Using Test SP Application in OIF and SP
- Test the Federation SSO flows
- Start Federation SSO with the specified Identity Provider (IdP)
- Authentication at the IdP
- Verify if the mapping rules work
- Find out which attributes are sent by the IdP, how they are named and how they are processed by OIF/SP
- View the Federation token (SAML Assertion or OpenID SSO Response)
- Diagnose issues with the SAML/OpenID flows, before rolling Federation SSO out
- Implement the SP functionality of OIF via a browser without creating any OAM session
- Display the Test SP operation result and SAML Assertion/OpenId SSO response
Enabling Test SP Engine
Note:
The Test SP application must be disabled once you have finished using it.Use the following OIF WLST commands to enable the Test SP application:
Using the Test SP Engine
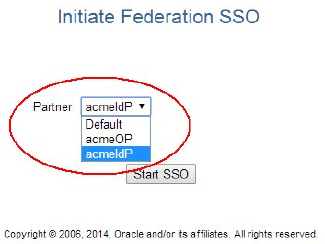
Starting Federation SSO Flow
- Navigating to the Test SP application through a browser
- Selecting the IdP to perform Federation SSO
- Starting the operation
To start Federation SSO:
Displaying Test SP Operation Result
When the IdP redirects the user with the SAML Assertion/OpenID Response to OIF/SP,
the server validates the response and maps it to an LDAP user record. 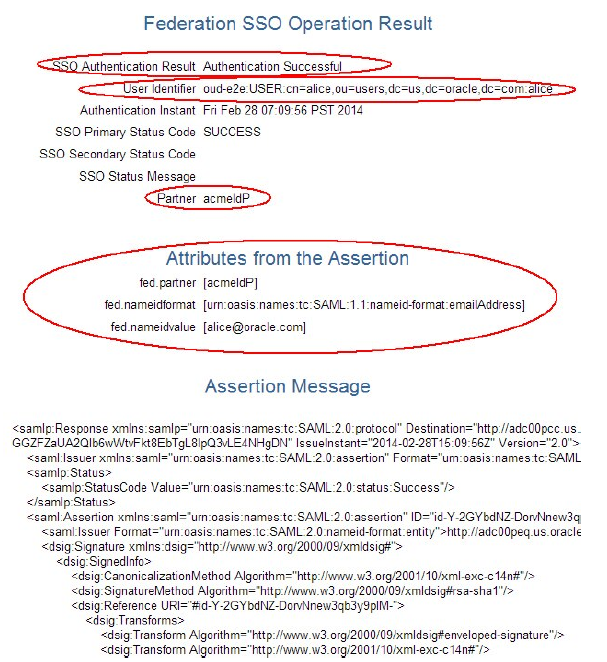
- The result of the authentication operation.
- The canonical user ID to which the response was mapped that contains the Identity Store Name, User DN, and User ID.
- The authentication instant.
- The IdP partner name.
- Attributes from the SSO Response that are stored in the OAM session.
- The decrypted/decoded SSO response.
Diagnosing Mapping and Response Validation Issues
If the Federation SSO between the IdP and OIF/SP is not working then use the Test SP engine together with the Oracle Access Manager (OAM) to diagnose the problem. You can diagnose the following issues:
Mapping Issues
- An error Message
- The NameID/attributes sent by the IdP
- The SSO message sent by the IdP, which contains the NameID/attributes
In the following example, the IdP and OIF/SP administrators agreed to use
SAML 2.0 and identified the user through the email address. The issue is that the email
address for Alice at the IdP is alice.appleton@oralce.com, where as the
email address used by OIF/SP in the LDAP directory is
alice@oracle.com.
- The authentication operation failed message.
- The assertion could not be mapped to a local user record message.
- The data extracted from the assertion and the SAML message.
<Feb 28, 2014 7:18:05 AM PST> <Warning>
<oracle.security.fed.eventhandler.fed.profiles.sp.sso.assertion.Saml20AssertionProcessor>
<FED-15108> <User was not found during attribute based authentication using NameID mapping for name identifier: alice.appleton@oracle.com name identifier format :
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress and message :
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
Destination="http://adc00pcc.us.oracle.com:23002/oam/server/fed/sp/sso" ID="idaWfL5-
f37nhQWh0WWjHbobsVetM-" InResponseTo="id-hqkZGMV-wEO5-
CulpYxArIvr91Y14dA-WSRYZ8zP" IssueInstant="2014-02-28T15:18:05Z"
Version="2.0"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
Format="urn:oasis:names:tc:SAML:2.0:nameidformat:
entity">http://adc00peq.us.oracle.com:7499/fed/idp</saml:Issuer>
<samlp:Status><samlp:StatusCode
Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status><saml:Assertion
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="id-PoODBDUeoiSY4ajPCQ86yjZWkw-"
IssueInstant="2014-02-28T15:18:05Z" Version="2.0">
<saml:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameidformat:
entity">http://adc00peq.us.oracle.com:7499/fed/idp</saml:Issuer>
<dsig:Signature xmlns:dsig="http://www.w3.org/2000/09/xmldsig#"><dsig:SignedInfo>
<dsig:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"
/><dsig:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<dsig:Reference URI="#id-PoOD-BDUeoiSY4ajPCQ86yjZWkw-"><dsig:Transforms>
<dsig:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"
/><dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"
/></dsig:Transforms><dsig:DigestMethod Algorithm="http://www.w3.org/2000/09
/xmldsig#sha1"/><dsig:DigestValue>X5ojFxrpBOS4klosM5jcBOF8Bqg=
</dsig:DigestValue></dsig:Reference></dsig:SignedInfo>
<dsig:SignatureValue>VJKJOBOowHZ4lVkHjX4w2YHi+0ZAa4ez
/+D+ketAQcOxxtwOZPcBYERwkMgazudMh0XEMbIkwsBTVwb4tX+uV327Gjlp1hXc0uYnm2n8mZfen9Ppru6jTES4N7PoD3mOpCfFEHBUJg118DihWGLfzBWw7LMLaN2A
</dsig:SignatureValue></dsig:Signature><saml:Subject><saml:NameID
Format="urn:oasis:names:tc:SAML:1.1:nameidformat:
emailAddress">alice.appleton@oracle.com</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData InResponseTo="id-hqkZGMV-wEO5-
CulpYxArIvr91Y14dA-WSRYZ8zP" NotOnOrAfter="2014-02-28T15:23:05Z" Recipient="http://adc00pcc.us.oracle.com:23002/oam/server/fed/sp/sso"/>
</saml:SubjectConVrmation></saml:Subject><saml:Conditions
NotBefore="2014-02-28T15:18:05Z" NotOnOrAfter="2014-02-28T15:23:05Z">
<saml:AudienceRestriction><saml:Audience>http://adc00pcc.us.oracle.com:23002
/oam/fed</saml:Audience></saml:AudienceRestriction></saml:Conditions>
<saml:AuthnStatement AuthnInstant="2014-02-28T15:18:05Z" SessionIndex="id-
2i7BY1gGnhukoBSDmrvkBIaG-NI-" SessionNotOnOrAfter="2014-02-28T16:18:05Z">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</saml:AuthnContext></saml:AuthnStatement></saml:Assertion></samlp:Response>Response Validation Issues
- An error message
- The SSO message sent by the IdP
In the following example, the IdP and OIF/SP administrators agreed to use SAML 2.0 but the IdP is not signing the assertion as required by OIF/SP.
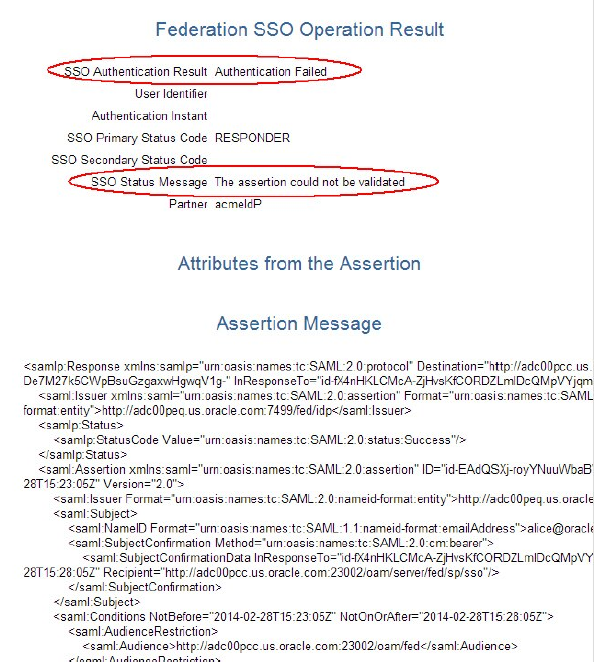
- The authentication operation failed message.
- The assertion could not be validated message.
- The SAML message.
<Feb 28, 2014 7:23:05 AM PST> <Error>
<oracle.security.fed.eventhandler.fed.profiles.utils.CheckUtils> <FEDSTS-18003>
<Assertion is not signed.>
<Feb 28, 2014 7:23:05 AM PST> <Error>
<oracle.security.fed.eventhandler.fed.profiles.sp.sso.v20.ProcessResponseEventHandler>
<FED-18012> <Assertion cannot be validated: <samlp:Response
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
Destination="http://adc00pcc.us.oracle.com:23002/oam/server/fed/sp/sso" ID="id-
De7M27k5CWpBsuGzgaxwHgwqV1g-" InResponseTo="id-fX4nHKLCMcAZjHvsKfCORDZLmIDcQMpVYjqmxQb"
IssueInstant="2014-02-28T15:23:05Z"
Version="2.0"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
Format="urn:oasis:names:tc:SAML:2.0:nameidformat:
entity">http://adc00peq.us.oracle.com:7499/fed/idp</saml:Issuer>
<samlp:Status><samlp:StatusCode
Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status><saml:Assertion
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="id-EAdQSXjroyYNuuWbaBWZVdBtu8-"
IssueInstant="2014-02-28T15:23:05Z" Version="2.0">
<saml:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameidformat:
entity">http://adc00peq.us.oracle.com:7499/fed/idp</saml:Issuer>
<saml:Subject><saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameidformat:
emailAddress">alice@oracle.com</saml:NameID><saml:SubjectConfirmation
Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><saml:SubjectConfirmationData
InResponseTo="id-fX4nHKLCMcA-ZjHvsKfCORDZLmIDcQMpVYjqmxQb"
NotOnOrAfter="2014-02-28T15:28:05Z"
Recipient="http://adc00pcc.us.oracle.com:23002/oam/server/fed/sp/sso"/>
</saml:SubjectConfirmation></saml:Subject><saml:Conditions
NotBefore="2014-02-28T15:23:05Z" NotOnOrAfter="2014-02-28T15:28:05Z">
<saml:AudienceRestriction><saml:Audience>http://adc00pcc.us.oracle.com:23002
/oam/fed</saml:Audience></saml:AudienceRestriction></saml:Conditions>
<saml:AuthnStatement AuthnInstant="2014-02-28T15:23:05Z" SessionIndex="id--
0QWpaU2AV-L7UpNvLH5Bn7Z5Xk-" SessionNotOnOrAfter="2014-02-28T16:23:05Z">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</saml:AuthnContext></saml:AuthnStatement></saml:Assertion></samlp:Response>