Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Protect on-premises Web Applications with Oracle Cloud Infrastructure Load Balancer and Regional Web Application Firewall
Introduction
Oracle Cloud Infrastructure Web Application Firewall (OCI WAF) is a comprehensive security service designed to safeguard your web applications from a wide range of threats, including SQL injection, cross-site scripting (XSS), and more. By deploying this powerful firewall solution, you can fortify your web applications and reduce the risk of unauthorized access or data breaches.
Oracle Cloud Infrastructure Load Balancer acts as a virtual traffic manager, intelligently distributing incoming requests across a pool of backend servers. By efficiently balancing the load, it eliminates single points of failure and ensures that your application can handle increasing traffic volumes, providing uninterrupted service to your users.
The high-level process includes using an OCI Load Balancer attached to on-premises web application servers to distribute the load. An OCI WAF will be enforced on this Load Balancer to protect the on-premises web application from malicious traffic.
Note: You might find this tutorial useful for a swift onboarding experience with the Regional Web Application Firewall (WAF), especially if your on-premises web application server IP addresses are public and you don’t have direct control over DNS management. The objective of this tutorial is to provide users with a straightforward way to explore and experiment with the features and functionality of the WAF for web applications. The intention is to simplify the deployment and configuration process, allowing users to test the WAF’s capabilities without the complexities typically associated with deployment and setup.
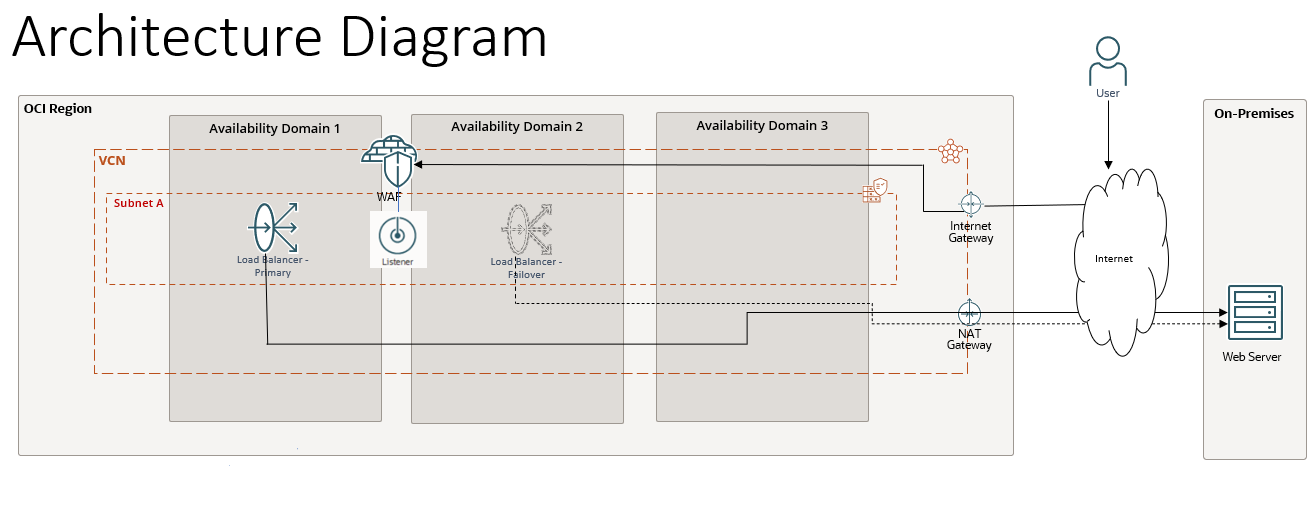
Objective
Step-by-step guide on how to create an OCI Load Balancer for on-premises web applications and enforcing WAF on them.
Prerequisites
- WAF is only compatible now for OCI Load Balancer (not Network Load Balancer) and with HTTP listeners (not TCP listeners). Documentation is available here.
- Users in OCI needs to have the required polices for creating Load Balancer and WAF. Follow the link here for creating the policies respectively.
- The on-premises web applications should be reachable via public internet, IPSec or OCI FastConnect. In this tutorial, the on-premises web application IP addresses can be reached by Load Balancer via public internet.
Task 1: Configure OCI Load Balancer
-
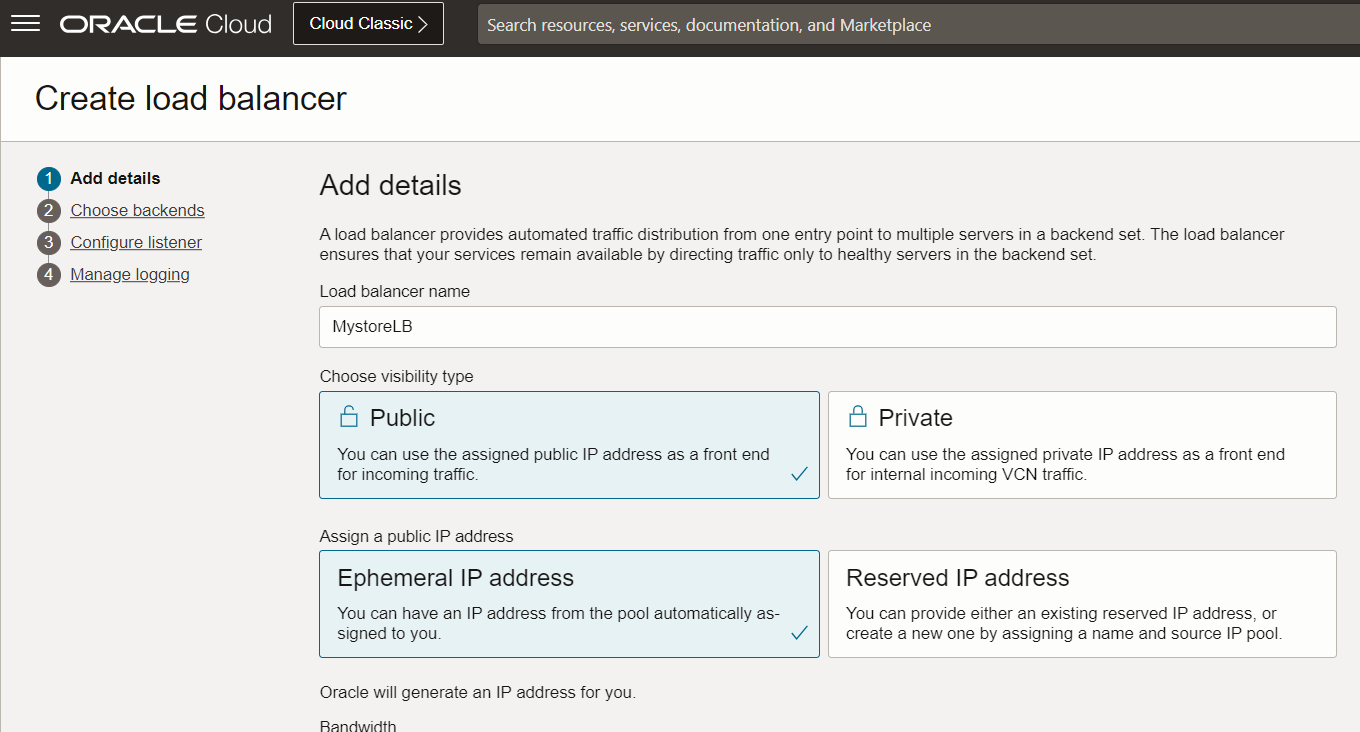
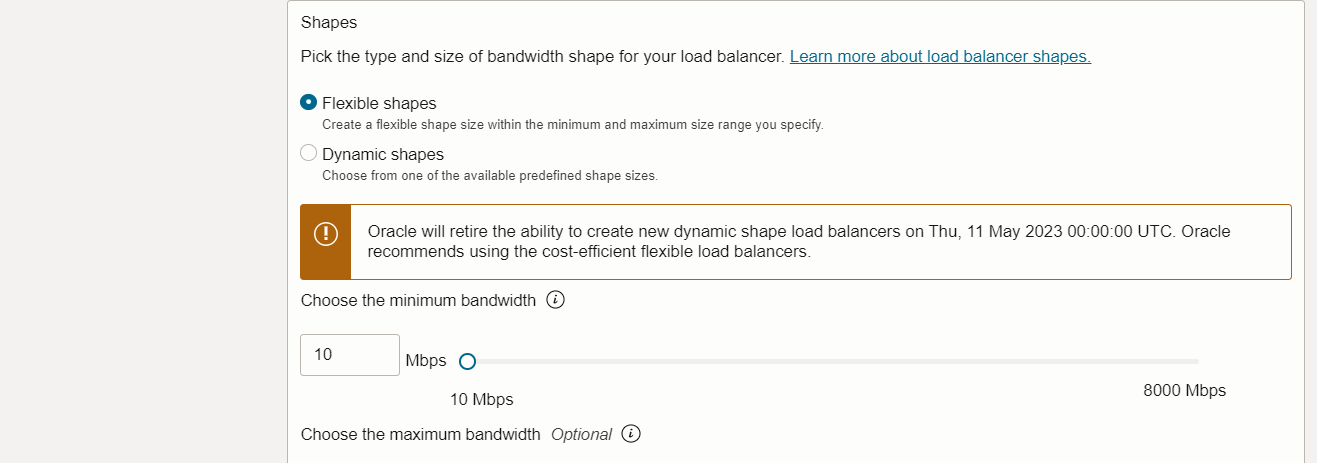
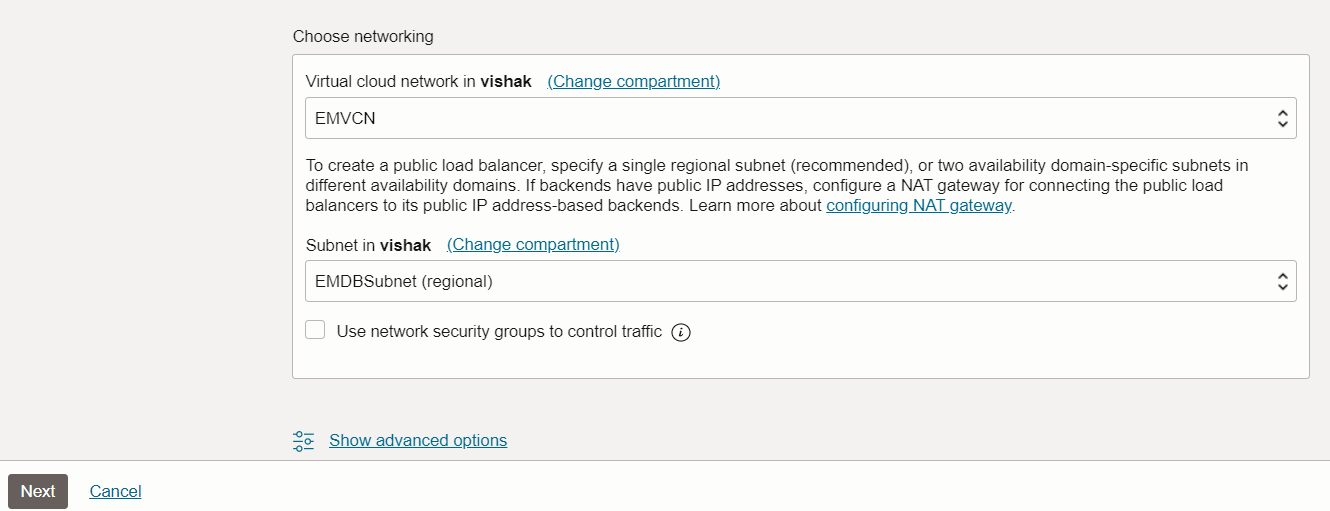
Create a Flexible Public Load Balancer in the required compartment. Navigate to OCI Console, Networking, Load Balancer, Create Load Balancer.
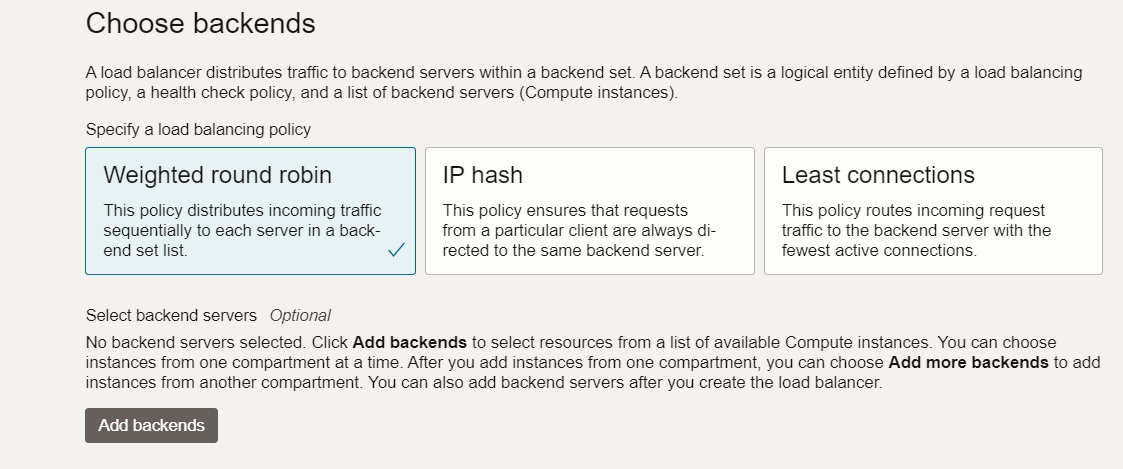
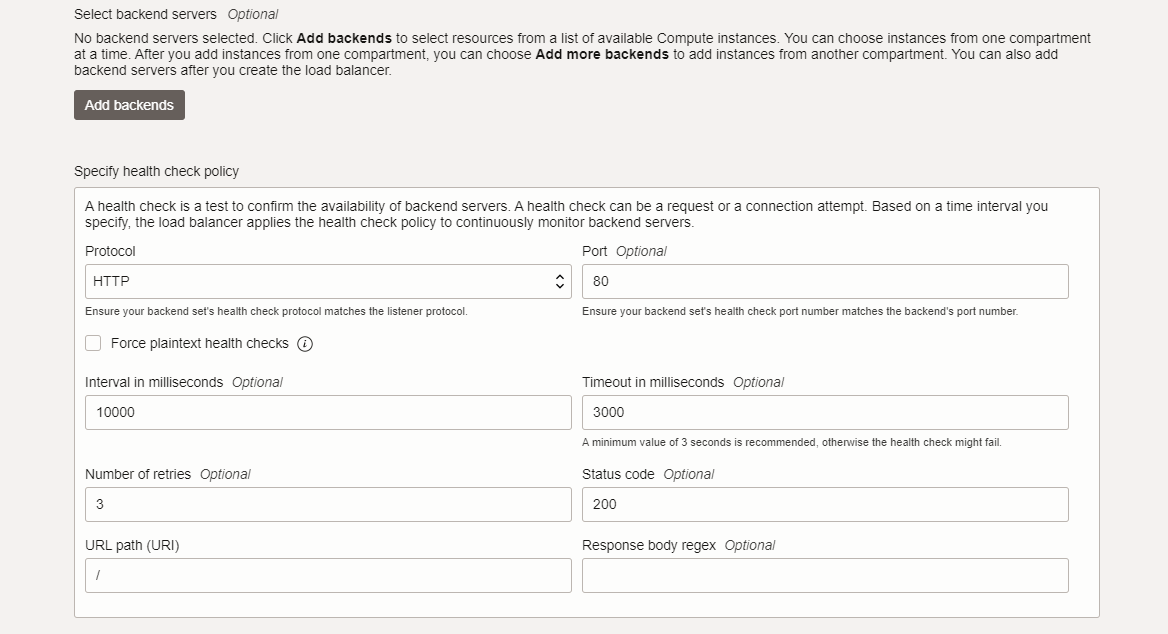
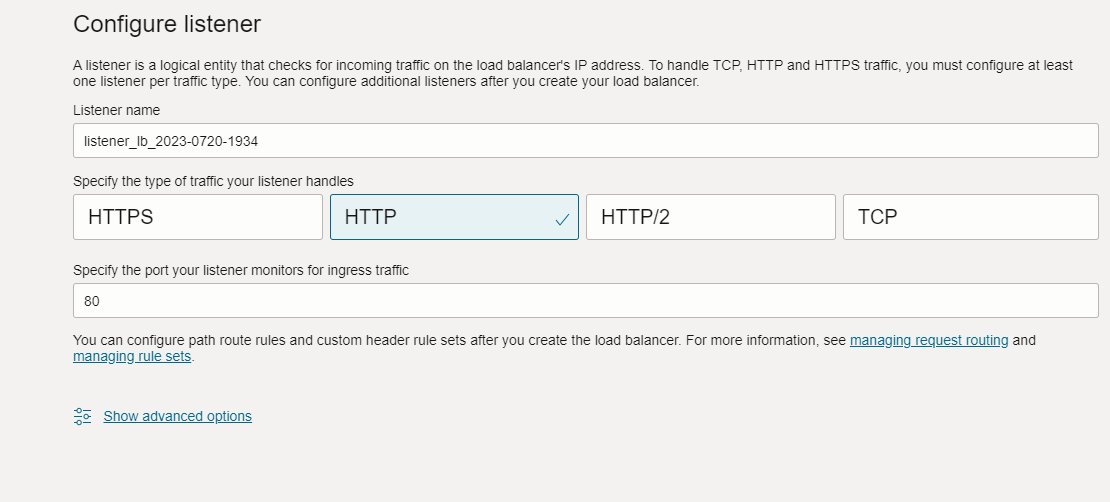
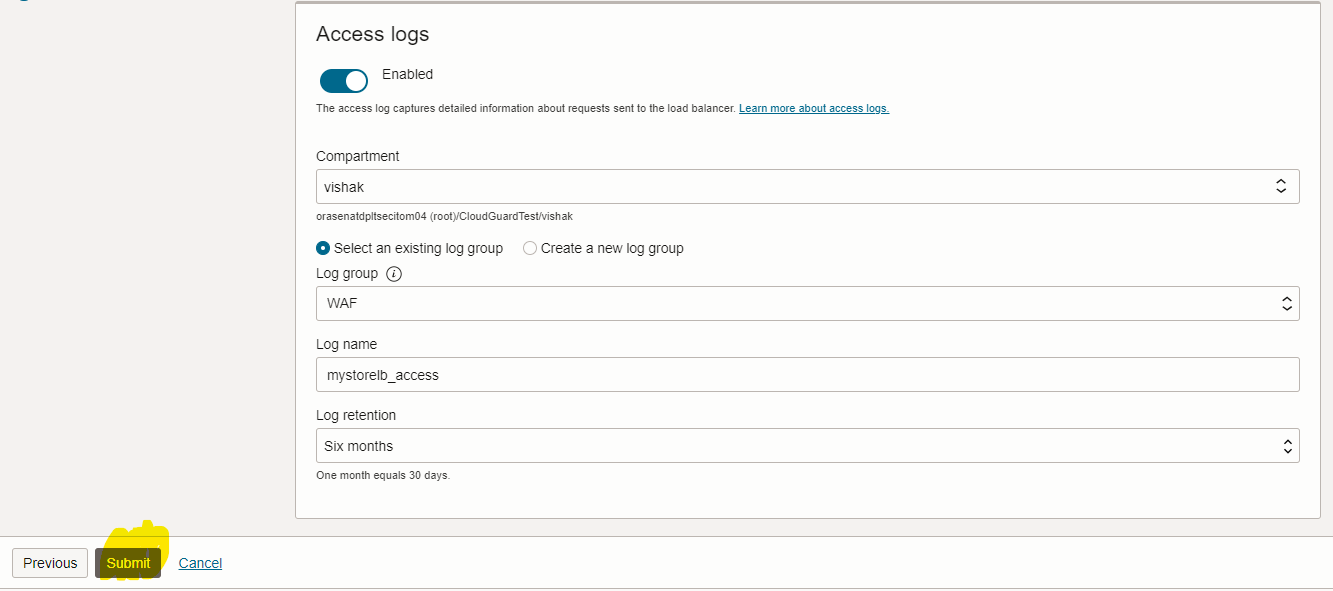
-
Add backends to the Load Balancer which was created in Step 1. Navigate to Backend Sets, Backend Name. Choose the IP addresses button from the backends wizard and add your web application on-premises IP addresses as backends to the Load Balancer.
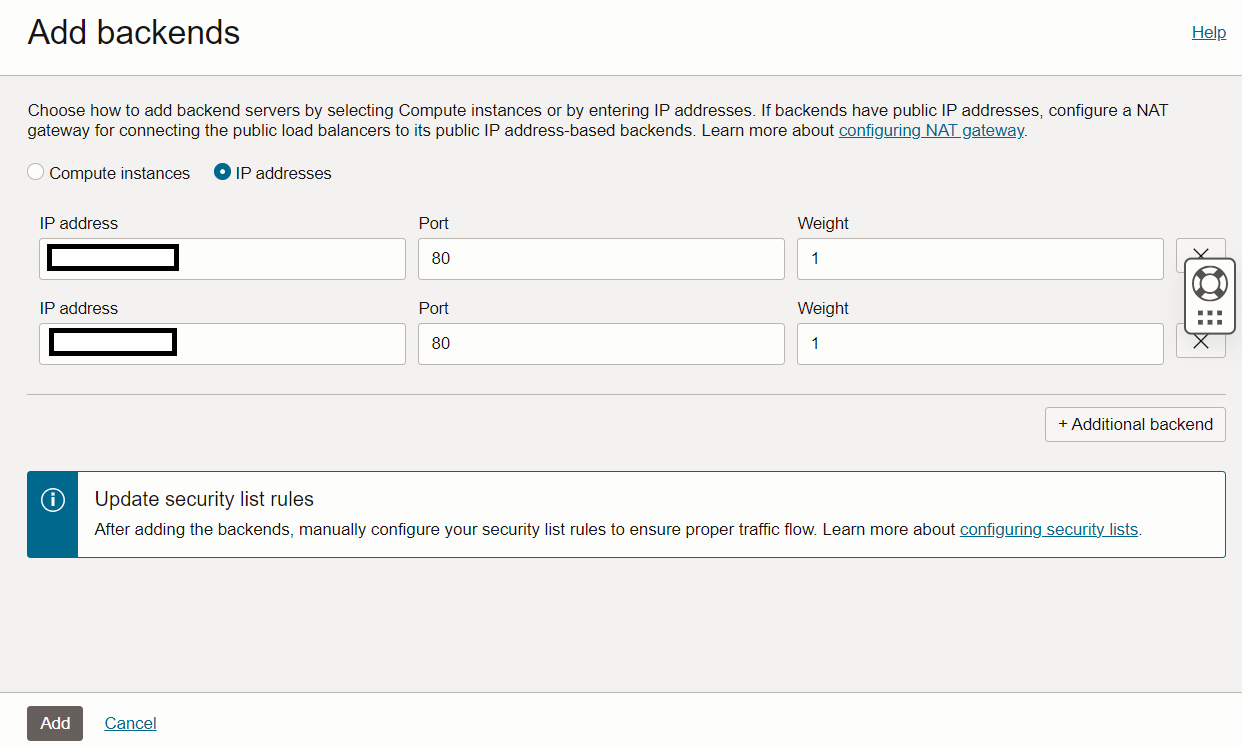
-
Add routes for the on-premises servers with public IPs, pointing them towards the NAT gateway in the Load Balancer subnet’s route tables. This ensures reachability between the public load balancer and its public IP address based backends. Navigate to OCI Console, Networking, Load Balancer, Load Balancer Name, Virtual Cloud Network Name, Route Table Name, Add Route Rules.
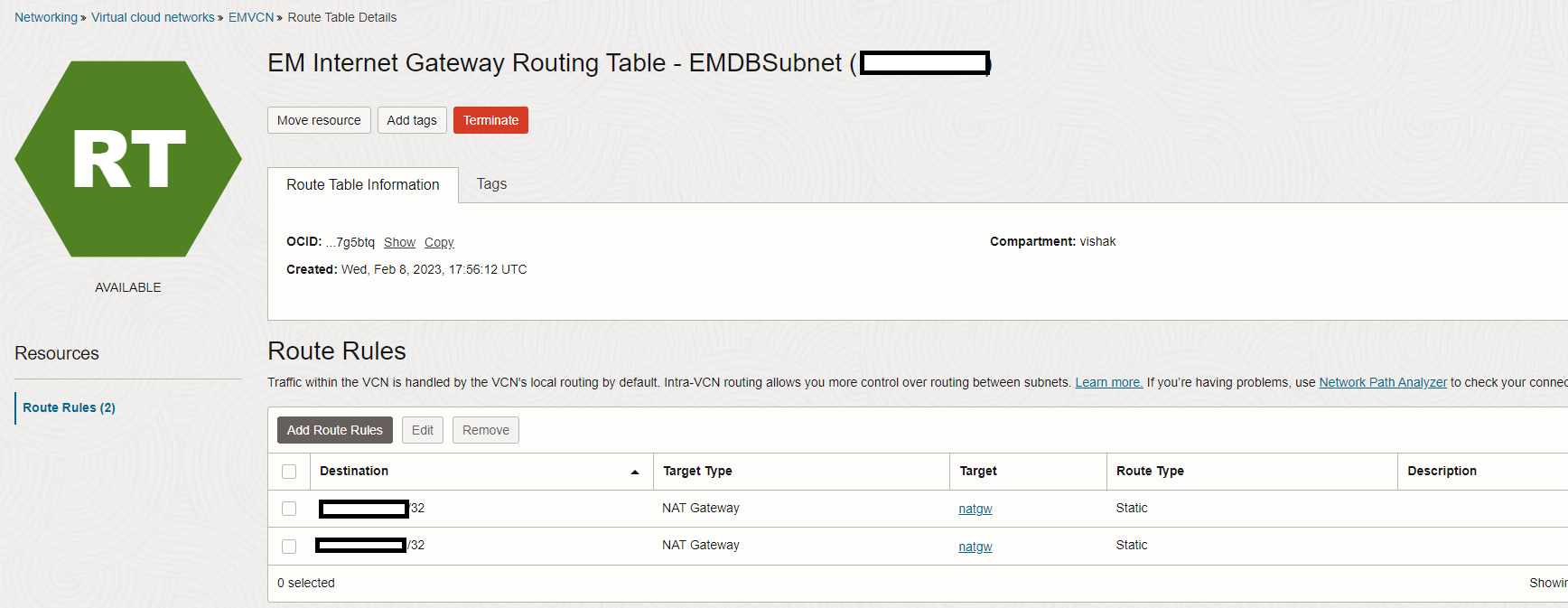
Task 2: Configure OCI WAF
-
Create a WAF policy in the required compartment and add the Load Balancer which was created in Task 1. Navigate to OCI console, Identity & Security, Web Application Firewall, Policies.
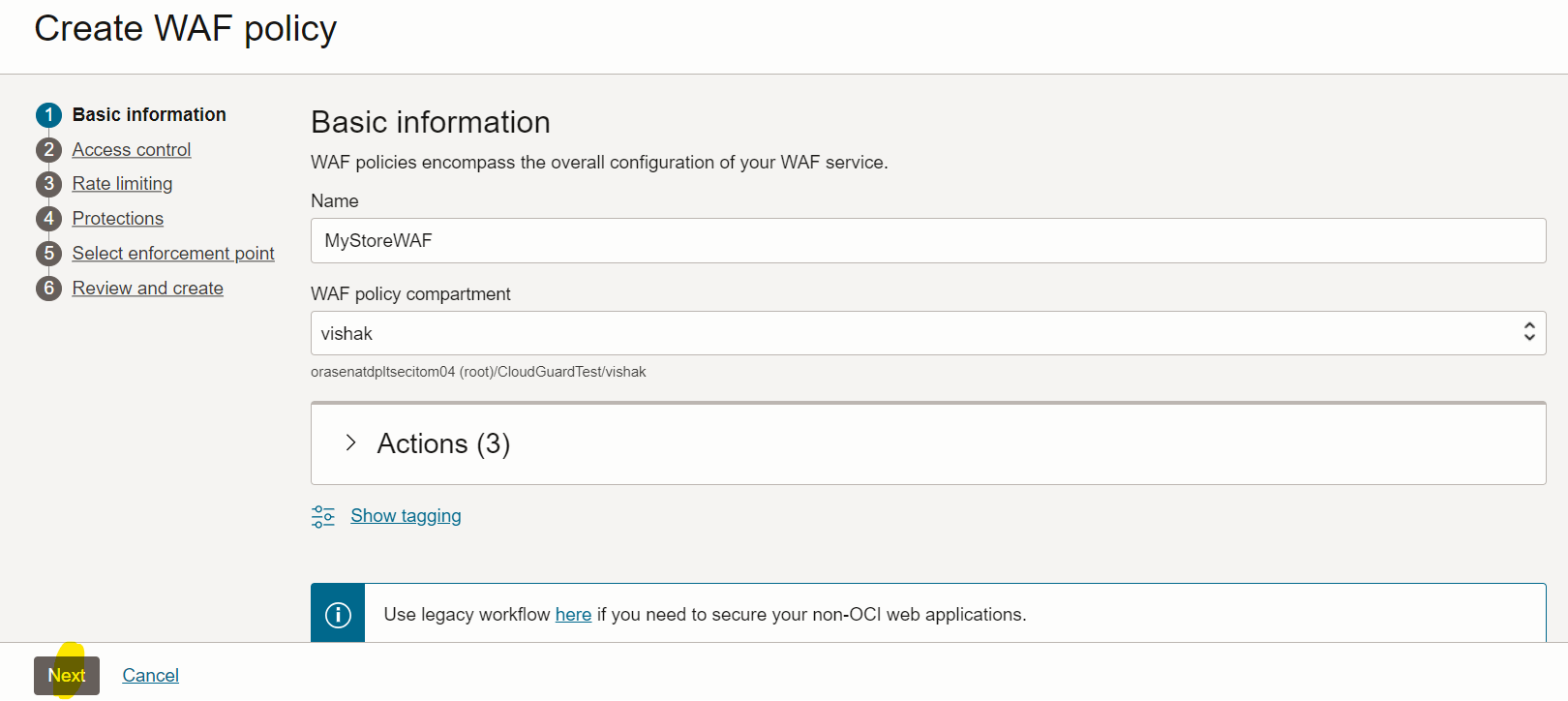
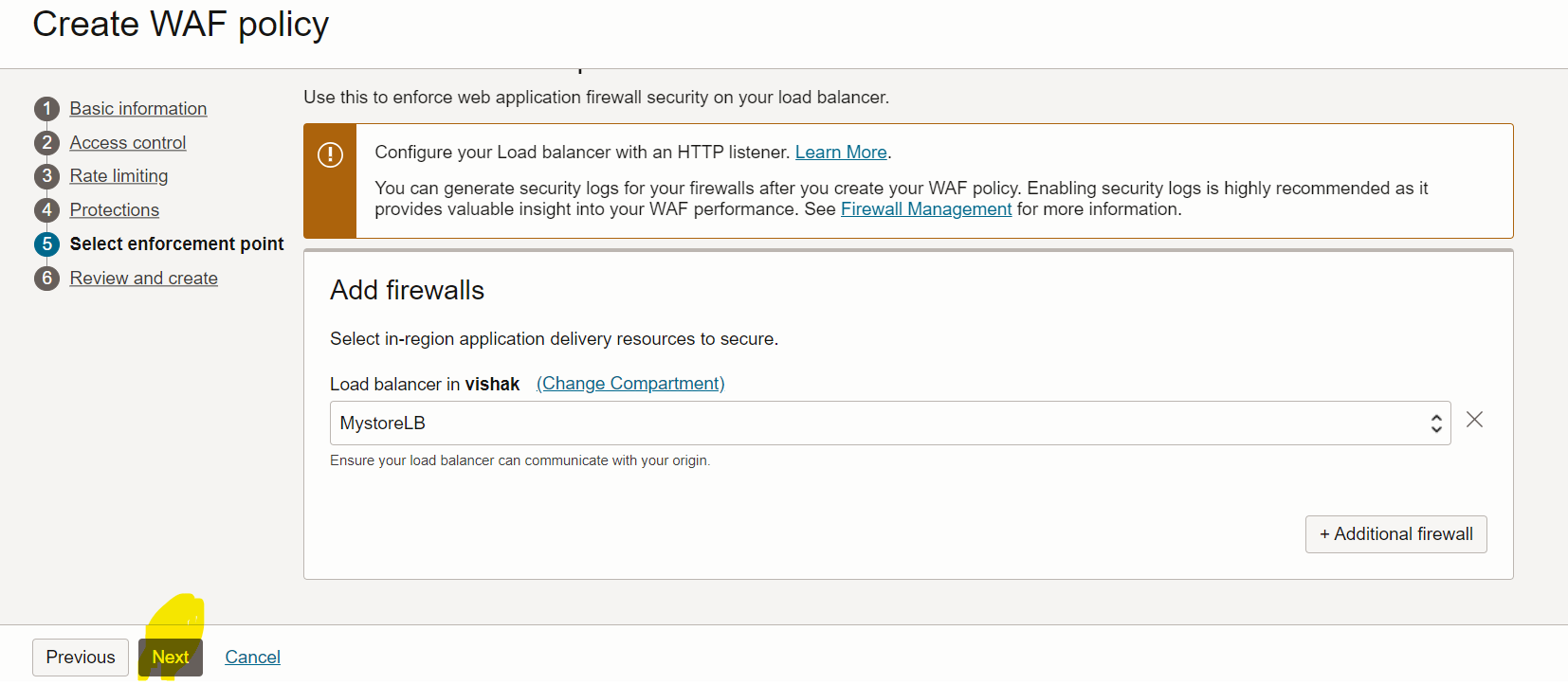
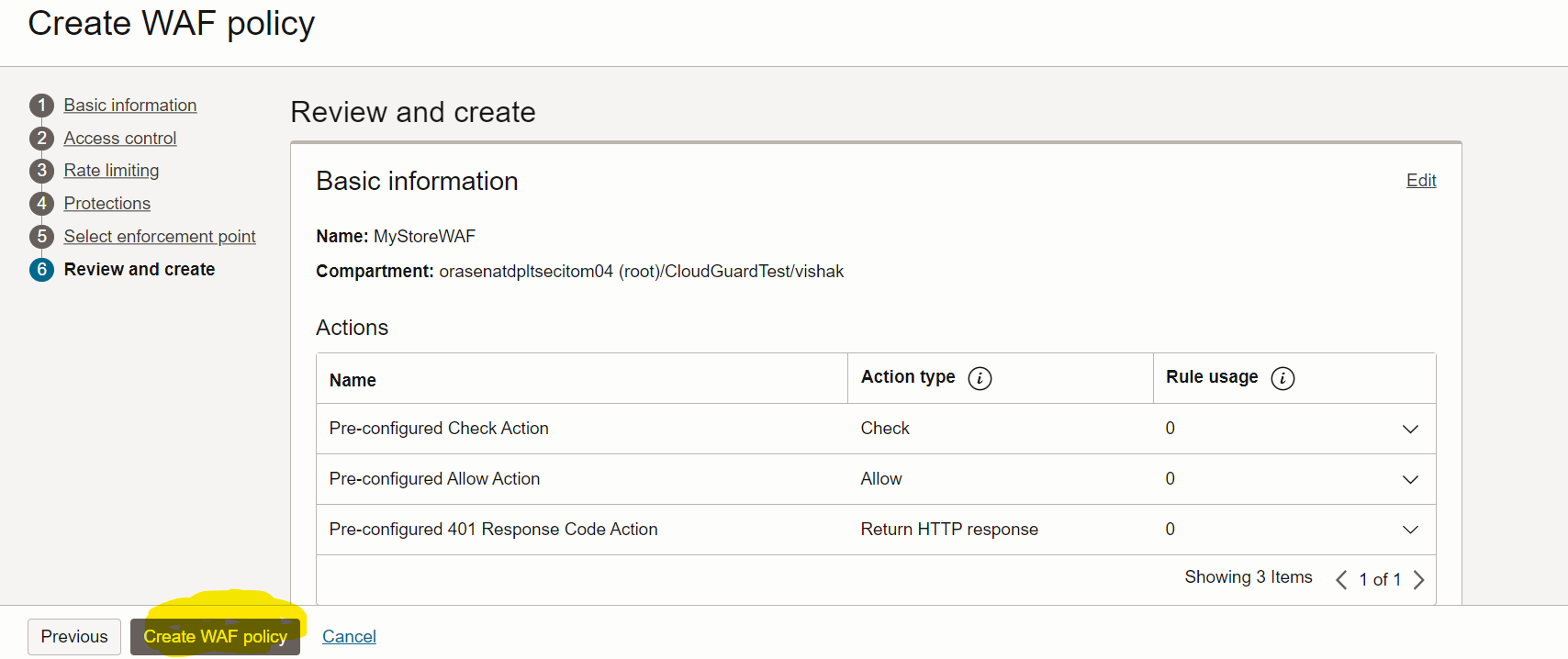
-
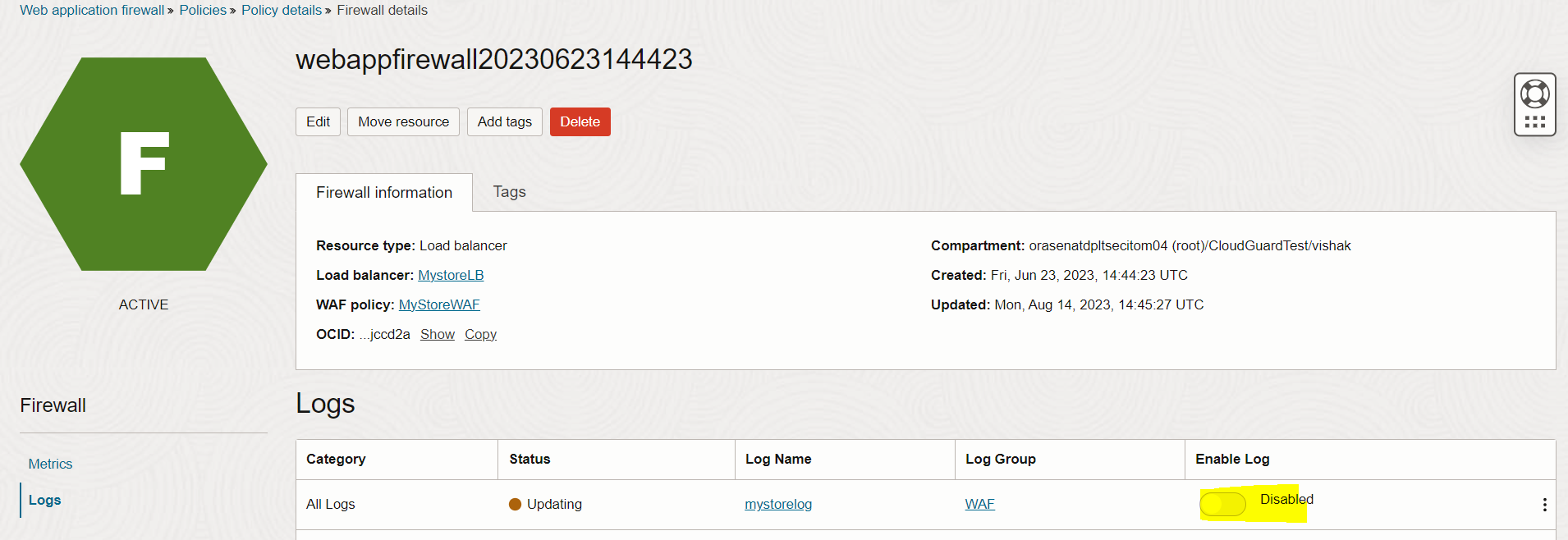
Enable logs for the created WAF policy from OCI console, Identity & Security, Web Application Firewall, Policies, Existing Policy, Firewalls, Firewall name, Logs, Enable Log.
Task 3: Configure Protection Rules in WAF
-
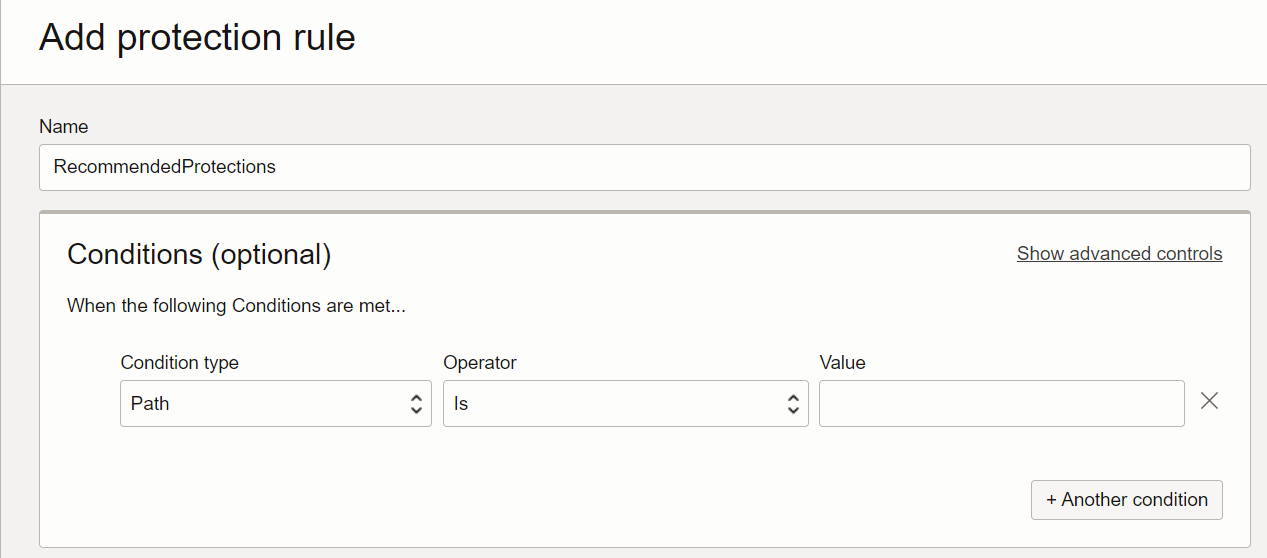
Enable Protection Rules to test Protection of the web application from some OWASP vulnerabilities like SQL script injection, cross-side scripting, and so on. Navigate to Previous WAF policy, Protections, Manage request Protection rules, Add Protection rule.
-
Provide a name for the protection rule and change the action name to 401 response code.
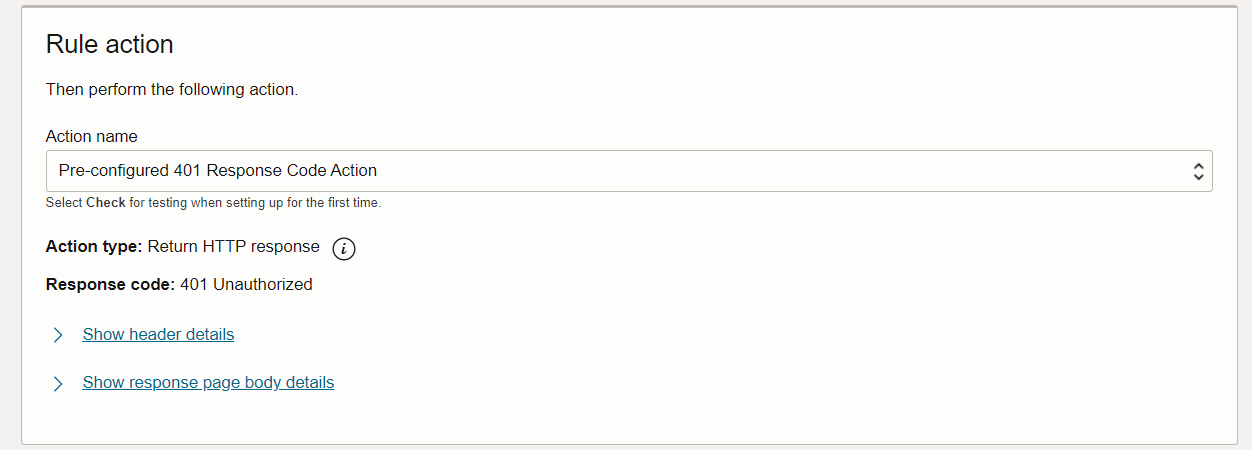
-
Click Choose Protection Rules and filter the Recommended Rules. Select all and apply to add the protection rules.
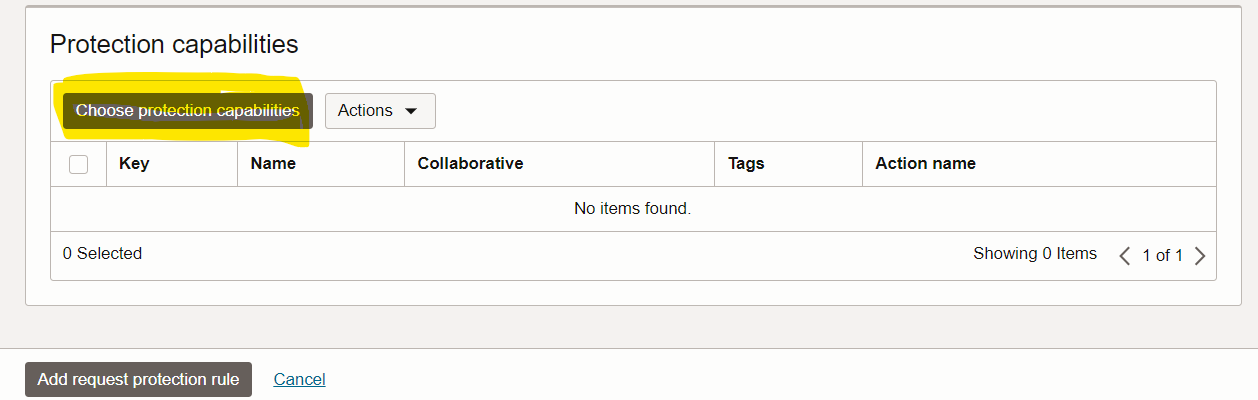
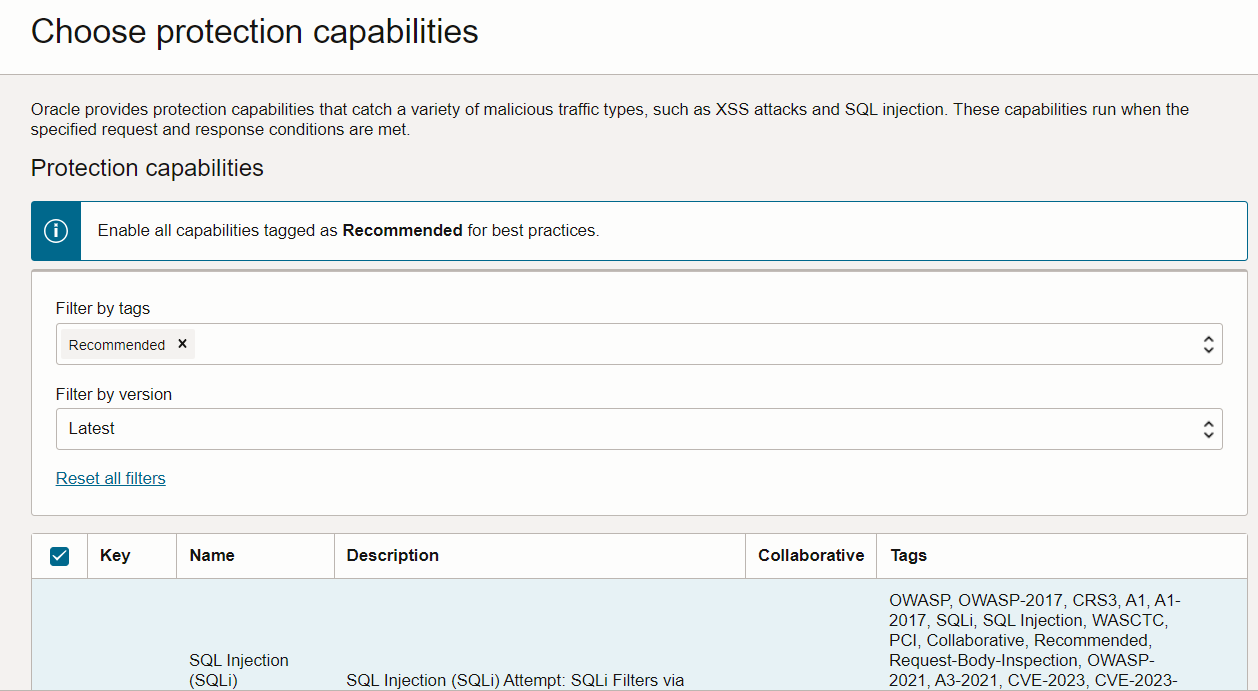
Task 4: Validate the test case for Cross-Site Scripting Attempt
-
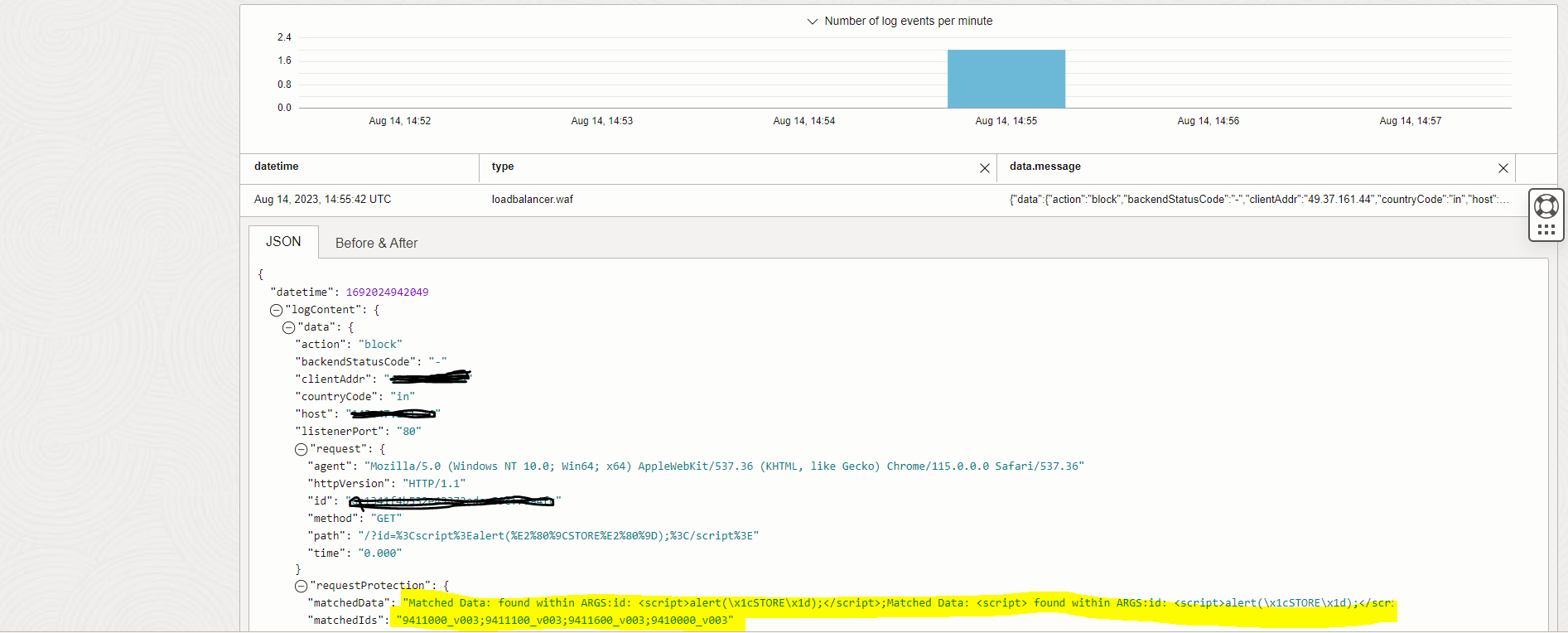
Access the web application with this sample cross-site scripting attempt. Change the app url to your web application url as required. The web application should return an error code by WAF.
< app url>?id=<script>alert(“STORE”);</script>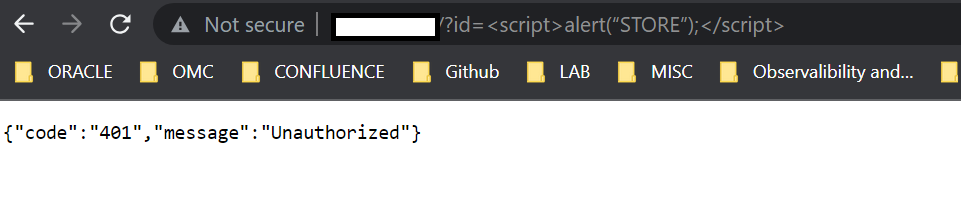
Task 5: Validate actions to the web application
Perform the following steps to validate actions to the web applications are recorded as expected in the logs.
-
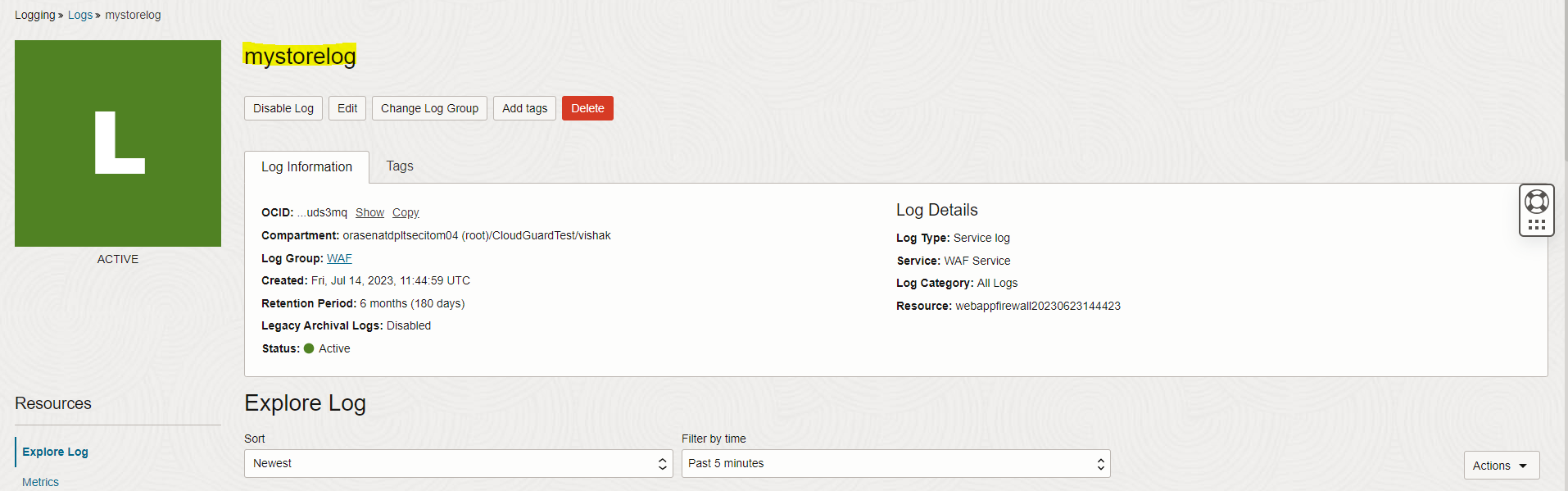
Select the log name which was enabled previously. Navigate to WAF Policy Name, Firewalls, Firewall Name, Logs, Log Name.
Next Steps
The next step involves exploring the features of the Regional Web Application Firewall (WAF) like access control, rate limiting, and so on. Once this exploration is complete, the plan is to engage with Oracle Solution Architects to discuss and develop sophisticated strategies for migrating the web applications to Oracle Cloud Infrastructure (OCI). These strategies will leverage various OCI services such as the Load Balancer, Web Application Firewall (WAF), and Logging services. This collaborative effort aims to ensure a seamless and secure migration process while optimizing the utilization of OCI’s powerful capabilities.
Related Links
Acknowledgments
Authors - Vishak Chittuvalapil (Senior Cloud Engineer), Chaitanya Chintala (Cloud Security Advisor)
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Protect on-premises Web Applications with Oracle Cloud Infrastructure Load Balancer and Regional Web Application Firewall
F86307-01
August 2023
Copyright © 2023, Oracle and/or its affiliates.