Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Configure seamless authentication for PeopleSoft applications using OCI IAM Identity Domains
Introduction
Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) Identity Domains is a comprehensive identity-as-a-service (IDaaS) solution that can be used to address a variety of IAM use cases and scenarios. OCI IAM can be used to manage access for users across numerous cloud and on-premises applications, enabling secure authentication, easy management of entitlements, and seamless SSO for end users. You might also want to configure an identity domain to enable access to supply chain or ordering systems for business partners. Alternatively, you can also use identity domains to enable IAM for consumer-facing applications and allow consumer users to perform self-registration, social logon, and/or terms-of-use consent.
If you need to provide a seamless sign-in experience between your Oracle PeopleSoft application (either on-premises or on OCI), use OCI IAM Identity Domains to enable single sign-on. OCI IAM Identity Domains has a feature called App Gateway which is a Nginx-based, software appliance deployed in a proxy configuration. To enhance security, you can leverage Adaptive security in sign-on policies to enforce allow-or-deny access, or to step-up authentication to a stricter MFA mechanism.
Audience
This tutorial is intended for OCI IAM Administrators. Familiarity with compute, networking and storage in a virtual environment is assumed, including IAM concepts. Knowledge of OCI IAM is required.
Objective
Configure seamless authentication for PeopleSoft applications using OCI IAM Identity Domains.
Prerequisites
- OCI IAM Identity Domains tenancy with Oracle Apps Premium license is required for using the App Gateway feature.
- A user with Identity Domain Administrator or Security administrator role is required on the domains to download the App Gateway file and register a confidential application.
- A fully functional PeopleSoft HCM Application.
Architecture
This architectural diagram shows the flow between OCI IAM Identity Domain, App Gateway and Oracle PeopleSoft application.
App Gateway acts as a reverse proxy. It intercepts all HTTP requests to the PeopleSoft web user interface and ensures that the user is logged in and authorized to access the application. OCI IAM Identity Domain handles authentication for PeopleSoft application.
Note: App Gateway is deployed on the same network infrastructure as Oracle PeopleSoft application. These two components must have network visibility into one another. Only access to HTTP resources (web UI mainly) is protected by the App Gateway.
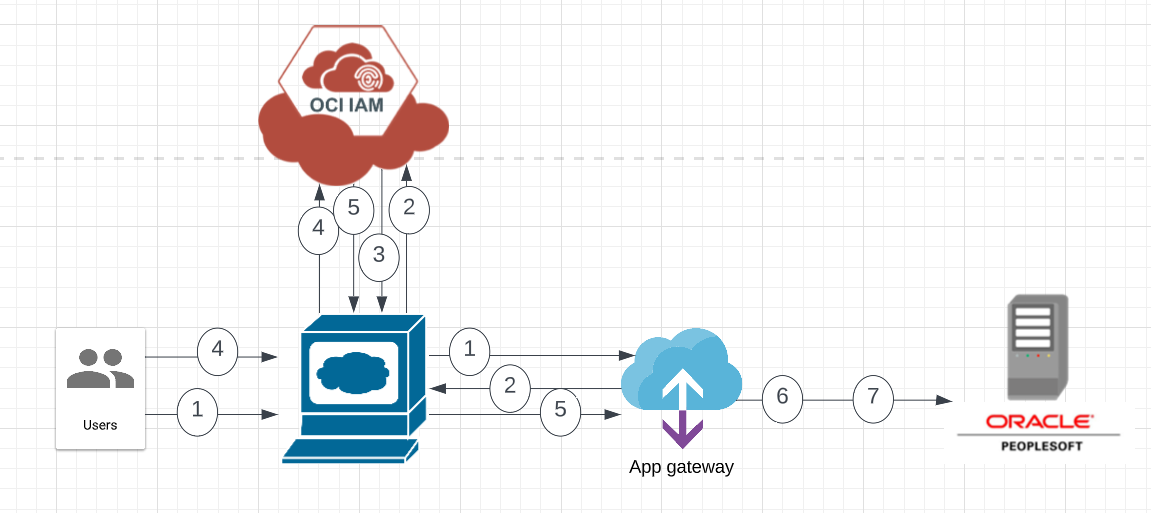
The following steps explain the authentication flow between the different components:
- In a web browser, a user requests access to PeopleSoft application through a URL exposed by App Gateway.
- App Gateway intercepts the request, verifies that the user hasn’t signed in previously, and then redirects the browser to OCI IAM Identity Domain.
- OCI IAM Identity Domain presents the sign-in page.
- The user provides the credentials needed to sign in to Identity Domain.
- Upon successful authentication, OCI IAM Identity Domain creates a session for the user and issues a Security Assertion Markup Language (SAML) token to App Gateway.
- App Gateway receives the SAML token, identifies the user, adds header variables in the request, and forwards the request to PeopleSoft app.
- PeopleSoft app receives the header variables, identifies the user, and starts the PeopleSoft user session.
Task 1: Set up the App Gateway Server
The software appliance app gateway, gets downloaded from the OCI IAM Identity Domain console in a compressed (.zip) file. This file contains an Open Virtual Appliance (.ova) file which needs to be used to install the App Gateway server.
App Gateway server can be easily installed in a compute instance on OCI or in a virtual machine hosted in your network environment or in an Oracle VM Virtual Box Manager running on your local machine, using the steps mentioned in this document.
Note: App gateway can be also deployed using Docker. This document talks about how to create and run the App Gateway Docker container.
Task 2: Create an Enterprise application in OCI IAM Identity Domains for the PeopleSoft Application
In the following steps, we will create an enterprise application in OCI IAM for the PeopleSoft application, using the URLs exposed by the App Gateway.
-
Log in to the OCI tenancy and navigate to the respective Identity Domain.
-
Click Applications, go to Add application tab and then select Enterprise Application to Launch workflow.
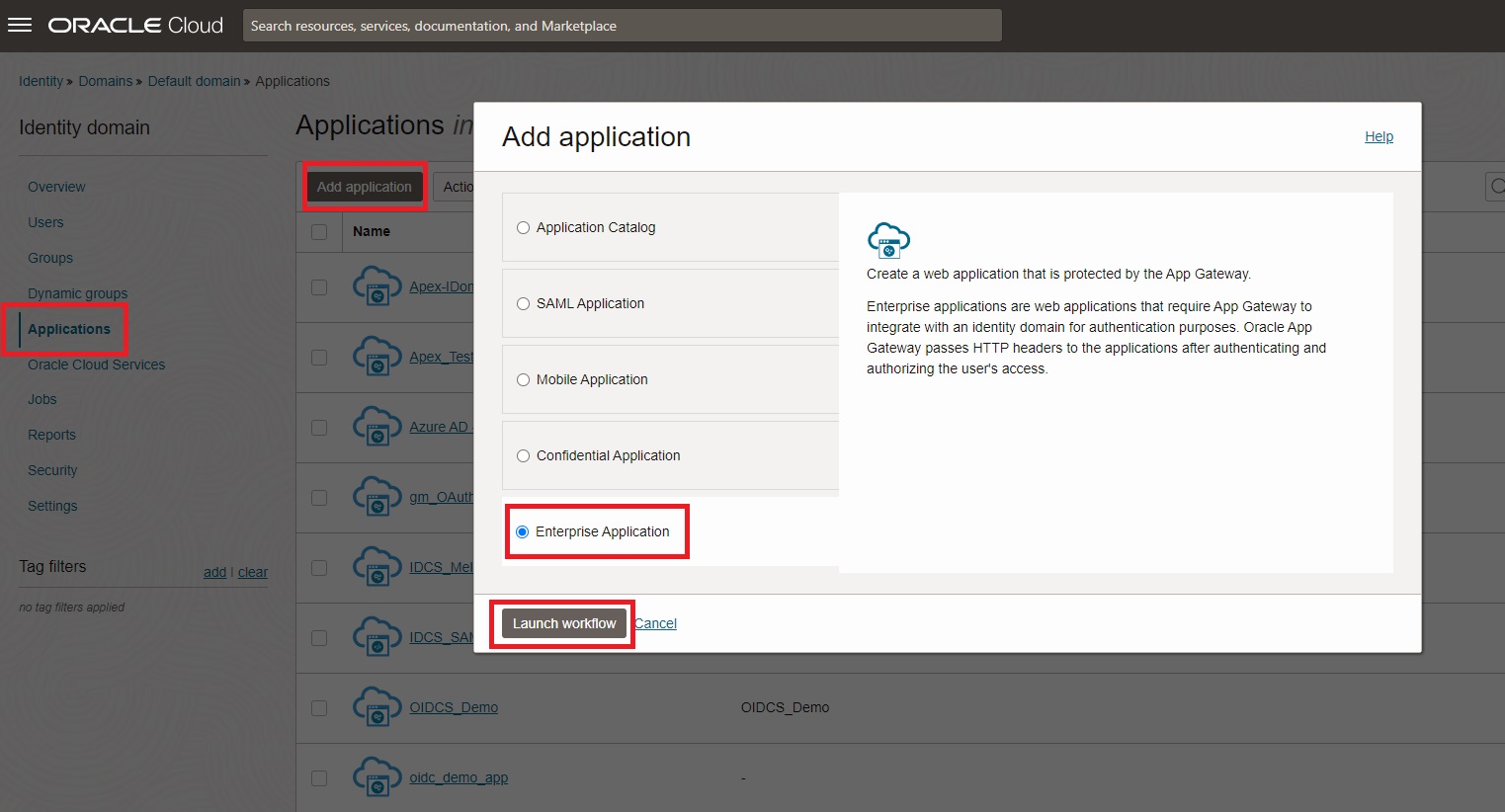
-
Provide a Name for the application and the Application URL.

Note:
- The Application URL is exposed by the App Gateway and hence the IP address and port is of the App Gateway server.
- This tutorial uses the PeopleSoft ERP application and hence the endpoint
/psc/peoplesoft01_22/EMPLOYEE/ERP/c/NUI_FRAMEWORK.PT_LANDINGPAGE.GBL?. - For PeopleSoft HCM, use
/psc/peoplesoft01_22/EMPLOYEE/HRMS/c/NUI_FRAMEWORK.PT_LANDINGPAGE.GBL?.
-
Select the Display in My Apps to display the application in the My Apps page of the assigned users. Select Users must be granted this app if you want to allow only the assigned users to access the app.

-
Select Skip for later in the Configure OAuth section.

-
In the Configure single sign-on section, click Add resource to add the following resources.

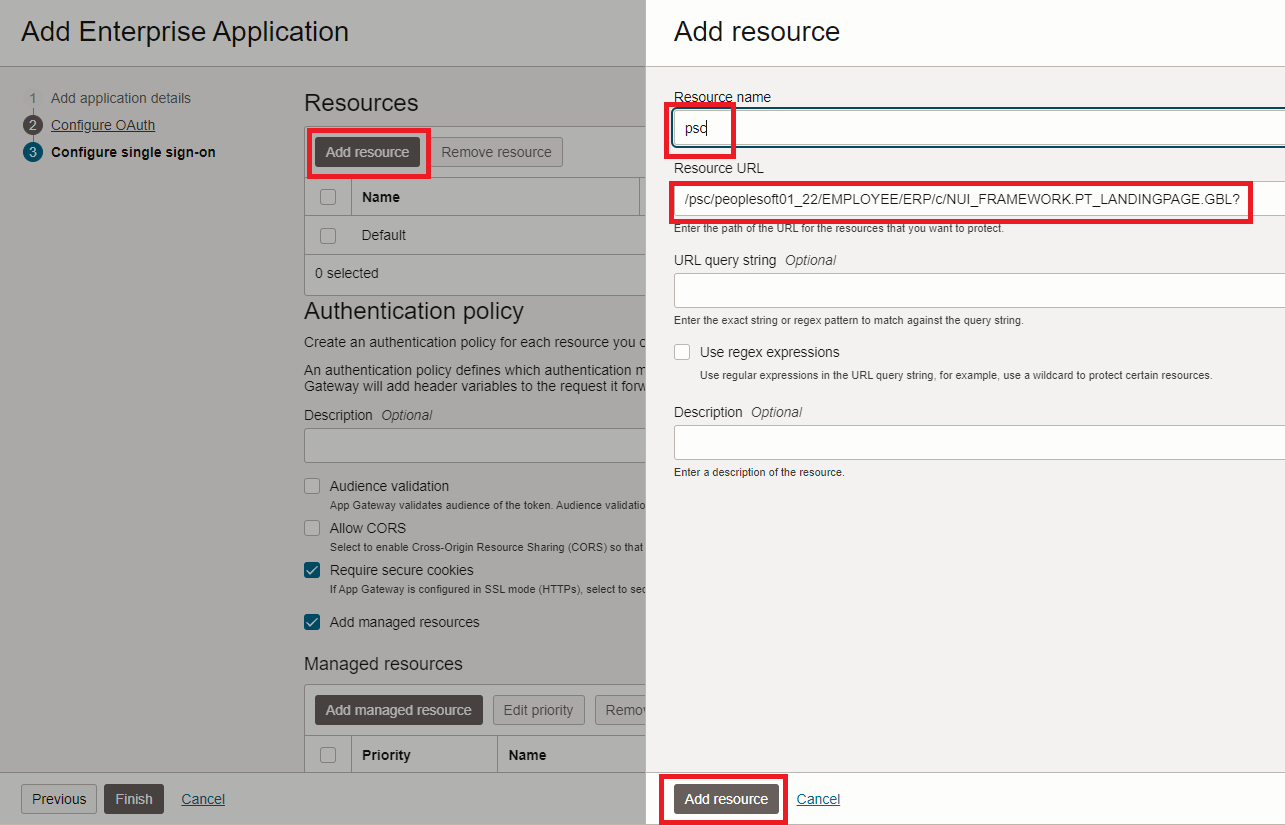
-
Once the resources are added, create an authentication policy for each resource by clicking Add managed resource and selecting the Authentication method as Form or Access token.
-
Add the mentioned Headers name and value.
-
Make sure that
Require secure cookiesandAdd managed resourcesoptions are enabled.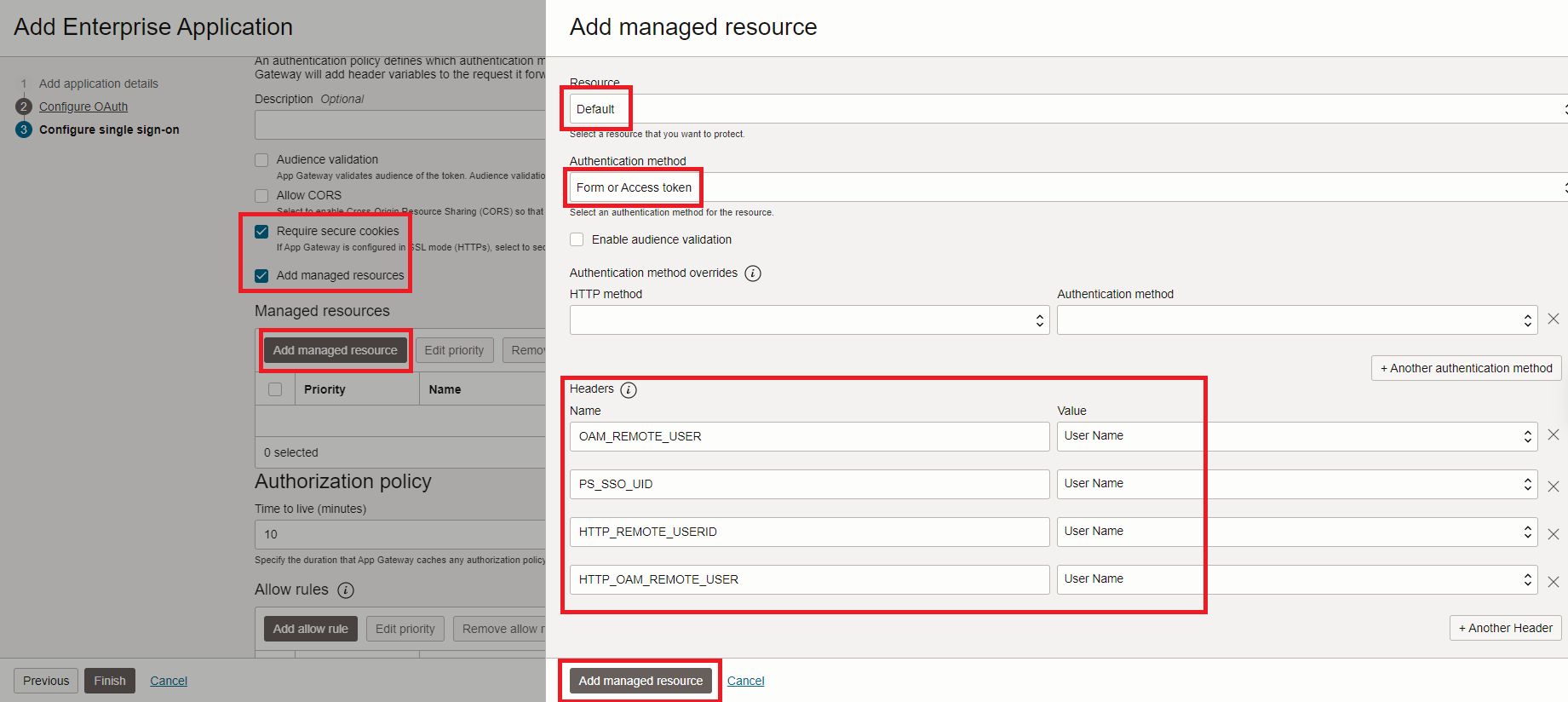

Note: The authentication policy defines which authentication method to use to protect your enterprise application resources and whether App Gateway will add header variables to the request it forwards to the application.
-
-
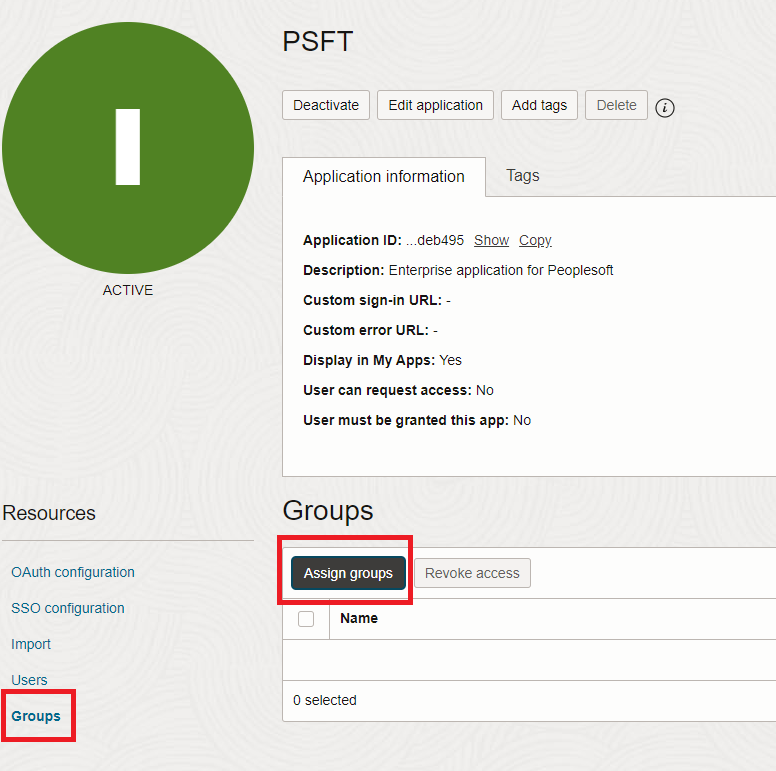
Activate the application once the setup is finished and then assign it to the appropriate
usersorgroups.
Task 3: Register the App Gateway server in OCI IAM Identity Domains
Before configuring the App Gateway, we must register the deployed App Gateway server in Identity Domains. We will add the host and associate the host with the PeopleSoft enterprise application in Domains, which App Gateway will protect.
-
In the OCI Identity Domains console, click Security, click App Gateways, and then click Create App Gateway.

-
Specify the Name of your App Gateway, and then click Next.

-
In the Add Hosts pane, click Add host.
-
In the Add Host dialog, provide a name in the Host Identifier field.
-
Enter the Host and Port values that the App Gateway server will respond to HTTP requests.
-
Enable App Gateway to listen to HTTP requests in secure mode (HTTPS), by selecting the SSL Enabled check box and click Add host.

Note: The Additional Properties text area needs to be specified with the certificate key pair the App Gateway server will use, protocols and ciphers for SSL. The /etc/ssl/private/server.crt is the full path of a certificate file in the App Gateway server. The /etc/ssl/private/server.key is the secret key of that certificate file. We must upload both files to the App Gateway server after we install the App Gateway binary file.
ssl_certificate /scratch/oracle/cloudgate/home/bin/server.crt; ssl_certificate_key /scratch/oracle/cloudgate/home/bin/server.key; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers HIGH:!aNULL:!MD5;
-
-
In the Add Apps tab, click Add App. Select the enterprise app to be protected and select the previously added host. In the Resource Prefix field, use
/and specify the base URL of the PeopleSoft application in the Origin Server.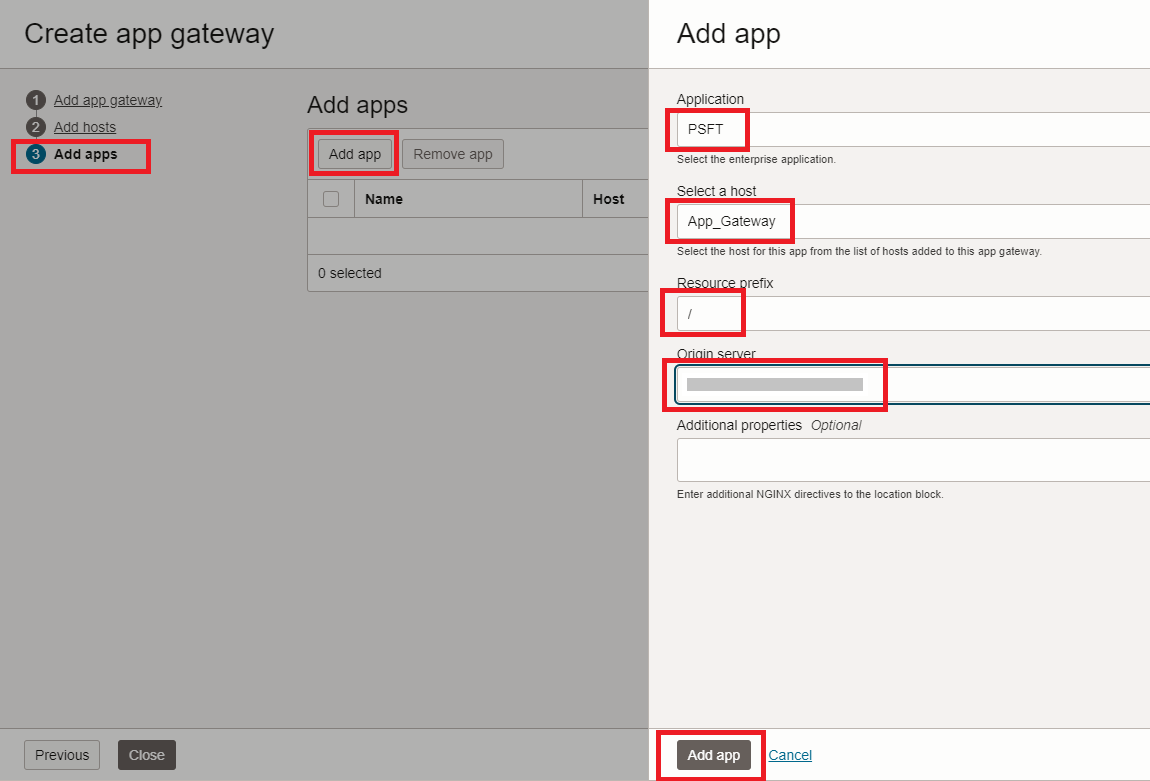
Note:
/in Resource Prefix indicates that every request aftere root path will be forwarded to the enterprise application you have selected. If the application is not directly accessible, but accessible through a web proxy, then enter the URL of the web proxy in the Origin Server field. -
Click Activate app gateway and note the Client ID and Client Secret which is to be used for configuring the App gateway.

Task 4: Configure the App Gateway
After the App gateway server is ready it can be easily accessed using the default credentials via SSH client.
Localhost login: oracle
Password: cloudgateR0X!
Note: You must change the provisioned password on the first login.
Once you are logged in to the App gateway server, execute the following steps:
-
Execute the
sudo yum updateinfo list security allcommand and provide sudo password. This command lists the security errata for your App Gateway Oracle Linux server. To update all packages for which security-related errata are available to the latest versions of the packages entersudo yum --security update.

-
Execute the
telnet <idcs-tenant>.identity.oraclecloud.comcommand to confirm that the App Gateway server can reach the OCI IAM Identity Domain instance. Iftelnetis not installed, install it usingsudo yum install telnet-server telnetcommand and then retry.

-
Generate a CSR and get it signed by a CA to configure the App gateway in SSL mode. For testing purpose or POC, self signed certificates can be used. Below are the steps to generate one.
openssl genrsa -aes128 -out server.key 2048 openssl rsa -in server.key -out server.key openssl req -new -days 3650 -key server.key -out server.csr openssl x509 -in server.csr -out server.crt -req -signkey server.key -days 3650
-
Restart the App Gateway server after applying the updates.
-
Execute the
nslookup <your_identity_cloud_service_domain>command, copy the Server IP Address, and update the resolver entry in the/usr/local/nginx/conf/nginx-cg-sub.conffile.

-
Navigate to the
/scratch/oracle/cloudgate/ova/bin/setupfolder, and then edit thecloudgate-envfile to include the following parameters.a. IDCS_INSTANCE_URL: The URL of your OCI IAM Identity Domains URL.
b. CG_APP_TENANT: The tenant name of the Identity Domain instance. For example,
idcs-123456789.c. CG_APP_NAME: The client ID value we collected during registering the App Gateway server in OCI IAM Identity Domains.
d. CG_APP_SECRET: The client secret value we collected during registering the App Gateway server in OCI IAM Identity Domains.
e. CG_CALLBACK_PREFIX: If App Gateway is configured in SSL mode (HTTPS), then set the value to
https://%hostid%. Otherwise, usehttp://%hostid%as the value for this parameter.

-
Navigate to the
/scratch/oracle/cloudgate/ova/bin/setupfolder and execute the./setup-cloudgatecommand. When prompted, enteryto proceed with the configuration. Review and verify all parameters used for the cloud gate configuration.
Note: Common problems that you might encounter while configuring the App Gateway can be easily solved by referring to this document.
Task 5 : Oracle PeopleSoft application configuration
Log in to the PeopleSoft console using admin credentials and perform the steps mentioned in the document to configure the PeopleSoft application for SSO.
Task 6 : Test access to the PeopleSoft application
After you configure the App Gateway server to communicate with your OCI IAM Identity Domains, and start the server, test access to your enterprise application. Because App Gateway proxies your PeopleSoft application, use the App Gateway base URL to access the application instead of the PeopleSoft application actual URL.
-
Open a new web browser and access the application using the App Gateway URL. In this example, the URL is:
https://##.##.##.##:4443/psc/peoplesoft01_22/EMPLOYEE/ERP/c/NUI_FRAMEWORK.PT_LANDINGPAGE.GBL?. -
App Gateway intercepts the request and communicates with OCI IAM Identity Domain to verify if the URL corresponds to an enterprise application. In this example,
PSFTis registered, and the authentication policy for this enterprise application is Form or Access Token. -
App Gateway verifies if the request contains a valid Identity Domain access token in the
Authorization Bearerheader or Identity Domain session cookie, indicating the user has already signed in to OCI IAM Identity Domain. -
If the user hasn’t signed in to OCI IAM Identity Domain, then App Gateway redirects the user browser to OCI IAM Identity Domain’s Sign In page.
-
If the user has signed in, then App Gateway adds header variables and a cookie to the request, and then forwards the request to the PeopleSoft application.
-
The application receives the request, uses the header variables to identify the user to present the content of the
/psc/peoplesoft01_22/EMPLOYEE/ERP/c/NUI_FRAMEWORK.PT_LANDINGPAGE.GBL?page.
Related Links
- OCI IAM
- Oracle Apps Premium
- Deploy PeopleSoft HCM Application on OCI
- Setup App Gateway
- Configure PeopleSoft Application for SSO
Acknowledgments
Author - Gautam Mishra (Senior Cloud Engineer)
Contributors - Deepthi Shetty (Manager Cloud Engineer), Aqib Bhat (Senior Cloud Engineer)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Configure seamless authentication for PeopleSoft applications using OCI IAM Identity Domains
F80225-01
April 2023
Copyright © 2023, Oracle and/or its affiliates.