8 FIPS 140 Support in Oracle Fusion Middleware
- About the FIPS Standard
Federal Information Processing Standards (FIPS) are a series of standards established by the US National Institute of Standards for Technology (NIST) for use in evaluating the security of computer systems and networks. - About FIPS 140-2 in Oracle Fusion Middleware Release 12c
Oracle Fusion Middleware Release 12c (12.2.1.2) supports the use of FIPS 140-2-enabled cryptographic libraries. - Components with FIPS 140 Support
When you plan to work with FIPS 140 in Oracle Fusion Middleware, be aware of the different components at various layers of the middleware stack where certain features may operate in FIPS 140 mode. If any component in the stack is operating in non-FIPS 140 mode, the transaction may not be FIPS 140-compliant. It is therefore important to ensure that all relevant components are operating in FIPS 140 mode. - Common Scenarios for an Operational FIPS 140-2 Environment
The implementation of a feature and the establishment of a connection between a client and a server are some of the possible scenarios you may use or encounter while operating in a FIPS 140–2 environment. Each component scenario uses a corresponding communication protocol and signature algorithm. - Troubleshooting FIPS 140 Issues
You may encounter problems while configuring FIPS 140 for different components of the Oracle Fusion Middleware and need information on how to troubleshoot those problems.
Parent topic: Secure Communication
About the FIPS Standard
Federal Information Processing Standards (FIPS) are a series of standards established by the US National Institute of Standards for Technology (NIST) for use in evaluating the security of computer systems and networks.
One of the FIPS standards, FIPS 140-2, specifies the security requirements that must be met by a cryptographic module to protect sensitive information. The standard provides four increasing, qualitative levels of security to cover the wide range of potential applications and environments in which cryptographic modules may be employed.
Note:
In the remainder of this chapter, the term 'FIPS 140' refers to the FIPS 140-2 standard.
Parent topic: FIPS 140 Support in Oracle Fusion Middleware
About FIPS 140-2 in Oracle Fusion Middleware Release 12c
Oracle Fusion Middleware Release 12c (12.2.1.2) supports the use of FIPS 140-2-enabled cryptographic libraries.
The ability to operate in FIPS 140 mode is not a generic, product suite-wide claim. Instead, it is specific to a defined set of scenarios and transactions supported by relevant Oracle Fusion Middleware 12c (12.2.1.2) product components. It applies where validated cryptography is used to support or enforce security-sensitive tasks such as authentication, authorization, confidentiality, integrity, and so on.
The use of cryptographic services for other tasks that are non-security sensitive does not require FIPS 140 compliance. Oracle Fusion Middleware 12c (12.2.1.2) supports enabling FIPS 140 mode for security-sensitive scenarios while complying and co-existing with product functionality that does not require operating in that mode.
- About FIPS 140-2 Validated Libraries
Oracle Fusion Middleware 12c (12.2.1.2) includes FIPS 140-validated RSA libraries from RSA, the Security Division of EMC (RSA) to support FIPS 140 operation. Algorithms not approved under FIPS 140 are disabled within the RSA libraries. - About Provider and Algorithm Selection
FIPS 140 implementation in Oracle Fusion Middleware occurs in the context of the Java platform's Java Cryptography Architecture (JCA). To accommodate the co-existence of FIPS 140-validated algorithms for security-sensitive tasks as well as algorithms for other tasks, additional cryptographic providers are also configured to provide functionality not supported in FIPS 140-validated RSA libraries, and for certain non-compliant cryptographic functions such as MD5, which are disabled within the FIPS 140-validated RSA libraries.
Parent topic: FIPS 140 Support in Oracle Fusion Middleware
About FIPS 140-2 Validated Libraries
Oracle Fusion Middleware 12c (12.2.1.2) includes FIPS 140-validated RSA libraries from RSA, the Security Division of EMC (RSA) to support FIPS 140 operation. Algorithms not approved under FIPS 140 are disabled within the RSA libraries.
The libraries are based on RSA version 6.2 BSAFE and JCE software and include the following modules:
-
Crypto-J V6.2.0.1
-
SSL-J V6.2
-
Cert-J V6.2
FIPS 140-2 support requires JDK 8. Fusion Middleware 12c uses Oracle JDK 1.7.0_80 or higher.
In addition to the continued support for RSA keys, Oracle Fusion Middleware 12c (12.2.1.2) also supports Elliptic Curve Cryptography (ECC). ECC is emerging as an attractive public-key cryptography because it offers equivalent security with smaller key sizes, which results in faster computations, lower power consumption, and memory and bandwidth savings.
Note:
These are the FIPS 140-certified library and module versions at the time of publication. The actual versions in effect at your installation could be slightly different from the ones listed here, as the vendor may issue some patches between certification and the time the product actually shipped. Thus the actual version could be a dot release of the certified version.
The version number is for information only; you can do any independent verification of certification and strength of algorithms.
For background about the FIPS 140 standards and algorithms, refer to the FIPS 140-2 documentation at:
http://csrc.nist.gov/publications/PubsFIPS.html
Parent topic: About FIPS 140-2 in Oracle Fusion Middleware Release 12c
About Provider and Algorithm Selection
FIPS 140 implementation in Oracle Fusion Middleware occurs in the context of the Java platform's Java Cryptography Architecture (JCA). To accommodate the co-existence of FIPS 140-validated algorithms for security-sensitive tasks as well as algorithms for other tasks, additional cryptographic providers are also configured to provide functionality not supported in FIPS 140-validated RSA libraries, and for certain non-compliant cryptographic functions such as MD5, which are disabled within the FIPS 140-validated RSA libraries.
The basic flow is as follows:
-
An application (for example, an external web client or Oracle HTTP Server) requests a service or connection to a server such as WebLogic Server. The request typically involves a "payload" such as a data packet to be transmitted.
-
JCA evaluates the request to determine whether FIPS 140 compliance is required.
-
The request is routed to JCA's "provider" framework, which contains a set of (FIPS 140-compliant and non-compliant) providers for digital signatures, message digests (hashes), certificates, and certificate validation, encryption, and other cryptographic services.
-
The providers are searched in preference order and the implementation from the first provider that supplies the correct algorithm is returned. For the security-sensitive cases, only FIPS 140 compliant algorithms are used to execute the cryptographic operations.
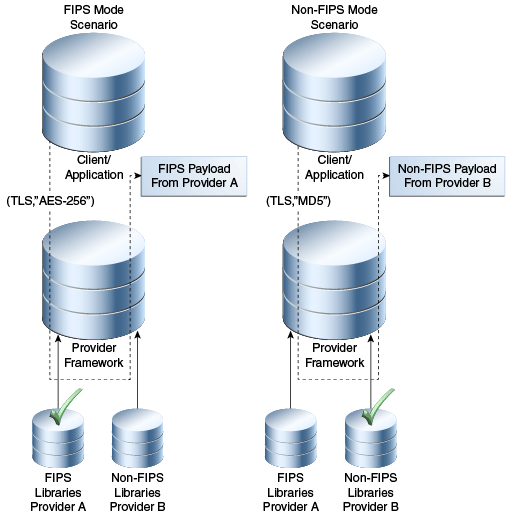
Figure 8-1 illustrates this flow:
-
The first request, on the left, is made in a security-sensitive scenario. JCA uses the SHA-256 provider from the RSA cryptographic library to process the request and deliver the FIPS 140 payload.
-
The second request, on the right, is executed in a non-sensitive scenario. JCA uses the MD5 provider from the non-cryptographic library to process the request with the non-FIPS 140 payload.
Thus, a security-sensitive scenario such as HTTPS/TLS inbound and outbound communication which is intended to be FIPS 140-compliant uses only those cryptographic functions available in the FIPS 140-validated RSA libraries to encrypt and sign HTTPS/TLS network payloads.
Parent topic: About FIPS 140-2 in Oracle Fusion Middleware Release 12c
Components with FIPS 140 Support
When you plan to work with FIPS 140 in Oracle Fusion Middleware, be aware of the different components at various layers of the middleware stack where certain features may operate in FIPS 140 mode. If any component in the stack is operating in non-FIPS 140 mode, the transaction may not be FIPS 140-compliant. It is therefore important to ensure that all relevant components are operating in FIPS 140 mode.
Table 8-1 lists the components where you can enable FIPS 140, and contains the following details:
-
The Oracle Fusion Middleware layer where the component resides;
-
the component name
-
the scenario which can be FIPS 140-enabled
-
cross-reference to product documentation for details, including how to enable or disable FIPS 140, other relevant configuration details, and what product functions support the use of FIPS 140-validated cryptography.
Note:
Not all features of each listed component are FIPS 140-compliant. Only the specified features support FIPS 140.
Table 8-1 Components with FIPS 140-2 Support in Oracle Fusion Middleware
| Component Layer | Component | Feature | Details |
|---|---|---|---|
|
Fusion Middleware Core |
Oracle HTTP Server |
Note: For outbound connections from OHS to WLS, FIPS must be enabled at WebLogic (for inbound connections) to enable FIPS communication between OHS and WLS. |
These topics in Administering Oracle HTTP Server:
|
|
Fusion Middleware Core |
Oracle WebLogic Server |
|
"Enabling FIPS Mode" in Administering Security for Oracle WebLogic Server "Use the SHA-256 Secure Hash Algorithm" in Securing WebLogic Web Services for Oracle WebLogic Server "Using Encrypted Connection Properties" in Administering JDBC Data Sources for Oracle WebLogic Server |
|
Fusion Middleware Core |
Oracle Platform Security Services |
|
"FIPS Support in OPSS" in Securing Applications with Oracle Platform Security Services |
|
Fusion Middleware Core |
Oracle Web Services Manager |
|
"Supported Algorithm Suites" in Securing Web Services and Managing Policies with Oracle Web Services Manager |
|
Fusion Middleware Core |
Oracle SOA Suite |
|
"About FIPS Compliance for the SFTP Transport" in Developing Services with Oracle Service Bus "Enabling FIPS Compliance in Oracle File and FTP Adapters" in Understanding Technology Adapters |
|
Fusion Middleware Core |
Oracle Traffic Director |
|
“Managing Security” in Administering Oracle Traffic Director |
|
Database |
Oracle Database |
|
“Oracle Database FIPS 140–2 Settings” in Oracle Database Security Guide |
Note:
Database is included for reference. Consult the certification matrix for supported versions and other details.
For detailed information about SSL FIPS 140-2 for OHS, OWLS, OPSS, and OWSM, refer to support Document 2115681.1 on My Oracle Support. You can access My Oracle Support at: https://support.oracle.com/.
Parent topic: FIPS 140 Support in Oracle Fusion Middleware
Common Scenarios for an Operational FIPS 140-2 Environment
The implementation of a feature and the establishment of a connection between a client and a server are some of the possible scenarios you may use or encounter while operating in a FIPS 140–2 environment. Each component scenario uses a corresponding communication protocol and signature algorithm.
Table 8-1 listed the components in Oracle Fusion Middleware with FIPS 140-2 features. Table 8-2 lists typical protocols for each component scenario:
Note:
These are representative scenarios - the table is not intended to provide a comprehensive listing of all possible scenarios.
Table 8-2 FIPS 140-2 Scenarios
| Feature or Connection | Communication Protocol | Signature Algorithm/Protocol Details |
|---|---|---|
|
Inbound connection from an external web client or application to Oracle HTTP Server |
|
HTTPS Server (TLS, Mutual Authentication, RSA-2048 with SHA-256 X.509 Certificates, AES-256 Bulk Data Encryption, ECDSA Signing Algorithm and ECDH Key Agreement) |
|
Outbound connection from Oracle HTTP Server to Oracle WebLogic Server |
|
HTTPS Client (TLS, Mutual Authentication, RSA-2048 with SHA-256 X.509 Certificates, AES-256 Bulk Data Encryption, ECDSA Signing Algorithm and ECDH Key Agreement) |
|
Inbound connection from an external web client or application to Oracle WebLogic Server |
|
HTTPS Server (TLS, Mutual Authentication, RSA-2048 with SHA-256 X.509 Certificates, AES-256 Bulk Data Encryption) |
|
Outbound connection from Oracle WebLogic Server to an external web, proxy or application server |
|
HTTPS Client (TLS, Mutual Authentication, RSA-2048 with SHA-256 X.509 Certificates, AES-256 Bulk Data Encryption) |
|
Outbound connection from Oracle WebLogic Server to Oracle Database 11gR2 |
|
JDBC (TLS, Mutual Authentication, RSA-2048 with SHA-256 X.509 Certificates, AES-256 Bulk Data Encryption) |
|
XML Message Protection (XML Signing) for SOAP messages using Oracle Web Services Manager |
|
XML Signature (RSA-SHA256, HMAC-SHA256); Entire Body, Include SwA Attachment |
|
XML Message Protection (XML Encryption) for SOAP messages using Oracle Web Services Manager |
|
XML Signature (RSA-SHA256, HMAC-SHA256); Entire Body, Include SwA Attachment |
|
Inbound JMS connection to Oracle WebLogic Server |
|
JMS/TLS |
|
Outbound JMS connection from Oracle WebLogic Server |
|
JMS/TLS |
|
Secure JNDI lookups from deployed components |
|
T3S |
|
Secure administrator access to servers |
|
T3S |
|
Keystore and Certificate Generation |
|
RSA 2048, AES 256, SHA-2 |
|
Hashing Algorithms, Password-Based Encryption |
|
SHA-2 |
|
Oracle Service Bus for SOA service-based components |
SFTP transport for service types:
|
Public Key Algorithm (diffie-hellman-group14-sha1) Key Exchange Algorithm (ssh-rsa) |
|
Managed File Transfer (MFT)
|
File transports:
|
Typical algorithms
|
|
JCA Adapters |
File Transfer Protocol |
|
Note:
Unless otherwise indicated, all component servers are at Release 12c (12.2.1.2).
Parent topic: FIPS 140 Support in Oracle Fusion Middleware
Troubleshooting FIPS 140 Issues
You may encounter problems while configuring FIPS 140 for different components of the Oracle Fusion Middleware and need information on how to troubleshoot those problems.
This section explains how to troubleshoot issues encountered with FIPS 140 configuration. It contains these topics:
- FIPS 140 Troubleshooting for Stand-alone WebLogic Server
Follow these steps to troubleshoot FIPS 140 mode for a stand-alone Oracle WebLogic Server while configuring a WebLogic Server and the Data Source properties. - FIPS 140 Troubleshooting for Oracle Platform Security Services
Find out how to troubleshoot issues that originate at different stages of FIPS configuration in Oracle Platform Security Services (OPSS). - FIPS 140 Troubleshooting for Oracle Web Services Manager
Find out how to troubleshoot issues originating in Oracle Web Services Manager during message protection policy enforcement. - FIPS 140 Troubleshooting for Database and JDBC Driver
Review this topic for information about security configuration for the database, the JDBC driver, including data source issues related to database.
Parent topic: FIPS 140 Support in Oracle Fusion Middleware
FIPS 140 Troubleshooting for Stand-alone WebLogic Server
Follow these steps to troubleshoot FIPS 140 mode for a stand-alone Oracle WebLogic Server while configuring a WebLogic Server and the Data Source properties.
During WebLogic Server Configuration
-
Make sure to prepend the server CLASSPATH with jcmFIPS.jar and sslj.jar.
-
To explicitly verify *
AES_256*cipher suites, update the local_policy.jar and US_export_policy.jar in the JAVA_HOME/jre/lib/security directory with the corresponding file with unlimited strength. -
Modify JAVA_HOME/jre/lib/security/java.security by putting security.provider.1=com.rsa.jsafe.provider.JsafeJCE and security.provider.2=com.rsa.jsse.JsseProvider on top of the list.
For more information on FIPS mode in Oracle WebLogic Server, see "Enabling FIPS Mode" in Administering Security for Oracle WebLogic Server.
During Data Source Configuration
Make sure that the value of the DataSource property oracle.net.ssl_version is set to 1.0.
Note:
oracle.net.ssl_version is an optional Oracle WebLogic Server DataSource configuration property. A value of 1.0 represents connection through TLS v 1.0 Protocol.
Parent topic: Troubleshooting FIPS 140 Issues
FIPS 140 Troubleshooting for Oracle Platform Security Services
Find out how to troubleshoot issues that originate at different stages of FIPS configuration in Oracle Platform Security Services (OPSS).
During WebLogic Domain Creation
You may see the following exceptions in wlsconfig_xxxxx.log during domain creation in FIPS 140 mode:
"CFGFWK-60455: The password must be at least 8 alphanumeric characters with at least one number or special character." "Caused by: java.lang.NoSuchMethodError: com.rsa.jsafe.JSAFE_SecretKey.generateInit([ILjava/security/SecureRandom;)"
This exception may occur if you are using cryptoJ 5 jars. Make sure you have installed Oracle WebLogic Server with cryptoJ 6 jars to avoid this error.
When Exporting from Domain Keystore
If you are using JKS and JCEKS type keystores in a FIPS 140-enabled domain, and see the following error:
Command FAILED, Reason: oracle.security.jps.service.keystore.KeyStoreServiceException: Failed to export the keystore
make sure that you have configured the following providers in the java.security file:
sun.security.provider.Sun com.sun.crypto.provider.SunJCE
During Key or Certificate Generation
When generating key or certificate with password protection, you may get the following error:
javax.management.MBeanException: javax.management.MBeanException: oracle.security.jps.service.keystore.KeyStoreServiceException: Failed to generate CA signed certificate.
make sure that you use permission protection.
Parent topic: Troubleshooting FIPS 140 Issues
FIPS 140 Troubleshooting for Oracle Web Services Manager
Find out how to troubleshoot issues originating in Oracle Web Services Manager during message protection policy enforcement.
During Message Protection Policy Enforcement
If you see this error during Oracle Web Services Manager message protection policy enforcement:
Caused by: java.lang.SecurityException: Algorithm not allowable in FIPS140 mode: MD5 at com.rsa.cryptoj.o.cc.b(Unknown Source) at com.rsa.cryptoj.o.cc.f(Unknown Source)
make sure that certificates used in message protection enforcement are generated using FIPS 140-compliant algorithms like SHA1WithRSA or SHA256WithRSA.
If you encounter this error for the JKS keystore during message protection policy enforcement:
oracle.fabric.common.PolicyEnforcementException: WSM-00143 : Failure creating Java Keystore instance for type JKS.
make sure that sun.security.provider.Sun is configured in the JDK.
Parent topic: Troubleshooting FIPS 140 Issues
FIPS 140 Troubleshooting for Database and JDBC Driver
Review this topic for information about security configuration for the database, the JDBC driver, including data source issues related to database.
For complete details, see the white paper "SSL With Oracle JDBC Thin Driver" on the Oracle Technology Network at:
http://www.oracle.com/technetwork/middleware/id-mgmt/documentation/index.htmlParent topic: Troubleshooting FIPS 140 Issues