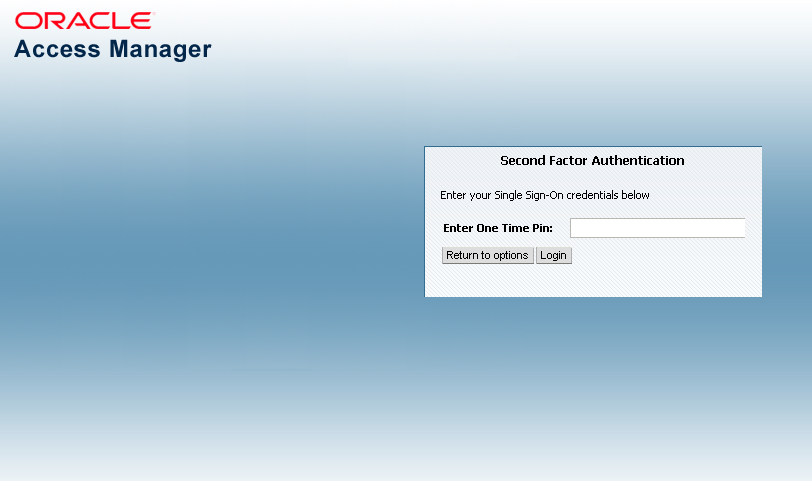
32 Introducing the Adaptive Authentication Service
The Adaptive Authentication Service offers stronger multifactor (also referred to as second factor) authentication for sensitive applications that require additional security in addition to the standard user name and password type authentication.
The following topics describe how the Adaptive Authentication Service and Access Manager Second Factor Authentication:
32.1 About Adaptive Authentication Service
The Adaptive Authentication Service offers the ability to add multiple steps to the authentication process.
Additional security may be enforced by adding a OTP step, or an Access Request (Push) Notification step after initial user authentication. This may or may not involve the use of the Oracle Mobile Authenticator, a mobile device app that uses Time-based One Time Password and push notifications to authenticate users within the second factor authentication scheme.
Note:
Installing Oracle Adaptive Access Manager is not required since the Adaptive Authentication Service uses a set of libraries that makes a OTP step feasible using the Oracle Mobile Authenticator.
The Adaptive Authentication Service has to be licensed and explicitly enabled in order to use it. Once the proper product license is procured you can enable the Adaptive Authentication Service using the Oracle Access Management Console. From the Oracle Access Management Console, the Adaptive Authentication Service can be enabled or disabled from the Available Services link on the Configuration Launch Pad.
32.2 Working with the Adaptive Authentication Service
The following options are available:
-
OTP from Oracle Mobile Authenticator
-
OTP through SMS
-
OTP through Email
-
Access Request Notification from Oracle Mobile Authenticator
Figure 32-1 shows the Second Factor Authentication page in which the user has selected the OTP Through Email option.
In this case, the user receives the OTP via a configured Email address.
Figure 32-1 Second Factor Authentication Preferred Method Page
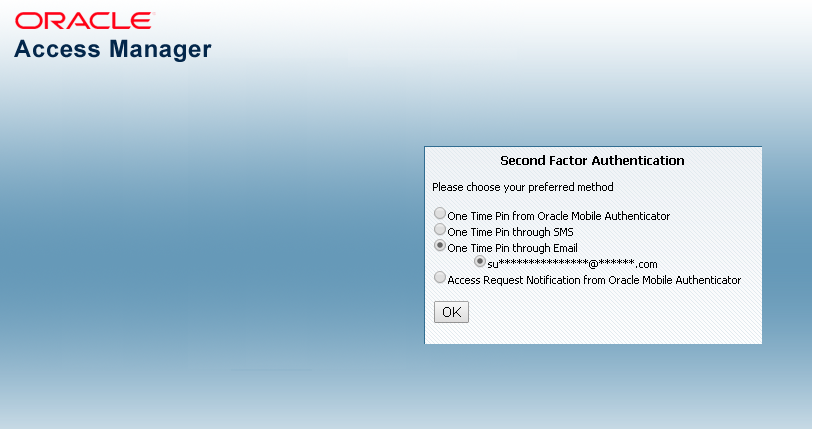
Description of "Figure 32-1 Second Factor Authentication Preferred Method Page"
If the selected option is either OTP From Oracle Mobile Authenticator or Access Request Notification from Oracle Mobile Authenticator, the Adaptive Authentication Service works in tandem with the Oracle Mobile Authenticator (OMA), a mobile device app that uses Time-based One Time Password and push notifications to authenticate users within the second factor authentication scheme.
In advance of using the OTP from OMA or Access Request Notification from OMA options, a user must download a supported authenticator app to a mobile device (for example, Oracle Mobile Authenticator to an Apple iPhone) and configure it by clicking a link provided by the Access Manager administrator. (The OMA app is not needed if using the OTP through Email or OTP through SMS options.)
Note:
You must configure the Oracle Mobile Authenticator mobile device app to retrieve a secret key required to generate a OTP.
See Generating a Secret Key for the Oracle Mobile Authenticator for information about the secret key.
See Understanding Oracle Mobile Authenticator Configuration for information on how to configure the OMA.
The following topics describe each option and how the Oracle Mobile Authenticator works:
32.2.1 Understanding the One Time Password Option
After the successful authentication of initial credentials, the user needs to choose one of the OTP options as a second-factor authentication. Access to the protected resource is provided when the OTP received by the user is entered in the OTP login page.
Let's assume the Adaptive Authentication Service is enabled and configured for second factor authentication. When the user accesses a resource protected by Access Manager, a page is displayed that requests a user name and password. If these initial credentials are authenticated successfully, a Second Factor Authentication Preferred Method Page page is displayed and the user selects from one of the options. In this use case, the user selects one of the OTP options and receives a OTP through SMS/Email or generated and displayed by the OMA app. The user enters the OTP in the OTP login page.
Figure 32-2 shows the OTP login page.
Once the OTP is successfully validated by Access Manager, the user is directed to the protected resource. On failure of any of the OTP options, an error message will be displayed, and the user will be returned to the same OTP page.
Note:
Access Manager validates the OTP using the Time-based One Time Password (TOTP) algorithm. TOTP is a two-factor authentication scheme specified by the Internet Engineering Task Force (IETF) under RFC 6238 and used by the Adaptive Authentication Service. TOTP is an extension of the HMAC-based One Time Password algorithm and supports a time-based moving factor (a value that must be changed each time a new password is generated).
The following topics describe how the user may receive the OTP:
32.2.1.1 About using OTP through Email or SMS
The user receives the OTP through an email or SMS and enters it in the OTP login page.
In cases where OTP through email or SMS is chosen, Access Manager will send a OTP to the configured email address or phone number respectively. The user then enters the received OTP and Access Manager will validate it. On a successful validation, the user will be directed to the protected resource.
The Adaptive Authentication Service expects that the required email address or phone number is configured in the appropriate field.
See Configuring the Adaptive Authentication Plug-in in the Oracle Access Management Console.
When you use the OTP with Email or SMS option, the OTP is accessible from any device on which the email address can be accessed or from the SMS app that is associated with the specified phone number, respectively.
Note:
The OMA mobile app is not used for the OTP through Email or OTP through SMS options.
32.2.1.2 About using OTP from Oracle Mobile Authenticator
In the use case where a OTP will be generated and displayed by the OMA app on a mobile device, the app must be configured with the Access Manager server details.
Following this configuration, the user authenticates with Access Manager using the proper credentials and Access Manager will return a secret key. This secret key is unique to each user and known only to Access Manager and the OMA. The secret key is used to generate the OTP.
See Generating a Secret Key for the Oracle Mobile Authenticator on how to populate the secret key with the required data.
After Access Manager generates a OTP for the user using the secret key, the OTP is pushed to the OMA. The user then enters the OTP in the One Time Pin Login Page. If the OTP generated by Access Manager matches the OTP entered by the user, access to the protected resource is allowed. If the OTP entries do not match, access is not allowed.
See Using the Oracle Mobile Authenticator with OTP And Access Request.
Note:
The OMA refreshes the OTP every 30 seconds so the OTP entered by a user is valid only for that period of time.
32.2.2 Understanding the Access Request (Push) Notification Option
The Access Manager sends an Access Request Notification to the notification server which is then pushed to the user’s configured device.
Let's assume the Adaptive Authentication Service is enabled and configured for second factor authentication. When the user accesses a resource protected by Access Manager, a page is displayed that requests a user name and password. If these initial credentials are authenticated successfully, a Second Factor Authentication Preferred Method page is displayed and the user selects from one of the options. In this use case, the user selects Access Request Notification from Oracle Mobile Authenticator.
Note:
This is a push notification option which works in tandem with the OMA.
See Using the Oracle Mobile Authenticator with OTP And Access Request.
Figure 32-3 shows the Second Factor Authentication Preferred Method Page with Access Request Notification that has been selected.
Figure 32-3 Access Request Notification Preferred Method Page
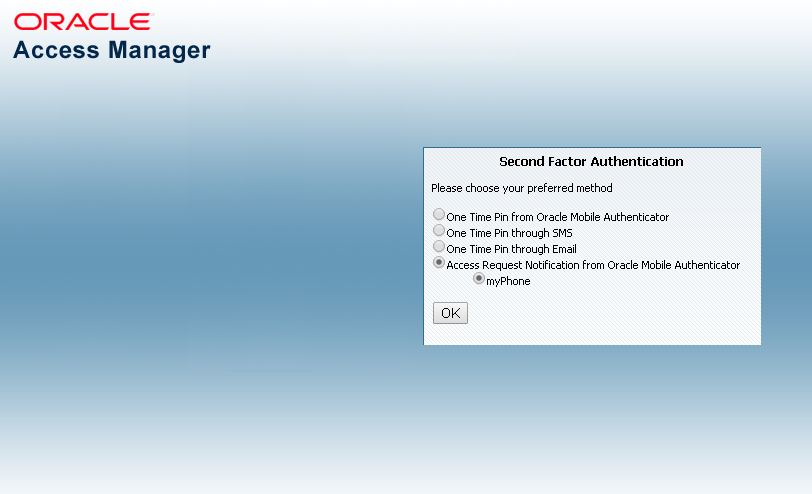
Description of "Figure 32-3 Access Request Notification Preferred Method Page"
When the user selects Access Request Notification from the Second Factor Authentication Preferred Method Page, Access Manager sends an Access Request Notification to either the Apple Push Notification Server or the Google Notification Server depending upon the user's configured device. The notification server then pushes a notification to the mobile device and the user will approve or deny it. Based on a successful response, the user will be directed to the protected resource. On failure, an error message will be displayed and the user will be returned to the same OTP page.
Figure 32-4 shows the Access Request Notification message that is displayed during this process.
Figure 32-4 Access Request Notification Wait Screen
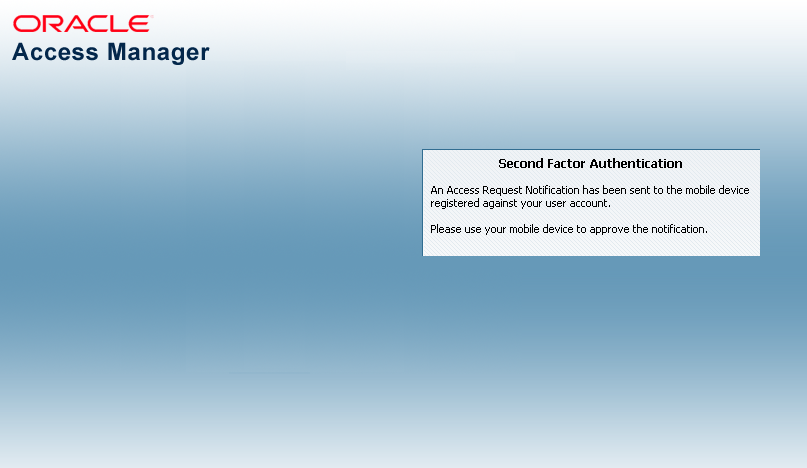
Description of "Figure 32-4 Access Request Notification Wait Screen"
32.2.3 Using the Oracle Mobile Authenticator with OTP And Access Request
The user downloads the OMA app to the mobile device and configures it to receive the access request notification.
Depending on the selected option, the Adaptive Authentication Service will need to work in tandem with the Oracle Mobile Authenticator (OMA), a mobile device app that uses Time-based One Time Password and push notifications to authenticate users with the second factor authentication scheme. To receive the OTP or Access Request Notification using the OMA, a user downloads it to an Apple or Android mobile device and configures it by clicking a link provided by the Access Manager administrator. Access Manager and OMA must share a secret key.
See Generating a Secret Key for the Oracle Mobile Authenticator about the secret key.
See Understanding Oracle Mobile Authenticator Configuration on how to configure OMA.
Note:
The OMA app is not needed if using the OTP through Email or OTP through SMS options.
32.3 Understanding Adaptive Authentication Service and OMA Configurations
You need to configure the Adaptive Authentication Service and, depending on the option, the OMA.
To configure the Adaptive Authentication Service, perform the following procedures:
32.4 Configuring an Adaptive Authentication Service
You can configure an Adaptive Authentication Service if you have already installed Access Manager, a WebGate, and Oracle HTTP Server (OHS).
Some of these configurations are specific to one or the other Adaptive Authentication Service options.
This section describes the following topics:
32.4.1 Generating a Secret Key for the Oracle Mobile Authenticator
The following RESTful endpoint is used to generate the secret key for a user in the Oracle Access Management identity store.
http://<HOST>:<PORT>/oauth2/rest/resources/secretkey HTTP/1.1
Where, <HOST> and <PORT> are those of the OAM server.
In the case of OMA online configuration (which is Oracle's recommended method of configuration), OMA uses the RESTful endpoint to store the key for a user in the identity store. In the cases of OMA manual configuration or Google Authenticator, the administrator sets up a web application which allows the user to generate a secret key also using above mentioned RESTful endpoint. The secret key is stored as a String in an LDAP attribute in the identity store and the name of this attribute must is passed to the business in the RESTful endpoint configuration before they generate the secret key.
See Understanding Oracle Mobile Authenticator Configuration.
32.4.2 Configuring Oauth Services to enable the Secret Key API
There are three parts to enabling the Secret Key API. The first part is to enable the secret key endpoint. The second part deals with enabling OAM configuration to enable the use of Time-based One-Time Password (TOTP). The third part deals with setting up OAM to produce a TOTP for a particular user Account.
To enable the Secret Key API:
32.4.3 Configuring the Adaptive Authentication Plug-in in the Oracle Access Management Console
Access Manager provides the Adaptive Authentication Plug-in that you can use for two-factor authentication.
To configure the Adaptive Authentication plugin in the Oracle Access Management Console:
32.4.4 Setting Credentials for UMS, iOS, and Android
Use the WLST command line script to set the credentials for the Oracle User Messaging Service (UMS), the iOS certificate or the Android API key.
These credentials are used by the OAM Server in the process of sending SMS/Email and push notifications. Table 32-2 lists information that you need to complete the procedure.
Table 32-2 Server Side Configuration for Adaptive Authentication Service
| Configuration | Information | Challenge Method |
|---|---|---|
|
iOS Certificate/Password |
Access Request (Push) notification using iOS |
|
|
API Key |
|
Access Request (Push) notification using Android |
|
UMS Credential |
UMS credentials that OAM will use to establish the connection to UMS Web service. |
Email/SMS |
To set credentials for UMS, iOS, and AndroidT:
Note:
For information on how to update, delete or otherwise manage credentials using Fusion Middleware Control, see Securing Applications with Oracle Platform Security Services.
32.4.5 Creating a Java KeyStore for iOS Access Request (Push) Notifications
When using Access Request Notifications on iOS, create a Java KeyStore (JKS) by using the cert file and key file.
Once the JKS is created, rename it as APNsCertificate.jks and put it in the <domain>/config/fmwconfig directory of the Oracle Access Management installation. The JKS should contain the user's locally generated private key and the Apple Push Notification service (APNs) certificate downloaded from the Apple Developer Center.
The following sample commands generate and import the certificate:
openssl x509 -in aps_production.cer -inform DER -out aps_production.pem -outform PEM openssl pkcs12 -nocerts -in OMAKey.p12 -out OMAKey.pem openssl pkcs12 -export -inkey OMAKey.pem -in aps_production.pem -out iOS_prod.p12 keytool -import -keystore APNsCertificate.jks -file aps_production.cer -alias PushCert keytool -importkeystore -destkeystore APNsCertificate.jks -deststoretype JKS -srcstoretype PKCS12 -srckeystore iOS_prod.p12
These commands assume:
-
aps_production.cer to be the name of the APNs certificate downloaded from the Apple Developer Center.
-
OMAKey.p12 is the user's locally generated private key.
Also see Setting Credentials for UMS, iOS, and Android.
Note:
The section Maintain Your Certificates, Identifiers, and Profiles at the following Apple URL provides relevant information about app distribution certificates and APNs. https://developer.apple.com/library/ios/documentation/IDEs/Conceptual/AppDistributionGuide/Introduction/Introduction.html
32.4.6 Connecting with Messaging Server
Create a Google firebase project enabled for Firebase Cloud Messaging (FCM).
Note:
Administrators should be aware of the following:-
Google is deprecating Legacy FCM API's in June 2024 and migrating to HTTP v1 API's. For all new configurations it is recommended to use HTTP v1 API's.
-
In order to use HTTPv1 API's you must be using the OAM Patch 36714022.
-
If you have configured push notifications for Android in releases prior to OAM Patch 36714022, you will be using Legacy FCM API's. Administrators should migrate to HTTP v1 API's by upgrading to OAM Patch 36714022. The steps to migrate to HTTP v1 API's can be found in Migrating to service account json for Android Push Notification.
-
For reference purposes, the configuration steps using Legacy FCM API's can be found in Setting the GCM API key within the OAM Credential Store.
Note:
The steps to create a firebase project are specific to Google and may change over time.- Login to the Google firebase console at
https://console.firebase.google.com/u/0/. - Click the Add Project button and specify a name for the project. The name can be any text as it is not used by OAM. For example,
OMA-OAM. - Navigate to the project settings by clicking the gears icon next to the project name in the upper left-hand part of the browser.
- Click on the Cloud Messaging tab and make note of the
Sender ID. - Download the
Server account json, which is required in the later steps.
32.4.7 Enabling REST API to update FCM Service Account JSON
Perform the following steps to enable REST API to update service account json.
- Export the
oam-config.xmlfile. - Add XML element to enable Rest
API
<Setting Name="FCMServiceAccountContent" Type="htf:map"> <Setting Name="Description" Type="xsd:string">FCM Service Account Content REST API</Setting> <Setting Name="Enabled" Type="xsd:boolean">true</Setting> <Setting Name="ServerType" Type="xsd:string">Admin</Setting> <Setting Name="RequireAuthorizationHeader" Type="xsd:boolean">true</Setting> <Setting Name="RootResources" Type="htf:list"> <Setting Name="0" Type="xsd:string">oracle.security.am.sfa.api.FCMServiceAccountContentResource</Setting> </Setting> <Setting Name="ExceptionMappers" Type="htf:list"></Setting> <Setting Name="Providers" Type="htf:list"></Setting> </Setting> - Import the
oam-config.xmlfile.
32.4.8 Migrating to service account json for Android Push Notification
Perform the following steps to download and seed the service account json from Google Firebase project.
- Login to the Google firebase console at
https://console.firebase.google.com/u/0/. - Select a Google project.
- Navigate to the project settings by clicking the gears icon next to the project name in the upper left-hand part of the browser.
- Click on the Service accounts tab and then Generate new private
key.
This downloads the Service account json file.
- Copy the content of the downloaded Service account json file as
request body for the following
API.
curl --location --request PUT '<Admin Host>:<Admin Port>/oam/services/rest/notifications/android/api/v1/service-account-content' \ --header 'Accept: text/plain' \ --header 'Content-Type: application/json' \ --header 'Authorization: Basic <Basic Authentication Header>' \ --data-raw '{ "type": "service_account", "project_id": "<Project Id>", "private_key_id": "<Private Key Id", "private_key": "<Private Key>", "client_email": "<Client Email>", "client_id": "<Client Id>", "auth_uri": "https://accounts.google.com/o/oauth2/auth", "token_uri": "https://oauth2.googleapis.com/token", "auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs", "client_x509_cert_url": "<uri>", "universe_domain": "googleapis.com" }'A response code of 201 indicates that the command was successful. If not, check the log files and the Troubleshooting Push Notifications section.
32.4.9 Configuring Host Name Verifier for Android Access Request (Push) Notifications
If you are setting up Android for Access Request notification, use the WebLogic console to update the WebLogic Managed Server for host name verification.
This step is required for Access Request notification configuration on Android only. It allows the verification of host names represented using wildcards; for example, *.googleapis.com.
To configure host name verifier for Android access requests (push) notifications:
- Navigate to base_domain -> Summary of Environment -> Summary of Servers -> oam_server1.
- Click the SSL tab.
- Expand Advanced and select the Hostname verification entry to configure the Hostname Verifier.
- Enter
weblogic.security.utils.SSLWLSWildcardHostnameVerifieras the Custom Hostname Verifier. - Click Save.
- Restart the oam_server1.
32.4.10 Configuring Access Manager for VPN in a Use Case
You can configure Access Manager when a user needs to have access to a protected resource with VPN software.
To configure Access Manager for VPN in a use case:
32.4.11 Troubleshooting Push Notifications
This section provides various errors, fixes, workarounds for troubleshooting the push notifications
Push Notification [FCM HTTP v1] is not sent to mobile device
-
Ensure that the FCM Service Account JSON is configured.
curl --location '<Admin Host>:<Admin Port>/oam/services/rest/notifications/android/api/v1/service-account-content' \ --header 'Accept: text/plain' \ --header 'Authorization: Basic <Basic Authentication Header>Status 200 indicates that the request has succeeded. Also, ensure the correctness and the completeness of the returned JSON.
Note:
For more information, see Migrating to service account json for Android Push Notification. -
Enable Trace:16 Log to check if new FCM api is being used.
Sample log file if the olderapi keyorsever keyis still being used:Legacy Firebase cloud messaging API is enabled. Legacy Api will be removed soon(https://firebase.google.com/docs/cloud-messaging/migrate-v1), Please switch to new process of using firebase service account json to avoid disruption in Second factor Push notification functionality.
Service account json is updated or rolled back, but changes are not reflecting
Service account JSON is cached. In case of an update or delete, please wait for 5 minutes for changes to reflect. A restart of the Managed Server would reflect the changes immediately.
FCM service account json configured, but 403 response in the logs
If you get 403 in from FCM v1 API with the message:
Firebase Cloud Messaging API has not been used in project <Project Id> before or it is disabled. Enable it by visiting https://console.developers.google.com/apis/api/fcm.googleapis.com/overview?project=<Project Id> then retry. If you enabled this API recently, wait a few minutes for the action to propagate to our systems and retry.
Visit the above mentioned link and enable the Firebase Cloud Messaging API.