13 Configuring Access Manager Settings
The Access Manager Settings provide configuration options for a number of specific Access Manager service operations.
This chapter describes these Access Manager-specific settings.
13.1 Oracle Access Management Overview
Familiarize with the Oracle Access Management, Serve registration and management before you start off with configuration options and service operations.
Be sure to review the following topics:
13.2 Managing Load Balancing
Configure two or more Managed Servers to operate as a cluster and use Oracle Access Management Console for Access Manager load balancing settings.
This section describes the following topics:
13.2.1 About Common Load Balancing Settings
For production environments that require increased application performance, throughput, or high availability, you can configure two or more Managed Servers to operate as a cluster. A cluster is a collection of multiple WebLogic Server server instances running simultaneously and working together to provide increased scalability and reliability.
In a cluster, most resources and services are deployed identically to each Managed Server (as opposed to a single Managed Server), enabling failover and load balancing. A single domain can contain multiple WebLogic Server clusters and multiple Managed Servers that are not configured as clusters. The key difference between clustered and non-clustered Managed Servers is support for failover and load balancing. These features are available only in a cluster of Managed Servers.
By default, Access Manager has a single OAM Server to which all login and logout requests are sent. In a high-availability deployment, you must change this setup so that login and logout requests are first sent to the load balancer.
See Also:
High Availability Guide, "Access Manager High Availability Configuration Steps" for high-level instructions to set up a high availability Access Manager deployment.
Figure 13-1 shows the Load Balancing Settings section of the Access Manager Settings page. In earlier releases this was part of the SSO Engine settings; the SSO Engine being the controller for sessions.
Figure 13-1 Access Manager Settings: Load Balancer
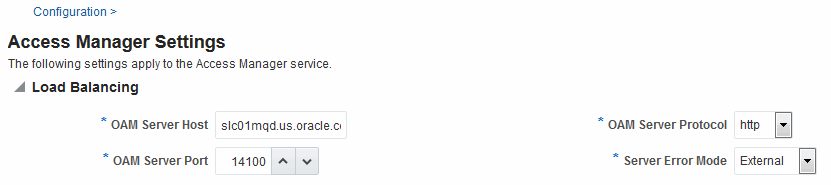
Description of "Figure 13-1 Access Manager Settings: Load Balancer"
Table 13-1 describes each element and how it is used. Settings are global and common to all OAM Servers in the WebLogic administration domain.
Table 13-1 Access Manager Settings: Load Balancer
| Element | Description |
|---|---|
|
OAM Server Host |
The virtual host name that represents the OAM Server Cluster, which might be exposed by a load balancer in front of an OAM Server Cluster. |
|
OAM Server Port |
The virtual host port associated with the OAM Server Cluster. Values between 1 and 65535 are supported. |
|
OAM Server Protocol |
The protocol, either HTTP or HTTPS, that is used to access the virtual host that represents the OAM Server Cluster. See Also: "About Security Modes and X509Scheme Authentication" |
13.3 Managing Secure Error Modes
A custom error page is packaged as part of the custom login application. An out-of-the-box custom Web application archive file is provided that you can use as a starting point to develop customized login and password pages.
Server Error Mode settings are global and common to all OAM Servers in the WebLogic administration domain. This section provides the following topics:
13.3.1 OAM Server Error Modes
The OAM Server Error Mode appears on the Load Balancing Settings area of the Access Manager Settings page.
Figure 13-1 shows the Server Error Mode function.
Figure 13-2 Access Manager Settings: Server Error Mode

Description of "Figure 13-2 Access Manager Settings: Server Error Mode"
Table 13-2 describes the options you can choose to configure Server Error Mode for your deployment.
Table 13-2 Server Error Mode
| Element | Description |
|---|---|
|
Server Error Mode |
The setting you choose determines the nature of error messages and error codes returned by the OAM Server when an operation fails (because of an invalid username or password, for example, or a server error (connection to the LDAP Server is down)). Choose one of the following settings to configure error messages with varying degrees of security for your custom login pages:
See Also: "Viewing or Editing OAM Server Secure Error Modes" |
Table 13-3 shows the error triggering condition and message codes for each of the three modes.
Table 13-3 Error Trigger Condition, Modes, and Message Codes
| Error Triggering Condition | Internal Mode | External Mode | Secure Mode |
|---|---|---|---|
|
Invalid login attempt |
OAM-1 |
OAM-2 |
OAM-8 |
|
Processing submitted credentials fails. For example: In WNA mode, the SPNEGO token is not received. |
OAM-3 |
OAM-3 |
OAM-8 |
|
An authentication exception is raised. |
OAM-4 |
OAM-4 |
OAM-9 |
|
User account gets locked based on certain conditions (exceeded invalid attempts, for instance). |
OAM-5 |
OAM-5 |
OAM-8 |
|
User account disabled. |
OAM-5 |
OAM-5 |
OAM-9 |
|
User has exceeded the maximum number of allowed sessions (a configurable attribute). |
OAM-6 |
OAM-6 |
OAM-9 |
|
Default error message, which is displayed when no other specific messages propagate up. This is not propagated to the user level. Cause could be multiple conditions. |
OAM-7 |
OAM-7 |
OAM-9 |
|
Password expired. |
OAM-10 |
OAM-10 |
OAM-9 |
Table 13-4 identifies the error codes, trigger conditions, and recommended messages.
See Also:
Developing Custom Error Pages in the Developing Applications with Oracle Access Management
Table 13-4 External Error Codes, Trigger Conditions, and Recommended Messages
| External Error Code | Trigger Condition | Recommended Display Message |
|---|---|---|
|
OAM-1 |
Invalid login attempts less than the allowed count. |
An incorrect Username or Password was specified |
|
OAM-2 |
Invalid login attempts less than the allowed count. |
An incorrect Username or Password was specified |
|
OAM-3 |
Processing submitted credentials fails for some reason. For example: in WNA mode, the SPENGO token is not received. |
Internal Error. |
|
OAM-4 |
An authentication exception is raised for some reason. |
System error. Please contact the System Administrator. |
|
OAM-5 |
The user account gets locked because of certain conditions (exceeded invalid attempts, for instance). |
The user account is locked or disabled. Please contact the System Administrator. |
|
OAM-5 |
The user account gets locked because of certain conditions (exceeded invalid attempts, for instance). OID Without OIG Integration: The Error page appears with contact details after the password is validated. |
The user account is locked or disabled. Please contact the System Administrator. |
|
OAM-5 |
The user account is disabled. |
The user account is locked or disabled. Please contact the System Administrator. |
|
OAM-6 |
The user has exceeded the maximum number of allowed sessions, which is a configurable attribute. |
The user has already reached the maximum allowed number of sessions. Please close one of the existing sessions before trying to login again. |
|
OAM-7 |
Failure could be due to multiple reasons; the exact reason is not propagated to the user level for security reasons. For instance:
The default error message is displayed when no other specific messages are propagated up. |
System error. Please re-try your action. If you continue to get this error, please contact the Administrator. |
|
OAM-8 |
See Table 13-3 |
Authentication failed. |
|
OAM-9 |
System error. Please re-try your action. If you continue to get this error, please contact the Administrator. |
System error. Please re-try your action. If you continue to get this error, please contact the Administrator. |
|
OAM-10 |
Password expired. |
The password has expired. |
13.4 Managing SSO Tokens and IP Validation
Use Oracle Access Management Console for modifying Access Manager SSO settings, IP Validation and SSO token version.
This section provides the following topics:
13.4.1 Access Manager SSO Tokens and IP Validation Settings
The Access Manager Settings page include information such as IP Validation and SSO token version.
Figure 13-3 shows the SSO portion of the Access Manager Settings page. Table 13-5 describes each element and how it is used.
Table 13-5 Access Manager Settings: SSO
| Element | Description |
|---|---|
|
IP Validation |
Specific to WebGates and is used to determine whether a client's IP address is the same as the IP address stored in the ObSSOCookie generated for single sign-on. Check the box to enable IP Validation. Clear the box to disable IP Validation if and only if IP Validation is disabled on all the configured WebGates. See IP Address Validation for WebGates. |
|
SSO Token Version |
Select your SSO token version from the list. |
13.5 Managing the Access Protocol for OAM Proxy Simple and Cert Mode Security
Configure secure server communication modes and manage through the settings for the common OAM Proxy.
This section describes the following topics:
13.5.1 OAM Proxy Simple and Cert Mode Transport Security
Open, Simple, and Cert are the modes of secure communication and there are similarities between these modes.
Table 13-6 outlines the similarities between Simple and Cert modes.
See Also:
Table 13-6 Summary: Simple and Cert Mode
| Artifact or Process | Simple Mode | Cert Mode | Open Mode |
|---|---|---|---|
|
X.509 digital certificates only. |
X |
X |
N/A |
|
Communication between OAM Agents and OAM Servers is encrypted using Transport Layer Security, RFC 2246 (TLS v1). |
X |
X |
N/A |
|
For each public key there is a corresponding private key that Access Manager stores in a file: |
aaa_key.pem generated by openSSL |
aaa_key.pem generated by your CA |
N/A |
|
Signed certificates in Privacy Enhanced Mail (PEM) format |
aaa_cert.pem generated by openSSL |
aaa_cert.pem generated by your CA |
N/A |
|
During OAM Server configuration, secure the private key with a Global passphrase or PEM format details, depending on which mode you are using. Before an OAM Server or Webgate can use a private key, it must have the correct passphrase. |
Global passphrase stored in a nominally encrypted file:
|
PEM format:
|
N/A |
|
During OAM Agent or OAM Server registration, the communication mode is propagated to the Oracle Access Management Console. |
Same passphrase for each Webgate and OAM Server instance. |
Different passphrase for each Webgate and OAM Server instance. |
N/A |
|
The certificate request for the Webgate generates the certificate request file, which you must send to a root CA that is trusted by the OAM Sever. The root CA returns the Webgate certificates, which can then be installed either during or after Webgate installation. |
cacert.pem The certificate request, signed by the Oracle-provided openSSL Certificate Authority |
aaa_req.pem The certificate request, signed by the your Certificate Authority |
N/A |
|
Encrypt the private key using the DES Algorithm. For example: openssl rsa -in aaa_key.pem -passin pass: -out aaa_key.pem -passout pass: passphrase -des |
N/A |
X |
N/A |
|
Agent Key Password |
N/A |
Enter a password during agent registration in Cert Security mode (see Table 15-1). |
N/A |
|
During Agent registration, ObAccessClient.xml is generated in: $DOMAIN_HOME/output/$Agent_Name/ |
ObAccessClient.xml Copy to:
|
ObAccessClient.xml Copy to:
|
ObAccessClient.xml Copy to:
|
|
During Agent registration, password.xml is generated in: $DOMAIN_HOME/output/$Agent_Name/ See Also: Securing Communication |
password.xml Copy to:
|
password.xml Copy to:
|
N/A |
|
During Agent registration, aaa_key.pem is generated in: $DOMAIN_HOME/output/$Agent_Name/ See Also: Securing Communication |
aaa_key.pem Copy to:
|
aaa_key.pem Copy to:
|
N/A |
13.5.2 Configuration Settings of Common OAM Proxy Page for Secure Server Communications
You can the configure settings of Common OAM Proxy Page for Secure Server Communications.
Table 13-7 describes the settings required for Simple or Cert mode configurations.
Table 13-7 Server Common OAM Proxy Secure Communication Settings
| Mode | Description |
|---|---|
|
Simple Mode Configuration |
The global passphrase for communication using OAM-signed X.509 certificates. This is set during initial OAM Server installation. Administrators can edit this passphrase and then reconfigure all existing OAM Agents to use it, as described in"Viewing or Editing Simple or Cert Settings for OAM Proxy". |
|
Cert Mode Configuration |
Details required for the Key KEYSTOREStore where the Cert mode X.509 certificates signed by an outside Certificate Authority reside:
Note: These are set during initial OAM Server installation. The certificates can be imported using the import certificate utility or the keytool shipped with JDK. Administrators can edit the alias and password and then reconfigure all existing OAM Agents to use them, as described in"Viewing or Editing Simple or Cert Settings for OAM Proxy". |
13.5.3 Viewing or Editing Simple or Cert Settings for OAM Proxy
Administrators can use view or edit Simple or Cert mode settings for the common OAM Proxy.
To view or edit:
13.5.4 Configuring 64-bit WebGate in Cert Mode
64-bit WebGates now support SHA2 (256,384 & 512 bit) certificates.
Run the following command to configure a 64-bit WebGate in cert mode.
<Oracle Middleware Home>/oracle_common/bin/orapki wallet add -wallet $DOMAIN_HOME/output/$Agent_Name/cwallet.sso -trusted_cert -cert <Root CA path .i.e. aaa_chain.pem> -auto_login_only
13.5.5 Tuning the Simple Mode WebGate
If using a simple mode WebGate, you can improve the response time of the OAM login page by changing the aaaTimeoutThreshold time parameter in the WebGate profile from -1 to 10.
For detailed information about the AAA Timeout Threshold configuration element, see Table 15-3 in Registering and Managing OAM Agents.
13.6 Managing Run Time Policy Evaluation Caches
Access Manager common run time policy evaluation cache settings are managed by administrators and policy evaluation caches are required during policy evaluation at run time.
This section describes the following topics:
See Also:
13.6.1 Settings for Run Time Policy Evaluation Caches
The Resource Matching Cache and the Authorization Result Cache are set and required during policy evaluation at run time.
Figure 13-4 illustrates the Policy section of the Access Manager Settings page.
Figure 13-4 Common Policy Evaluation Caches
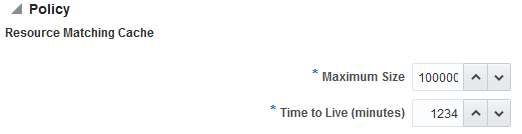
Description of "Figure 13-4 Common Policy Evaluation Caches"
Table 13-8 outlines these global settings that apply to all servers and requests.
Table 13-8 Policy Evaluation Caches
| Element | Description |
|---|---|
|
Resource Matching Cache |
Caches mappings between the requested URL and the policy holding the resource pattern that applies to the URL. Default Values:
|
|
Authorization Result Cache |
Caches policy decisions for the requested URL and user. Default Values:
See Also: Tuning Performance |
13.6.2 Managing Run Time Policy Evaluation Caches
Administrators manage the Access Manager common run time policy evaluation cache settings.
- In the Oracle Access Management Console, click Configuration at the top of the window.
- In the Configuration console, select Access Manager from the View menu in the Settings section.
- Expand the Policy section.
- Resource Matching Cache: Specify details and click apply (Table 13-8).
- Authorization Result Cache: Specify details and click apply (Table 13-8).
- Click Apply to submit the changes and dismiss the Confirmation window (or close the page without applying changes).
See Also:
-
High Availability Guide
-
Tuning Performance
