1 About the Connector
Oracle Identity Governance is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premises or on the Cloud. Oracle Identity Governance connectors are used to integrate Oracle identity Governance with the external identity-aware applications.
Note:
In this guide, the connector that is deployed using the Applications option on the Manage tab of Identity Self Service is referred to as an AOB application.From Oracle Identity Governance release 12.2.1.3.0 onward, connector deployment is handled using the application onboarding capability of Oracle Identity Self Service. This capability lets business users to onboard applications with minimum details and effort. The connector installation package includes a collection of predefined templates (XML files) that contain all the information required for provisioning and reconciling data from a given application or target system. These templates also include basic connectivity and configuration details specific to your target system. The connector uses information from these predefined templates allowing you to onboard your applications quickly and easily using only a single and simplified UI.
Application onboarding is the process of registering or associating an application with Oracle Identity Governance and making that application available for provisioning and reconciliation of user information.
The following topics provide a high-level overview of the Azure AD connector:
1.1 Connector Offerings Compared to Office 365
Azure AD connector provides additional benefits over the Office 365 connector. Here are a few top reasons to opt-in for Azure AD, instead of the Office 365 connector.
- Azure AD connector users can leverage latest Microsoft graph API using the Azure AD connector.
- Azure AD connector offers Out Of the Box feature that helps distinguish between security and Office 365 groups.
- Azure AD connector provides improved reconciliation performance over the Office 365 connector.
1.2 Certified Components
These are the software components and their versions required for installing and using the Azure AD connector.
Table 1-1 Certified Components
| Component | Requirement for AOB Application |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use any one of the following releases:
|
|
Oracle Identity Governance or Oracle Identity Manager JDK |
JDK 1.8 and later |
|
Target systems |
Azure AD |
|
Connector Server |
12.2.1.3.1 or 12.2.1.3.0 |
|
Connector Server JDK |
|
|
Target API version |
Azure Active Directory (AD) Microsoft graph API v1.0 and Authentication API version v2.0 |
1.3 Usage Recommendation
If you are using Oracle Identity Governance 12c (12.2.1.3.0) or Oracle Identity Governance 14c (14.1.2.1.0) or later, then use the latest 12.2.1.x version of this connector. Deploy the connector using the Applications option on the Manage tab of Identity Self Service.
1.4 Certified Languages
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.5 Supported Connector Operations
These are the list of operations that the connector supports for your target system.
Table 1-2 Supported Connector Operations
| Operation | Supported |
|---|---|
|
User Management |
|
|
Create user |
Yes |
|
Update user |
Yes |
|
Enable user |
Yes |
|
Disable user |
Yes |
|
Delete user |
Yes |
|
Reset Password |
Yes |
| Role Grant Management | |
|
Assign and Revoke Roles |
Yes |
|
License Grant Management |
|
|
Grant and Revoke Licences |
Yes |
| Security Group Management | |
|
Add, Update, and Remove Groups |
Yes |
| Office Group Management | |
|
Add, Update, and Remove Groups |
Yes |
| MS Teams Management | |
|
Create groups to the user |
Yes |
|
Delete groups from the user |
Yes |
|
Reconcile groups to the user |
Yes |
| Teams Group Assignment | |
|
Add Teams Group to the user |
Yes |
|
Remove Teams Group from the user
Note: The MS Teams support is applicable from 12.2.1.3.0B. |
Yes |
Note:
All the connector artifacts required for managing groups as an object (for example groups attribute mappings, reconciliation rules, jobs, and so on) are not visible in the Applications UI in Identity Self Service. However, all the required information is available in the predefined application templates of the connector installation package. For more information about the artifacts related to groups, see Connector Objects Used for Groups Management.1.6 Connector Architecture
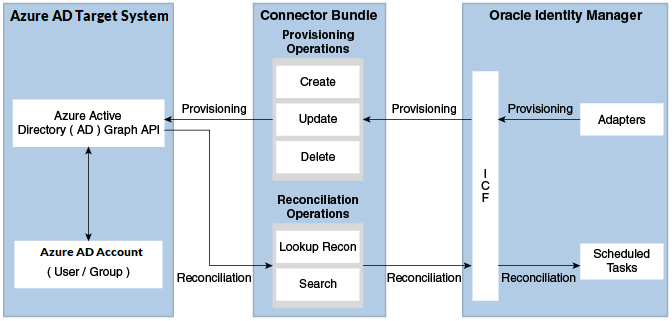
The Azure AD connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that is required in order to use Identity Connector. ICF provides basic reconciliation and provisioning operations that are common to all Oracle Identity Governance connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as, buffering, time outs, and filtering. ICF is distributed together with Oracle Identity Governance. Therefore, you do not need to configure or modify ICF.
Figure 1-1 shows the architecture of the Azure AD connector.
-
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this mode, the Azure AD application is used as the trusted source and users are directly created and modified on Oracle Identity Governance. During reconciliation, a scheduled task invokes an ICF operation. ICF inturn invokes a search operation on the Azure AD Identity Connector Bundle and then the bundle calls Azure AD API for Reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Governance.
Each user record fetched from the target system is compared with existing OIM Users. If a match is found between the target system record and the OIM User, then the OIM User attributes are updated with changes made to the target system record. If no match is found, then the target system record is used to create an OIM User.
-
Account management
Account management is also known as target resource management. In this mode, the target system is used as a target resource and the connector enables the following operations:
-
Provisioning
Provisioning involves creating, updating, or deleting users on the target system through Oracle Identity Governance. During provisioning, the Adapters invoke ICF operation, ICF inturn invokes create operation on the Azure AD Identity Connector Bundle and then the bundle calls the target system API (Microsoft Azure Active Directory (AD) Graph API) for provisioning operations. The API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters.
-
Target resource reconciliation
During reconciliation, a scheduled task invokes an ICF operation. ICF inturn invokes a search operation on the Azure AD Identity Connector Bundle and then the bundle calls Azure AD API for Reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Governance.
Each record fetched from the target system is compared with Azure AD resources that are already provisioned to OIM Users. If a match is found, then the update made to the Azure AD record from the target system is copied to the Azure AD resource in Oracle Identity Governance. If no match is found, then the userPrincipalName of the record is compared with the User Login of each OIM User. If a match is found, then data in the target system record is used to provision an Azure AD resource to the OIM User.
-
The Azure AD Identity Connector Bundle communicates with the Microsoft Graph API using the HTTPS protocol. The Microsoft Graph API provides programmatic access to Azure Active Directory through REST API endpoints. Apps can use the Microsoft Graph API to perform create, read, update, and delete (CRUD) operations on directory data and directory objects, such as users, groups.
See Also:
Understanding the Identity Connector Framework in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance for more information about ICF
1.7 Use Cases Supported by the Connector
The Azure AD connector is used to integrate Oracle Identity Governance with Azure AD to ensure that all Azure AD accounts are created, updated, and deactivated on an integrated cycle with the rest of the identity-aware applications in your enterprise. The Azure AD connector supports management of identities for Cloud Identity, Synchronized Identity, and Federated Identity models of Azure AD. In a typical IT scenario, an organization using Oracle Identity Governance wants to manage accounts, groups, roles and licenses across Azure AD Cloud Service.
-
Azure AD User Management
An organization using Azure AD wants to integrate with Oracle Identity Governance to manage identities. The organization wants to manage its user identities by creating them in the target system using Oracle Identity Governance. The organization also wants to synchronize user identity changes performed directly in the target system with Oracle Identity Governance. In such a scenario, a quick and an easy way is to install the Azure AD connector and configure it with your target system by providing connection information.
To create a new user in the target system, fill in and submit the OIM process form to trigger the provisioning operation. The connector executes the CreateOp operation against your target system and the user is created on successful execution of the operation. Similarly, operations like delete and update can be performed.
To search or retrieve the user identities, you must run a scheduled task from Oracle Identity Governance. The connector will run the corresponding SearchOp against the user identities in the target system and fetch all the changes to Oracle Identity Governance.
-
Azure AD Group Management
An organization has a number of Azure AD Security Groups allowing its users to set up new groups, manage memberships, and delete groups. The organization now wants to know the list of groups that have not been recently accessed or who have inactive members. In such a scenario, you can use the Azure AD connector to highlight the usage trend for groups. By using the Azure AD connector, you can leverage the reporting capabilities of Oracle Identity Governance to track any operations (such as create, update, delete) performed on groups and changes made in their memberships .
-
Azure AD Admin Role Management
In large organizations, it may be necessary for an administrator to designate other employees to act as administrators to serve different functions. For example, you can set admin roles for your IT staff that can act as support agents to other employees, partners, customers and vendors. With the Azure AD connector, you can assign or revoke an Azure AD admin role to users as an entitlement, thus facilitating you to leverage the delegated administration capability of Azure AD.
-
Azure AD User License Management
Another scenario is one in which an organization is using Azure AD for business and manages user licenses as per the changing needs of the organization by assigning or unassigning licenses for users. What is needed is an effective way to keep track of all the licenses and user rights both in cloud and on-premise servers. In such a scenario, you can use the Azure AD connector to effectively track all user licenses. You can keep track of these license assignment changes by leveraging Oracle Identity Governance capability of auditing and reporting.
There are two types of Licensing available to make your large-scale license management easier.
- Direct License
Assigns product licenses to a group of users and verifys that they are licensed correctly in Azure Active Directory, for example, Office 365 Enterprise E3 licenses.
- Inherited License
Microsoft has made group-based license management available through the Azure portal. The customer can enable/disable the individual service plans available for a single product. Service plans are known as Inherited licenses, for example, Office 365 Enterprise E3 licenses have available service plans such as, Teams, PowerBI, Yammer, and SharePoint.
Note:
If Direct License is added to a user without any service plans there is a default license attached to that user. The user cannot add/remove the default license. If a user wants to remove all the Inherited Licenses, they should mandatorily remove the Direct License. - Direct License
- MS Teams Group Support
Microsoft Teams is a proprietary business communication platform developed by Microsoft, as part of the Microsoft 365 family of products. By using the MS Team, users can share files, organize meetings from their calendar, and sync with other Office apps like MS OneNote, MS OneDrive, and Skype for Business. This improves collaboration and communication while simultaneously aiding the adoption of Office 365.
1.8 Connector Features
The features of the connector include support for connector server, full reconciliation, limited reconciliation, and reconciliation of deleted account data.
Table 1-3 Supported Connector Features Matrix
| Feature | AOB Application |
|---|---|
|
Full reconciliation |
Yes |
|
Limited reconciliation |
Yes |
|
Delete reconciliation |
Yes |
|
Support for authoritative source reconciliation |
Yes |
|
Support for authoritative source delete reconciliation |
Yes |
|
Use connector server |
Yes |
|
Transformation and validation of account data |
Yes |
|
Perform connector operations in multiple domains |
Yes |
|
Support for paging |
Yes |
|
Test connection |
Yes |
|
Reset password |
Yes |
|
MS Teams management |
Yes |
|
Teams Group assignment |
Yes Note: MS Teams support is applicable from 12.2.1.3.0B. |
The following topics provide more information on the features of the AOB application:
1.8.1 Full Reconciliation and Incremental Reconciliation
You can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Governance.
After the first full reconciliation run, you can configure your connector for incremental reconciliation if the target system contains an attribute that holds the timestamp at which an object is created or modified.
In the Azure AD connector, the incremental reconciliation option is not enabled by default. The connector supports incremental reconciliation only if the target system contains an attribute that holds the timestamp at which an object is created or modified.
Note:
The connector supports incremental reconciliation if the target system contains an attribute that holds the timestamp at which an object is created or modified.You can perform a full reconciliation run at any time. See Performing Full Reconciliation and Incremental Reconciliation for more information about performing full and incremental reconciliation.
1.8.2 Limited Reconciliation
You can reconcile records from the target system based on a specified filter criterion. To limit or filter the records that are fetched into Oracle Identity Governance during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled.
You can set a reconciliation filter as the value of the Filter Suffix attribute of the user reconciliation scheduled job. The Filter Suffix attribute helps you to assign filters to the API based on which you get a filtered response from the target system.
For more information, see Performing Limited Reconciliation.
1.8.3 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not want to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements if the bundle works faster when deployed on the same host as the native managed resource.
See Also:
Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Manager for more information about installing and configuring connector server and running the connector server
1.8.4 Transformation and Validation of Account Data
You can configure transformation and validation of account data that is brought into or sent from Oracle Identity Governance during reconciliation and provisioning operations by writing Groovy scripts while creating your application.
For more information, see Validation and Transformation of Provisioning and Reconciliation Attributes in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.