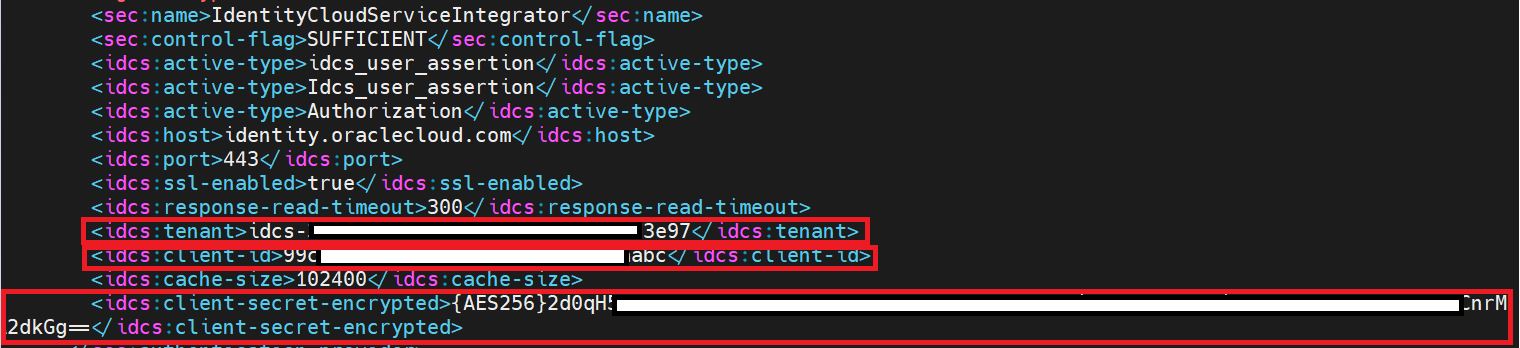
Update the below mentioned details and Save.
-
<idcs:tenant>- New Identity Cloud Service Tenant ID. -
<idcs:client- id>- New Client ID of the application you created in New Identity Cloud Service instance. -
<idcs:client-secret-encrypted>- This is the new value generated in Step 2.
-
-
-
Task 4: Restart Oracle Essbase and test the login flow with the updated Identity Cloud Service instance
-
As an Oracle user, Stop Oracle Essbase by executing the
stop.shscript.-
Location to the script file -
cd /u01/config/domains/essbase_domain/esstools/bin -
Execute the file as
./stop.sh
-
After the Stop script is successfully executed, start Oracle Essbase by executing the
start.shcommand.
-
Note: This will have a downtime for your Oracle Essbase application and needs to done first at the test instances for checking any impact on the functionality.
Task 5: Test access for the new Identity Cloud Service
- Open the Oracle Essbase external URL in the browser.
- The browser should redirect you to the new Identity Cloud Service login page.
- Enter the credentials of an existing Oracle Essbase user (The user should also exist in the new Identity Cloud Service).
- Post successful authentication, browser should route to the Oracle Essbase landing page.
- Look closely for any impact in the role/access specific for the Oracle Essbase user account that you logged in with.
Note If you see any abnormalities in the access or/and roles for the user, Do not Proceed for the Production instance and open a Service Request with Oracle Support for more details and guided assistance.
Related Links
-
Oracle Essbase Stack Deployment on Oracle Cloud Infrastructure
-
Unable to Login to Oracle Essbase After Identity Cloud Service Client Secret is Regenerated
Acknowledgments
Author - Chetan Soni (Cloud Solutions Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Update the authentication flow for Oracle Essbase users to a different Identity Cloud Service
F80265-01
June 2023
Copyright © 2023, Oracle and/or its affiliates.