2 Creating an Application By Using the UNIX Connector
Learn about onboarding applications using the connector and the prerequisites for doing so.
2.1 Process Flow for Creating an Application By Using the Connector
From Oracle Identity Governance release 12.2.1.3.0 onward, connector deployment is handled using the application onboarding capability of Identity Self Service.
Figure 2-1 is a flowchart depicting high-level steps for creating an application in Oracle Identity Governance by using the connector installation package.
Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector
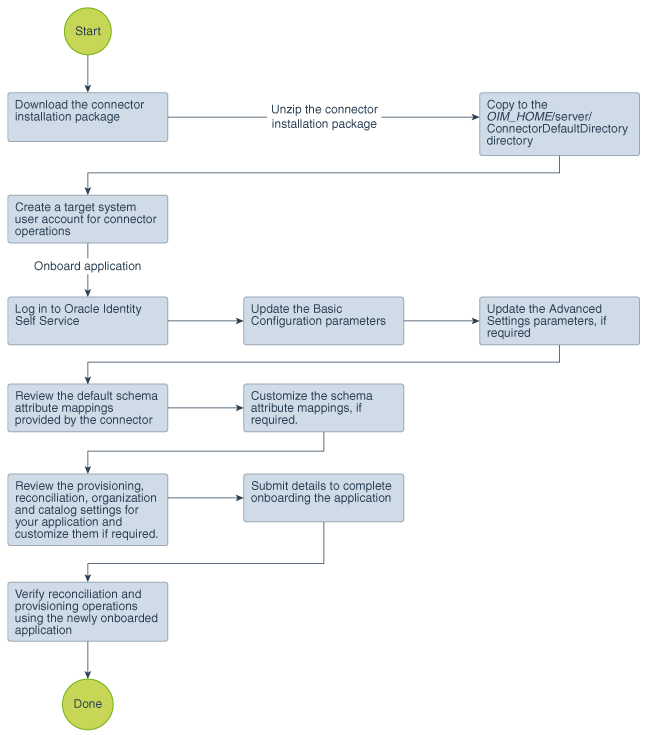
Description of "Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector"
2.2 Prerequisites for Creating an Application By Using the Connector
Learn about the tasks that you must complete before you create the application.
2.2.1 Downloading the Connector Installation Package
You can obtain the installation package for your connector on the Oracle Technology Network (OTN) website.
2.2.2 Configuring the Target System
Depending on the target system and your requirements, perform these procedures to configure your environment, install OpenSSH, create a target system user account with the minimum permissions required to perform connector operations, create an RBAC user account, and configure public key and SSH public key authentication.
2.2.2.1 Configuring Solaris, Linux, and AIX
Perform the following steps to configure Solaris, Linux, and AIX environments:
2.2.2.2 Configuring HP-UX
Perform the following steps for HP-UX environments:
-
If you want to switch to HP-UX Trusted mode, then:
Note:
If you are converting the target system to the trusted system, then please make sure that no shadow file exists on the target after it is converted to trusted system. You can use
pwunconvcommand to get rid of the shadow file, if it exists.-
Log in as root and then run the following command:
/usr/bin/sam
/usr/sbin/sam
-
Select Auditing and Security and then select System Security Policies. A message is displayed asking if you want to switch to the trusted mode.
-
Click Yes. The following message is displayed:
System changed successfully to trusted system
-
-
Ensure that the /etc/passwd and /etc/shadow directories are available on the target server.
-
Create a directory on the target system where the connector can create mirror files for the /etc/passwd and /etc/shadow files.
This directory is specified in the Mirror Files Location parameter. The default value is
/etc/connector_mirror_filesfor a Target application and/etc/connector_mirror_files_trustedfor an Authoritative application. If the directory path is different from the default value, then you must update the parameter value. The loginUser (sudo or root user) must have read and write privileges to this directory.
2.2.2.3 Installing OpenSSH
Perform the following procedures to install OpenSSH on the target system:
2.2.2.3.1 Installing OpenSSH for Solaris 9
Perform the following steps to install OpenSSH on Solaris 9:
2.2.2.3.2 Installing OpenSSH for Solaris 10 and Later Versions
By default, OpenSSH is installed on Solaris 10 and later versions. If it is not installed, then install the OpenSSH server from the operating system installation CD. To enable SSH, make the following changes in the /etc/ssh/ssh_config file:
2.2.2.3.3 Installing OpenSSH for HP-UX
If SSH is not installed on the UNIX server, then install the appropriate OpenSSH from the installation media.
2.2.2.3.4 Installing OpenSSH for Linux
By default, OpenSSH is installed on Red Hat Linux. If it is not installed, then install the OpenSSH server from the operating system installation CD.
2.2.2.4 Creating a Target System SUDO User Account for Connector Operations
Oracle Identity Governance uses a target system account for performing reconciliation and provisioning operations. On all supported target systems, this account must be either the root user or sudo user.
See Also:
Privileges Required for Performing Provisioning and Reconciliation for information about the privileges required to perform connector operations
To create a target system user account with the minimum permissions required to perform connector operations, perform the following procedure:
-
If SUDO is not installed on the target system, then install it from the installation media.
-
Use the
visudocommand to edit and customize the /etc/sudoers file according to your requirements.Note:
If you cannot use the
visudocommand to edit thesudoersfile, then:-
Enter the following command:
chmod 777 /etc/sudoers
-
Make the required changes in the
sudoersfile. -
Enter the following command:
chmod 440 /etc/sudoers
For example, if you have a group named
mqmon the Linux server and require all members of the group to act as SUDO users with all possible privileges, then thesudoersfile must contain the following line:mqm ALL= (ALL) ALL
This example is only a sample configuration. If you need other group members or individual users to be SUDO users with specific privileges, then edit this file as was done for the sample value
mqm.Therefore, the SUDO user must have the privileges required to run these commands.
Note:
NOPASSWD: ALLoption for any SUDO user or group is supported. To configure this, you need to update the Sudo Passwd Expect Expression parameter. See Advanced Settings Parameters. -
-
Edit the same
sudoersfile so that the SUDO user stays validated for 10 minutes after being validated once. You may need to increase the timeout if the reconciliation operation takes longer than 10 minutes and if you encounter errors such as "Permission denied". At the beginning of each operation, the connector validates the user usingsudo -voption so that the operation stays validated for a maximum of 10 minutes. After carrying out the operation, the connector runs thesudo -kto kill the validation.Add the following line under the
# Defaults specificationheader:Defaults timestamp_timeout=10
This is a prerequisite for this connector to work successfully.
-
Create a SUDO user as follows:
-
Enter the following command:
useradd -g group_name -d /home/directory_name -m user_name
In this command:
group_nameis the SUDO users group for which there is an entry in the/etc/sudoersfile.directory_nameis the name of the directory in which you want to create the default directory for the user. -
In the .bash_profile file, which is created in the /home/directory_name directory, add the following lines to set the
PATHenvironment variable:PATH=/usr/sbin:$PATH export PATH
-
-
In the sudo user's .bashrc, .cshrc, or .kshrc file, which is created in the sudo user's home directory, add the following line to change the prompt end character from $ (dollar sign) to # (pound sign):
PS1="[\\u@\\h:\\w]#"
The encrypted passwords in the shadow file contain $ (dollar sign), which matches the default prompt end character. You must change the prompt end character to ensure that changes made to the shadow file are reconciled correctly.
-
Login with the sudo user.
-
Run the
sudo -kcommand on the target system to clear the validation. -
Run the
sudo -vcommand on the target system and ensure that the password prompt is displayed.The connector would not work if the sudo user is not prompted for password at this step.
2.2.2.5 Creating an RBAC User Account for Connector Operations on Solaris
On Solaris, you can either create a sudo user or apply the role-based access control (RBAC) feature to create an account and assign to it the minimum privileges required for connector operations.
Note:
You use the RBAC Role Expect Expressions parameter to specify if you want to use an RBAC user. See Advanced Settings Parameters.
To create an RBAC user account:
-
Run the following command to create a role for the user.
roleadd -d /export/home/ROLE_NAME -m ROLE_NAME
In this command, replace
ROLE_NAMEwith the name that you want to assign to the role, for example,OIMRole. -
Run the following command to assign a password to the role:
passwd ROLE_NAMEAt the prompt, enter a password for the role.
See Also:
Privileges Required for Performing Provisioning and Reconciliation for information about the privileges required to run the commands that are used for provisioning and reconciliation
-
Create a profile for the user as follows:
-
Open the /etc/security/prof_attr file in a text editor and insert the following line in the file:
PROFILE_NAME:::Oracle Identity Manager Profile:In this line, replace
PROFILE_NAMEwith the name that you want to assign to the profile, for example,OIMProf. -
Save and close the file.
-
-
Add execution attribute entries in the /etc/security/exec_attr file. Each entry defines a task to be run and the uid that the role will assume when running the task.
Open the /etc/security/exec_attr file in a text editor, and insert the following lines:
Note:
There are seven fields in this file, and the colon (:) is used as the delimiting character.
On Solaris 10, the value
susercan be replaced withsolaris.Some of the entries contain
euid. These instances ofeuidcan be replaced withuid.PROFILE_NAME:suser:cmd:::/usr/sbin/usermod:uid=0 PROFILE_NAME:suser:cmd:::/usr/sbin/useradd:uid=0 PROFILE_NAME:suser:cmd:::/usr/sbin/userdel:uid=0 PROFILE_NAME:suser:cmd:::/usr/bin/passwd:uid=0 PROFILE_NAME:suser:cmd:::/usr/bin/cat:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/diff:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/sort:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/rm:uid=0 PROFILE_NAME:suser:cmd:::/usr/bin/grep:euid=0 PROFILE_NAME:suser:cmd:::/usr/bin/egrep:euid=0 PROFILE_NAME:suser:cmd:::/bin/echo:euid=0 PROFILE_NAME:suser:cmd:::/bin/sed:euid=0
You can add similar entries for other commands if you have customized the pre-configured Solaris scripts to use other commands.
-
Run the following command to associate the profile with the role:
rolemod -P PROFILE_NAME ROLE_NAME
-
Run the following command to create the user:
useradd -d /export/home/USER_NAME -m USER_NAME
-
Run the following command to assign a password to the user:
passwd USER_NAME -
Run the following command to grant the role to the user:
usermod -R ROLE_NAME USER_NAME
-
To verify the changes that you have made, open the /etc/user_attr file in a text editor and verity that the following entries are present in the file:
ROLE_NAME::::type=role;profiles=PROFILE_NAME USER_NAME::::type=normal;roles=ROLE_NAME
2.2.2.6 Configuring Public Key Authentication
To configure Public Key Authentication:
Note:
-
If Public Key Authentication is used, then an RBAC user for a Solaris target system cannot be used.
-
This section contains the procedure to configure Public Key Authentication for a root user. It can also be configured for a SUDO user.
2.2.2.7 Configuring SSH Public Key Authentication
Depending on the target system and your requirements, perform some of the following procedures to configure SSH Public Key Authentication:
2.2.2.7.1 Configuring SSH Public Key Authentication for Solaris
Perform the following steps to configure SSH Public Key Authentication on Solaris:
2.2.2.7.2 Configuring SSH Public Key Authentication for HP-UX
Perform the following steps to configure SSH Public Key Authentication on HP-UX:
2.2.2.7.3 Configuring SSH Public Key Authentication for Linux
Perform the following steps to configure SSH Public Key Authentication on Linux:
2.3 Creating an Application By Using the Connector
You can onboard an application into Oracle Identity Governance from the connector package by creating a target or an authoritative application. To do so, you must log in to Identity Self Service and then choose the Applications box on the Manage tab.
Note:
For detailed information on each of the steps in this procedure, see Creating Applications of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
- Create an application in Identity Self Service. The high-level steps are as follows:
- Verify reconciliation and provisioning operations on the newly created application.
See Also:
-
Configuring the UNIX Connector for details on basic configuration and advanced settings parameters, default user account attribute mappings, default correlation rules, and reconciliation jobs that are predefined for this connector
-
Configuring Oracle Identity Governance for details on creating a new form and associating it with your application, if you chose not to create the default form