24 Using Password Policy
This chapter contains details on these forms and how to configure a password policy.
24.1 Understanding Password Management
The Password Management feature is only supported when the identity store used is an LDAP directory.
When enabled, Password Management can be used for the following scenarios.
-
When a user account is disabled by an administrator, the user is not allowed to enter the system. An appropriate error message is displayed if the user requests access.
-
When a user account is locked by an administrator (whether permanently or temporarily due to incorrect passwords or challenges), the user is not allowed to enter the system. An appropriate error message is displayed if the user requests access.
-
A user can be forced by the administrator to change a password if specific values are set in the user's LDAP entry.
-
When a user has to change a soon-to-be expiring password, a screen is displayed from which the user can choose one of the following options: change the password now or continue to the requested page without changing the password.
-
If a user submits a password with invalid characters during a password reset operation, an error message can be displayed with the password creation rules that the user must follow.
Oracle-Provided Password Forms has screenshots of the error messages discussed.
Caveats for Integrated Deployments
When you are using Oracle Identity Management and Oracle Access Management with Oracle Internet Directory, there are two sets of password policy definitions and enforcement. Password Policy Definition can be configured in both Oracle Identity Management and in Oracle Internet Directory. Password Policy Enforcement occurs according to the following:
-
Oracle Access Management enforces state policies (incorrect password, for example) during Web access; Oracle Internet Directory enforces its own state policies as well as LDAP operations (bind and compare, for example).
-
Oracle Identity Management enforces value policies (characteristics of the password) during user creation of the password update; Oracle Internet Directory enforces it's own value policies as well for policies for LDAP operations (add, modify for example).
Password Policy is only certified when the configured Identity Store is an LDAP directory. It is not certified with a virtualized LDAP directory (for example, Oracle Virtual Directory fronting another data repository) or a non LDAP directory
Any LDAP directory (such as Oracle Internet Directory) has a way to configure password policies that define lexical constraints to which the user password must conform (minimum characters, maximum length of time the password is valid, use of special characters, etc.) This password policy gets applied when the user's password is changed in the LDAP directory. To make sure that this LDAP directory password policy does not conflict with the password policy configured in OAM, the administrator has to manually study the LDAP password policy and do one of the following.
-
Make the backend LDAP identity store policies weaker or the same strength as the Oracle Identity Management and Oracle Access Management policies. However, this leads to a double enforcement.
-
Disable native LDAP password policy validation, which unfortunately leaves no enforcement for direct LDAP operations.
24.2 Enabling Password Management
Use the Oracle Access Management Console to enable the Password Management service. This is done as a configuration of the defined user identity store.
Table 24-1 Password Policy Configuration Parameters
| Parameter | Description |
|---|---|
|
Enable Password Management |
Enables password management for this identity store. If password management is not
enabled, the password plugin returns right away and the status
is not captured.
Note: Ensure Password Management is enabled before you use the Multifactor authentication OTP REST APIs. If Password Mangement is not enabled, the null pointer exception occurs:Exception occurred
while resetting password using OTP for user with
exception
java.lang.NullPointerException |
|
Use Oblix Schema |
If checked, the Oblix schema is used. If not, the Oracle Schema is used. |
|
Global Common ID Attribute |
This is the userid attribute used for password policy verification to make sure the password doesn't contain the user id attribute value. |
|
First Name Attribute |
This is the first name attribute used for password policy verification to make sure the password doesn't contain the first name attribute value. |
|
Last Name Attribute |
This is the last name attribute used for password policy verification to make sure the password doesn't contain the last name attribute value. |
|
Email Address Attribute |
This is the email attribute of the users in this identity store. It is used for password policy verification. |
Note: Password Management Module replaces the deprecated Password Policy Validation Module.
24.3 Accessing Password Policy Configuration Page
Once Password Management is enabled, you can configure the Password Policy. Administrators define password policy based on enterprise requirements. When configured, the Password Options and Challenge Options are used by both the Embedded Credential Collector (ECC) and Detached Credential Collector (DCC).
See Understanding Credential Collection and Login for information on the Credential Collection options.
Follow this procedure to access the Password Policy configuration page.
- Log in to the Oracle Access Management Console as Administrator.
- Click Application Security at the top right of the Oracle Access Management Console.
- Click Password Policy in the Application Security console. For detailed information about the options see, Password Policy Configuration Page.
24.3.1 Password Policy Configuration Page
Various options are available on the password policy configuration page.
Figure 24-1 Password Policy Configuration Page
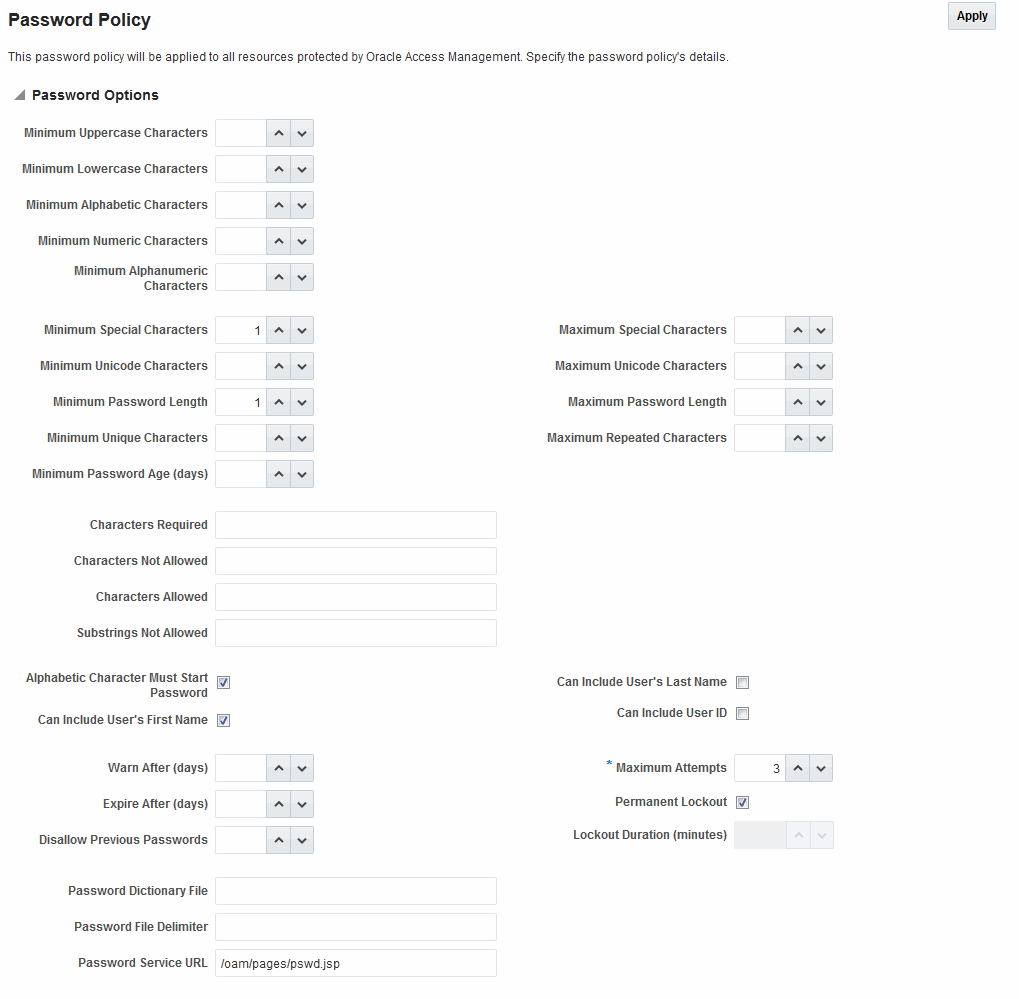
Description of "Figure 24-1 Password Policy Configuration Page"
Note: Use Password Policy Configuration page to configure only Global Password Policies. Multiple Password Policies can be configured using REST APIs. See REST API for Password Management in Oracle Access Manager
Table 24-2 describes the configurable Password Policy options (as read from left to right in the console). These elements are used by both the ECC and DCC.
Table 24-2 Password Policy Elements
| Element | Description |
|---|---|
|
Minimum Uppercase Characters |
Defines the minimum number of uppercase characters required in a password. |
|
Minimum Lowercase Characters |
Sets the minimum number of lowercase characters required in a password. |
|
Minimum Alphabetic Characters |
Defines the minimum number of special characters allowed in the password. |
|
Minimum Numeric Characters |
Sets the minimum number of numeric characters required in a password. |
|
Minimum Alphanumeric Characters |
Defines the minimum number of alphanumeric characters required in a password. |
|
Minimum Special Characters |
Sets the minimum number of special characters required in a password. |
|
Maximum Special Characters |
Defines the maximum number of special characters allowed in a password. |
|
Minimum Unicode Characters |
Defines the minimum number of unicode characters required in a password. |
|
Maximum Unicode Characters |
Sets the maximum number of unicode characters allowed in a password. |
|
Minimum Password Length |
Sets the total minimum number of characters required in a password. |
|
Maximum Password Length |
Defines the total maximum number of characters allowed in a password. |
|
Characters Required |
Defines the specific characters that are required in a password. No delimiter is needed or allowed in this definition. |
|
Characters Not Allowed |
Sets the specific characters that cannot be used in a password. No delimiter is needed or allowed in this definition |
|
Characters Allowed |
Defines all allowed characters in a password. No delimiter is needed or allowed in this definition |
|
Substrings Not Allowed |
Specific character strings that are not allowed in a password. Use a comma as the delimiter in this definition. |
|
Alphabetic Character Must Start Password |
Specifies that the first character in a password must be alphabetic, when checked. |
|
Can Include User's Last Name |
Specifies that the user's last name is allowed in the password, when checked. |
|
Can Include User's First Name |
Specifies that the user's first name is allowed in the password, when checked. |
|
Can Include User ID |
Specifies that the user's userID is allowed in the password, when checked. |
|
Warn after (days) |
Defines the number of days before a designated date in which a user will be warned about password expiration. For example, you enter 30 in the Expires After (Days) field, and 20 in the Warn After (Days) field, and the password is created on November 1. On November 21, the user will be informed that the password will expire on December 1. This field accepts values from 0 to 999. |
|
Maximum Attempts |
Identifies the maximum number of login attempts a user can make before a lockout. |
|
Expire after (days) |
Defines the period of time (in days) that the password is valid. |
|
Lockout Duration (minutes) |
Identifies the period of time the user is locked out (in minutes) after the designated number of failed login attempts. After this period, the user can attempt a fresh login. |
|
Permanent Lockout |
specifies permanent lockout after the designated number of failed login attempts. |
|
Disallow Last |
Defines the number of previous passwords that cannot be used when the user changes her password. |
|
Password Dictionary File |
Identifies the physical file on OAM Servers that contain the list of restricted words that can not be specified in a password. |
|
Password File Delimiter |
Defines the delimiter used in the Password Dictionary file to separate various words. For example, if the file contains |
|
Password Service URL |
Note: The Password Service URL is deprecated and works only when used with Password Policy Validation authentication module which is deprecated. To configure different pages for ECC/DCC as well as custom pages for Password Management Module, please use the URL_REDIRECT field to set appropriate page |
24.4 Specifying Credential Collector URLs with Password Policy
Regardless of the credential collection method, you can configure one global password policy that applies to all Access Manager-protected resources (using the Password Policy Validation Module in the authentication scheme).
The relevant URLs for the credential collector and related forms must be specified as outlined in Table 24-3.
Table 24-3 Specifying Credential Collectors and Related Forms for Authentication
| In the . . . | For the ECC . . . | For the DCC . . . |
|---|---|---|
|
OAM Agent Registration DCC Only |
N/A. |
Check the box beside Allow Management Operations in the OAM Agent registration page. See Also: "Enabling DCC Credential Operations" |
|
login, error, and password pages |
Pages where the user enters credentials arrive out of the box on the OAM Server and require no additional settings or changes.
|
Dynamic pages for general login/logout and password policy with the DCC are excluded automatically through the OHS See WebGate host directories
Perl Scripts for DCC-based Login and Logout The path name of the Perl executable must be updated in Oracle-provided Perl scripts on the WebGate host See Also: Table 22-4 |
|
Password Policy, Password Service URL |
The Default/ECC password page is used automatically: Password Service URL for ECC: See Also: "Defining Your Global Password Policy" |
Enter the DCC password page: Password Service URL for DCC: See Also: "Locating and Updating DCC Forms for Password Policy" |
|
User Identity Store |
The user data object definition in the Access Manager schema is extended with attributes that enable password user status and password history maintenance. This definition is provided in an LDIF file, and must be added to each user identity store using the |
Same for both DCC and ECC: See Also: |
|
Password Management Module |
Enter the Default Store as the KEY_IDSTORE_REF for each of the three plug-ins / steps (with an Error redirect on Failure): See Also: |
Same for both DCC and ECC: |
|
Authentication Scheme, Challenge Redirect URL |
Enter the Credential Collector host:
See Also: "Configuring the PasswordPolicyValidationScheme" |
Enter the Credential Collector host:
See Also: "Configuring the PasswordPolicyValidationScheme" |
|
Authentication Scheme, Challenge URL |
Enter the Credential Collector login form relative URI:
See Also: "Configuring the PasswordPolicyValidationScheme" |
Enter the Credential Collector login form relative URI:
See Also: "Configuring the PasswordPolicyValidationScheme" |
|
Authentication Scheme, Challenge Parameters |
ECC: User-defined Challenge Parameters:
See Also: |
DCC: User-defined Challenge Parameters:
See Also: |
|
Server Error Mode |
Same for both DCC and ECC. See: "Setting the Error Message Mode for Password Policy Messages" |
Same for both DCC and ECC. See: "Setting the Error Message Mode for Password Policy Messages" |
|
Authentication Policy |
Credential collectors in authentication policies:
See Also: "Adding Your PasswordPolicyValidationScheme to ECC Authentication Policy" |
Credential collectors in Authentication Policies: DCC Separate from Resource Webgate:
See Also: "Adding PasswordPolicyValidationScheme to Authentication Policy for DCC" |
|
Logout Configuration |
ECC: In the protecting (Resource) Webgate Agent registration, configure the |
DCC:
See "Configuring Logout When Using Detached Credential Collector-Enabled WebGate" |
24.5 Oracle-Provided Password Forms
Access Manager provides several pages for user interactions during credential collection. The location can be customized, depending on the desired topology of the authentication scheme being developed.
The Credential Collectors password pages are described in Table 24-4.
Table 24-4 Credential Collector Password Pages
| Credential Collector | Description |
|---|---|
|
ECC pages |
The default embedded credential collector jsp forms, by default, reside on the OAM Servers.
|
|
DCC pages |
Dynamic pages general login/logout and password policy with the DCC are excluded automatically through the OHS httpd.conf/webgate.conf file--you do not need to configure a policy to exclude these. See the Webgate host:
See Also: For details about customizing pages and messages, see the Developing Applications with Oracle Access Management. |
Table 24-5 shows the password forms provided. The default pages can be customized for your enterprise, or replaced entirely with custom pages. For example, you can design, implement, and deploy a custom page that displays a different version of the login form for a mobile browser than is used for a desktop browser.
Table 24-5 Password Management Forms and Functions
| Form | Function |
|---|---|
|
Sign In Form |
The standard login form provides fields for userID and password. Clicking the Login button initiates authentication processing governed by the configured authentication module. See: Developing Applications with Oracle Access Management for details about customizing login forms. |
|
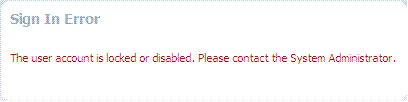
Sign In Error |
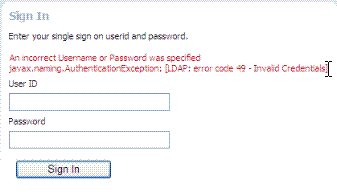
This standard login form appears when an error occurs. The text in red identifies the errors, which can be suppressed or displayed. See: Developing Applications with Oracle Access Management for details about suppressing or displaying. |
|
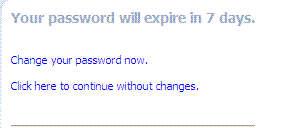
Password Expiry Notification |
The following message appears to inform the user that her password will expire, based on the notification policy. |
|
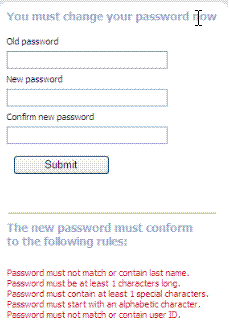
Change Password Form |
Based on password expiration policy configuration, the following window appears to enforce the policy and require user to change his password. |
|
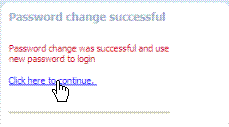
Password Change Success |
The following message appears to confirm the password change was successful. |
|
Locked or Disabled User Account |
Based on the password policy, user account lockout occurs when supplied credentials fail during the maximum allowed login attempts. |
24.6 Managing Global Password Policy
Regardless of whether you choose the ECC or DCC, you can configure a global password policy that applies to all Access Manager-protected resources. In addition, multiple password policies are also supported with configuration changes.
Authentication involves determining which credentials a user must supply when requesting access to a resource, gathering credentials, and returning a response that is based on the results of credential validation. Access Manager authentication processing relies on an authentication module (or plug-in) to define the rules governing requirements and transmission of information to the back-end authentication scheme. By default, Access Manager supports using the OAM Server Embedded Credential Collector (ECC) for authentication processing. However, you can also configure an OAM WebGate to use as an detached credential collector (DCC) instead.
Note:
Both the ECC and DCC facilitate multi-step authentication flows where credentials are not provided all at once. This increases the flexibility of interaction with users or programmatic entities for the purpose of collecting authentication-related information. For more information, see Orchestrating Multi-Step Authentication with Plug-in Based Modules.
The following overview provides links to topics that describe how to configure and use the password policy. Unless explicitly stated, all tasks apply equally to the ECC and DCC. Skip any tasks that do not apply to your deployment.
Password policy management includes
24.6.1 Defining Your Global Password Policy
Users with Oracle Access Management Administrator credentials can define a common password policy based on enterprise-defined requirements.
Note:
The only difference between a global password policy for the ECC versus the DCC is Password Service URL, which is credential collector-specific and defaults to ECC pages as shown in Step 2.
The specifications in this example are for illustration only. Your environment will be different.
24.6.2 Designating the Default Store for Your Password Policy
The Password Policy operates only with the designated Default Store. Administrator roles and credentials must reside in the System Store.
See Also:
-
In the Oracle Access Management Console, click Configuration at the top of the window.
-
In the Configuration console, click User Identity Stores.
-
Set the System Store: Administrator roles and credentials must reside in this store.
-
Open the page of the store to designate as the System Store.
-
Check Set as system store (for domain wide authentication and authorization operations).
-
Click Apply.
-
Add Administrators: See "Managing Administrator Roles".
-
Authentication Module: Set the LDAP Authentication Module used by the
OAMAdminConsoleScheme(authentication scheme) to use this System Store. -
Configure one or more authentication plug-ins to use this store, as described in "Orchestrating Multi-Step Authentication with Plug-in Based Modules".
-
-
Set Default Store: This store is required for Password Policy and migration when patching.
-
Open the page of the store to designate as the Default Store.
-
Check the box beside Set as default store.
-
Authentication Module: Locate
OAMAdminConsoleSchemeand confirm that the LDAP module does not refer to this store. See "Managing Native Authentication Modules". -
Authorization Policy Conditions: Choose the desired user identity store when setting Identity Conditions in Authorization Policies. See "Defining Authorization Policy Conditions".
-
-
Close the registration page.
24.6.3 Adding Key Password Attributes to the Default Store
The Password Policy operates only with the designated Default Store.
This section provides steps for extending the default store schema for Oracle Access Management password policy operations.
24.6.3.1 LDIF Files and Key Password Attributes for Password Policy
The LDIF (Lightweight Directory Interchange Format) files distributed as part of Access Manager are meant to extend the schema with required object classes. Generally, these are applied using the Access Manager and Oracle Identity Management wiring has been performed manually. The user data object definition in the Access Manager schema is extended with attributes that enable password user status and password history maintenance. This definition is provided in an LDIF file, and must be added to each user identity store using the ldapadd tool.
Oracle-provided LDIFs are identified in Table 24-6.
Note:
OAM_HOME contains installed files necessary to host Oracle Access Management. OAM_HOME resides within the directory structure of the Middleware home ($MW_HOME).
Table 24-6 Location of Oracle-provided LDIFs for LDAP Providers
| LDAP Provider | LDIF Location |
|---|---|
|
OID: Oracle Internet Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/OID_PWDPersonSchema.ldif |
|
OVD: Oracle Virtual Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/OVD_PWDPersonSchema.ldif |
|
AD: Microsoft Active Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/AD_PWDPersonSchema.ldif |
|
SJS: sun Java System Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/IPLANET_PWDPersonSchema.ldif |
|
eDirectory: Novell eDirectory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/EDIR_PWDPersonSchema.ldif |
|
ODSEE: Oracle Directory Server Enterprise Edition |
$OAM_ORACLE_HOME/server/pswdservice/ldif/IPLANET_PWDPersonSchema.ldif |
|
OUD: Oracle Unified Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/OUD_PWDPersonSchema.ldif |
|
SLAPD: OpenLDAP Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/OLDAP_PWDPersonSchema.ldif |
|
IBM: OBM Tivoli Directory |
$OAM_ORACLE_HOME/server/pswdservice/ldif/TIVOLI_PWDPersonSchema.ldif |
Note:
The above ldif files extension for userid stores are required only when using Password Policy Validation Module. Password Policy Validation Module is deprecated and may not be available in future releases. Instead Password Management Module which handles same functionality with new features such as multiple password policies, password reset with OTP and various modes are available. Please refer, Table 24-9 to extend the directory for Password Management Service.
The attributes that enable password user status and password history maintenance are shown in Table 24-7. The user data object of each user identity store must include the attributes shown in Table 24-7. These can be added with the ldapadd tool, LDIF (Lightweight Directory Interchange Format) file.
Table 24-7 Key Password Attributes in a Password Policy
| Attribute | Description | Format and Values |
|---|---|---|
|
obPasswordCreationDate |
The date and time used to calculate (at the time of user login) whether the password has expired and whether a warning needs to be issued. |
YYYY-MM-DDThh:mm:ssZ |
|
obPasswordHistory |
Used to track the number of last passwords used. Access Manager understands 12c oblixPersonPwdPolicy format and changes it to new format. |
New format: Previous format:
|
|
obPasswordChangeFlag |
Used during forced password change for first time user login (or forced password change initiated by the Administrator). Note: Forced password change is administered using REST API’s. Administrator can invoke these Rest API’s. See, Rest API for Password Management in Oracle Access Manager |
Boolean string value.
Empty string represents |
|
obuseraccountcontrol |
Used to represent a disabled user. |
Non-encrypted string value.
Empty string represents "activated". |
|
obpasswordexpirydate |
The time after which the user password is considered to be expired. |
YYYY-MM-DDThh:mm:ssZ Empty value represents |
|
obLockoutTime |
The time up to which the user is considered to be locked out due to too many login attempts. |
Epoch value (in seconds) representing time in the future.
|
|
obLoginTrvCount |
The number of consecutive login failures by the user. This counter is reset on the first correct password entry. |
Non-encrypted integer value.
|
|
oblastsuccessfullogin |
The time of the last successful login. |
YYYY-MM-DDThh:mm:ssZ |
|
oblastfailedlogin |
The time of the last failed login. |
YYYY-MM-DDThh:mm:ssZ |
24.6.3.2 Extending the Default Store Schema with Password Policy Attributes
idmConfigTool -prepareIDStore. If your user identity store has not been extended with the oblix schema, you must update the schema to include the object classes required by the password service. LDAP tools should be run from the /bin directory beneath $OAM_HOME. The following procedure illustrates extending the Oracle Internet Directory schema. Your environment might be different.
24.6.4 Adding an Administrator to Change User Attributes After a Password Change
You can modify the Default Store (Oracle Internet Directory in this example) to use a different privileged account as the Bind DN. This enables sufficient privileges to change user attributes after a password change.
Prerequisites
Register a supported LDAP store and designate it as the Default Store. Ensure that the user you add is defined within the Default Store.
See Also:
-
In the Oracle Access Management Console, click Configuration at the top of the window.
-
In the Configuration console, click Administration.
-
Add a New Administrator:
-
In the Administration page, click Grant.
-
In the dialog that appears, click Search.
-
Select the desired role from the Roles drop-down list and click Add Selected to grant it to the selected user.
-
Click Apply to submit the changes.
-
-
Proceed with "Configuring Password Policy Authentication".
24.7 Configuring Password Policy Authentication
After preparing your password policy, Default Store, and Administrator, you can develop your authentication module and scheme.
-
Adding Your PasswordPolicyValidationScheme to ECC Authentication Policy—If you are using the DCC, skip this topic and go to "Configuring OAM WebGate and Authentication Policy for DCC"
-
Supporting DCC Authentication Schemes with Pre-Authentication Rules
24.7.1 Password Policy Validation Module
You must also configure the Password Policy Validation Authentication Module to use the Default Store.
Note:
There are no credential collector dependencies when defining the Password Policy Validation Module for authentication.
Password Policy Validation Module is deprecated and is replaced using Password Policy Management Module. See Configuring Password Policy Management Module.
A sample module is shown in Figure 24-2. The User Password Status Step is the unique step that relies on the UserPasswordPolicyPlugin.
Note:
UserPasswordPolicyPlugin is supported only when using LDAP based authentication modules. It does not work with non LDAP authentication modules.
Figure 24-2 Password Policy Validation Authentication Module with Orchestrated Plug-ins
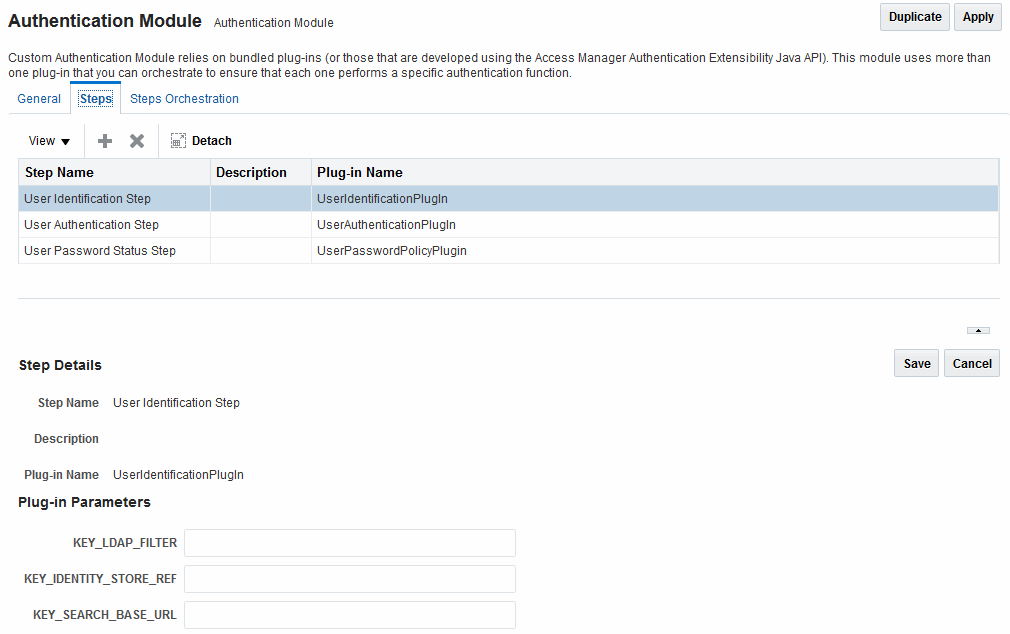
Description of "Figure 24-2 Password Policy Validation Authentication Module with Orchestrated Plug-ins"
Each step identifies the action provided by a specific named plug-in.
Figure 24-3 shows the orchestration of steps within the authentication module. For more information on modules and steps, see "Pre-populated Plug-ins for Configuring Access Manager with Multi-Step Authentication".
Figure 24-3 Step Orchestration for Password Policy Validation Module
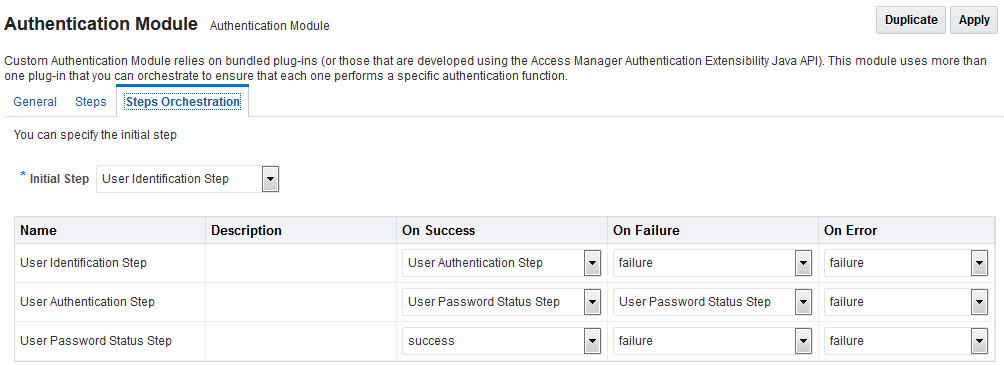
Description of "Figure 24-3 Step Orchestration for Password Policy Validation Module"
Table 24-8 describes the Password Policy Validation module step details that you specify.
Table 24-8 User Password Step Details
| Step Name | Step Details | Description |
|---|---|---|
|
User Identification Step |
KEY_LDAP_FILTER |
Add the LDAP filter to the KEY_LDAP_FILTER attribute. Only standard LDAP attributes can be used when defining an LDAP search filter. For example: (uid={KEY_USERNAME})
See Also: Table 25-15 and your vendor documentation for the exact syntax for your identity store |
|
User Identification Step |
KEY_IDENTITY_STORE_REF |
The name of the registered Identity Store containing the module users. Default: The registered Default Store. |
|
User Identification Step |
KEY_SEARCH_BASE_URL |
Base URL for user searches. For example: dc=us,dc=example,dc=com |
|
User Authentication Step |
KEY_IDENTITY_STORE_REF |
The name of the registered Identity Store containing the module users. Default: The registered Default Store. |
|
User Authentication Step |
KEY_PROP_AUTHN_EXCEPTION |
Enable or disable the propagation of LDAP errors. "KEY_PROP_AUTHN_EXCEPTION" needs to be set to TRUE when the Authentication module has "Password Policy Plugin" as the next step of plugin execution; for example, when the module has Authentication Plugin ->Password Plugin, change this parameter to TRUE. |
|
User Password Status Step |
PLUGIN_EXECUTION_MODE |
The execution mode of plug-in. Depending upon the configuration, this plug-in can operate either alone or with other default plug-ins. Values are one of the following:
Default: PSWDONLY |
|
User Password Status Step |
OBJECTCLASS_EXTENSION_SUPPORTED |
The object classes "oblixpersonpwdpolicy" and "oblixorgperson" are required to be present in the OAM user's entry for successful execution of this plugin. If this parameter is FALSE, the plugin will not add these object classes. If this parameter is TRUE, the plugin will try to add these object classes to the user's entry if the current user's entry does not already have them present. Default: FALSE |
|
User Password Status Step |
KEY_IDENTITY_STORE_REF |
The name of the registered Identity Store containing the module users. Default: The registered Default Store. |
|
User Password Status Step |
NEW_USERPSWD_BEHAVIOR |
Configures retroactive behavior of the new-user password-policy. Values are either:
Default: NOFORCEPASSWORDCHANGE |
|
User Password Status Step |
URL_ACTION |
The type of servlet action needed for redirecting the user to the specific password page for expiry and warning pages. Values can be either:
Default: REDIRECT_POST |
|
User Password Status Step |
DISABLED_STATUS_SUPPORT |
Specifies whether the disabled status is to be supported and acted upon in this password service. Valid values are either True or False. Default: TRUE |
Prerequisites
Defining Your Global Password Policy
Note:
There are no credential collector dependencies when defining the Password Policy Validation Module. Enter the Default Store as the KEY_IDSTORE_REF for each of the three plug-ins (with an Error redirect on Failure).
-
In the Oracle Access Management Console, click Application Security at the top of the window.
-
In the Application Security console, click Authentication Modules. in the Plug-ins section.
-
In the Authentication Modules page, click Search, then click Password Policy Authentication Module.
-
Select the Steps tab; for each of the three steps add the Default Store name in the field beside KEY_IDSTORE_REF (Save after each change). For example:
-
User Identification Step
KEY_IDSTORE_REF: OID
Save.
-
User Authentication Step
KEY_IDSTORE_REF: OID
Save.
-
User Password Status Step
KEY_IDSTORE_REF: OID
Save.
-
-
Click Apply.
-
Proceed to "Configuring the PasswordPolicyValidationScheme".
24.7.2 Configuring the PasswordPolicyValidationScheme
Users with Administrator credentials can configure the PasswordPolicyValidationScheme.
You can have multiple authentication schemes for use with the global password policy.
Note:
-
Multiple password policy feature
-
Forgot password using OTP
-
Changing user status using REST API
Differences between values for the ECC versus the DCC include (Table 24-3):
-
Challenge Redirect URL: Credential Collector host and port
-
Challenge URL: Credential Collector Pages
-
Challenge Parameters: Table 22-21
Prerequisites
Password Policy Validation Module
See Also:
24.7.3 Adding Your PasswordPolicyValidationScheme to ECC Authentication Policy
A user with Administrative privileges can use the PasswordPolicyValidationScheme configured for the ECC in the application domain of the protecting Webgate (Resource Webgate).
Prerequisites
Configuring the PasswordPolicyValidationScheme
-
ECC: In the console, search for and open the appropriate Application Domain. (See "Searching for an Existing Application Domain").
-
ECC: Protect Resources using the PasswordPolicyValidationScheme:
-
Find and open your Protected Resource Policy on the Authentication Policies tab (see "Viewing or Editing an Authentication Policy"):
- Authentication Policies
- Protected Resource Policy
-
Select PasswordPolicyValidationScheme for the Protected Resource Policy (Authentication Scheme) and click Apply.
-
Finish updating your Authentication and Authorization policies, as desired (Managing Policies to Protect Resources and Enable SSO).
-
-
Proceed as needed for your environment:
24.7.4 Supporting DCC Authentication Schemes with Pre-Authentication Rules
Pre-authentication rules allow you to define a policy that can either block access to the user or allow OAM to use a different authentication scheme based on certain conditions.
The host parameter in the request data allows pre-authentication rules to be executed against the host name of a protected resource. When the request is originating from a DCC WebGate, the host parameter is unable to distinguish between internal and external URLs from different proxies. If you want the DCC WebGate to work with the proxy, you have to create a new pre-authentication rule as follows:
request.returnHost.lower().find('<proxy_host_name>')>0
The returnHost parameter has the proxy host name for internal and external URLs irrespective of whether the request is originated from a ECC or DCC WebGate. When you access the resource through the specified proxy, the authentication scheme is switched as specified in the new pre-authentication rule. In case of other configured proxy, the original authentication scheme specified in the Authentication Policy tab is retained.
24.8 Completing Password Policy Configuration
Administrators can set error mode for password policy messages, override native LDAP password policy validation, and perform evaluations to confirm the deployment is working as required.
These tasks are the same regardless of the credential collector you have configured. Perform the following tasks to complete your password policy configuration:
24.8.1 Setting the Error Message Mode for Password Policy Messages
Users with administrative privileges can set the Server Error Mode for password policy messages.
Figure 24-4shows the Access Manager settings.
Figure 24-4 Server Error Mode for Password Management

Description of "Figure 24-4 Server Error Mode for Password Management"
Prerequisites
- In the Oracle Access Management Console, click Configuration at the top of the window.
- In the Configuration console, select Access Manager from the Settings drop-down list.
- In the Load Balancing section, set the Server Error Mode to Internal.
- Click Apply.
- Proceed with "Overriding Native LDAP Password Policy Validation".
24.8.2 Overriding Native LDAP Password Policy Validation
You need to disable native LDAP password policy validation before the non-native password policy can be used.
For example, with Oracle Internet Directory registered for Oracle Access Management, native password policy is generally located as follows:
dn: cn=default,cn=pwdPolicies,cn=Common,cn=Products,cn=OracleContext,<DOMAIN_CONTAINER>
Caution:
Disabling the native LDAP password policy validation leaves no enforcement for direct LDAP operations. There are various password policies in Oracle Internet Directory, including one in the following:
dn: cn=default,cn=pwdPolicies,cn=Common,cn=Products,cn=OracleContext
However, this might not apply to your domain.
You can disable the Oracle Internet Directory password policy by setting the orclpwdpolicyenable parameter to zero (0).
See Also:
The various attributes described in Administering Oracle Internet Directory
The following procedure is only an example. Your environment will be different.
Prerequisites
24.8.3 Disabling ECC Operation and Using DCC Exclusively
Note:
After disabling the ECC, access to resources protected by schemes and policies that rely on the ECC will be prohibited, including access to the Oracle Access Management Console.
Prerequisites
24.8.4 Testing Your Multi-Step Authentication
You can perform a number of evaluations to confirm that your deployment is working properly.
-
Confirm access after login:
-
Open a new browser and request a resource.
-
Log in with your user credentials.
-
Confirm that you have access to the resource.
-
-
Confirm no access on incorrect login:
-
Open a new browser and request a resource.
-
Log in with incorrect user credentials.
-
Confirm that you must re-authenticate.
-
-
Confirm lockout after exceeding maximum incorrect login attempts:
-
Open a new browser and request a resource.
-
Log in with incorrect user credentials repeatedly.
-
Confirm that the user account is locked.
-
-
Modify and evaluate your password expiry policy:
-
Log in to the Oracle Access Management Console.
-
In your password policy, reset the expiry and lockout periods (Table 24-2) so that you will see warnings on your next login.
-
Save the policy updates.
-
Open a new browser and request a resource.
-
Verify the warning page appears advising that the password will expire.
-
Click the link to continue without password change.
-
-
Change your password:
-
Open a new browser and request a resource.
-
On the password expiry warning page, click the link to change your password.
-
On the password change page, enter your correct old password.
-
In the new password field, enter a different new password that does not follow the password policy and confirm the password validation error.
-
Enter a new password that meets requirements and confirm success and access to the resource.
-
24.9 Configuring the PasswordManagementPlugin
The Password Management policy plugin handles the password related flows during login. Configuring the Password Management policy plugin is the most critical step in making sure that OAM and OIG LDAP applications can work in tandem.
Using the Password Management plugin in OAM makes sure that password features act across both OAM and OIG in similar ways. This section contains the following information:
24.9.1 Configuring Password Policy for PasswordManagement Service
Note that the password policy in OAM should be in sync with that of OAM LDAP to work consistently between both products.
See Accessing Password Policy Configuration Page for details. It is up to the administrator to ensure that the policies are indeed the same and consistent.
24.9.2 Extending the LDAP Definitions
Depending on the type of the directory, add the required objectclass schema definitions so that the LDAP directory can use these to extend the user objectclass. The appropriate schema files are located in $IDM_HOME/modules/oracle.idm.ipf_11.1.2/scripts/ldap.
Table 24-9 documents the LDIF file to use with supported LDAP directories.
Table 24-9 Included LDIF Schema Files
| LDAP Directory | LDIF Schema File |
|---|---|
|
OID |
OID_OblixSchema.ldif, OID_OracleSchema.ldif |
|
AD |
AD_OblixSchema.ldif, AD_OracleSchema.ldif |
|
OUD |
OUD_OblixSchema.ldif, OUD_OracleSchema.ldif |
|
ODSEE |
IPLANET_OblixSchema.ldif, IPLANET_OracleSchema.ldif |
|
OPENLDAP |
OLDAP_OblixSchema.schema, OLDAP_OracleSchema.schema |
|
OVD |
OVD_OblixSchema.ldif, OVD_OracleSchema.ldif |
|
Tivoli |
TIVOLI_OblixSchema.ldif, TIVOLI_OracleSchema.ldif |
|
EDIR |
EDIR_OblixSchema.ldif, EDIR_OracleSchema.ldif |
24.9.3 Configuring Password Policy Management Module
You must configure the Password Policy Management Module to configure the store that you want to be protected by Password Policy Management Module.
Note:
There is no credential collector dependencies when defining the Password Policy Management Module for authentication.
Sample module is as shown in the Fig. below. The User Password Status Step is the unique step that relies on the PasswordManagementPlugin.
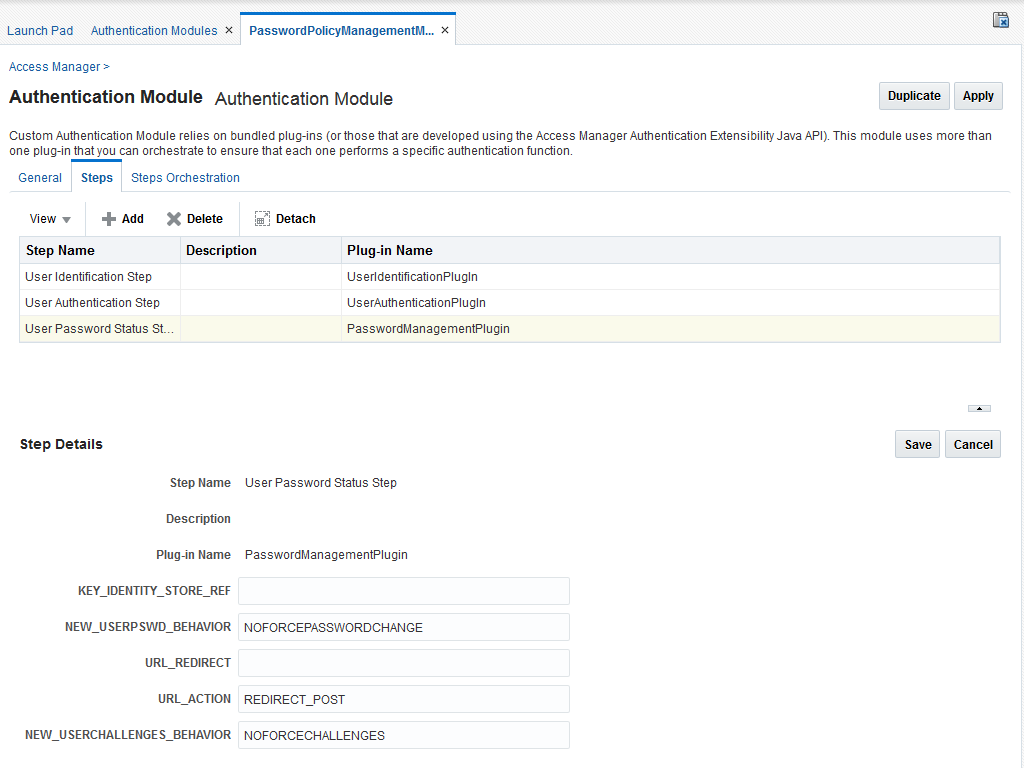
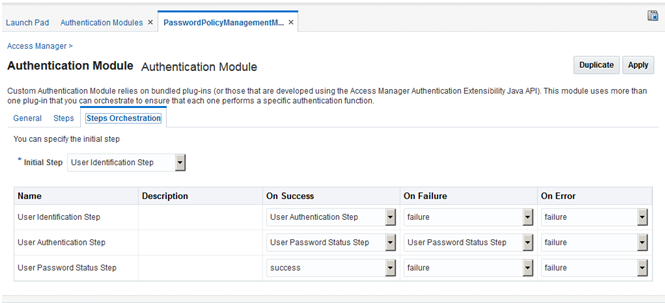
The following table describes the Password Policy Validation module step details that you should specify:
| Step Name | Step Details | Description |
|---|---|---|
|
User Identification Step |
|
Add the LDAP filter to the |
|
User Identification Step |
|
The name of the registered Identity Store containing the module users. Default: The registered Default Store. |
|
User Identification Step |
|
Base URL for user searches. For example: |
|
User Authentication Step |
|
The name of the registered Identity Store containing the module users. Default: The registered Default Store. |
|
User Authentication Step |
|
Enable or disable the propagation of LDAP errors. |
|
User Password Status Step |
|
The name of the registered Identity Store containing the module users. Default: The registered Default Store. |
|
User Password Status Step |
|
Configures retroactive behavior of the new-user password-policy. Values are either:
Default: NOFORCEPASSWORDCHANGE |
|
User Password Status Step |
|
The URL to Redirect the password pages. In case of DCC, the page needs to be specified as |
|
User Password Status Step |
|
The type of servlet action needed for redirecting the user to the specific password page for expiry and warning pages. Values can be either:
Deafult: REDIRECT_POST |
|
User Password Status Step |
|
Not supported. |
Note:
There is no credential collector dependencies when defining the Password Policy Management Module. Enter the Default Store as theKEY_IDSTORE_REF for each of the three plug-ins (with an Error redirect on Failure).
Password Policy Validation Module is deprecated and is replaced using Password Policy Management Module.
24.9.4 Setting up the Forgot Password Module
The forgot password feature in OAM can be accomplished using One Time Pin (OTP) generation and ChangePassword using OTP REST APIs.
The administrator can setup forgot password URL by following the procedure documented in Administering the Forgot Password URL.
OTP (One Time Pin) can be generated for a OAM user by using Adaptive Authentication Plugin. Once enabled, users can change their passwords using OTP and password change REST APIs through application which can orchestrate these REST calls.
The forgot password feature in OAM can be accomplished using One Time Pin (OTP) generation and ChangePassword using OTP REST APIs.
See also,
REST API for Password Management in Oracle Access Manager
REST API for OTP Forgot Password in Oracle Access Manager
The sample forgot password application can be downloaded from the OTN location. Please create a support request to get the forgot password sample application.
24.9.5 Configuring Forgot Password using OTP
The forgot password feature in OAM can be accomplished using One Time Pin (OTP) generation and ChangePassword using OTP Rest APIs. The following sections provide the setup steps required for enabling forgot password flow using OTP in OAM
Directory Setup
-
Create an OID profile in OAM, add the required
objectclasses()and add it as the default idstore in OAM. See Creating an Identity Directory Service Profile for more information on creating an ID profile. -
Run the following command to add ldif files. See Extending the LDAP Definitions for more information.
ldapadd -D <DIRECTORY_USERNAME> -w <DIRECTORY_PASSWORD> -h <DIRECTORY_HOST_NAME> -p <DIRECTORY_PORT> -f $MW_HOME/idm/modules/oracle.idm.ipf_12.2.2/scripts/ldap/OID_OblixSchema.ldif ldapadd –D <DIRECTORY_USERNAME> -w <DIRECTORY_PASSWORD> -h <DIRECTORY_HOST_NAME> -p <DIRECTORY_PORT> -f $MW_HOME/idm/modules/oracle.idm.ipf_12.2.2/scripts/ldap/OID_OracleSchema.ldifNote:
Ensure that the LDAP directory has password management enabled.
Ensure that the LDAP profile is configured as the default store in the User Identity Stores
Setup Related to OTP Rest API
These steps are required to be able to use the OTP Rest service for creating and validating the OTP for users successfully.
-
Add otprestusergroup to OAM admin user in the LDAP directory.
In case of admin user being weblogic, add the privilege in embedded ldap in weblogic console. Add a group called otprestusergroup to groups and add weblogic user to this group.
-
Enable UMS in Adaptive Auth Plugin. See Configuring the Adaptive Authentication Plug-in in the Oracle Access Management Console
Note:
Ensure the settings UmsAvailable = true and UmsClientUrl = < has the relevant client url>Use the following WLST command line script to set the credentials for the Oracle User Messaging Service
cd <MW_HOME>/oracle_common/common/bin ./wlst.sh connect() createCred(map="OAM_CONFIG", key="umsKey", user="weblogic", password="welcome1")
Note:
For further information on OTP Rest APIs in OAM refer REST API for Multifactor Authentication One Time PIN in Oracle Access ManagerSetup for forgot password link on default login page
On the OAM console, Enable the Adaptive Authentication Service. This is a pre-requisite for enabling the OTP forgotpassword link on OAM login pages. For information on available services , See Available Services of the Common Configuration Section.
Use the following Rest API command with the relevant hostname:port to enable the OTP forgot password link on the default login page in OAM
curl -X PUT \
http://hostname:port/oam/services/rest/access/api/v1/config/otpforgotpassword/ \
-H 'authorization: Basic d2VibG9naWM6d2VsY29tZTE=' \
-H 'content-type: application/json' \
-d '{"displayOTPForgotPassworLink":"true","defaultOTPForgotPasswordLink":"false","localToOAMServer":"false","forgotPasswordURL": "http://hostname:port/otpfp/pages/fp.jsp", "mode":"userselectchallenge"}'
The following table describes the values for the mode parameter in the Curl command.
| Value | Description |
|---|---|
| OTP will be sent to the email configured in the mail field | |
| sms | OTP will be sent to the mobile number configured in the mobile field |
| userchoose | OTP will be sent by letting the user choose either mail or phone option, without exact values |
| userselectchallenge | User can see masked values either as mail or mobile and select one of the options |
Adding Rest admin credentials to CSF
Use the following WLST command to add the Rest admin credentials to the Credential Store Framework (CSF). The credential is required for accessing OAM Rest services.
cd <MW_HOME>/oracle_common/common/bin
./wlst.sh
connect()
createCred(map="OAM_CONFIG", key="oam_rest_cred", user="Adminusername", password="password")
Note:
The user and password are the Rest adminusername and password to connect to the Rest service.Once all the above steps are completed, the default login page also shows the OTP forgot password link that the user can click to change the forgotten password based on a one-time-pin and login to access the protected page thereafter.
24.10 Multiple Password Policies
Multiple Password policies facilitate user logons belonging to different groups in an organization ensuring the organization's security.
Multiple password policies is useful for setting up varied levels of password based complexity protections to users belonging to different groups.
The Multiple Password policies cannot be configured using OAM console in this release. It can be configured using REST API’ s only. The policy Admin users can invoke these REST API’s. See Rest API for Password Policy Management in Oracle Access Manager
Policies can be defined at different granularities and the priority of the password policy determines which password policy gets applied to the user. The different granularities being:
-
IDSTORE level
-
GROUP level
For example, while resolving the password policy for a user:
-
The list of password policies for the idstore that the user belongs to is retrieved.
-
The password policies are sorted by priority.
-
The applicable password policy with the highest priority is chosen for the user.
-
If the user has no specific password policy defined, then the default password policy is applied to that user.
Note: After any configuration change, you should wait for 60 seconds for the changes to reflect.
Resolving which password policy can be applied for the login user is done as part of the PasswordManagementPlugin via the PasswordPolicyManagementModule.
24.11 Using ESAPI and Validation Properties
In OAM 11g PS3, the OAM server read the
$DOMAIN_HOME/config/fmwconfig/ESAPI.properties and
$DOMAIN_HOME/config/fmwconfig/validation.properties if it
existed.
oracle.oam.esapi.resources java system property and
specifying the location of the files, as shown in the following
example:-Doracle.oam.esapi.resources=/scratch/esapiconfig/Tip:
You can add this parameter tosetDomainEnv.sh so that
it is set at startup. For example, see the following snippet from
setDomainEnv.sh
:EXTRA_JAVA_PROPERTIES="-Doracle.oam.esapi.resources=/oam/Middleware/user_proje
cts/domains/oam_domain/config/fmwconfig/esapi ${EXTRA_JAVA_PROPERTIES}"
export EXTRA_JAVA_PROPERTIES