Using Federation Attributes for OAM Authorization and Protected Web Applications
This chapter describes how attributes received in SAML/OpenID SSO messages can be used in the Oracle Access Manager (OAM) authentication process and how they can be provided to protected web applications.
- As conditions in authorization rules
- As responses to provide the SAML/OpenID attributes to protected web applications
- The IdP partner name, referenced by
$session.attr.fed.partner. - The NameID value from the SSO response, referenced by
$session.attr.fed.nameidvalue. - The NameID format from the SSO response for SAML protocols
referenced by
$session.attr.fed.nameidformat. - Attributes contained either in the SAML Assertion's Attribute
Statement or in the OpenID SSO Response are referenced using
$session.attr.fed.attr.ATTR_NAME, withATTR_NAMEbeing either the local session attribute name, if the IdP Attribute Profile mapping is applied or the attribute name from the SSO response, if no IdP Attribute Profile mapping is applied for this attribute.
Overview of Authenticating User Access to a Protected Resource
- LDAP directory
- OAM admin server, with the OAM admin console
- OAM runtime server
- Web applications
- WebGate agents protecting web applications on HTTP servers (OHS, IIS, and so on)
- Interprets the call and ensures that the:
- User is authenticated
- User is authorized to access the resource by evaluating authorization policies for the resource
- Injects data as cookies or HTTP headers into the HTTP request, and forwards the HTTP request to the protected resource
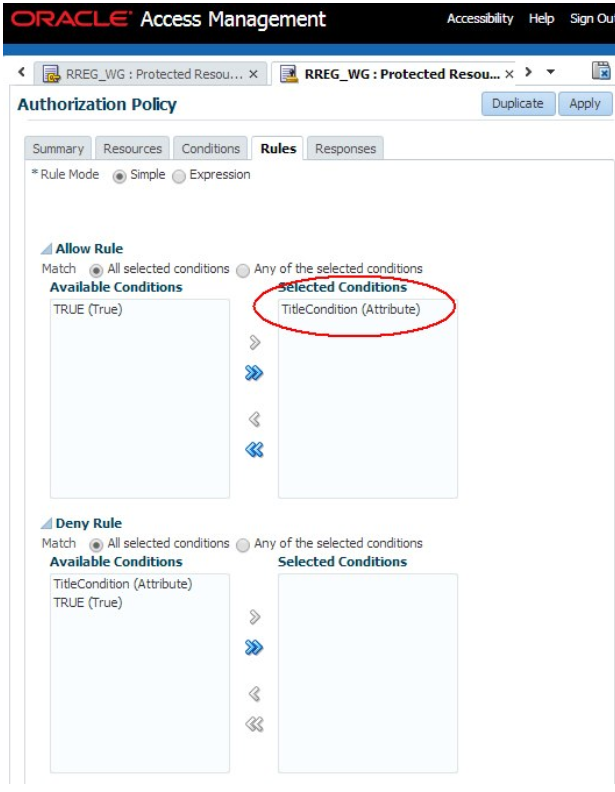
- Identity: Condition based on the user's identity or groups to which the user belongs
- IP Address: Condition based on the user's IP address
- Temporal: Condition based on time
- Attributes: Condition based on attributes (LDAP, HTTP request, or session attributes)
- User LDAP attributes
- HTTP request data
- Static strings
- OAM session attributes
Similar to OAM Authization Policies, an administrator can inject federation data into an
HTTP request using OAM session attributes ($session.attr.fed.partner,
$session.attr.fed.attr.ATTR_NAME…)
Prerequisites for Setting up Federation SSO
- OIF acting as a Service Provider
- The IdP (AcmeIdP) sending a SAML assertion with NameID set to userID
- Set the following attributes:
- email to user's email address
- fname to user's first name
- surname to user's last name
- title to user's last job title
- Confugure OIF/SP with an IdP attribute profile to map:
- fname to firstname
- surname to lastname
- leave email as is
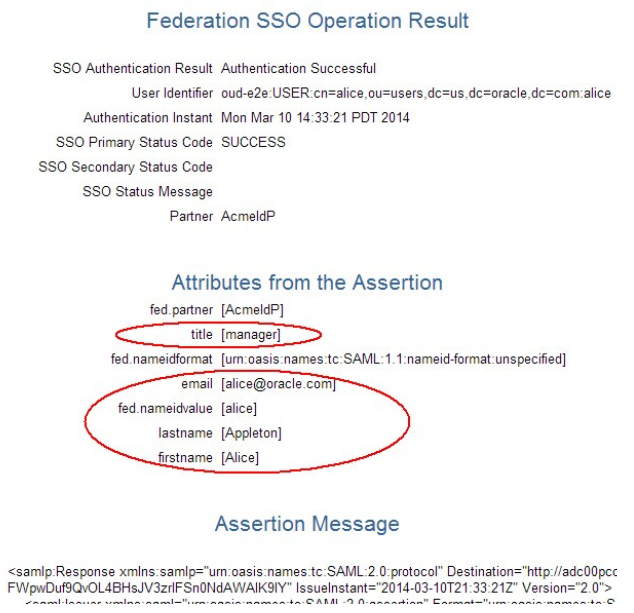
- User 1: Alice
- userID: alice
- email: alice@oracle.com
- first name: Alice
- last name: Appleton
- title: manager
- User 2: Bob
- userID: bob
- email: bob@oracle.com
- first name: Bobby
- last name: Smith
- title: engineer
<samlp:Response ..>
<saml:Issuer ...>http://acme.com/idp</saml:Issuer>
<samlp:Status>
<samlp:StatusCode
Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
</samlp:Status>
<saml:Assertion ...>
<saml:Issuer ...>http://acme.com/idp</saml:Issuer>
<dsig:Signature ...>
...
</dsig:Signature>
<saml:Subject>
<saml:NameID ...>alice</saml:NameID>
...
</saml:Subject>
<saml:Conditions ...>
...
</saml:Conditions>
<saml:AuthnStatement ...>
...
</saml:AuthnStatement>
<saml:AttributeStatement ...>
<saml:Attribute Name="email" ...>
<saml:AttributeValue...>alice@oracle.com</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="title" ...>
<saml:AttributeValue...>manager</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="surname" ...>
<saml:AttributeValue...>Appleton</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="fname" ...>
<saml:AttributeValue...>Alice</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>- email was not changed
- title was not changed
- fname was mappped to firstname
- surname was mapped to lastname
Prerequisites for Protected Web Application
- OHS is installed
- A WebGate agent must be configured for the OHS instance
- An OAM Application Domain must be created for the WebGate, which protects all the resources on the OHS server
- Authentication Policy:
- Name: Protected Resource Policy
- Authentication Scheme: FederationScheme
- Authorization Policy:
- Name: Protected Resource Policy
- Resources linked to 'Protected Resource Policy' of Authentication Policy and 'Protected Resource Policy' of the Authorization Policy
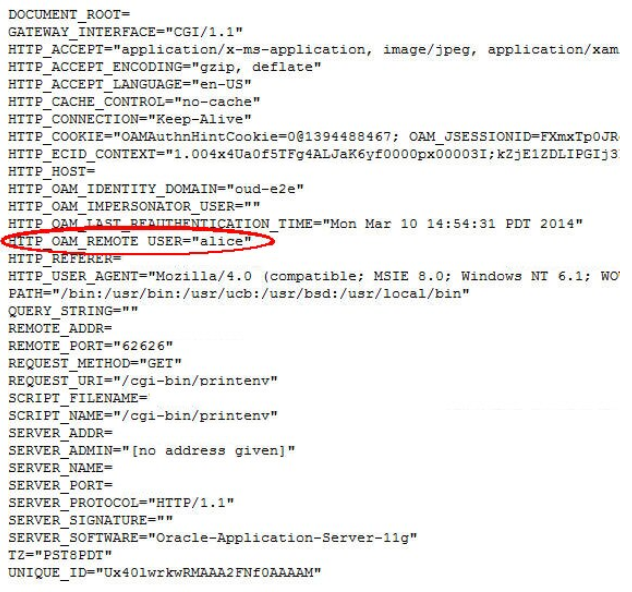
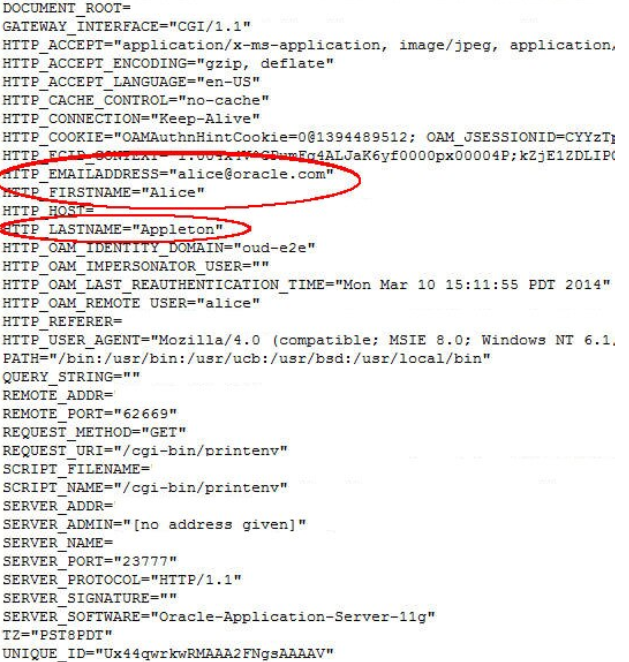
/cgi-bin/printenv resource on OHS prints the following data when
processing the HTTP Request sent by the browser:
- HTTP Headers
- Request Data (path, query string)
- Server Data (IP address, port)
An example of a browser accessing the resource without being protected by OAM/WebGate
would result in the following display (in the test, the web application will be
protected as listed below):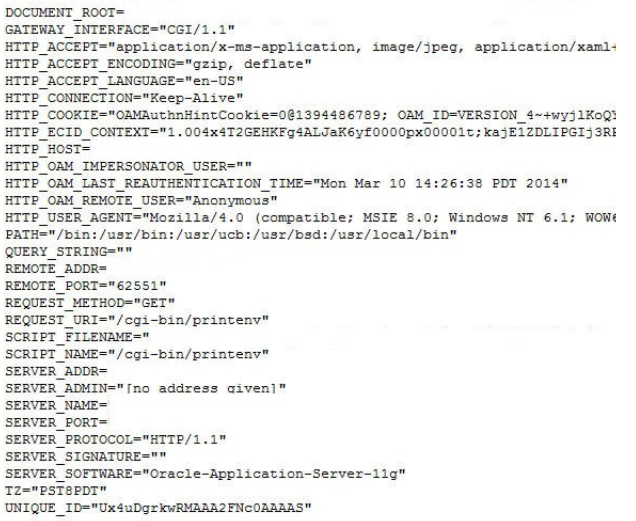
Constructing Authorization Policy Using Federation Attributes
- Users authenticated through Federation SSO (The resource is protected through FederationScheme Authentication Policy).
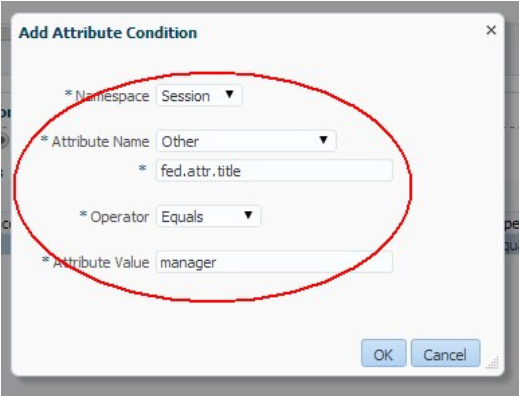
- IdP provides the job title of the user and is locally known as title (if an IdP sends the job title through a name other than the title then an IdP Attribute Profile must be used to map it to the local title name).
- Only users with the manager title must have access to the resource.
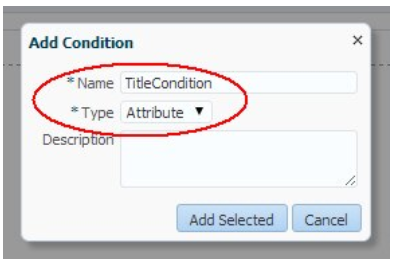
Following are the steps to create an authorization policy:
Injecting Federation Attributes
- Users authenticated through Federation SSO (The resource is protected through a FederationScheme Authentication Policy).
- IdP provides the job title of the user and is locally known as title (if an IdP sends the job title through a name other than the title then an IdP Attribute Profile must be used to map it to the local title name).
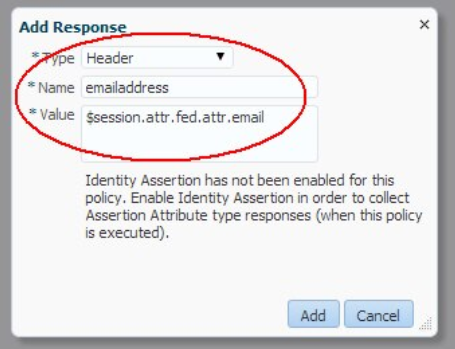
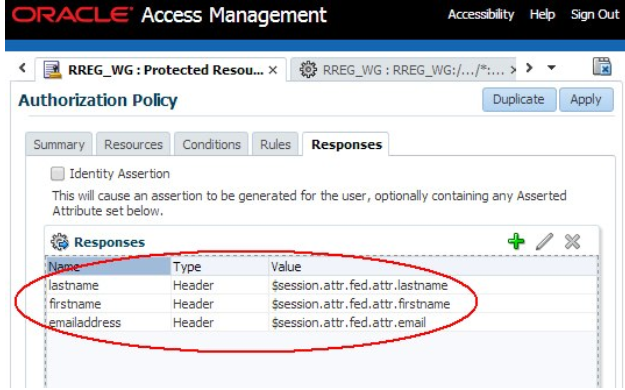
- OAM/WebGate is configured to inject:
- Email address as emailaddress
- First name as firstname
- Last name as lastname
- The configuration is done through the use of Authorization Response objects in an Authorization Policy definition.
Following are the steps to inject Federation attributes: