1 About the UNIX Connector
Oracle Identity Governance is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premises or on the Cloud. Oracle Identity Governance connectors are used to integrate Oracle identity Governance with the external identity-aware applications.
Note:
In this guide, the connector that is deployed using the Applications option on the Manage tab of Identity Self Service is referred to as an AOB application. The connector that is deployed using the Manage Connector option in Oracle Identity System Administration is referred to as a CI-based connector (Connector Installer-based connector).Application onboarding is the process of registering or associating an application with Oracle Identity Governance and making that application available for provisioning and reconciliation of user information.
The following topics provide a high-level overview of the connector:
Note:
In this guide, the term Oracle Identity Governance server refers to the computer on which Oracle Identity Governance is installed.
1.1 Certified Components
These are the software components and their versions required for installing and using the connector.
Note:
If you are using Oracle Identity Manager release 11.1.x, then you can install and use the connector only in the CI-based mode. If you want to use the AOB application, then you must upgrade to Oracle Identity Governance release 12.2.1.3.0 or later.
Table 1-1 Certified Components
| Component | Requirement for AOB Application | Requirement for CI-Based Connector |
|---|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
Oracle Identity Governance or Oracle Identity Manager JDK |
JDK 1.7 or later |
JDK 1.7 or later |
|
Target systems |
The target system can be any one of the following operating systems:
Note: You can also configure and use the connector on any other UNIX-based operating system that supports SSH and Telnet protocols. See Configuring the Connector for a New Target System for more information. |
The target system can be any one of the following operating systems:
Note: You can also configure and use the connector on any other UNIX-based operating system that supports SSH and Telnet protocols. See Configuring the Connector for a New Target System for more information. |
|
Connector Server |
11.1.2.1.0 |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.7 or later |
JDK 1.7 or later |
|
Other systems |
OpenSSH, OpenSSL, operating system patches (HP-UX), and SUDO software (only if the SUDO Admin mode is required) |
OpenSSH, OpenSSL, operating system patches (HP-UX), and SUDO software (only if the SUDO Admin mode is required) |
|
Target system user account |
Depending on the target system that you are using, the target system user account can be one of the following:
You provide the credentials of this user account as part of Basic Configuration Parameters while creating an application. |
Depending on the target system that you are using, the target system user account can be one of the following:
You provide the credentials of this user account while configuring the IT resource. |
|
Character encoding supported by the target system |
The target system must support the default C (POSIX) locale. Use the following command to check the locale that the target system supports:
|
The target system must support the default C (POSIX) locale. Use the following command to check the locale that the target system supports:
|
Note:
The connector requires sh shell on the target system to run the scripts. Therefore, the connector switches to sh before running the commands.
If the user account indicated in the loginUser basic configuration parameter has access to sh and the user account can switch to sh, then there is no restriction on the original login shell.
1.2 Usage Recommendation
These are the recommendations for the UNIX connector versions that you can deploy and use depending on the Oracle Identity Governance or Oracle Identity Manager version that you are using.
-
If you are using Oracle Identity Governance 12c (12.2.1.3.0), then use the latest 12.2.1.x version of this connector. Deploy the connector using the Applications option on the Manage tab of Identity Self Service.
-
If you are using any of the Oracle Identity Manager releases listed in the “Requirement for CI-Based Connector” column in Certified Components, then use the 11.1.x version of the connector. If you want to use the 12.2.1.x version of this connector, then you can install and use it only in the CI-based mode. If you want to use the AOB application, then you must upgrade to Oracle Identity Governance release 12.2.1.3.0.
Note:
If you are using the latest 12.2.1.x version of the UNIX connector in the CI-based mode, then see Oracle Identity Manager Connector Guide for UNIX, Release 11.1.1 for complete details on connector deployment, usage, and customization.
1.3 Certified Languages
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
1.4 Supported Connector Operations
These are the list of operations that the connector supports for your target system.
Table 1-2 Supported Connector Operations
| Operation | Supported? |
|---|---|
|
User Management |
|
|
Create user |
Yes |
|
Update user |
Yes |
|
Delete user |
Yes |
|
Enable user |
Yes |
|
Disable user |
Yes |
|
Update user login |
Yes |
|
Update user shell |
Yes |
|
Update UID |
Yes |
|
Group Management |
|
|
Update primary group |
Yes |
|
Insert secondary group |
Yes |
|
Update secondary group |
Yes |
|
Delete secondary group |
Yes |
|
Entitlement Grant Management |
|
|
Add role |
Yes |
|
Update GECOS |
Yes |
|
Update home directory |
Yes |
|
Update inactive days |
Yes |
|
Update expire date |
Yes |
|
Update password |
Yes |
1.5 Connector Architecture
You can configure the UNIX connector to run in the Target (or account management) and Authoritative (or trusted) mode, and is implemented using the Integrated Common Framework (ICF) component.
The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Governance connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped along with Oracle Identity Governance. Therefore, you need not configure or modify the ICF.
This connector enables management of target system accounts through Oracle Identity Governance. Figure 1-1 shows the architecture of the connector.
Figure 1-1 Architecture of the UNIX Connector
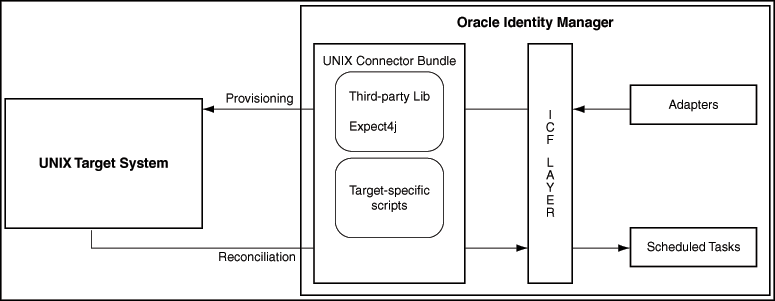
Description of "Figure 1-1 Architecture of the UNIX Connector "
As shown in this figure, the UNIX connector enables you to use the target system as a managed resource (target) or as an authoritative (trusted) source of identity data for Oracle Identity Governance.
In the target mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Governance. In addition, you can use Oracle Identity Governance to perform provisioning operations on the target system.
In the authoritative configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Governance.
Provisioning involves creating and managing user accounts. When you allocate (or provision) a UNIX resource to an OIM User, the operation results in the creation of an account on the target system for that user. Similarly, when you update the resource on Oracle Identity Governance, the same update is made to the account on the target system.
During provisioning operations, adapters carry provisioning data submitted through the process form to the Expect4j third-party library, which in turn submits the provisioning data to the target system. The user account maintenance commands accept provisioning data from the adapters, carry out the required operation on the target system, and return the response from the target system to the adapters. The adapters return the response to Oracle Identity Governance.
1.6 Supported Connector Features Matrix
Provides the list of features supported by the AOB application and CI-based connector.
Table 1-3 Supported Connector Features Matrix
| Feature | AOB Application | CI-Based Connector |
|---|---|---|
|
Switch between SSH and Telnet protocols to connect to UNIX-based target systems |
Yes |
Yes |
|
Run scripts on a computer where the UNIX connector is deployed |
Yes |
Yes |
|
Configure the connector to support an additional flavor of UNIX by using custom scripts |
Yes |
Yes |
|
Support multiple instances and multiple versions of UNIX |
Yes |
Yes |
|
Integrate the target system as a target resource and an authoritative source of Oracle Identity Governance |
Yes |
Yes |
|
Perform full and incremental reconciliation |
Yes |
Yes |
|
Perform limited reconciliation |
Yes |
Yes |
|
Perform batched reconciliation |
Yes |
Yes |
|
Configure validation and transformation of account data |
Yes |
Yes |
|
Use connector server |
Yes |
Yes |
|
Reconcile user account status information from the target system |
Yes |
Yes |
|
Add custom attributes for reconciliation and provisioning |
Yes |
Yes |
1.7 Connector Features
The features of the connector include support for connector server, target resource and trusted source reconciliation, configuring custom scripts to support additional flavors of UNIX, reconciliation of all existing or modified account data, limited and batched reconciliation, transformation and validation of account data during reconciliation and provisioning, and so on.
The following are the features of this connector:
1.7.1 Support for Switching Between SSH and Telnet Protocols
You can switch between SSH and Telnet protocols to connect to UNIX-based target systems. You can specify the connection type by using the connectionType parameter of the IT Resource.
The connector supports the following connection types:
-
SSH - This is the default connection. Used for SSH with password-based authentication.
-
SSHPUBKEY - Used for SSH with key-based authentication.
-
TELNET - Used for Telnet connection.
See Basic Configuration Parameters for related information.
1.7.2 Support for Running Custom Scripts
You can run scripts on a computer where the UNIX connector is deployed. You can configure custom scripts to support additional flavors of UNIX.
You can configure the scripts to run before or after the create, update, or delete an account provisioning operations. For example, you could configure a script to run before a user is created by the connector. See Configuring Action Scripts for more information.
1.7.3 Support for Configuring the Connector for a New Target System
You can configure the connector to support an additional flavor of UNIX by using custom scripts.
By default, the connector uses pre-configured scripts to support AIX, HP-UX, Linux, and Solaris. You can customize these scripts to support an additional flavor of UNIX. See Configuring the Connector for a New Target System for more information.
1.7.4 Support for Multiple Instances and Multiple Versions of UNIX
The connector supports multiple instances and multiple versions of UNIX.
You can deploy a single connector bundle on Oracle Identity Governance and create multiple instances and multiple versions of UNIX. Then, you can use Oracle Identity Governance to manage accounts on these target systems. See Configuring the Connector for Multiple Installations of the Target System for more information.
1.7.5 Support for Both Target Resource and Trusted Source Reconciliation
You can use the connector to configure the target system as either a target resource or trusted source of Oracle Identity Governance.
See Configuring Reconciliation for more information.
1.7.6 Support for Both Full and Incremental Reconciliation
After you create the application, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Governance. After the first full reconciliation run, incremental reconciliation is automatically enabled from the next run of the user reconciliation.
You can perform a full reconciliation run at any time. See Performing Full Reconciliation for more information.
1.7.7 Support for Limited Reconciliation
You can set a reconciliation filter as the value of the Filter attribute of the scheduled tasks. This filter specifies the subset of newly added and modified target system records that must be reconciled.
See Performing Limited Reconciliation for more information.
1.7.8 Support for Batched Reconciliation
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
See Performing Batched Reconciliation for more information.
1.7.9 Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not wish to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements.
For information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Server, see Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance.
1.7.10 Transformation and Validation of Account Data
You can configure transformation and validation of account data that is brought into or sent from Oracle Identity Governance during reconciliation and provisioning operations by writing Groovy scripts while creating your application.
For more information, see Validation and Transformation of Provisioning and Reconciliation Attributes in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.