3 Configuring the Microsoft Active Directory User Management Connector
While creating an application, you must configure connection-related parameters that the connector uses to connect Oracle Identity Governance with your target system and perform connector operations. In addition, you can view and edit attribute mappings between the process form fields in Oracle Identity Governance and target system columns, predefined correlation rules, situations and responses, and reconciliation jobs.
Basic Configuration Parameters
These are the connection-related parameters that Oracle Identity Governance requires to connect to Microsoft Active Directory or Microsoft AD LDS. These parameters are common for both target applications and authoritative applications.
Table 3-1 Parameters in the Basic Configuration Section for the Microsoft Active Directory User Management Connector
| Parameter | Mandatory? | Description |
|---|---|---|
|
Connector Server Name |
Yes |
If you are using this connector with a .NET Connector Server, then enter the name of Connector Server IT resource. Default value: |
|
Domain Name |
Yes |
Enter the domain name for the Microsoft Active Directory domain controller in which you are creating an application by using the connector. Sample value: Note: This is a mandatory parameter if you are using Microsoft Active Directory as the target system. |
|
Admin User Name |
Yes |
Enter the user name of account that you create by performing the procedure described in Creating a Target System User Account for Connector Operations. Enter the value for this parameter in the following format:
Sample value: Note: If you are using AD LDS as the target system and this machine belongs to a workgroup, then enter a value for this parameter. Enter a value for this parameter in the following format:
Sample value: |
|
Admin Password |
Yes |
Enter the password of the user account that you create by performing the procedure described in Creating a Target System User Account for Connector Operations. |
|
Container |
Yes |
Enter the fully qualified domain name of the user container into or from which users must be provisioned or reconciled into Oracle Identity Governance, respectively. Sample value: |
|
LDAP Host Name |
Yes |
Enter the host name, IP address, or domain name of the Microsoft Windows computer (target system host computer) on which Microsoft Active Directory is installed. Note: If you do not specify a value for this parameter and the Backup Host Names parameter (discussed later in this table), then a serverless bind is used. The connector leverages ADSI for determining the domain controller in the domain and then creates the directory entry. Therefore, all interactions with the target system are not specific to a domain controller. To determine the host name, on the computer hosting the target system, right-click My Computer and select Properties. On the Computer Name tab of the System Properties dialog box, the host name is specified as the value of the Full computer name field. Sample values: w2khost 172.20.55.120 example.com |
|
Domain Controller |
No |
Enter the name of the domain controller from which user accounts must be reconciled. Note: The value specified in this parameter is used if the value of the Search Child Domains parameter of Advanced Settings is set to no. If you specify no value for the Domain Controller parameter and the value of the Search Child Domains parameter is set to no, then the connector automatically finds a domain controller for the target system and reconciles users from it. Sample value: |
|
Port |
No |
Enter the number of the port at which Microsoft AD LDS is listening. Sample value: Note: Do not enter a value for this parameter if you are using Microsoft Active Directory as the target system. |
|
UseSSL |
No |
Enter yes if the target system has been configured for SSL. This enables secure communication between the Connector Server and target system. Otherwise, enter no. Default value: Note:
|
|
Backup Host Names |
No |
Enter the host name of the backup domain controller to which Oracle Identity Governance must switch to if the primary domain controller becomes unavailable. Sample value: Note: Multiple backup domain controllers must be separated by semicolon (;). |
|
Is ADLDS? |
No |
Enter yes to specify that the target system is Microsoft AD LDS. Enter no to specify that the target system is Microsoft Active Directory. Default value: |
|
Global Catalog Server |
No |
Enter the host on which the global catalog server is located. Note: The value specified in this parameter is used if you set the value of the Search Child Domains parameter to yes. If no value is specified for the Global Catalog Server parameter and the Search Child Domains parameter is set to yes, then the connector automatically finds a global catalog server for the target system, and then reconciles user accounts from the domain controller on which the global catalog server is running. It is strongly recommended to provide a value for this parameter if you have set the value of the Search Child Domains parameter to Sample value: |
Advanced Settings Parameters
These are the configuration-related entries that the connector uses during reconciliation and provisioning operations. These parameters are common for both target applications and authoritative applications.
Table 3-2 Advanced Setting Parameters for Oracle Database
| Parameter | Mandatory? | Description |
|---|---|---|
|
Object Class |
No |
This parameter holds the name of the object class to which the connector assigns newly created users on the target system. If you create a custom object class, then enter the name of that object class. For example, Default value: |
|
Lockout Threshold |
No |
Enter the number of unsuccessful login attempts after which a user's account must be locked. Note: This entry is applicable only for the Microsoft AD LDS target system. Default value: |
|
Always Use Object GUID? |
No |
This parameter specifies whether the connector must use the GUID of an object for searching records during reconciliation. Default value: Note: Do not change the value of this entry. |
|
Native Guid Convention |
No |
This parameter specifies whether GUID is stored in its native format. This entry is used by the connector internally. Default value: Note: Do not change the value of this entry. |
|
Page Size |
No |
Enter the page size of the records fetched by the connector in each call to the target system during a reconciliation run. Paging splits the entire result set of a query into smaller subsets called, appropriately enough, pages. In general, it is recommended to set this value to the maximum page size for simple searches. By setting the page size to the maximum value, you can minimize the network roundtrips necessary to retrieve each page, which tends to be a more expensive operation for simple searches. While it is possible to specify a PageSize greater than the MaxPageSize of the target system, the Active Directory server will ignore it and use the MaxPageSize instead. No exception will be generated in this case. In some cases, you might need to specify a smaller page size to avoid timeouts or overtaxing the server. Some queries are especially expensive, so limiting the number of results in a single page can help avoid this. Default value: |
|
Search Child Domains |
No |
This parameter determines the search scope of users, groups, or organizational units within the domain name specified as the value of the DomainName attribute. Enter no if you want the connector to search for users, groups, or organizational units only from the specified domain. The domain name is specified as the value of the DomainName attribute. Note that the connector fetches records from the domain controller that is specified as the value of the Domain Controller parameter of Basic Configuration. Enter yes if you want the connector to search for users, groups, or organizational units from the specified domain and its child domains. In this case, the global catalog server is used for fetching records. Note that you specify the global catalog server as the value of the Global Catalog Server parameter of Basic Configuration. Default value: no |
|
Connector Name |
Yes |
This parameter holds the name of the connector class. Value: |
|
Bundle Name |
Yes |
This parameter holds the name of the connector bundle package. Value: |
|
Bundle Version |
Yes |
This parameter hods the version of the connector bundle class. Value: 12.3.0.0 |
|
Recon Date Format |
No |
This parameter holds the format in which the last reconciliation run timing must be displayed. Default value: |
|
Maintain Hierarchy? |
No |
Enter yes to specify that you want to maintain in Oracle Identity Governance the same organization hierarchy that is maintained on the target system. Otherwise, enter no. Default value: |
|
Use Delete Tree For Accounts |
No |
This parameter specifies whether the associated leaf nodes of an __ACCOUNT__ object to be deleted are to be removed along with the object. If the value of this entry is not set to true and the __ACCOUNT__ object to be deleted has leaf nodes, then the operation fails and an error message is displayed. If the value of this entry is set to false, then the __ACCOUNT__ objects are removed from the child list of its parent only. Otherwise, regardless of the object class, the whole tree is removed recursively. Default value: |
|
Create Home Directory |
No |
This parameter holds the information whether a home directory must be created. Enter yes if you want the connector to create a home directory for user accounts. Otherwise, enter no. Default value: |
|
Pool Max Idle |
No |
Maximum number of idle objects in a pool. Default value: |
|
Pool Max Size |
No |
Maximum number of connections that the pool can create. Default value: |
|
Pool Max Wait |
No |
Maximum time, in milliseconds, the pool must wait for a free object to make itself available to be consumed for an operation. Default value: |
|
Pool Min Evict Idle Time |
No |
Minimum time, in milliseconds, the connector must wait before evicting an idle object. Default value: |
|
Pool Min Idle |
No |
Minimum number of idle objects in a pool. Default value: |
Attribute Mappings
The attribute mappings on the Schema page vary depending on whether you are creating a target application or an authoritative application.
Attribute Mappings for a Target Application
The Schema page for a target application displays the default schema (provided by the connector) that maps Oracle Identity Governance attributes to target system attributes. The connector uses these mappings during reconciliation and provisioning operations.
AD User Account Attributes
Table 3-3 lists the user-specific attribute mappings between the process form fields in Oracle Identity Governance and AD target system attributes. The table also lists whether a specific attribute is used during provisioning or reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit the default attribute mappings by adding new attributes or deleting existing attributes as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Note:
If you are using AD LDS as the target system, then you must perform the following on the default attribute mappings list of the Schema page:
-
Delete the rows containing the following Display Name attributes:
-
Redirection Mail Id
-
Terminal Allow Login
-
Terminal Home Directory
-
Terminal Profile Path
-
-
Update the “User Id” Display Name row with the following values:
-
In the Target Attribute column, replace sAMAccountName with __UPN_WO_DOMAIN__.
-
Deselect the Provision Field checkbox.
-
Select the Recon Field checkbox.
-
Table 3-3 Default Attribute Mappings for an AD User Account
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Provision Field? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|---|
|
User Id |
sAMAccountName |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
User Principal Name |
userPrincipalName |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
First Name |
givenName |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Middle Name |
middleName |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Last Name |
sn |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Full Name |
displayName |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Password Never Expires |
PasswordNeverExpires |
Boolean |
No |
Yes |
Yes |
No |
Not applicable |
|
User Must Change Password At Next Logon |
__PASSWORD_EXPIRED__ |
Boolean |
No |
Yes |
Yes |
No |
Not applicable |
|
Account is Locked out |
__LOCK_OUT__ |
Boolean |
No |
Yes |
Yes |
No |
Not applicable |
|
Telephone Number |
telephoneNumber |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Account Expiration Date |
__PASSWORD_EXPIRATION_DATE__ |
Date |
No |
Yes |
Yes |
No |
Not applicable |
|
E Mail |
|
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Post Office Box |
postOfficeBox |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
City |
l |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
State |
st |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Zip |
postalCode |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Home Phone |
homePhone |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Mobile |
mobile |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Pager |
pager |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Fax |
facsimileTelephoneNumber |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Title |
title |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Department |
department |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Company |
company |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Manager Name |
manager |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Office |
physicalDeliveryOfficeName |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Country |
c |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Street |
streetAddress |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Terminal Home Directory |
TerminalServicesHomeDirectory |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Terminal Allow Login |
AllowLogon |
Boolean |
No |
Yes |
Yes |
No |
Not applicable |
|
Terminal Profile Path |
TerminalServicesProfilePath |
String |
No |
Yes |
Yes |
No |
Not applicable |
|
Status |
__ENABLE__ |
String |
No |
No |
Yes |
No |
Not applicable |
|
AD Server |
Long |
Yes |
No |
Yes |
Yes |
No |
|
|
Unique Id |
__UID__ |
String |
No |
No |
Yes |
Yes |
No |
|
Common Name |
cn |
String |
Yes |
No |
Yes |
No |
Not applicable |
|
Organization Name |
ad_container |
String |
Yes |
No |
Yes |
No |
Not applicable |
|
Password |
__PASSWORD__ |
String |
No |
Yes |
No |
No |
Not applicable |
|
Password Not Required |
PasswordNotRequired |
Boolean |
No |
Yes |
No |
No |
Not applicable |
|
Homedirectory |
homeDirectory |
String |
No |
Yes |
No |
No |
Not applicable |
|
Redirection Mail Id |
__MAILREDIRECTION__ |
String |
No |
Yes |
No |
No |
Not applicable |
|
User Full DN |
__NAME__ |
String |
No |
Yes |
No |
No |
Not applicable |
Figure 3-1 shows the default User account attribute mappings for an AD Target application.
Figure 3-1 Default Attribute Mappings for an AD User Account
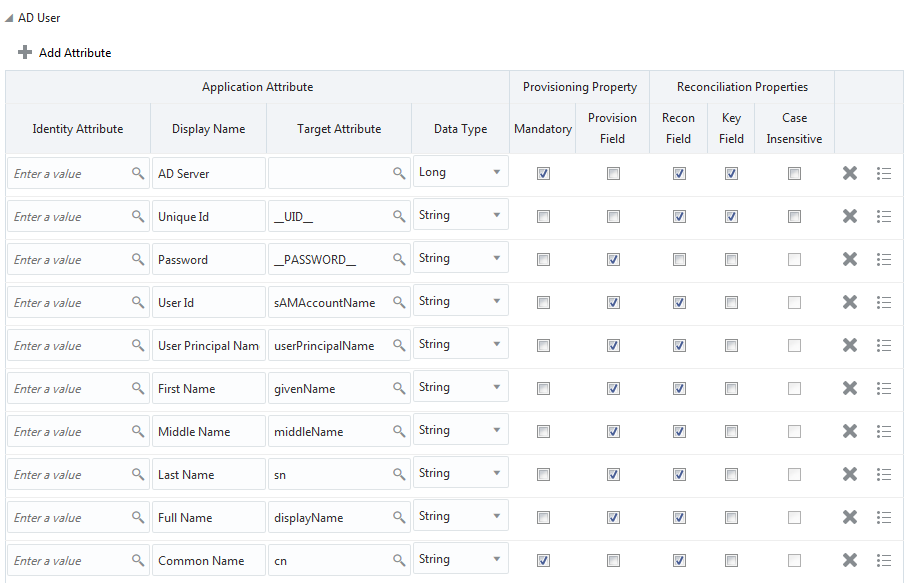
Description of "Figure 3-1 Default Attribute Mappings for an AD User Account"
Group Entitlement Attributes
Table 3-4 lists the groups-specific attribute mappings between the process form fields in Oracle Identity Governance and target system attributes. The table lists whether a given attribute is mandatory during provisioning. It also lists whether a given attribute is used during reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit the default attribute mappings by adding new attributes or deleting existing attributes as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-4 Default Attribute Mappings for a Group Entitlement
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|
|
Group Name |
__GROUPS__ |
String |
No |
Yes |
Yes |
No |
Figure 3-2 shows the default Group entitlement mapping.
Figure 3-2 Default Attribute Mappings for a Group Entitlement
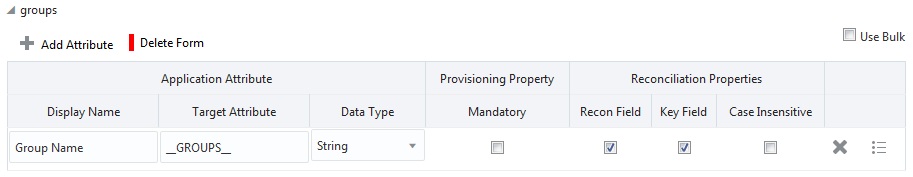
Description of "Figure 3-2 Default Attribute Mappings for a Group Entitlement"
Attribute Mappings for an Authoritative Application
The Schema page for an authoritative application displays the default schema (provided by the connector) that maps Oracle Identity Governance attributes to target system attributes. The connector uses these mappings during reconciliation operations.
Table 3-5 lists the user-specific attribute mappings between the reconciliation fields in Oracle Identity Governance and AD target system attributes. The table also lists the data type for a given attribute and specified whether it is a mandatory attribute for reconciliation.
If required, you can edit these attributes mappings by adding new attributes or deleting existing attributes on the Schema page as described in Creating an Authoritative Application in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
You may use the default schema that has been set for you or update and change it before continuing to the next step.
The Organization Name, Xellerate Type, and Role identity attributes are mandatory fields on the OIG User form that cannot be left blank during reconciliation. As there are no corresponding attributes in the target system for the Organization Name, Xellerate Type, and Role identity attributes, they have been mapped to attributes in Oracle identity Governance. In addition, the connector provides default values (as listed in the “Default Value for Identity Display Name” column of Table 3-5) that it can use during reconciliation. For example, the default target attribute value for the Organization Name attribute is Xellerate Users. This implies that the connector reconciles all target system user accounts into the Xellerate Users organization in Oracle Identity Governance. Similarly, the default attribute value for Xellerate Type attribute is End-User, which implies that all reconciled user records are marked as end users.
Note:
If you are using AD LDS as the target system, then you must perform the following on the default attribute mappings list of the Schema page:
-
Delete the row containing the Manager Login Display Name attribute.
-
In the “User Login” Display Name row, update the Target Attribute mapping by replacing sAMAccountName with __UPN_WO_DOMAIN__.
Table 3-5 AD User Account Schema Attributes for an Authoritative Application
| Identity Display Name | Target Attribute | Data Type | Mandatory Reconciliation Property? | Recon Field? | Default Value for Identity Display Name |
|---|---|---|---|---|---|
|
Manager Login |
Manager Id |
String |
No |
Yes |
NA |
|
Status |
__ENABLE__ |
String |
No |
Yes |
NA |
|
ObjectGUID |
__UID__ |
String |
No |
Yes |
NA |
|
User Login |
sAMAccountName |
String |
No |
Yes |
NA |
|
First Name |
givenName |
String |
No |
Yes |
NA |
|
Last Name |
sn |
String |
No |
Yes |
NA |
|
Middle Name |
middleName |
String |
No |
Yes |
NA |
|
Xellerate Type |
OIM User Type |
String |
No |
Yes |
End-User |
|
Role |
OIM Employee Type |
String |
No |
Yes |
Full-Time |
|
Organization Name |
__PARENTCN__ |
String |
No |
Yes |
Xellerate Users |
|
|
|
String |
No |
Yes |
NA |
Figure 3-3 shows the default AD User account attribute mappings for an AD authoritative application.
Figure 3-3 Default Attribute Mappings for an AD User Account in an Authoritative Application
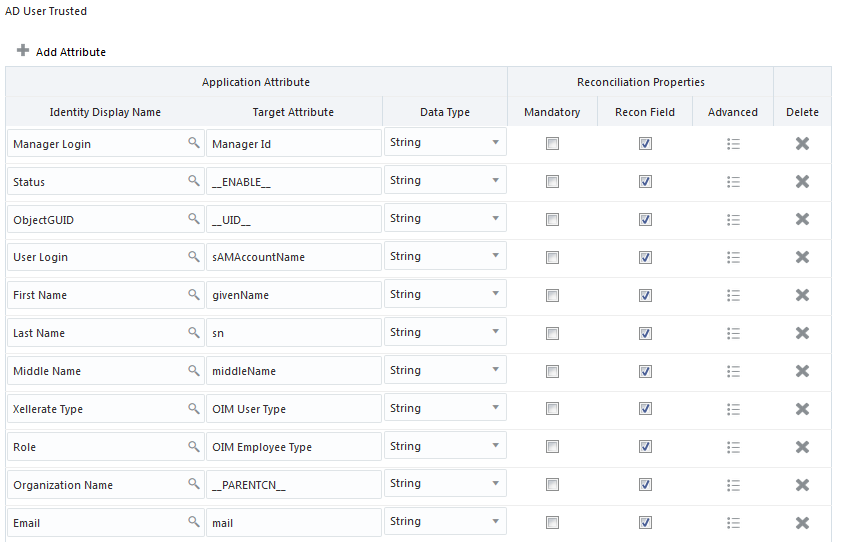
Description of "Figure 3-3 Default Attribute Mappings for an AD User Account in an Authoritative Application"
Correlation Rules for the Connector
Learn about the predefined rules, responses and situations for Target and Authoritative applications. The connector use these rules and responses for performing reconciliation.
Correlation Rules for a Target Application
When you create a Target application, the connector uses correlation rules to determine the identity to which Oracle Identity Governance must assign a resource.
Predefined Identity Correlation Rules
By default, the Active Directory User Management connector provides a simple correlation rule when you create a Target application. The connector uses this correlation rule to compare the entries in Oracle Identity Governance repository and the target system repository, determine the difference between the two repositories, and apply the latest changes to Oracle Identity Governance.
Table 3-6 lists the default simple correlation rule for an AD target system. If required, you can edit the default correlation rule or add new rules. You can create complex correlation rules also. For more information about adding or editing simple or complex correlation rules, see Updating Identity Correlation Rule in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-6 Predefined Identity Correlation Rule for an AD Target Application
| Target Attribute | Element Operator | Identity Attribute | Case Sensitive? |
|---|---|---|---|
|
__UID__ |
Equals |
ObjectGUID |
No |
|
sAMAccountName |
Equals |
User Login |
No |
Note:
If you are using Microsoft AD LDS as the target system, then you must update the identity reconciliation rule by replacing sAMAccountName in the Target Attribute column with userPrincipalName.
The identity correlation rule for an AD target application is as follows:
(__UID__ Equals ObjectGUID) OR (sAMAccountName Equals User Login)
The identity correlation rule for an AD LDS target application is as follows:
(__UID__ Equals ObjectGUID) OR (userPrincipalName Equals User Login)
-
__UID__ is an attribute on the target system that uniquely identifies the user account.
-
ObjectGUID is the unique identifier of the resource assigned to the OIG User.
-
For an AD target application, sAMAccountName is a field on Microsoft Active Directory that represents the login name of the user account.
-
For an AD LDS target application, For an AD LDS target application, userPrincipalName is a field on AD LDS that represents the domain-specific name of the user.
-
User Login is the field on the OIM User form.
Both the rule components are joined using the OR logical operator.
Figure 3-4 shows the simple correlation rule for this connector that is applicable to both AD and AD LDS target systems.
Figure 3-4 Simple Correlation Rule for a Target Application
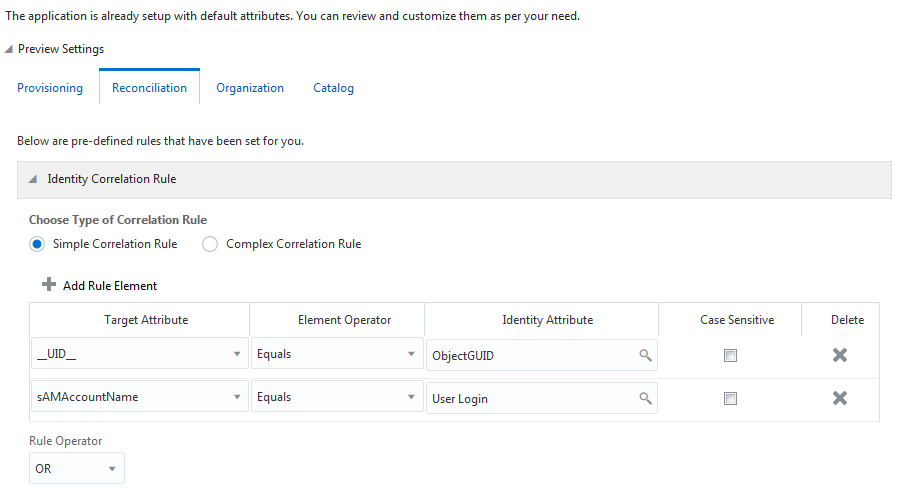
Description of "Figure 3-4 Simple Correlation Rule for a Target Application"
Predefined Situations and Responses
The Active Directory User Management connector provides a default set of situations and responses when you create a Target application. These situations and responses specify the action that Oracle Identity Governance must take based on the result of a reconciliation event.
Table 3-7 lists the default situations and responses for this connector that is applicable to both AD and AD LDS target systems. If required, you can edit these default situations and responses or add new ones. For more information about adding or editing situations and responses, see Updating Situations and Responses in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-7 Predefined Situations and Responses for a Target Application
| Situation | Response |
|---|---|
|
No Matches Found |
Assign to Administrator With Least Load |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Figure 3-5 shows the situations and responses that the connector provides by default for both AD and AD LDS target applications.
Figure 3-5 Predefined Situations and Responses for a Target Application
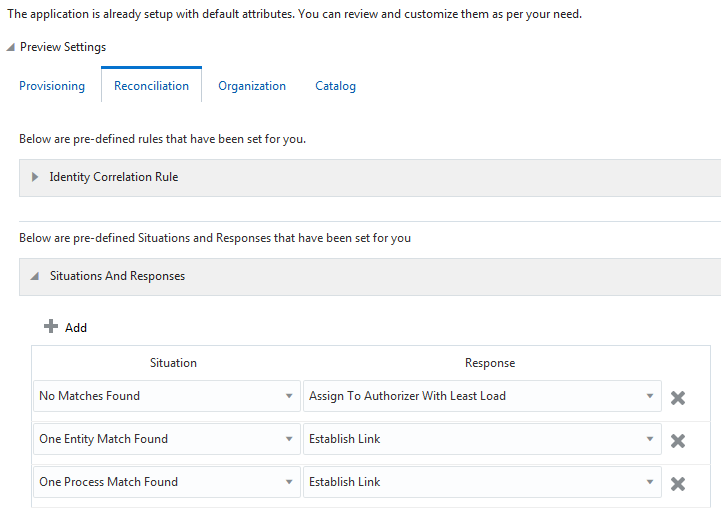
Description of "Figure 3-5 Predefined Situations and Responses for a Target Application"
Correlation Rules for an Authoritative Application
When you create an Authoritative application, the connector uses correlation rules to determine the identity that must be reconciled into Oracle Identity Governance.
Predefined Identity Correlation Rules
By default, the Active Directory User Management connector provides a simple correlation rule when you create an Authoritative application. The connector uses this correlation rule to compare the entries in Oracle Identity Governance repository and the target system repository, determine the difference between the two repositories, and apply the latest changes to Oracle Identity Governance.
Table 3-8 lists the default simple correlation rule for an AD authoritative application. If required, you can edit the default correlation rule or add new rules. You can create complex correlation rules also. For more information about adding or editing simple or complex correlation rules, see Updating Identity Correlation Rule in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-8 Predefined Identity Correlation Rule for an AD Authoritative Application
| Target Attribute | Element Operator | Identity Attribute | Case Sensitive? |
|---|---|---|---|
|
__UID__ |
Equals |
ObjectGUID |
No |
|
sAMAccountName |
Equals |
User Login |
No |
Note:
If you are using Microsoft AD LDS as the target system, then you must update the identity reconciliation rule by replacing sAMAccountName in the Target Attribute column with userPrincipalName.
The identity correlation rule for an AD target application is as follows:
(__UID__ Equals ObjectGUID) OR (sAMAccountName Equals User Login)
The identity correlation rule for an AD LDS target application is as follows:
(__UID__ Equals ObjectGUID) OR (userPrincipalName Equals User Login)
-
__UID__ is an attribute on the target system that uniquely identifies the user account.
-
ObjectGUID is the unique identifier of the resource assigned to the OIG User.
-
For an AD target application, sAMAccountName is a field on Microsoft Active Directory that represents the login name of the user account.
-
For an AD LDS target application, userPrincipalName is a field on AD LDS that represents the domain-specific name of the user.
-
User Login is the field on the OIG User form.
Both the rule components are joined using the OR logical operator.
Figure 3-6 shows the simple correlation rule for an AD authoritative application.
Figure 3-6 Simple Correlation Rule for an Authoritative Application

Description of "Figure 3-6 Simple Correlation Rule for an Authoritative Application"
Predefined Situations and Responses
The Active Directory User Management connector provides a default set of situations and responses when you create an Authoritative application. These situations and responses specify the action that Oracle Identity Governance must take based on the result of a reconciliation event.
Table 3-9 lists the default situations and responses for both AD and AD LDS authoritative application. If required, you can edit these default situations and responses or add new ones. For more information about adding or editing situations and responses, see Updating Situations and Responses in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-9 Predefined Situations and Responses for an Authoritative Application
| Situation | Response |
|---|---|
|
No Matches Found |
Create User |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Figure 3-7 shows the situations and responses for an authoritative application that the connector provides by default for both AD and AD LDS target systems.
Figure 3-7 Predefined Situations and Responses for an Authoritative Application
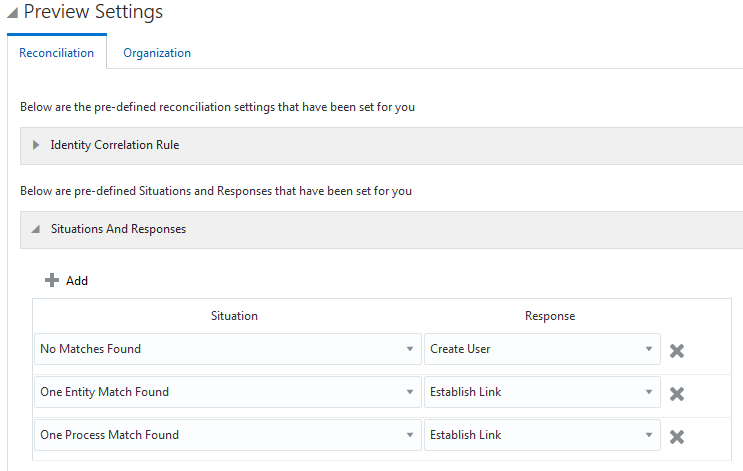
Description of "Figure 3-7 Predefined Situations and Responses for an Authoritative Application"
Reconciliation Jobs for the Connector
These are the reconciliation jobs that the connector creates after you create a target or an authoritative application
Reconciliation Jobs for a Target Application
These are the reconciliation jobs that are automatically created in Oracle Identity Governance after you create a target application.
User Reconciliation Job
Use the Active Directory User Target Reconciliation job to reconcile user data from a target application.
Note:
In release 12.2.1.3.0 of the connector, a new job named Active Directory User Target Concurrent Recon has been introduced, which is similar to the Active Directory User Target Reconciliation job. The Active Directory User Target Concurrent Recon job is recommended for performing bulk reconciliation, reconciles user data from a target application in the multithreaded mode. You can search for and run this scheduled job from Oracle Identity System Administration. The parameters of this job is the same as that of the Active Directory User Target Reconciliation job.Table 3-10 Parameters of the Active Directory User Target Reconciliation and Active Directory User Target Concurrent Recon Jobs
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Number of Batches |
Enter the number of batches in which the connector must reconcile user records. Default value: |
|
Search Scope |
Enter Enter Note: If you want to enter onelevel, then ensure that you do not include a space between the words "one" and "level." Default value: |
|
Scheduled Task Name |
This parameter holds the name of the scheduled job. Note: For the scheduled job included with this connector, you must not change the value of this parameter. However, if you create a new job or create a copy of the job, then enter the unique name for that scheduled job as the value of this parameter. Default value: |
|
Sort Direction |
Use this parameter to specify whether the connector must sort the records that it fetches in ascending or descending order. The value of this attribute can be either Default value: |
|
Incremental Recon Attribute |
Enter the name of the target system attribute that holds last update-related number, non-decreasing value. For example, numeric or strings. The value in this attribute is used during incremental reconciliation to determine the newest or most youngest record reconciled from the target system. Default value: Note: Do not change the value of this attribute. |
|
Sort By |
Enter the name of the target system field by which the connector must sort records in a batch. Default value: Note: If you are using AD LDS as the target system, then change the default value of this parameter to some other attribute (for example, |
|
Latest Token |
This parameter holds the value of the uSNChanged attribute of a domain controller that the connector uses for reconciliation. Note: The reconciliation engine automatically enters a value for this attribute. It is recommended that you do not change the value of this parameter. If you manually specify a value for this attribute, then the connector only user accounts whose uSNChanged value is greater than the Latest Token attribute value. |
|
Filter |
Enter the expression for filtering records that the scheduled job must reconcile. Sample value: For information about the filters expressions that you can create and use, see ICF Filter Syntax in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance. |
|
Batch Start |
Enter the number of the target system record from which a batched reconciliation run must begin. Default value: This parameter is used in conjunction with the Batch Size, Number of Batches, Sort By, and Sort Direction parameters. All these parameters are discussed in Performing Batched Reconciliation. |
|
Batch Size |
Enter the number of records that the connector must include in each batch that it fetches from the target system. Default value: This attribute is used in conjunction with the Batch Start, Number of Batches, Sort By, and Sort Direction attributes. All these attributes are discussed in Performing Batched Reconciliation. |
|
Object Type |
This parameter holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
Search Base |
Enter the container in which the connector must search for user records during reconciliation. Sample Value: Note: If you do not specify a value for this attribute, then the connector uses value specified as the value of the Container parameter of the Basic Configuration section as the value of this parameter. |
Incremental Reconciliation Job
Use the Active Directory User Group Membership Recon job to reconcile user accounts with group changes. The first time you run this job, the connector fetches only the user account that was last updated in the target system and automatically populates the Sync Token parameter value with the latest timestamp. In the subsequent runs, the connector fetches only information about user accounts that have group changes.
Table 3-11 Parameters of the Active Directory User Group Membership Recon Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Scheduled Task Name |
This parameter holds the name of the scheduled job. Note: For the scheduled job included with this connector, you must not change the value of this parameter. However, if you create a new job or create a copy of the job, then enter the unique name for that scheduled job as the value of this parameter. Default value: |
|
Object Type |
This parameter holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
Users Page Size |
Enter the number of records that the connector must fetch in each call to the target system during a reconciliation run. Default value: |
|
Timeout |
Enter an integer value that specifies the number of seconds within which the connector must fetch the number of records specified in the Users Page Size parameter, failing which an exception is thrown. Default value: |
|
Sync Token |
Ensure that this parameter is left blank when you run group membership reconciliation for the first time. The connector fetches only the last-updated user record from the target system and automatically enters a value for this attribute in an XML serialized format. From the next reconciliation run onward, only data about records that are updated since the last reconciliation run ended are fetched into Oracle Identity Manager. |
|
User Group MemberShip Recon |
Enter yes to specify that the connector must fetch details of a user’s group membership. Otherwise enter no, in which case the connector fetches only user data. Default value: |
Delete User Reconciliation Job
The Active Directory User Target Delete Recon job is used to reconcile data about deleted users from a target application. During a reconciliation run, for each deleted user account on the target system, the Active Directory resource is revoked for the corresponding OIM User.
Table 3-12 Parameters of the Active Directory User Target Delete Recon Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Sync Token |
This parameter must be left blank when you run delete reconciliation for the first time. This ensures that data about all records that are deleted from the target system are fetched into Oracle Identity Governance. After the first delete reconciliation run, the connector automatically enters a value for this attribute in an XML serialized format. From the next reconciliation run onward, only data about records that are deleted since the last reconciliation run ended are fetched into Oracle Identity Governance. This attribute stores values in the following format:
A value of A value of |
|
Scheduled Task Name |
This parameter holds the name of the scheduled job. Note: For the scheduled job included with this connector, you must not change the value of this parameter. However, if you create a new job or create a copy of the job, then enter the unique name for that scheduled job as the value of this parameter. Default value: |
|
Object Type |
This parameter holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
Delete Recon |
This parameter specifies whether the connector must perform delete reconciliation. Default value: Note: Do not change the value of this attribute. |
Reconciliation Jobs for Entitlements
The following jobs are available for reconciling entitlements:
-
Active Directory Organization Lookup Recon
This reconciliation job is used to synchronize organization lookup fields in Oracle Identity Governance with organization-related data in the target system.
-
Active Directory Group Lookup Recon
This reconciliation job is used to synchronize group lookup fields in Oracle Identity Governance with group-related data in the target system.
The parameters for both the reconciliation jobs are the same.
Table 3-13 Parameters of the Reconciliation Jobs for Entitlements
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Decode Attribute |
Enter the name of the connector or target system attribute that is used to populate the Decode column of the lookup definition (specified as the value of the Lookup Name attribute). Default value: |
|
Filter |
Enter a filter to filter out records to be stored in the lookup definition. For more information about the Filter attribute, see Performing Limited Reconciliation. |
|
Lookup Name |
This parameter holds the name of the lookup definition that maps each lookup definition with the data source from which values must be fetched. Depending on the reconciliation job you are using, the default values are as follows:
|
|
Object Type |
Enter the type of object whose values must be synchronized. Depending on the scheduled job you are using, the default values are as follows:
Note: Do not change the value of this attribute. |
|
Code Key Attribute |
Enter the name of the connector or target system attribute that is used to populate the Code Key column of the lookup definition (specified as the value of the Lookup Name attribute). Default value: Note: Do not change the value of this attribute. |
Reconciliation Jobs for an Authoritative Application
These are the reconciliation jobs that are automatically created in Oracle Identity Governance after you create an authoritative application.
User Reconciliation Job
The Active Directory User Trusted Recon job is used to reconcile user data from a target application.
Table 3-14 Parameters of the Active Directory User Trusted Recon Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Number of Batches |
Enter the number of batches in which the connector must reconcile user records. Default value: |
|
Search Scope |
Enter Enter Note: If you want to enter onelevel, then ensure that you do not include a space between the words "one" and "level." Default value: |
|
Manager Id |
Enter the distinguished name of a user who is a manager. The connector fetches all user records that have their manager properties set to this distinguished name. If you are using Microsoft Active Directory as the target system, then the default value of this parameter is If you are using Microsoft AD LDS as the target system, then set the value of this parameter to Default value: |
|
Scheduled Task Name |
This parameter holds the name of the scheduled job. Note: For the scheduled job included with this connector, you must not change the value of this parameter. However, if you create a new job or create a copy of the job, then enter the unique name for that scheduled job as the value of this parameter. Default value: |
|
Sort Direction |
Use this parameter to specify whether the connector must sort the records that it fetches in ascending or descending order. The value of this attribute can be either Default value: |
|
Incremental Recon Attribute |
Enter the name of the target system attribute that holds last update-related number, non-decreasing value. For example, numeric or strings. The value in this attribute is used during incremental reconciliation to determine the newest or most youngest record reconciled from the target system. Default value: |
|
Maintain Hierarchy |
Enter Default value: Note: If you set this parameter to |
|
Sort By |
Enter the name of the target system field by which the connector must sort records in a batch. Default value: Note: If you are using AD LDS as the target system, then change the default value of this parameter to some other attribute (for example, |
|
Latest Token |
This parameter holds the value of the uSNChanged attribute of a domain controller that the connector uses for reconciliation. Note: The reconciliation engine automatically enters a value for this attribute. It is recommended that you do not change the value of this parameter. If you manually specify a value for this attribute, then the connector only user accounts whose uSNChanged value is greater than the Latest Token attribute value. |
|
Filter |
Enter the expression for filtering records that the scheduled job must reconcile. Sample value: For information about the filters expressions that you can create and use, see ICF Filter Syntax in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance. |
|
Batch Start |
Enter the number of the target system record from which a batched reconciliation run must begin. Default value: This parameter is used in conjunction with the Batch Size, Number of Batches, Sort By, and Sort Direction parameters. All these parameters are discussed in Performing Batched Reconciliation. |
|
Batch Size |
Enter the number of records that the connector must include in each batch that it fetches from the target system. Default value: This attribute is used in conjunction with the Batch Start, Number of Batches, Sort By, and Sort Direction attributes. All these attributes are discussed in Performing Batched Reconciliation. |
|
Object Type |
This parameter holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
Search Base |
Enter the container in which the connector must search for user records during reconciliation. Sample Value: Note: If you do not specify a value for this attribute, then the connector uses value specified as the value of the Container parameter of the Basic Configuration section as the value of this parameter. |
Delete User Reconciliation Job
The Active Directory User Trusted Delete Recon job is used to reconcile data about deleted users from an Authoritative application. During a reconciliation run, for each deleted target system user account, the corresponding OIM User is deleted.
Table 3-15 Parameters of the Active Directory User Trusted Delete Recon Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Sync Token |
This parameter must be left blank when you run delete reconciliation for the first time. This ensures that data about all records that are deleted from the target system are fetched into Oracle Identity Governance. After the first delete reconciliation run, the connector automatically enters a value for this attribute in an XML serialized format. From the next reconciliation run onward, only data about records that are deleted since the last reconciliation run ended are fetched into Oracle Identity Governance. This attribute stores values in the following format:
A value of A value of |
|
Scheduled Task Name |
This parameter holds the name of the scheduled job. Note: For the scheduled job included with this connector, you must not change the value of this attribute. However, if you create a new job or create a copy of the job, then enter the unique name for that scheduled job as the value of this attribute. Default value: |
|
Object Type |
This parameter holds the type of object you want to reconcile. Default value: Note: If you configure the connector to provision users to a custom class (for example, InetOrgPerson) then enter the value of the object class here. |
|
Delete Recon |
This parameter specifies whether the connector must perform delete reconciliation. Default value: Note: Do not change the value of this attribute. |