1 About the WebEx Connector
Oracle Identity Governance is a centralized identity management solution that provides self service, compliance, provisioning and password management services for applications residing on-premises or on the Cloud. Oracle Identity Governance connectors are used to integrate Oracle identity Governance with the external identity-aware applications.
Note:
In this guide, the connector that is deployed using the Applications option on the Manage tab of Identity Self Service is referred to as an AOB application. The connector that is deployed using the Manage Connector option in Oracle Identity System Administration is referred to as a CI-based connector (Connector Installer-based connector).Application onboarding is the process of registering or associating an application with Oracle Identity Governance and making that application available for provisioning and reconciliation of user information.
Note:
In this guide, WebEx is sometimes referred to as the target system.
The following topics provide a high-level overview of the WebEx connector:
Note:
In this guide, the term Oracle Identity Governance server refers to the computer on which Oracle Identity Governance is installed.Certified Components
These are the software components and their versions required for installing and using the connector.
Note:
If you are using Oracle Identity Manager release 11.1.x, then you can install and use the connector only in the CI-based mode. If you want to use the AOB application, then you must upgrade to Oracle Identity Governance release 12.2.1.3.0.
Table 1-1 Certified Components
| Component | Requirement for AOB Application | Requirement for CI-Based Connector |
|---|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use any one of the following releases:
|
You can use one of the following releases:
|
|
Target System |
Cisco WebEx |
Cisco WebEx |
|
Connector Server |
12.2.1.3.1 or 12.2.1.3.0 |
12.2.1.3.1 or 12.2.1.3.0 |
|
Connector Server JDK |
For Connector Server 12.2.1.3.1, use JDK 17 or later For Connector Server 12.2.1.3.0, use JDK 8 or later |
For Connector Server 12.2.1.3.1, use JDK 17 or later For Connector Server 12.2.1.3.0, use JDK 8 or later |
Usage Recommendation
These are the recommendations for the WebEx connector versions that you can deploy and use depending on the Oracle Identity Governance or Oracle Identity Manager version that you are using.
-
If you are using Oracle Identity Governance release 12c (12.2.1.3.0) or Oracle Identity Governance 14c (14.1.2.1.0) or later, then use the latest 12.2.1.x version of this connector. Deploy the connector using the Applications option on the Manage tab of Identity Self Service.
-
If you are using any of the Oracle Identity Manager releases listed in the “Requirement for CI-Based Connector” column of Table 1-1, then use the 11.1.1.x version of the WebEx connector. If you want to use the 12.2.1.x version of this connector, then you can install and use it only in the CI-based mode. If you want to use the AOB application, then you must upgrade to Oracle Identity Governance release 12c (12.2.1.3.0) or later.
Note:
If you are using the latest 12.2.1.x version of the Webex connector in the CI-based mode, then see Oracle Identity Manager Connector Guide for WebEx, Release 11.1.1 for complete details on connector deployment, usage, and customization.Certified Languages
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English (US)
-
Finnish
-
French
-
French (Canadian)
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
Supported Connector Operations
These are the list of operations that the connector supports for your target system.
Table 1-2 Supported Connector Operations
| Operation | Supported? |
|---|---|
|
User Management |
|
|
Create User |
Yes |
|
Recon User |
Yes |
|
Update User |
Yes |
|
Delete User |
Yes |
|
Set Password |
Yes |
|
Reset Password |
Yes |
|
Enable User |
Yes |
|
Disable User |
Yes |
|
Meeting Type Management |
|
|
Add MeetingTypes |
Yes |
|
Add multiple MeetingTypes |
Yes |
|
Update MeetingTypes |
Yes |
|
Update multiple MeetingTypes |
Yes |
|
Remove MeetingTypes |
Yes |
|
Remove multiple MeetingTypes |
Yes |
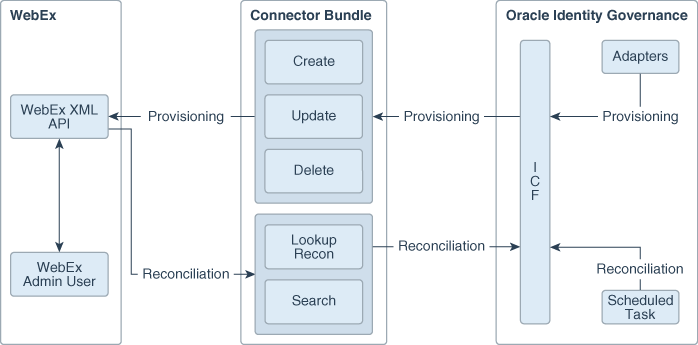
Connector Architecture
The WebEx connector is implemented by using the Identity Connector Framework (ICF).
The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Governance connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped along with Oracle Identity Governance. Therefore, you need not configure or modify the ICF.
Figure 1-1 shows the architecture of the WebEx connector.
As shown in this figure, the connector enables you to use the target system as a managed resource (target) of identity data for Oracle Identity Governance. In this mode, the connector enables the following operations:
-
Provisioning
Provisioning involves creating, updating, enabling, disabling or deleting users on the target system through Oracle Identity Governance. During provisioning, the Adapters invoke ICF operation, ICF inturn invokes create operation on the WebEx Connector Bundle and then the bundle calls the target system API for provisioning operations. The WebEx XML API on the target system accepts provisioning data from the bundle, carries out the required operation on the target system, and returns the response from the target system back to the bundle, which passes it to the adapters.
-
Target Resource Reconciliation
During reconciliation, a scheduled task invokes an ICF operation. ICF in turn invokes a search operation on the WebEx Connector Bundle and then the bundle calls WebEx XML API for reconciliation operation. The API extracts user records that match the reconciliation criteria and hands them over through the bundle and ICF back to the scheduled task, which brings the records to Oracle Identity Governance.
Each record fetched from the target system is compared with WebEx resources that are already provisioned to Oracle Identity Governance Users. If a match is found, then the update made to the WebEx record from the target system is copied to the WebEx resource in Oracle Identity Governance. If no match is found, then the user ID of the record is compared with the user ID of each Oracle Identity Governance User. If a match is found, then data in the target system record is used to provision a WebEx resource to the Oracle Identity Governance User.
The WebEx Identity Connector Bundle communicates with the WebEx XML API using the HTTPS protocol. The WebEx XML API provides programmatic access through REST API endpoints. Apps can use the WebEx API to perform create, read, update, and delete (CRUD) operations on directory data and directory objects, such as users.
Supported Use Cases
WebEx provides on-demand collaboration, online meeting, web conferencing, and video conferencing applications. Each user should have a valid subscription for using the WebEx services. The WebEx connector is used to integrate Oracle Identity Governance with WebEx to ensure that all WebEx accounts are created, updated, and deactivated on an integrated cycle with the rest of the identity-aware applications in your enterprise.
While most of the organizations are leveraging WebEx services, a vital drawback is that an Admin user needs to manage all user identities and subscriptions manually. Since it is a time and effort consuming process for an administrator, it is advisable to use the WebEx connector. The connector automates the process of managing user identities and subscriptions and additionally reduces the burden of managing the whole life cycle of a WebEx user manually. The WebEx connector automates the process of user account provisioning, de-provisioning and subscription without any Admin intervention. Another important challenge faced is that all users are placed at a central location where the Admin can apply various organizational policies for WebEx users and generate an audit report for the same. This process is also automatically managed by the WebEx connector. To overcome these challenges, a quick and easy solution is to install the WebEx connector and configure it with your target system by providing connection information in the IT resource.
The WebEx Connector enables Oracle Identity Governance to manage all WebEx users at a single place where WebEx accounts are automatically provisioned or de-provisioned based upon the defined policies in Oracle Identity Governance respective to account users. With the help of Oracle Identity Governance, the WebEx connector Admin can perform all operations in Oracle Identity Governance and apply all Identity and Access Management features accordingly. The WebEx connector provides the ability to manage accounts and related operations across all applications without spending additional resources and time.
Supported Connector Features Matrix
Provides the list of features supported by the AOB application and CI-based connector.
Table 1-3 Supported Connector Features Matrix
| Feature | AOB Application | CI-Based Connector |
|---|---|---|
|
Perform full reconciliation |
Yes |
Yes |
|
Perform limited reconciliation |
Yes |
Yes |
|
Support for Connector Server |
Yes |
Yes |
|
Configure validation and transformation of account data |
Yes |
Yes |
|
Perform connector operations in multiple domains |
Yes |
Yes |
|
Support for paging |
Yes |
Yes |
|
Test connection |
Yes |
No |
|
Reset password |
Yes |
Yes |
|
Clone applications or create new application instances |
Yes |
Yes |
|
Provide secure communication to the target system through SSL |
Yes |
Yes |
Connector Features
The features of the connector include support for provisioning user accounts, target resource reconciliation, reconciliation of all existing account data, limited reconciliation, transformation and validation of account data during reconciliation and provisioning, support for the connector server, multiple installations of the target system, secure communication to the target system through SSL, and so on.
Support for Full Reconciliation
After you create the application, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Governance.
You can perform a full reconciliation run at any time. See Performing Full Reconciliation.
Support for Limited (Filtered) Reconciliation
You can reconcile records from the target system based on a specified filter criterion.
You can set a reconciliation filter as the value of the Filter attribute of the user reconciliation scheduled job. This filter specifies the subset of newly added and modified target system records that must be reconciled. The Filter attribute helps you to assign filters to the API based on which you will get a filtered response from target system.
Support for the Connector Server
Connector Server is one of the features provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles.
A Java connector server is useful when you do not wish to execute a Java connector bundle in the same VM as your application. It can be beneficial to run a Java connector on a different host for performance improvements.
For information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Server, see Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance.
Transformation and Validation of Account Data
You can configure transformation and validation of account data that is brought into or sent from Oracle Identity Governance during reconciliation and provisioning operations by writing Groovy scripts while creating your application.
For more information, see Validation and Transformation of Provisioning and Reconciliation Attributes in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Support for Cloning Applications and Creating Instance Applications
You can configure this connector for multiple installations of the target system by cloning applications or by creating instance applications.
When you clone an application, all the configurations of the base application are copied into the cloned application. When you create an instance application, it shares all configurations as the base application.
For more information about these configurations, see Cloning Applications and Creating Instance Applications in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Secure Communication to the Target System
To provide secure communication to the target system, SSL is required. You can configure SSL between Oracle Identity Governance and the Connector Server and between the Connector Server and the target system.
If you do not configure SSL, passwords can be transmitted over the network in clear text. For example, this problem can occur when you are creating a user or modifying a user's password.