Note:
- This tutorial requires access to Oracle Cloud. To sign up for a free account, see Get started with Oracle Cloud Infrastructure Free Tier.
- It uses example values for Oracle Cloud Infrastructure credentials, tenancy, and compartments. When completing your lab, substitute these values with ones specific to your cloud environment.
Enable SAML 2.0 authentication for VMware Horizon with Unified Access Gateway and OCI IAM Identity Domains
Introduction
VMware Horizon helps in the efficient and secure delivery of virtual desktops and apps from on-premises to the cloud. This tutorial walks through configuring Oracle Cloud Infrastructure (OCI) Identity and Access Management (IAM) Identity domains as SAML identity provider (IdP) integration with VMware Unified Access Gateway™ to access VMware Horizon virtual desktops and applications.
This tutorial uses OCI IAM Identity Domains as an IdP. The steps are sequential and build upon one another, so make sure that you complete each step before going to the next step.
Architecture
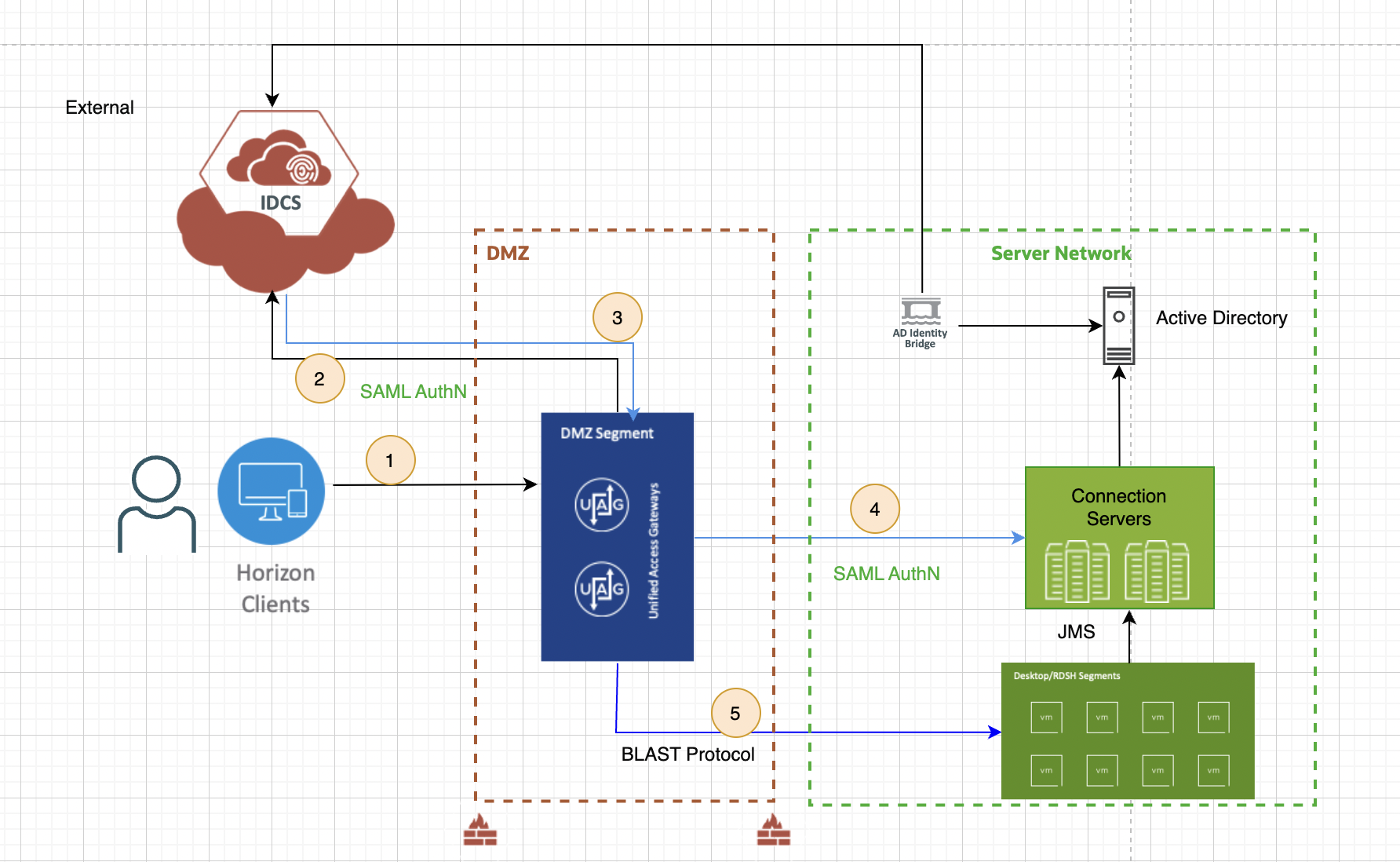
As part of the SAML 2.0 feature, we can launch VMware Horizon desktops and applications using both VMware Horizon client and web client.
Audience
This tutorial is intended for IT professionals and VMware Horizon administrators. Familiarity with networking and storage in a virtual environment is assumed, including Active Directory and Identity solutions. Knowledge of Oracle Cloud VMware Solution is required.
Prerequisites
- Deploy a VMware Horizon 7.11 (or later) Connection Server and configure it with at least one application and desktop pool.
- True SSO configured for VMware Horizon.
- Deploy Unified Access Gateway (UAG) 22.12 and configure the VMware Horizon edge service.
- Install VMware Horizon client on a Windows 10 or MacOS client machine.
- Obtain access to an OCI IAM Identity Domain environment as a Domain Administrator.
Task 1: Configure the Microsoft Active Directory (AD) Bridge for AD Synchronization and Delegated Authentication
Microsoft AD bridge for OCI IAM Identity Domains can be easily configured for synchronizing the directory structure so that any new, updated, or deleted user or group records are transferred into OCI IAM. Once the user profiles are synchronized, users can then use their AD passwords to sign in to IAM for accessing resources and applications protected by OCI IAM. With delegated authentication, Identity domain administrators and security administrators don’t have to synchronize user passwords between AD and OCI IAM.
For more information, see Setting Up a Microsoft Active Directory (AD) Bridge.
Task 2: Configure SAML integration for VMware Unified Access Gateway in OCI IAM Identity Domains
Identity provider metadata is required to enable the integration between OCI IAM and UAG, which enables the flow of communication between the service provider (SP) and IdP during the authentication process. In this section, we configure the SAML 2.0 application in OCI IAM (IdP), to obtain the IdP metadata which is to be used in the Unified Access Gateway (SP) and enable Single sign-on (SSO).
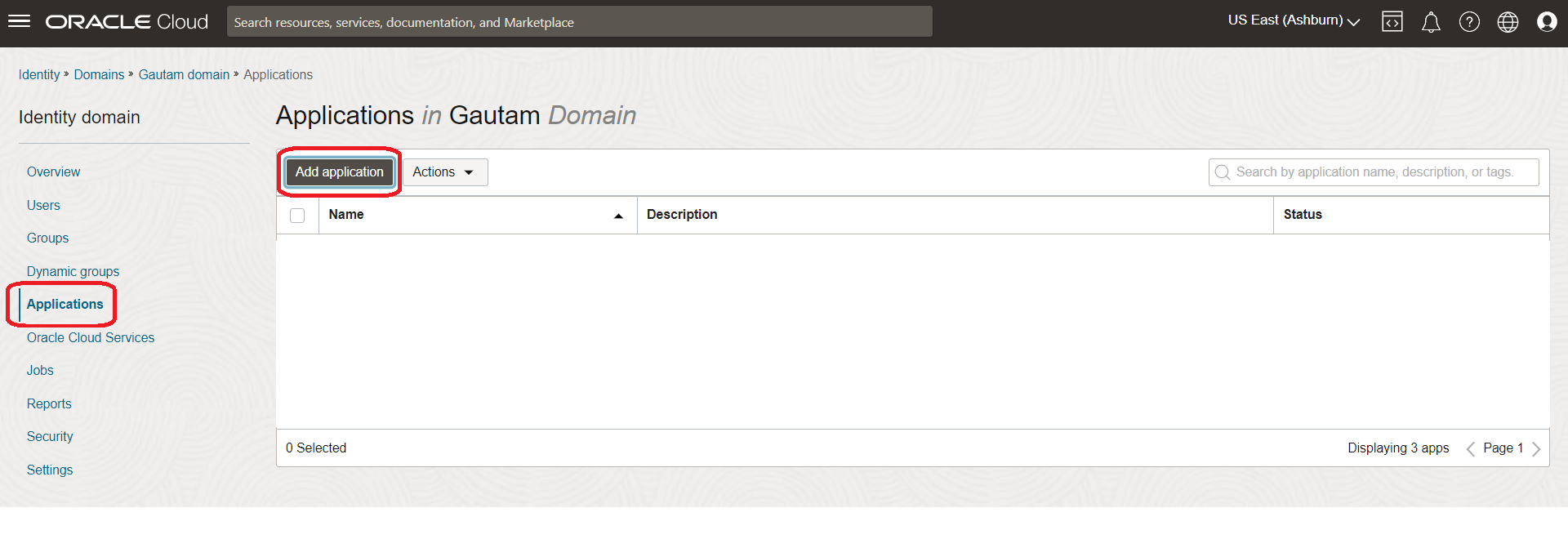
-
Log in to Oracle Cloud, click Applications, and then click Add Application.
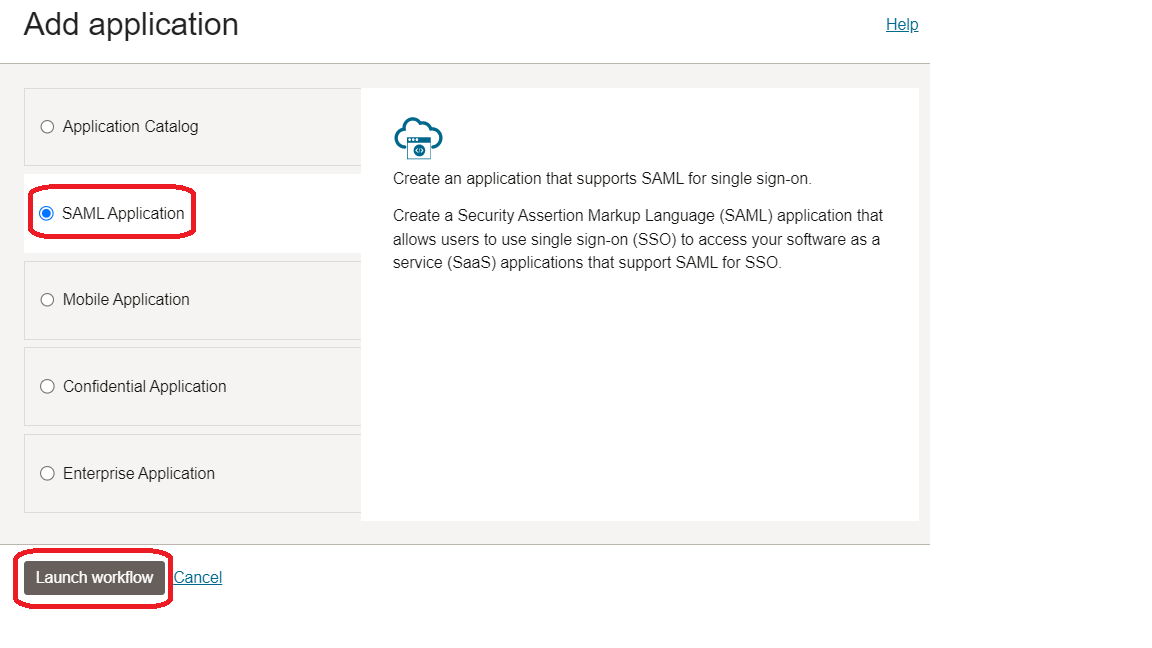
-
Select SAML Application and then click Launch workflow.
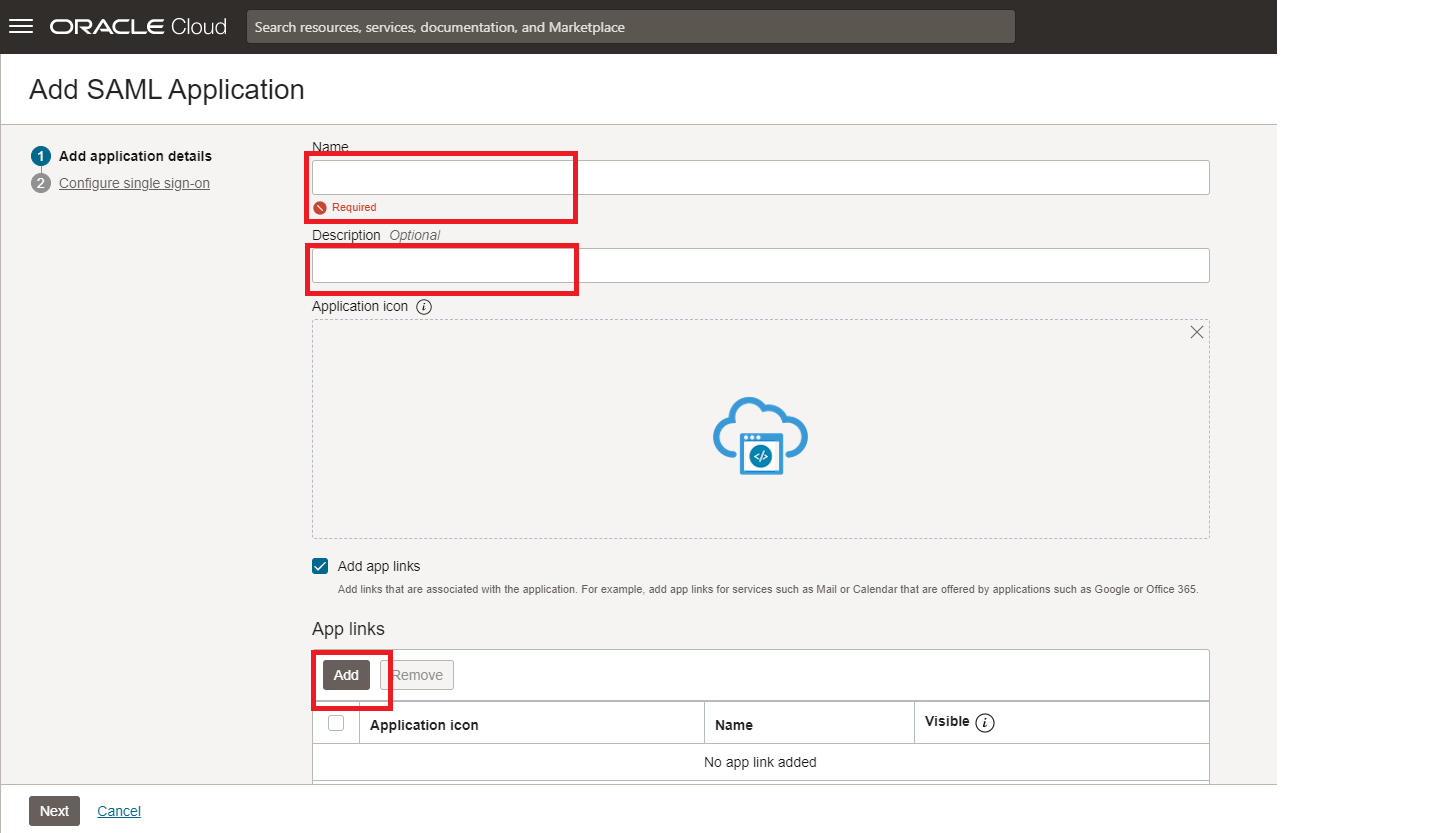
-
Configure the New Application details.
-
Enter
VMware Horizonas the app name. -
(Optional) Define the application in the Description section.
-
(Optional) Provide an App logo if you want in App links section.
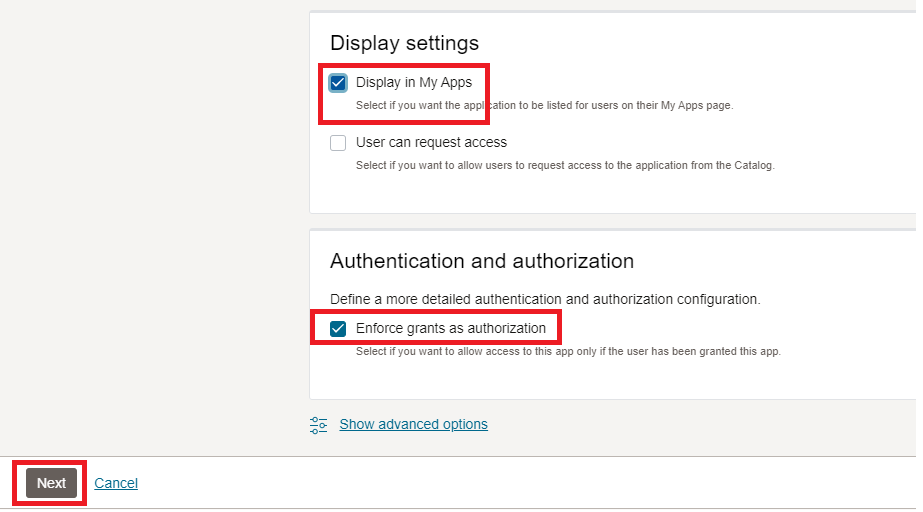
-
Select the Enforce grants as authorization checkbox, if you want to allow access to the application only if the user is authorized.
-
Click Next.
-
-
Configure Single Sign-On Settings: Replace
<UAG-FQDN>from the following parameters with the respective FQDN from your environment. This example usesVMware Horizon.asknikhil.com.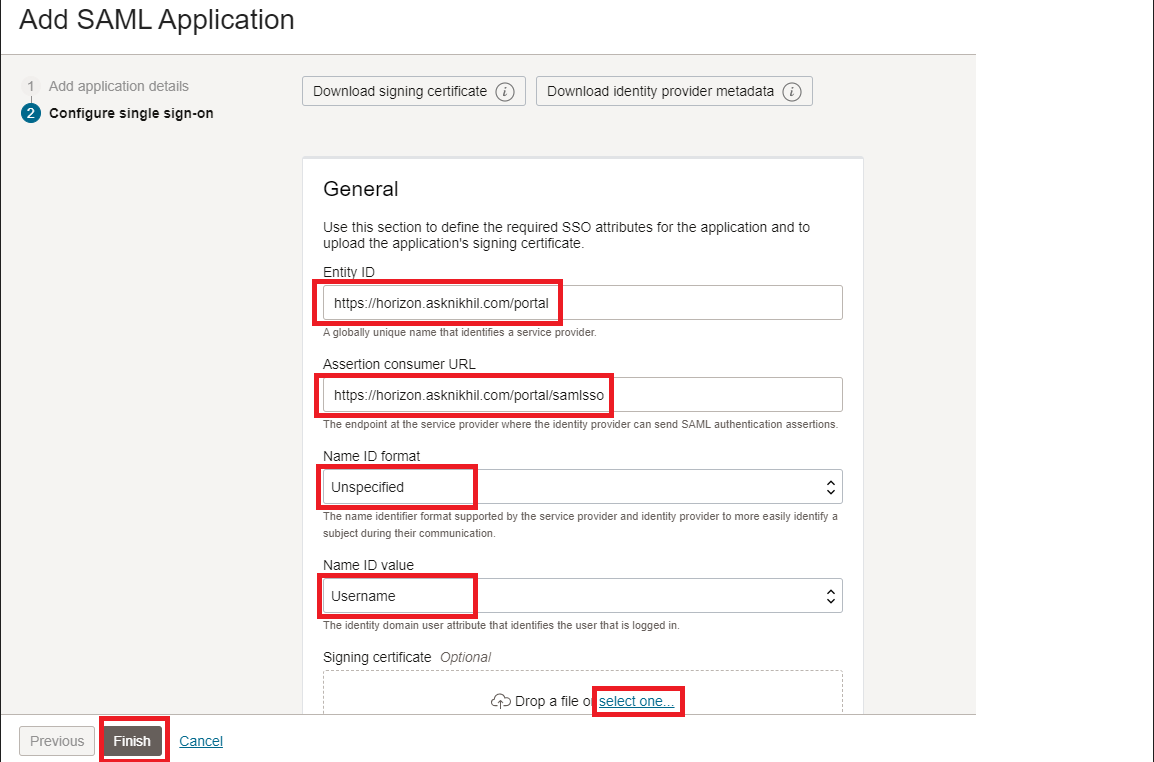
-
Enter
https://<UAG-FQDN>/portalfor Entity ID. -
Enter
https://<UAG-FQDN>/portal/samlssofor Assertion consumer URL. -
Name ID format as Unspecified. Name ID value as Username.
-
Upload the Signing certificate downloaded from UAG console.
-
Keep the default values in the remaining text boxes before scrolling down and then click Finish.
-
-
Activate the application and download the IDP metadata.
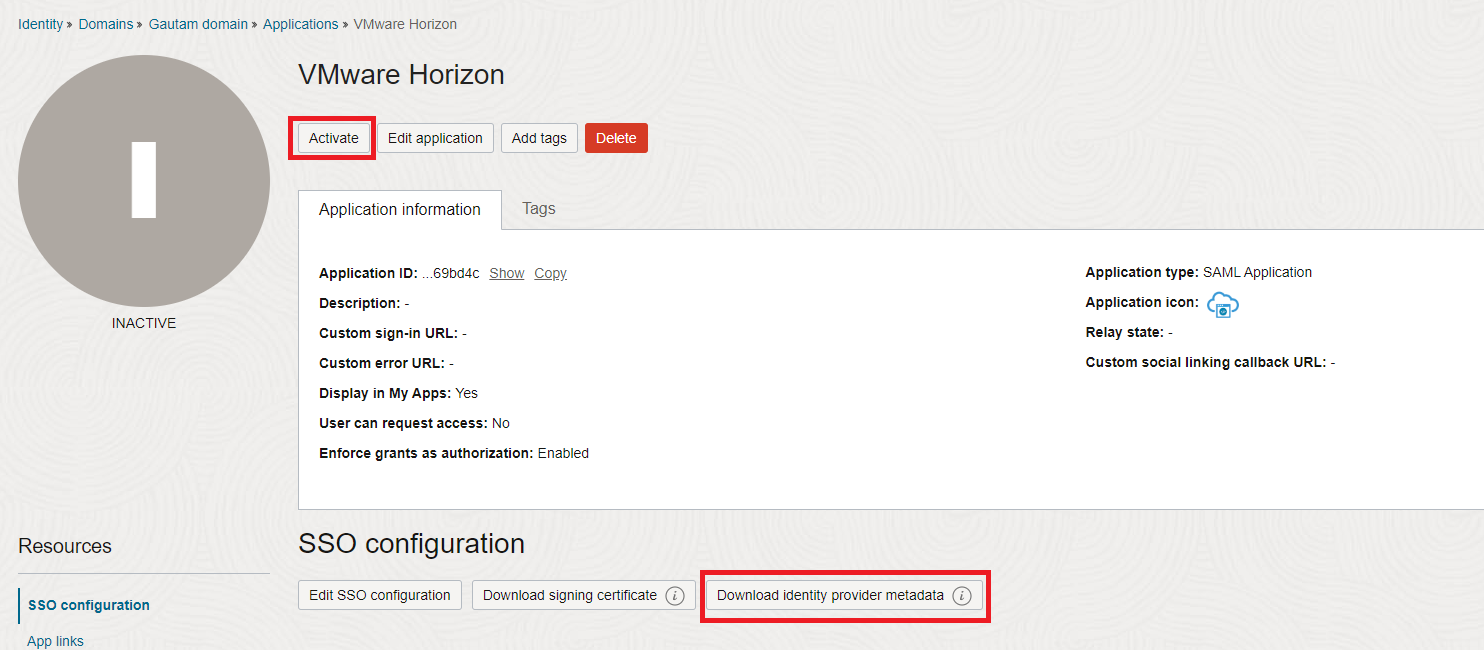
Note: After you configure the SSO settings and click Finish, you get redirected to the application details page where you can Activate the application and then Download the Identity Provider metadata. This metadata will be uploaded to Unified Access Gateway and VMware Horizon Connection Server in later steps.
-
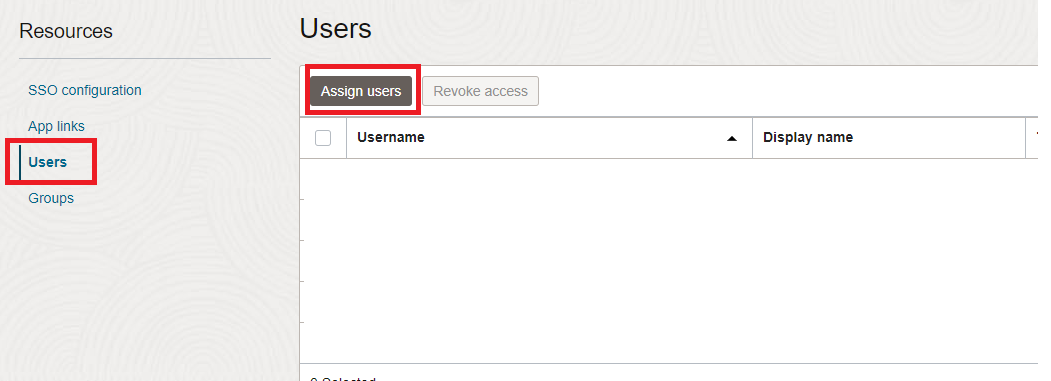
Assign Users or Groups to the application: Assign the users/groups as per the requirement.
Task 3: Configure SAML Integration for VMware Unified Access Gateway in OCI IAM Identity Domains
On Unified Access Gateway, you must enforce SAML authentication and upload OCI IAM metadata to enable third-party SAML 2.0 authentication when launching remote desktops and applications. In this section, we will upload the IdP metadata and configure VMware Horizon edge service for SAML authentication using the Unified Access Gateway administration console.
Upload OCI IAM Identity Domain Metadata to Unified Access Gateway
Here we upload the IDP metadata on UAG to enable trust between the both.
-
Under
Advanced Settingson Unified Access Gateway. Click the gear next toUpload Identity Provider Metadata.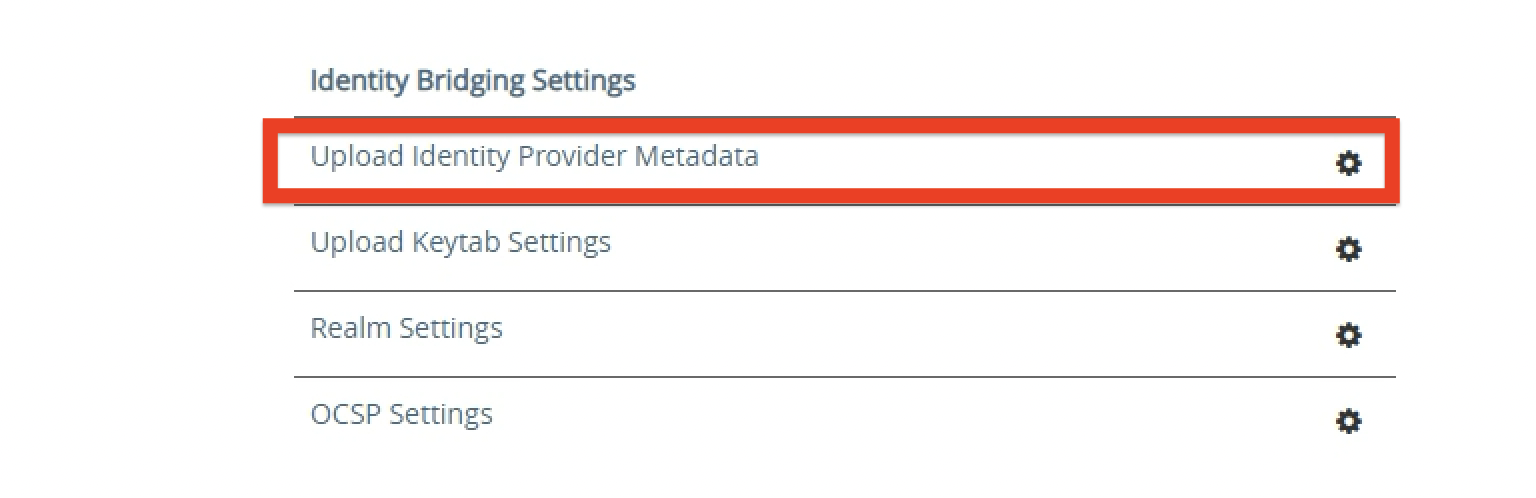
-
Upload IDP Metadata: Keep
Entity IDempty, as this value will be defined based on the metadata XML file.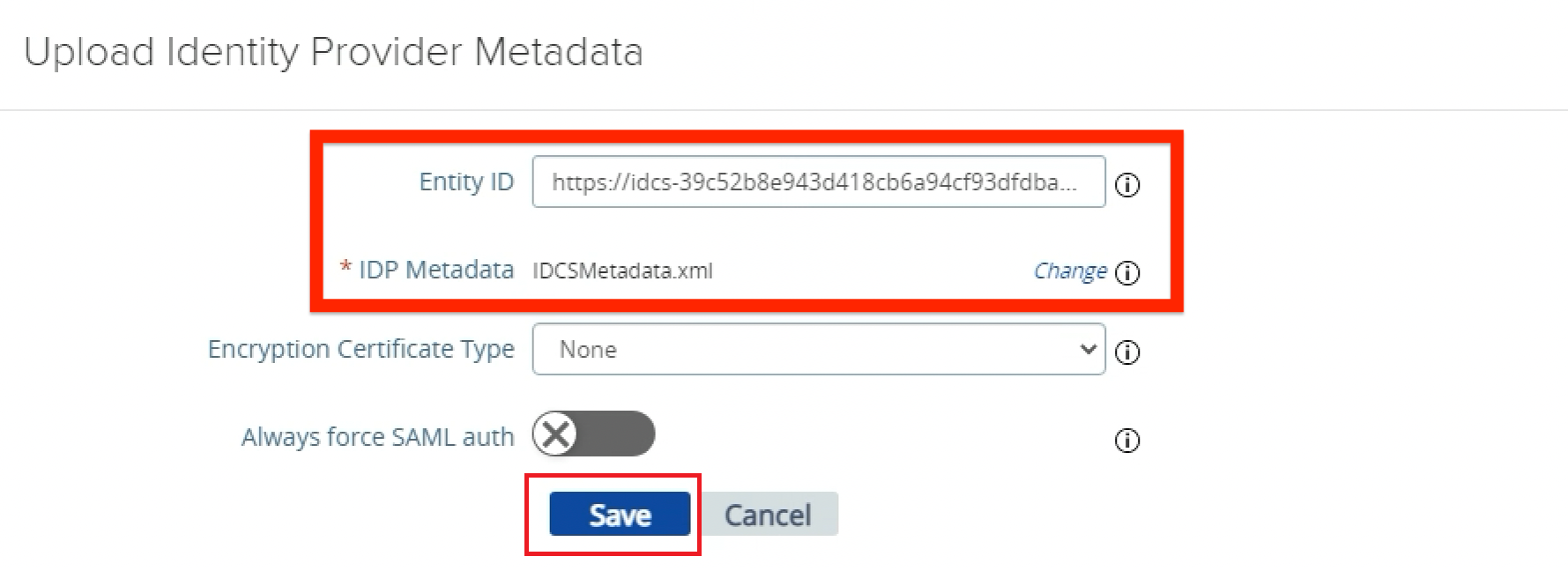
-
Click Select for IDP Metadata and select the XML metadata file previously downloaded from OCI IAM.
-
Click Save.
-
Configure VMware Horizon Edge Service in UAG for SAML authentication
Here we configure SAML as the authentication method for the VMware Horizon service on Unified Access Gateway.
-
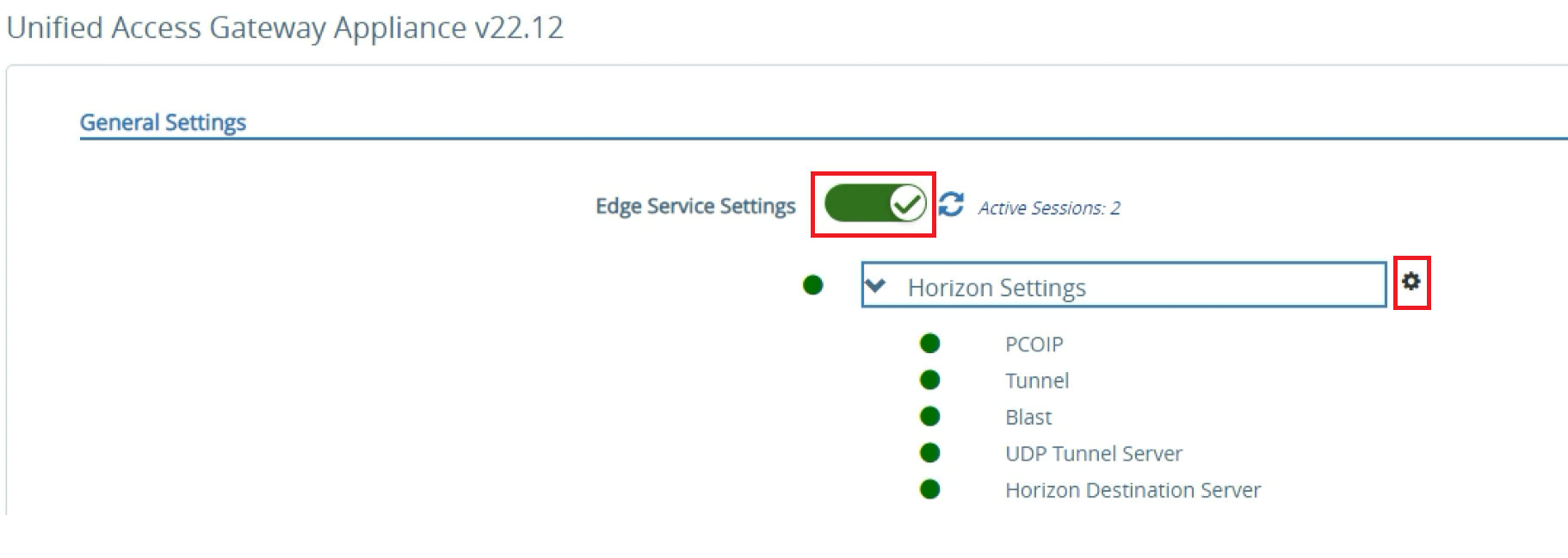
Click Show toggle next to Edge Service Settings.
-
Click the gear icon next to VMware Horizon Settings.
Note: All items should be GREEN, representing that the appliance can communicate with the VMware Horizon Connection Server through the multiple protocols configured. Items not fully functional are presented in RED.
-
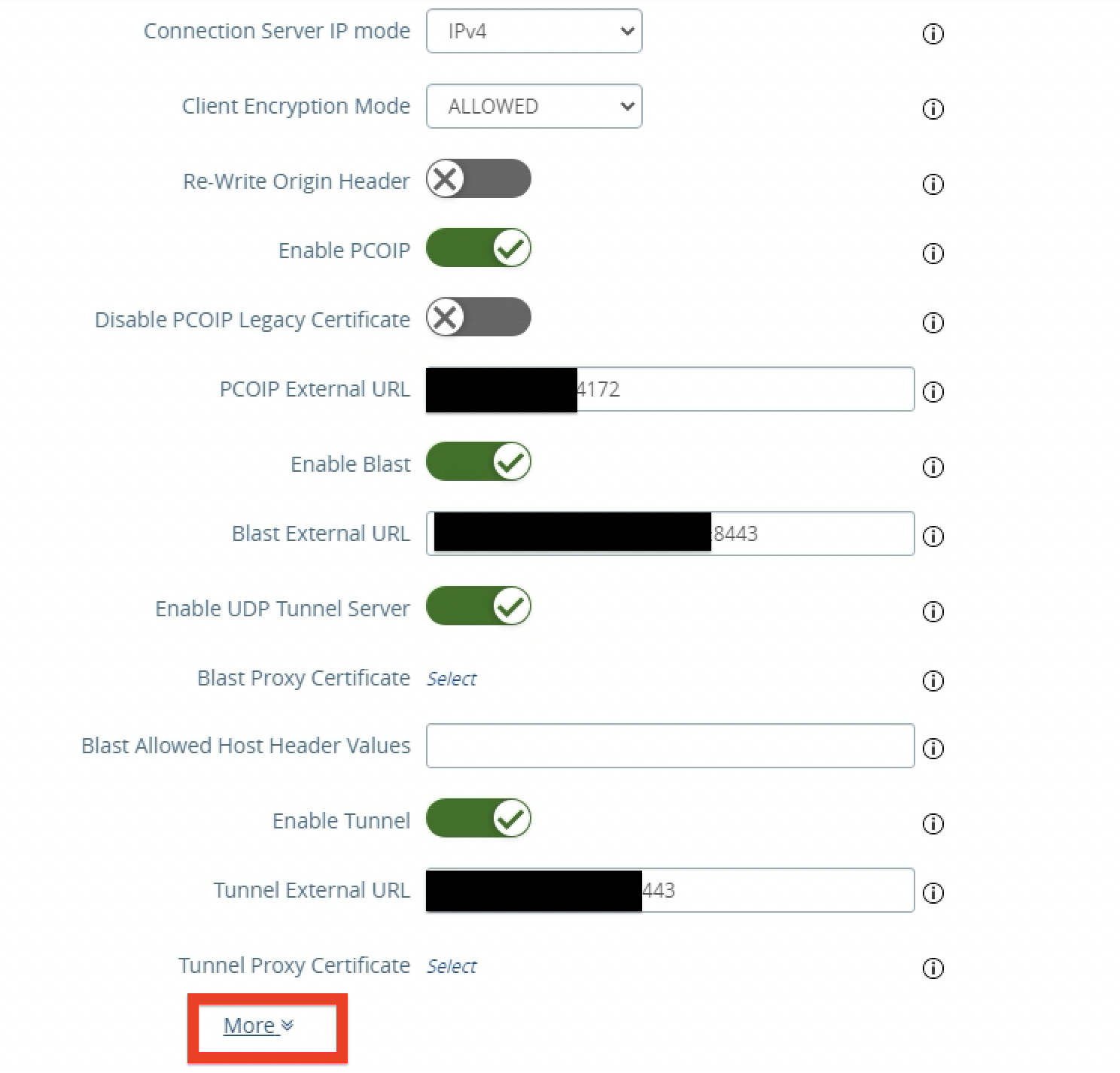
Access Authentication Methods Configuration: Click More at the bottom of the VMware Horizon settings.
-
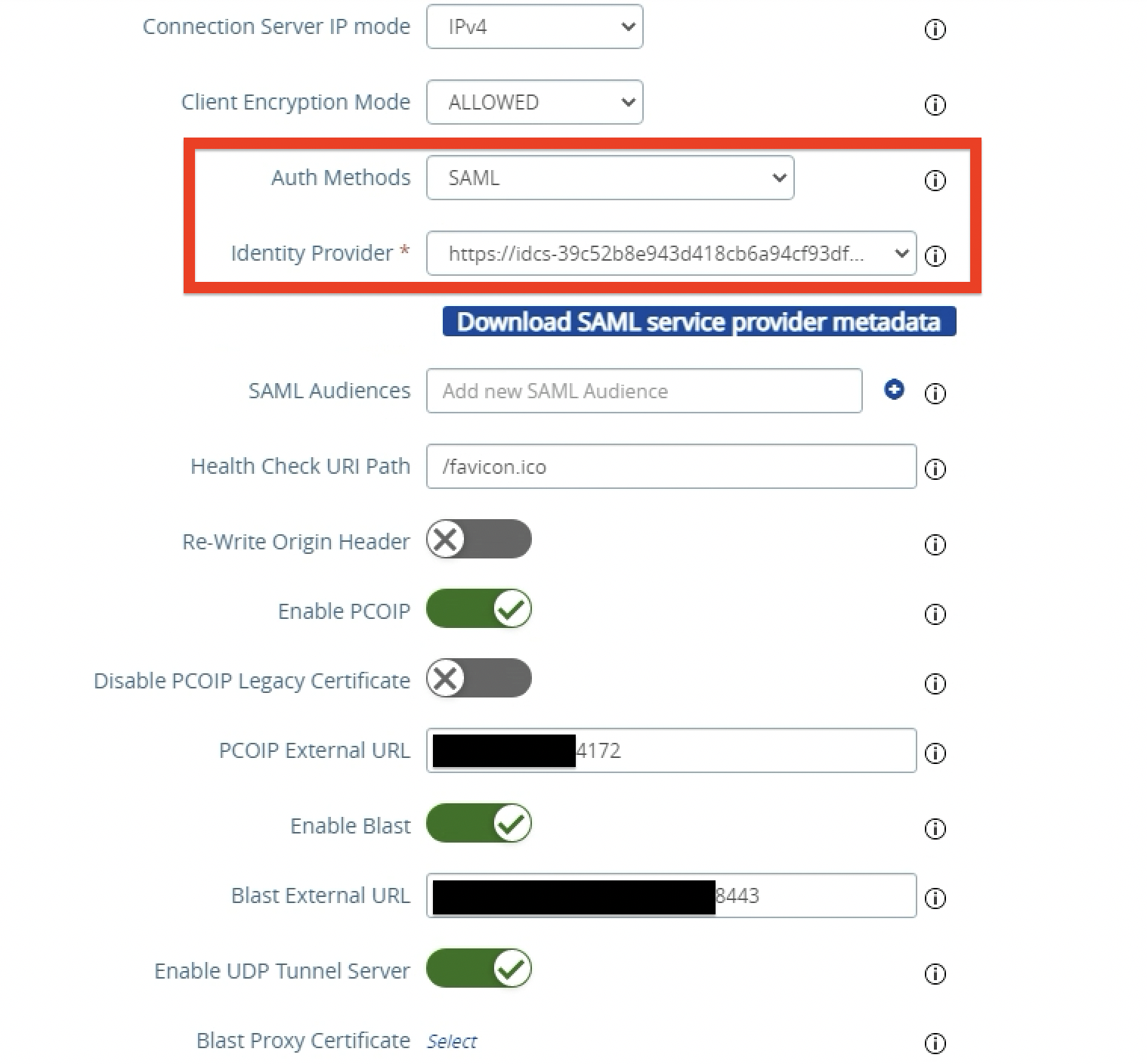
Configure SAML as Authentication Method.
-
Select SAML.
-
Select
https://idcs-#####for Identity Provider.https://idcs-#####is the name of the Entity ID specified in the OCI IAM Identity Domain metadata. -
Scroll down and click Save.
-
Note: When Auth Methods is set to SAML, SAML assertion is validated by Unified Access Gateway and passed to the backend for user single sign-on leveraging True SSO to the remote desktops and applications. When Auth Methods is set to SAML + passthrough, SAML assertion is validated by Unified Access Gateway and Connection Server authenticates the user against Active Directory when launching remote desktops and applications. In both AuthN methods user will be redirect to OCI IAM for SAML authentication, and service provider (SP) and IdP initiated flows are supported.
Task 4: Configure VMware Horizon Integration with OCI IAM Identity Domain for SAML and True SSO
To provide an end-to-end SSO experience to the end-user, we must configure True SSO on our VMware Horizon environment. When True SSO is enabled, users are not required to enter Active Directory credentials in order to use a remote desktop or applications.
When Unified Access Gateway is setup to use third-party IdP and True SSO is enabled on VMware Horizon, we must create a SAML authenticator into the VMware Horizon administration console to provide the same end-to-end single sign-on experience, otherwise the end-user will have to enter their AD credentials for log in to the desktop or application. A SAML authenticator contains the IdP trust and metadata exchange between VMware Horizon and the device to which clients connect.
In this section, we create a SAML authenticator for OCI IAM Identity Domain on the VMware Horizon administration console, and enable True SSO for the OCI IAM SAML authenticator created.
Note: We associate a SAML authenticator with a Connection Server instance. If the deployment includes more than one Connection Server instance, you must configure the SAML authenticator with each instance.
Configure the SAML Authenticator for True SSO
Here we configure OCI IAM Identity Domain as the SAML authenticator for VMware Horizon.
-
To access the VMware Horizon administration console, navigate to
https://server/adminin your Web browser, where server is the host name of the Connection Server instance.
-
Enter the User Name.
-
Enter the Password.
-
Enter the Domain.
-
Click Sign in.
-
-
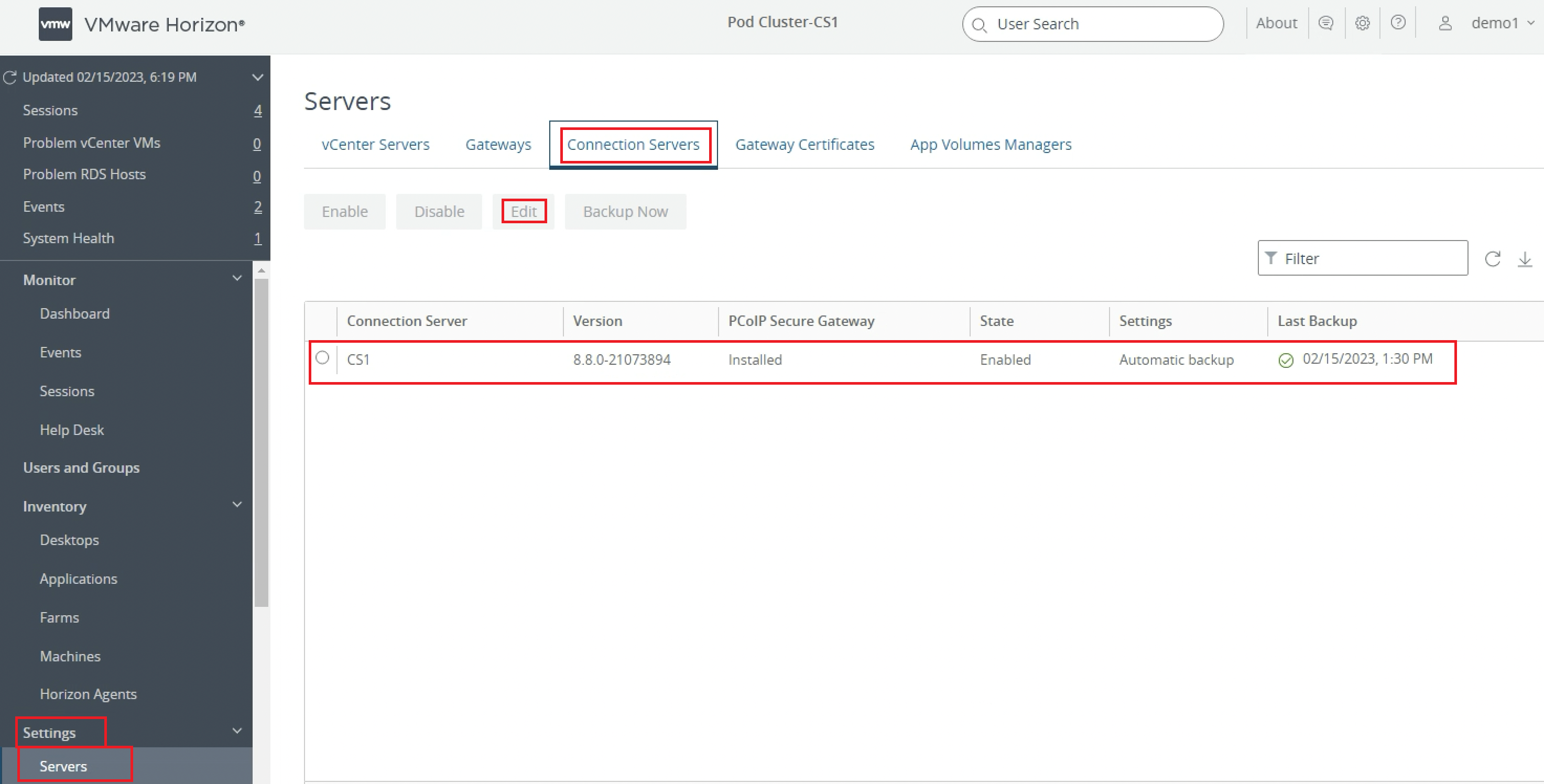
Configure Connection Server Settings.
-
Click Settings.
-
Click Servers.
-
Select Connection Servers and then select the Connection Server to be used as the front-end server for Unified Access Gateway.
-
Click Edit.
-
-
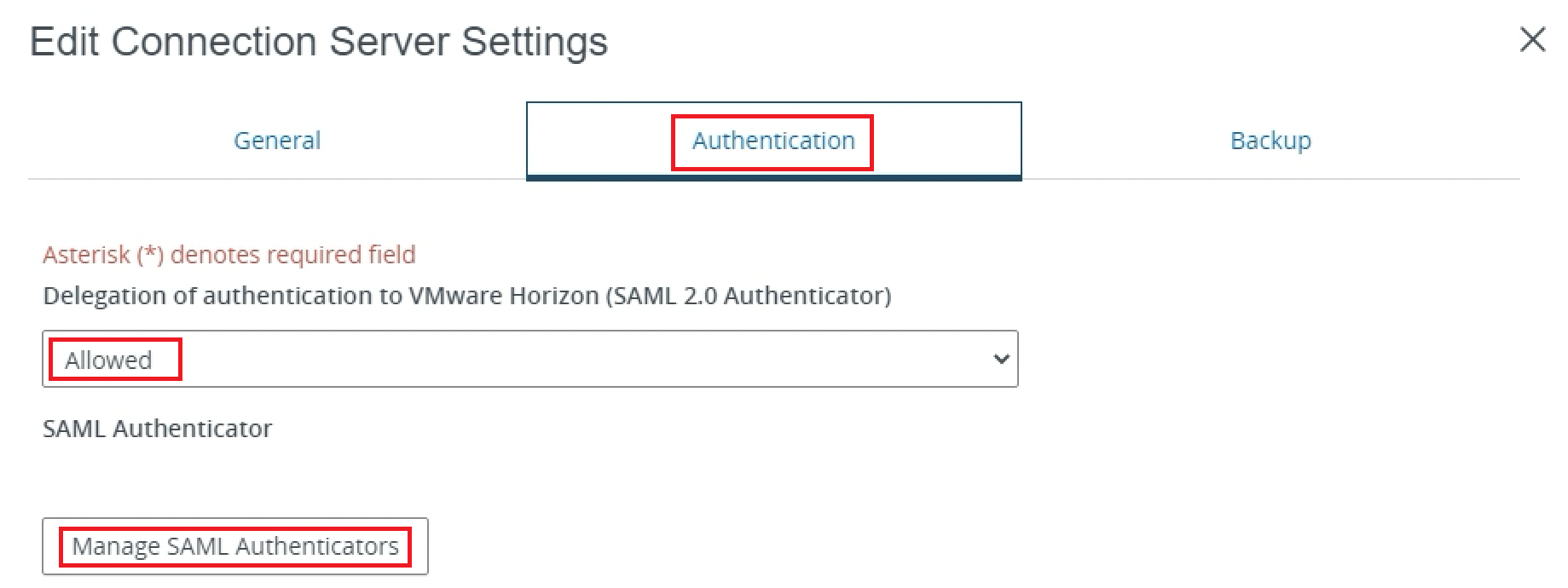
Configure SAML Authentication Settings.
-
Select the Authentication tab.
-
Select Allowed for Delegation of authentication to VMware Horizon (SAML 2.0 Authenticator).
-
Click Manage SAML Authenticators.
-
-
Click Add.
-
Configure SAML Authenticator for OCI IAM Identity Domain.
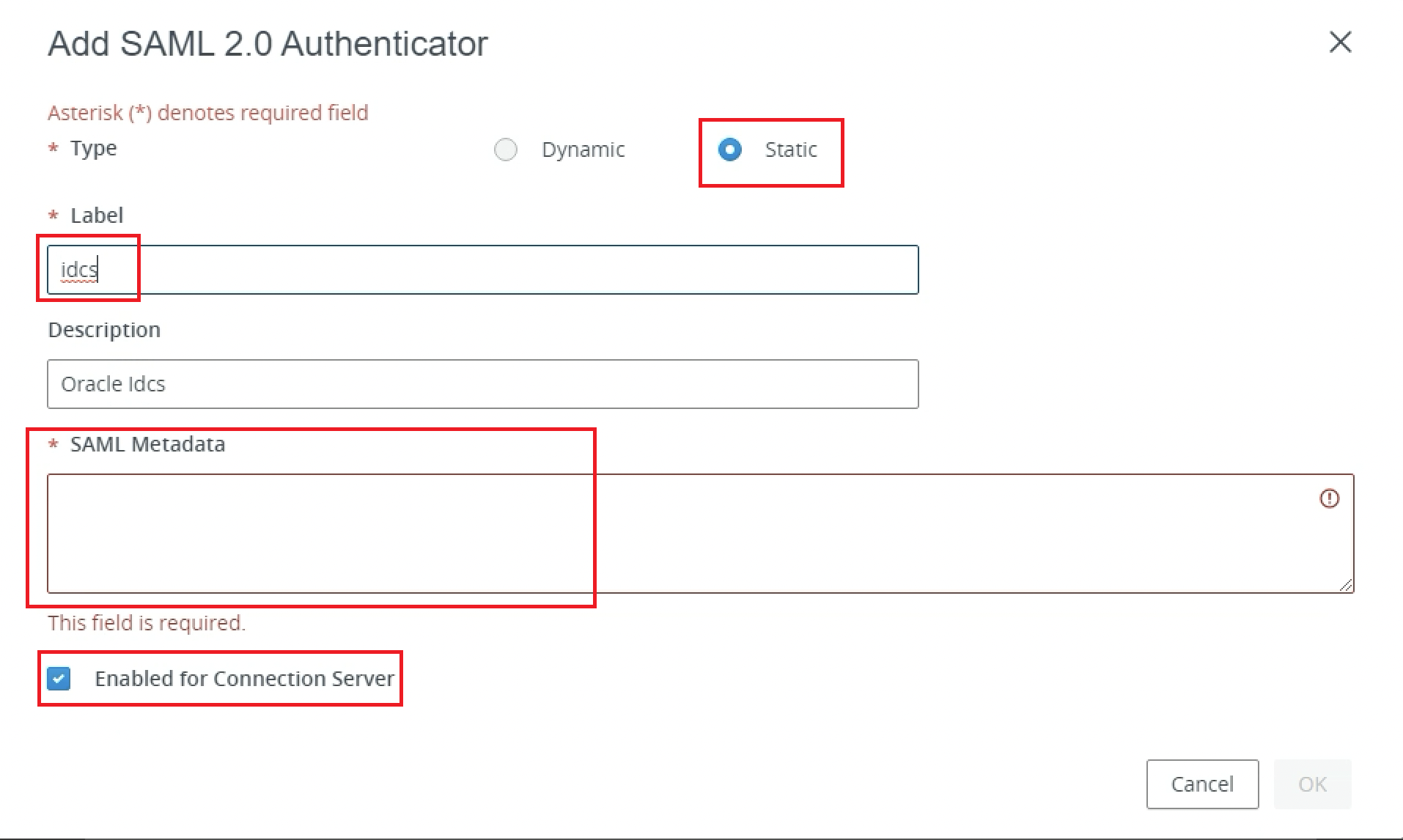
-
Select Static for Type.
-
Enter
idcsfor Label. -
Paste the content of the OCI IAM Identity Domain metadata XML file we previously downloaded from OCI IAM into the SAML Metadata text box.
-
Make sure Enabled for Connection Server is selected.
-
Click OK.
-
-
Confirm the SAML Authenticator is Enabled.
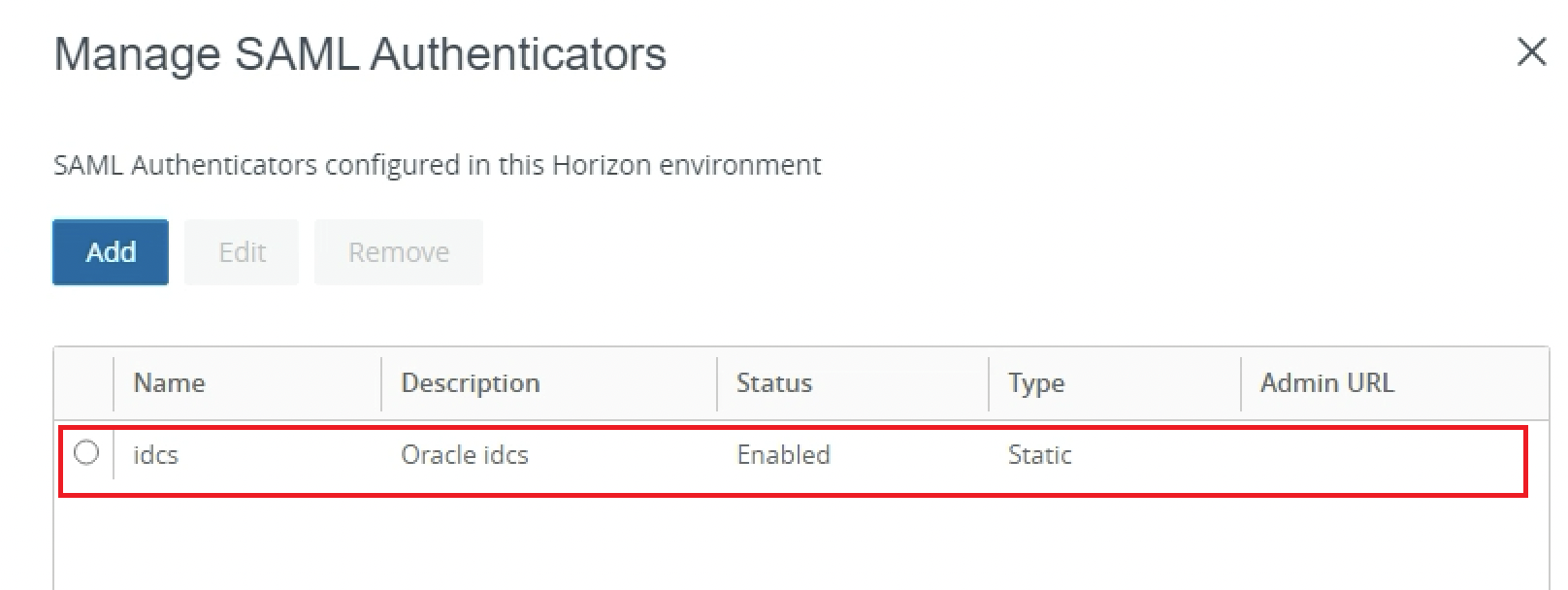
-
Confirm that OCI IAM is now configured as a SAML authenticator for VMware Horizon.
-
Click OK.
Note: We can configure more than one SAML authenticator to a Connection Server and all the authenticators can be active simultaneously. However, the entity-ID of each SAML authenticator configured on the Connection Server must be different.
-
-
Enable True SSO for Third-party SAML Authenticator
-
If the environment leverages VMware Horizon TrueSSO, we must enable the OCI IAM SAML Authenticator on True SSO. Use the following command line to list all the authenticators and their True SSO mode status.
vdmutil --authAs <VMware Horizon admin user> --authDomain <fqdn> --authPassword <VMware Horizon admin password> --truesso --list --authenticatorReplace
<VMware Horizon admin user>with the VMware Horizon administrator user<fqdn>with the fully qualified domain name for the VMware Horizon admin user<VMware Horizon admin password>with the password for the VMware Horizon administrator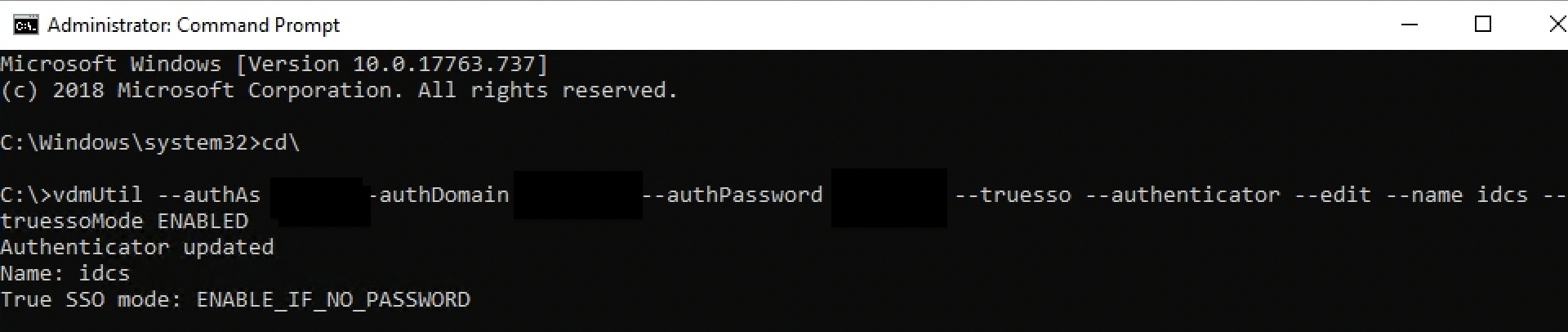
-
If True SSO mode is
DISABLEDfor the authenticator we are trying to configure, execute the following command line to enable.vdmutil --authAs <VMware Horizon admin user> --authDomain <fqdn> --authPassword <VMware Horizon admin password> --truesso --authenticator --edit --name <SAML authenticator name> --truessoMode ENABLED -
After we enable True SSO, the
True SSO modefor the authenticator, we are enabling displays as:ENABLE_IF_NO_PASSWORD
-
Task 5: Validate Desktop and Application through SAML and True SSO authentication
Here we launch the VMware Horizon Client to launch remote desktops and applications through Unified Access Gateway, and validate the SAML and True SSO authentication flow.
-
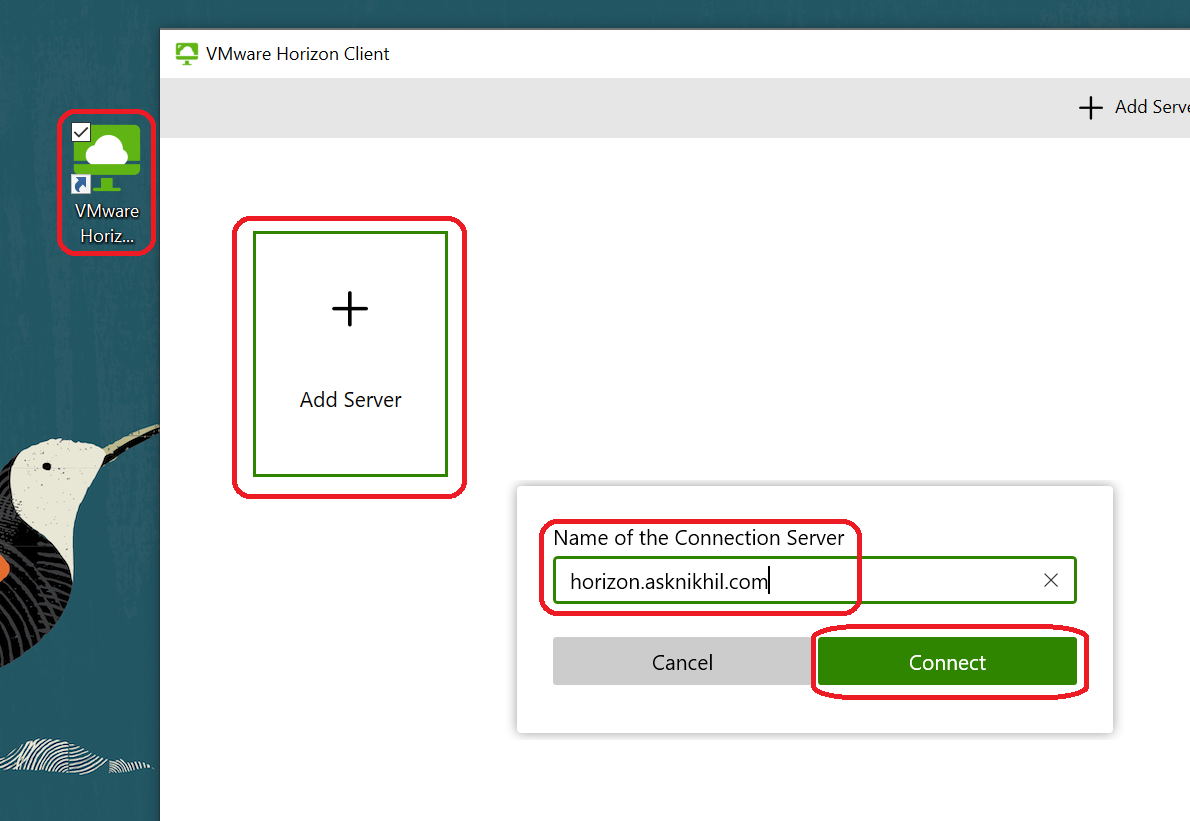
Configure VMware Horizon Client.
-
Launch VMware Horizon Client.
-
Click Add Server.
-
Enter the Unified Access Gateway IP/FQDN.
-
Click Connect.
-
-
Authenticate by OCI IAM.
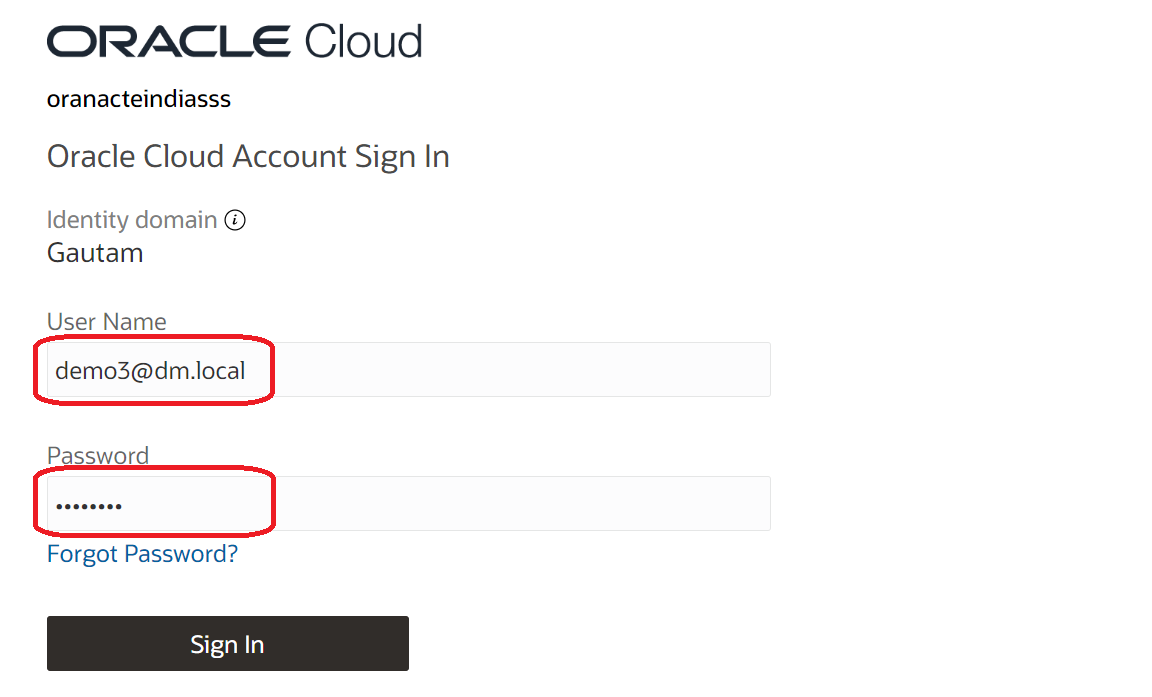
User is redirected to OCI IAM for authentication. User enters their AD Username and Password and after successful authentication (Delegated Authentication) they are redirected back to the VMware Horizon client with a valid token.
-
Launch a Virtual Desktop or Application.
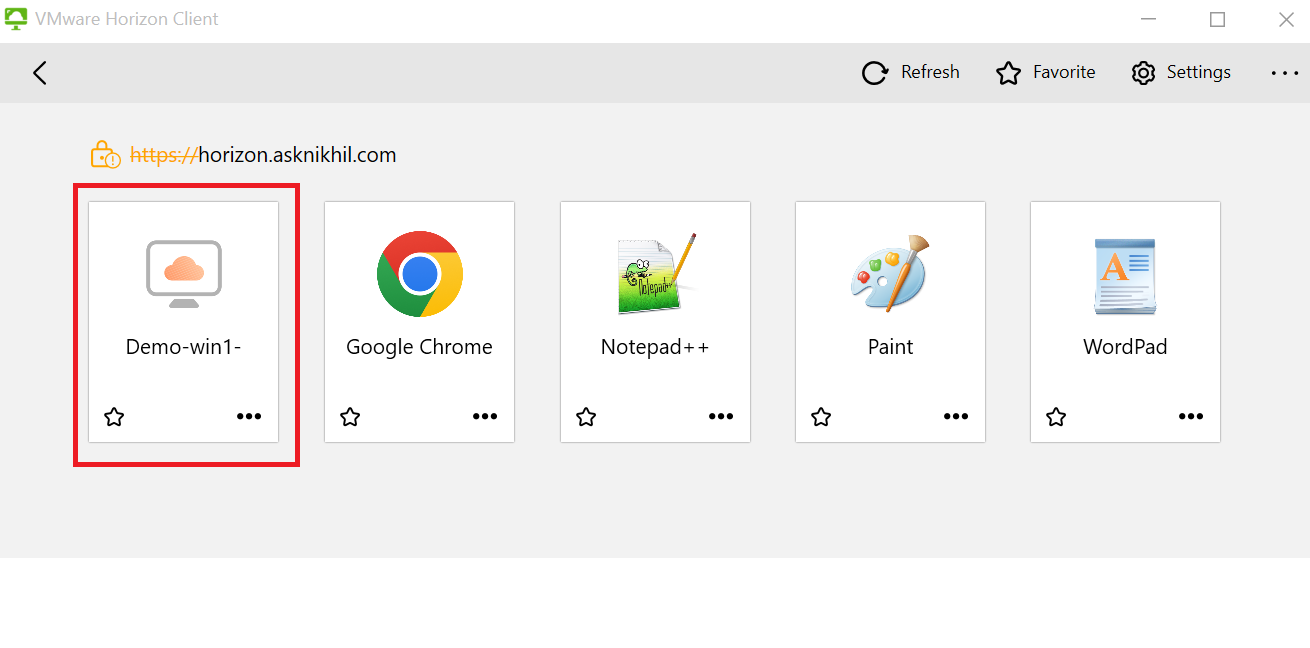
After successful authentication, user will be presented with the desktops and applications entitled to them. Double Click in one of the Desktop or Applications icons to launch the resource.
-
Confirm the Virtual Desktop or Application has been launched.
Task 6: Configure MyConsole Applications to Launch Horizon Desktop and Applications
In this task, you configure a confidential application to launch a Horizon desktop. You can repeat the same steps to create multiple applications.
-
Add a new application.
-
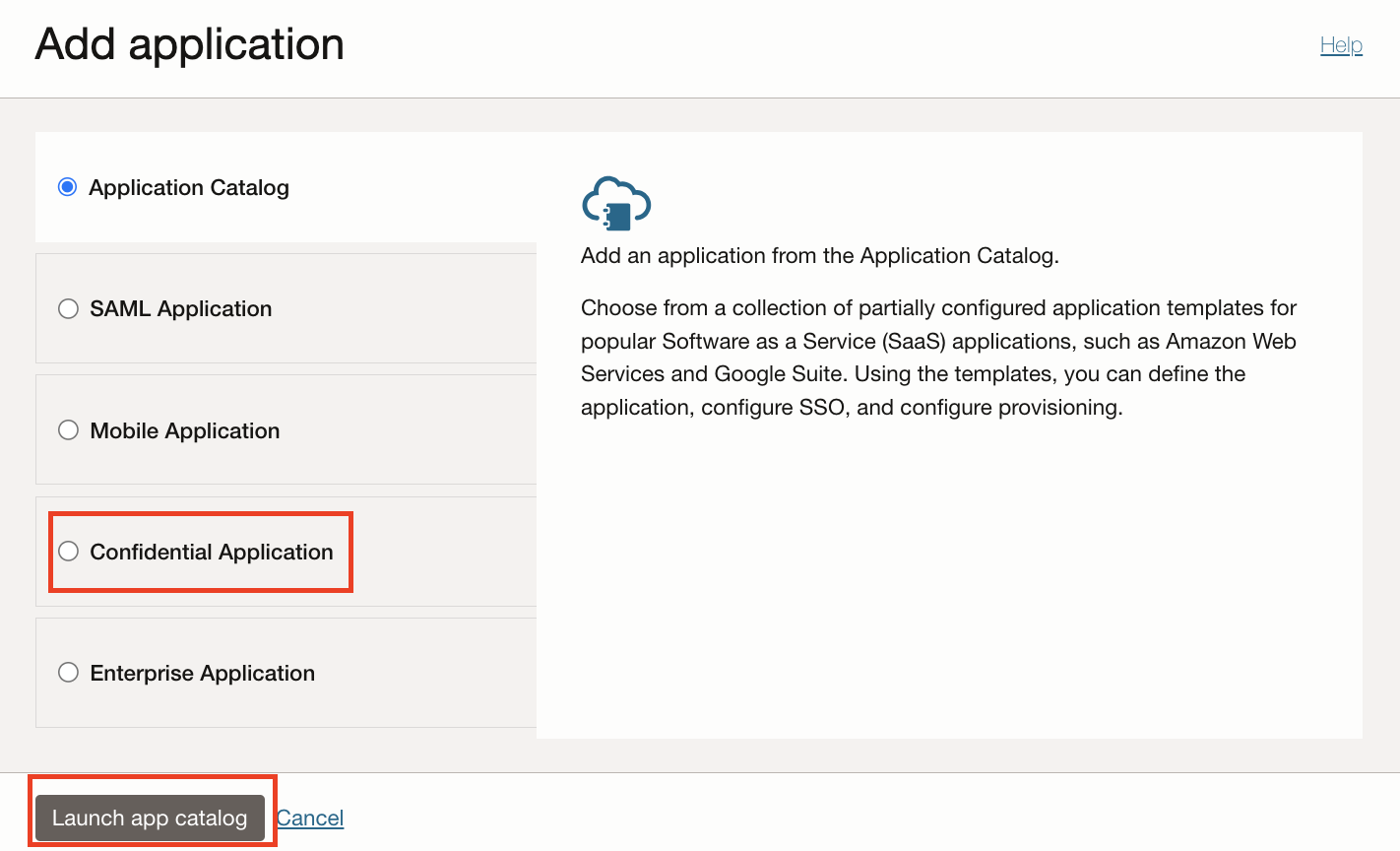
Navigate to Applications and then click Add Application .
-
Select Confidential Application and then click Launch Workflow.
-
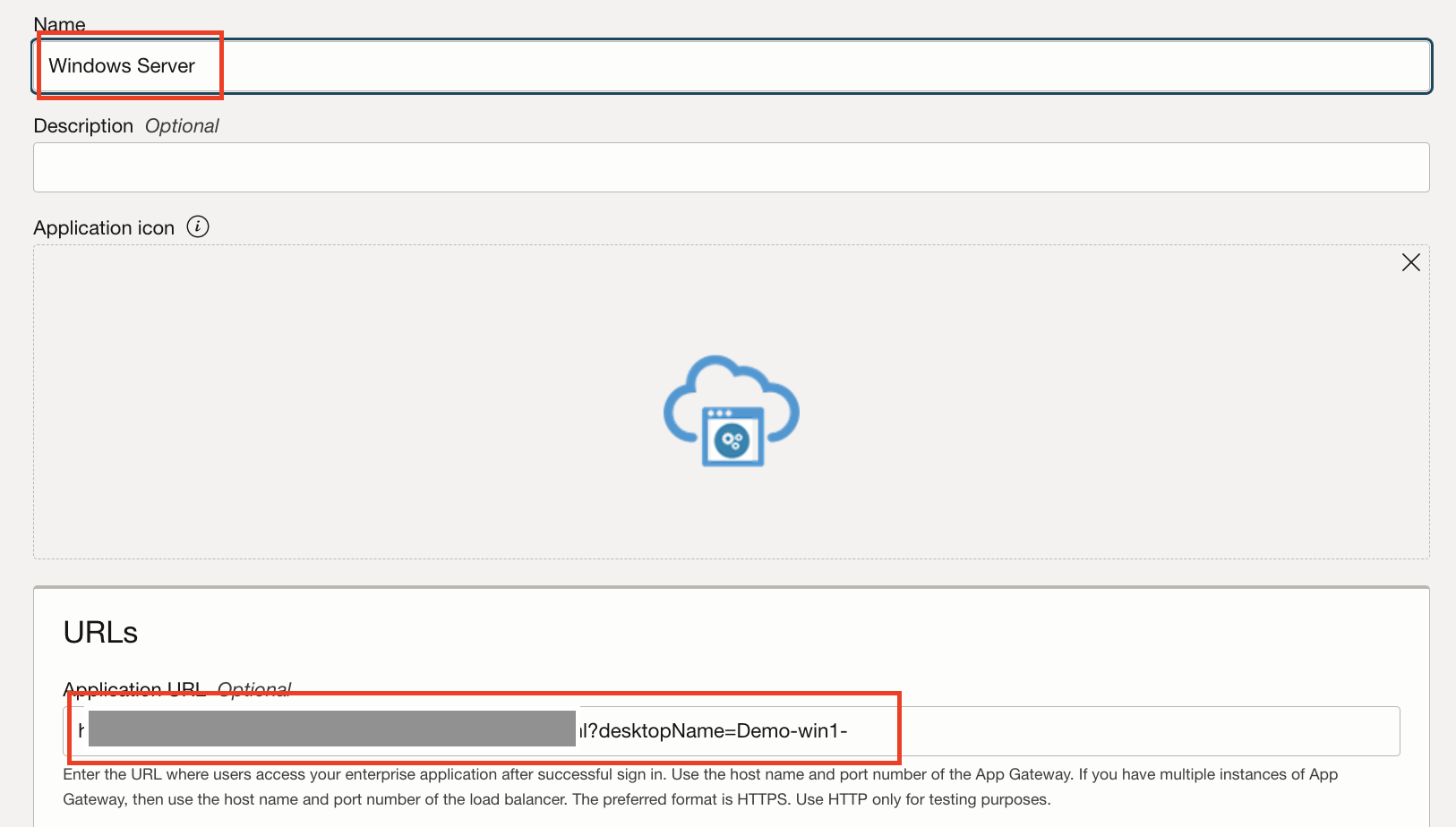
On the new application wizard, provide the Application name and Application URL.
Note: To launch a virtual desktop named Demo-win1- from the Desktop Pool using OCI IAM Identity Domain My Console, the URL syntax is as follows
https://<UAG-hostname>/portal/webclient/index.html?desktopName=Win10Desktop. For example, the URL syntax to launch Notepad from the Application Pool will behttps://<UAG-hostname>/portal/webclient/index.html?applicationName=Notepad.
-
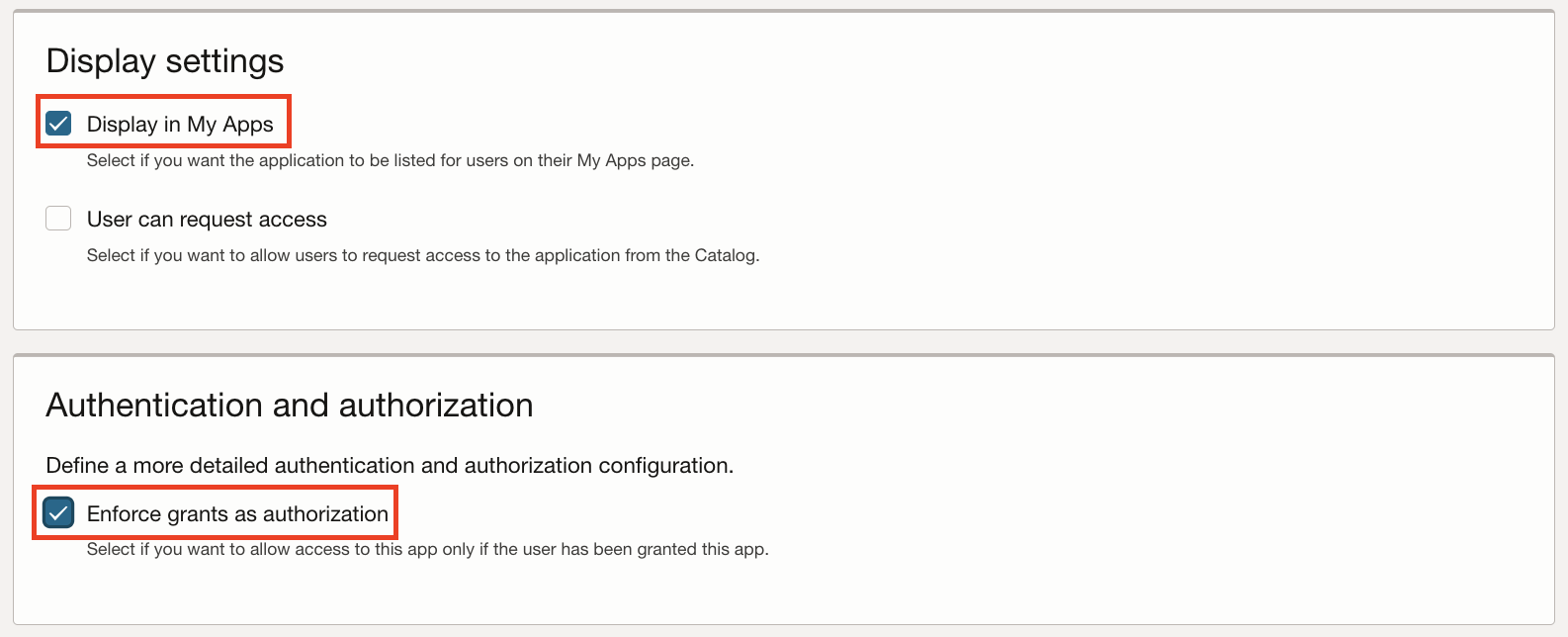
In the Display Settings, select the option Display in My Apps.
-
Select Enforce grants as authorization in Authentication and authorization section and click Next.
-
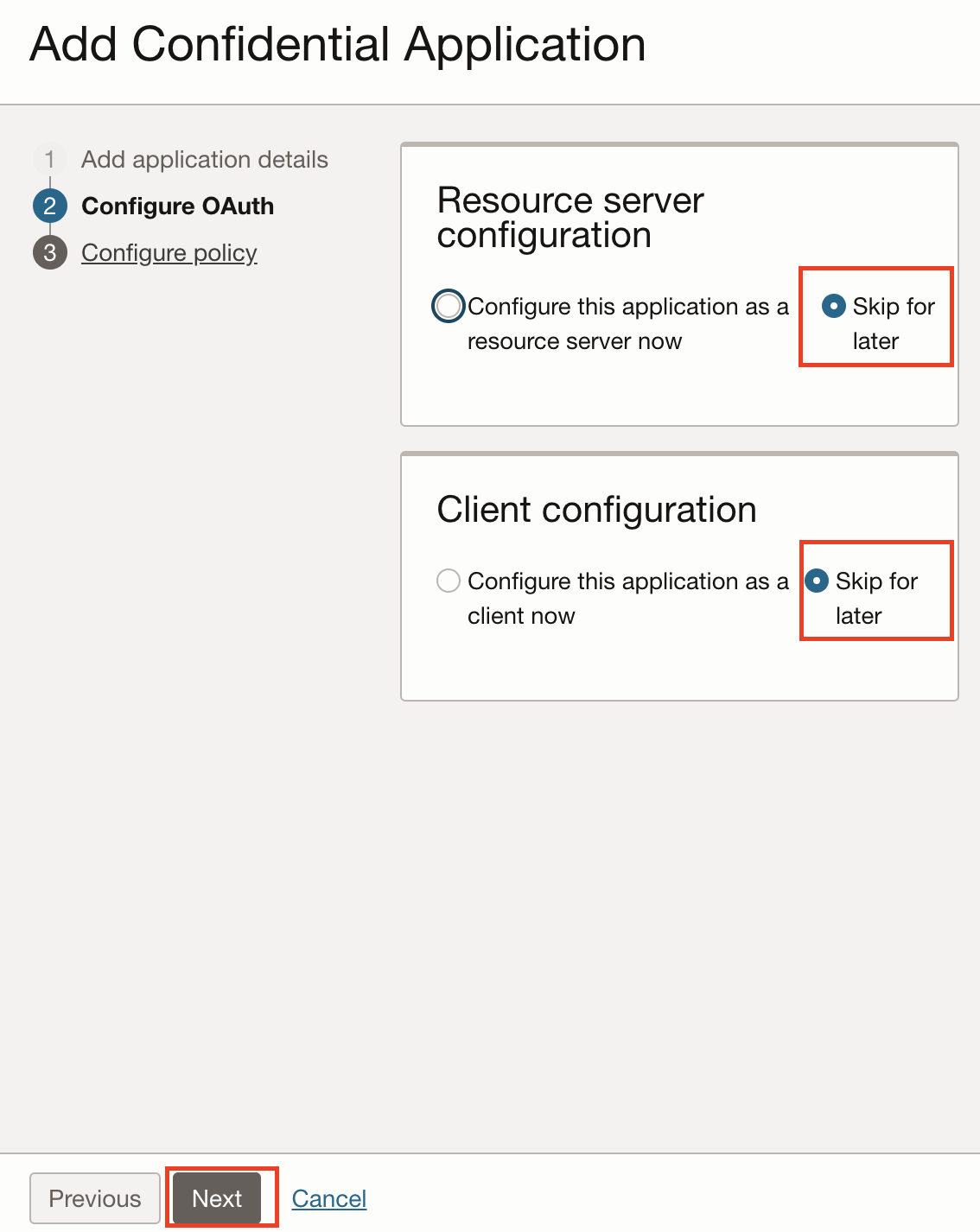
In the Configure OAuth section, select the Skip for later option for both Resource Server configuration and Client configuration and then click Next.
-
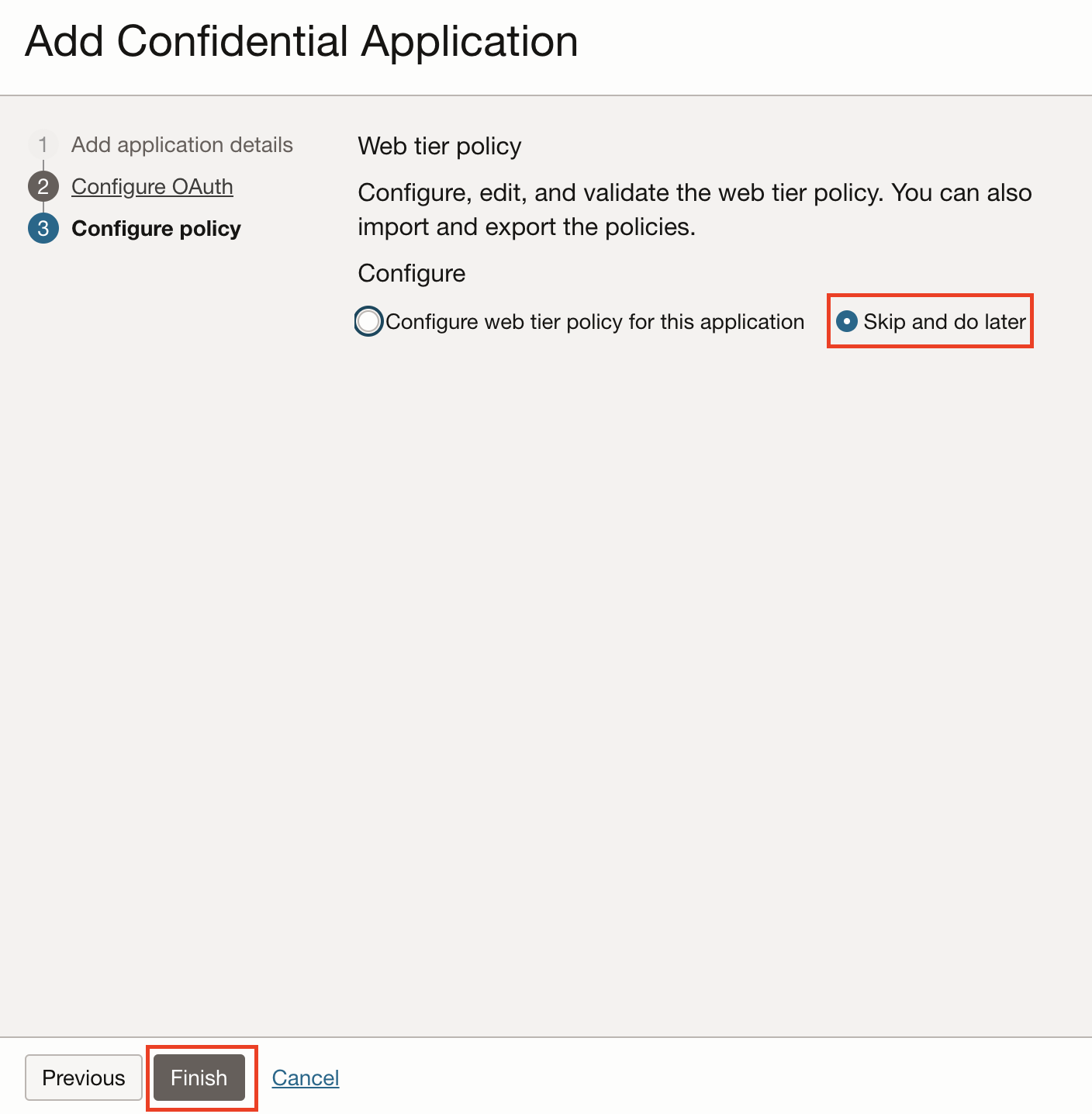
Select the Skip and do later option in the Configure Policy section and then click Finish.
-
-
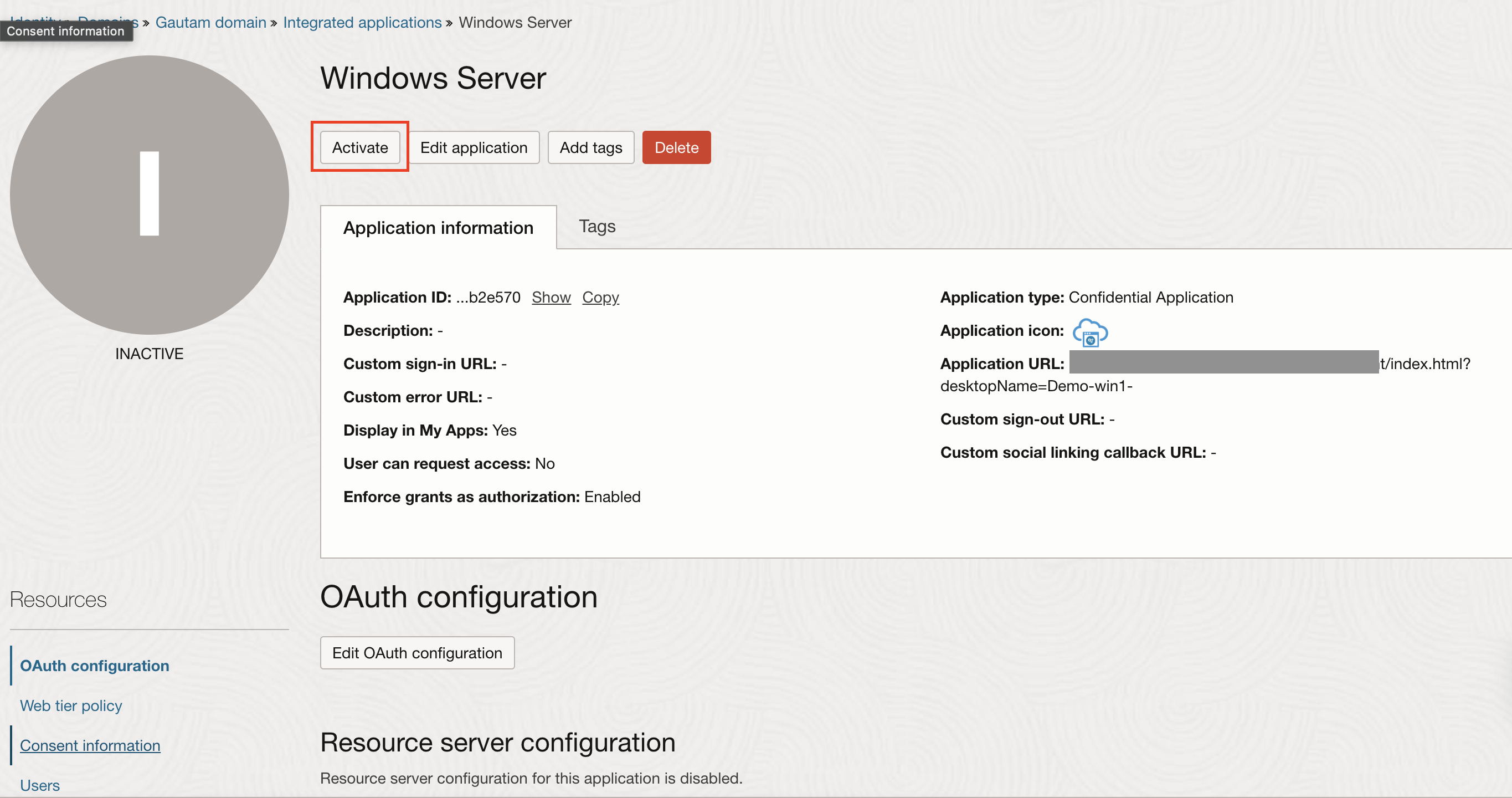
Activate the application once created.
-
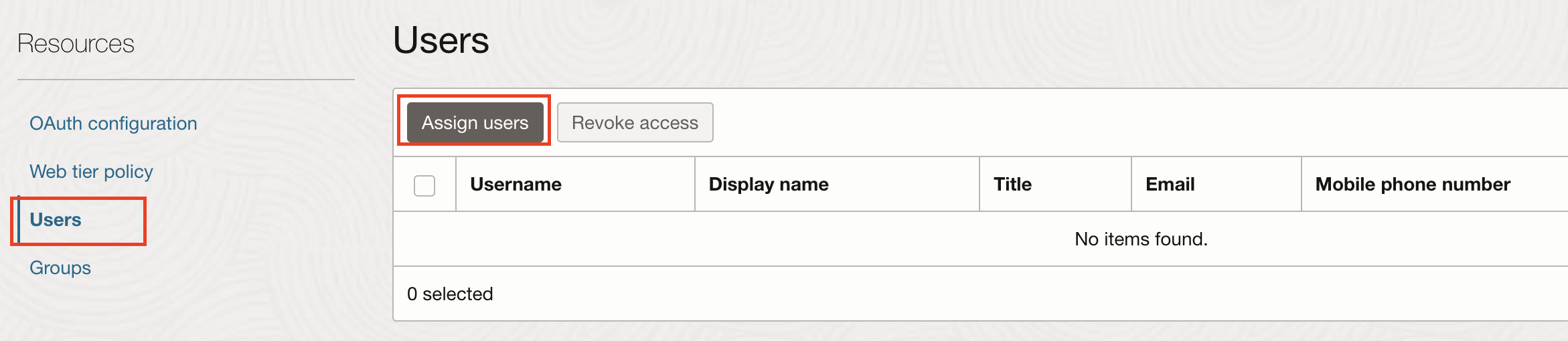
Assign users and groups: Click Users or Groups to assign the respective user or group of users.
Task 7: Validate Desktop and Application Launch from OCI IAM MyConsole.
-
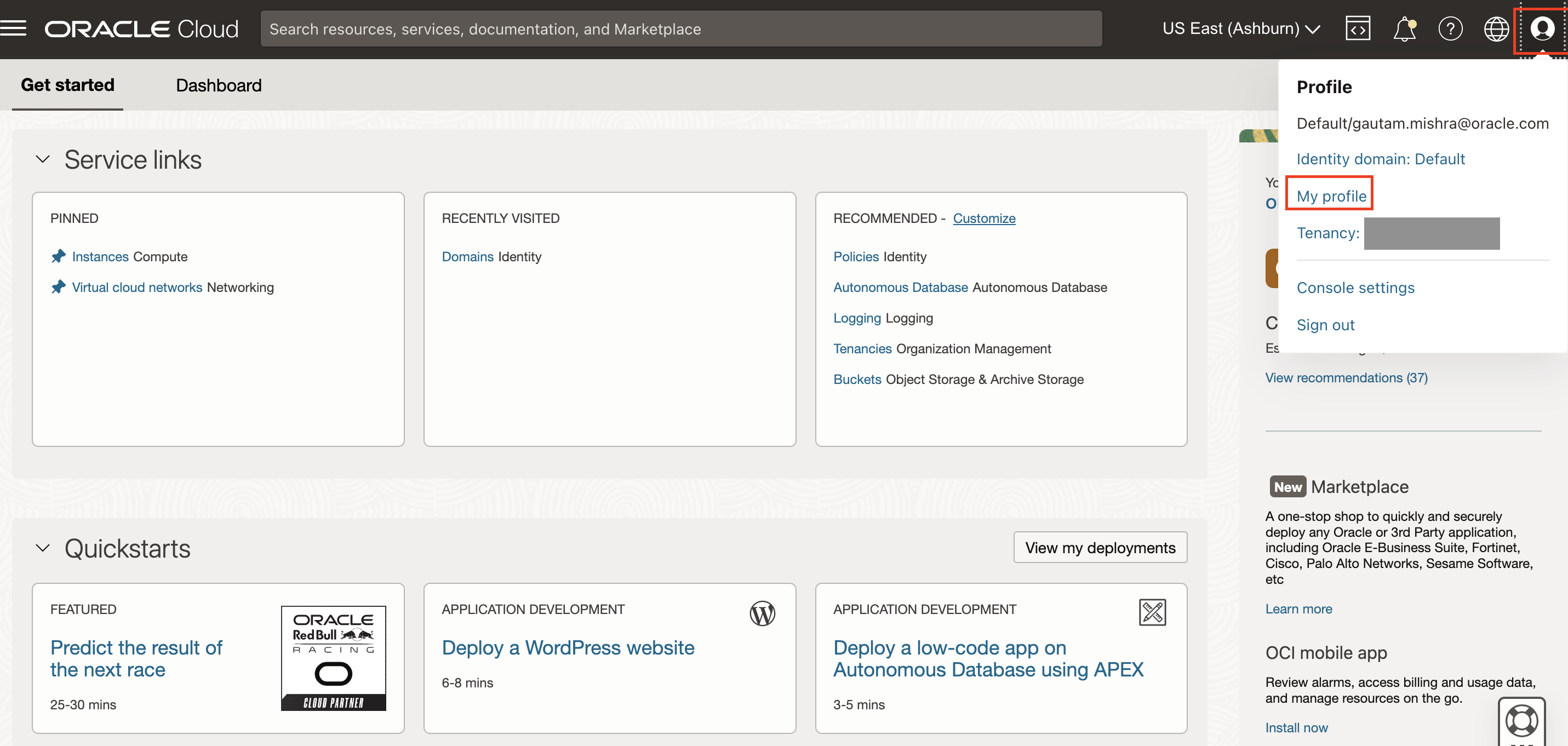
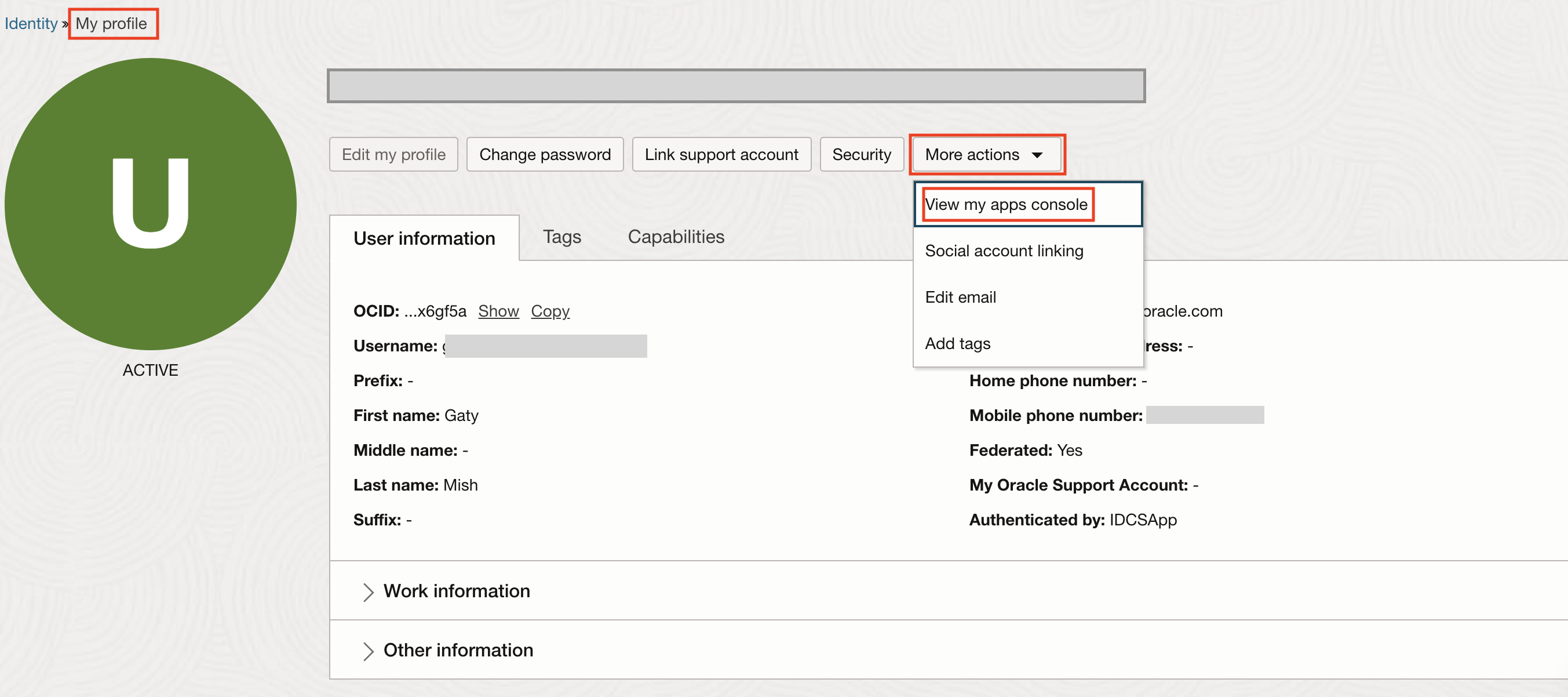
Log in to the OCI console and navigate to My Profile.
-
Click View my apps console under More Actions.
-
A successful login will present all the applications assigned to your account. Select an application to launch.

- VMware UAG — This is the SAML 2.0 application used to generate the IdP metadata. Launching this app redirects you to the Horizon HTML client. You can hide this app on the OCI IAM administration console.
- Notepad — Refers to the Notepad application pool, which will launch a new Notepad session.
- Windows Server — Refers to the Demo-win1- desktop pool, which will launch a new Desktop session.
-
Confirm the virtual desktop or application has been launched.
-
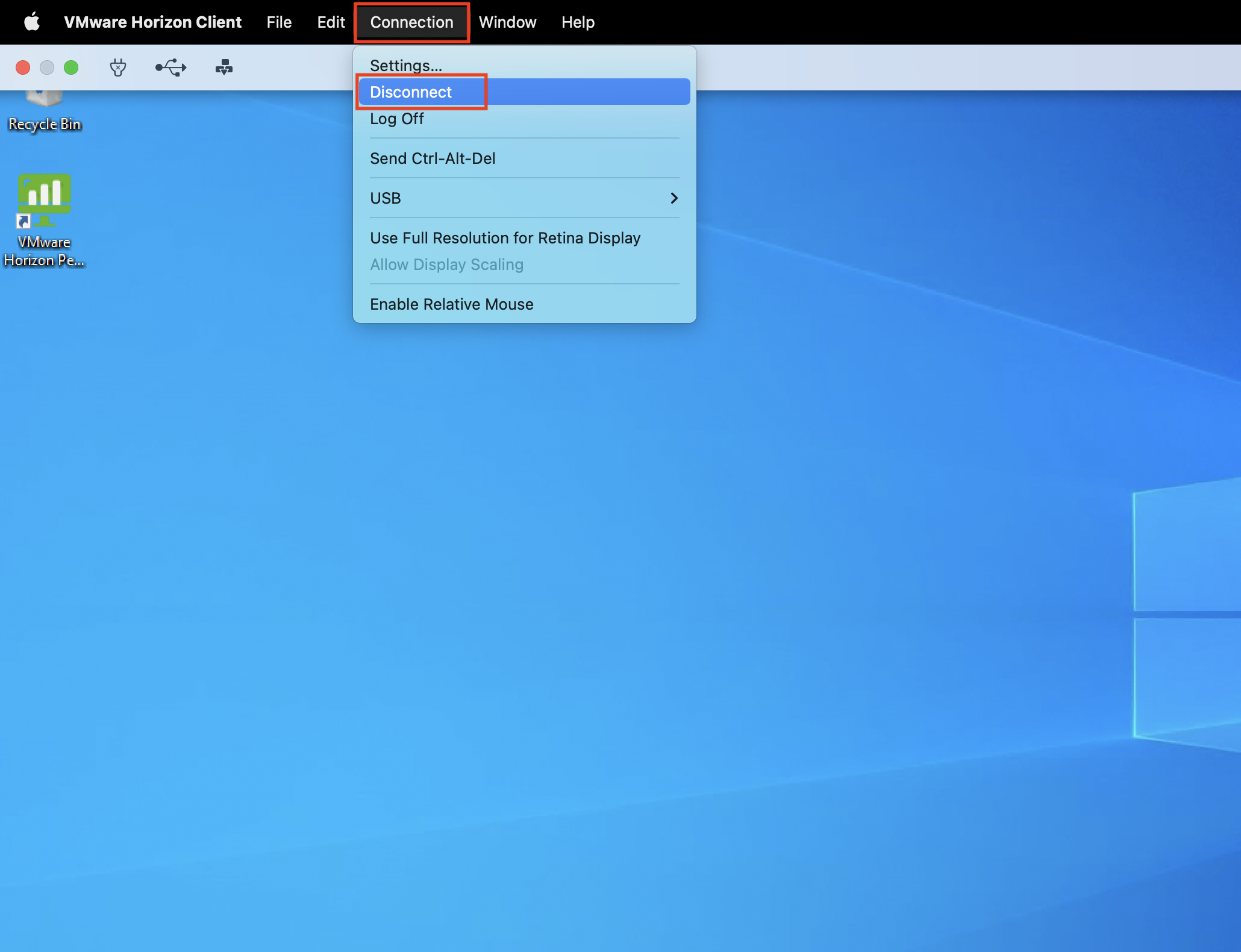
Click Options.
-
Click Connection and then click Disconnect.
-
As result of the SAML Authenticator and True SSO configuration in VMware Horizon, single sign-on is configured and the user is automatically logged in.
Related Links
- VMware Horizon on Oracle Cloud VMware Solution
- Deploy and Configure VMware Unified Access Gateway™
- Oracle Cloud VMware Solution
- Configuring the Microsoft Active Directory (AD) Bridge for AD Synchronization and Delegated Authentication
Acknowledgments
Authors - Gautam Mishra (Senior Cloud Engineer), Nikhil Verma (Principal Cloud Architect).
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally, visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation, visit Oracle Help Center.
Enable SAML 2.0 authentication for VMware Horizon with Unified Access Gateway and OCI IAM Identity Domains
F78558-02
September 2023
Copyright © 2023, Oracle and/or its affiliates.