2 Creating an Application By Using the Microsoft Active Directory User Management Connector
Learn about onboarding applications using the connector and the prerequisites for doing so.
Process Flow for Creating an Application By Using the Connector
From Oracle Identity Governance release 12.2.1.3.0 onward, connector deployment is handled using the application onboarding capability of Identity Self Service.
Figure 2-1 is a flowchart depicting high-level steps for creating an application in Oracle Identity Governance by using the connector installation package.
Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector
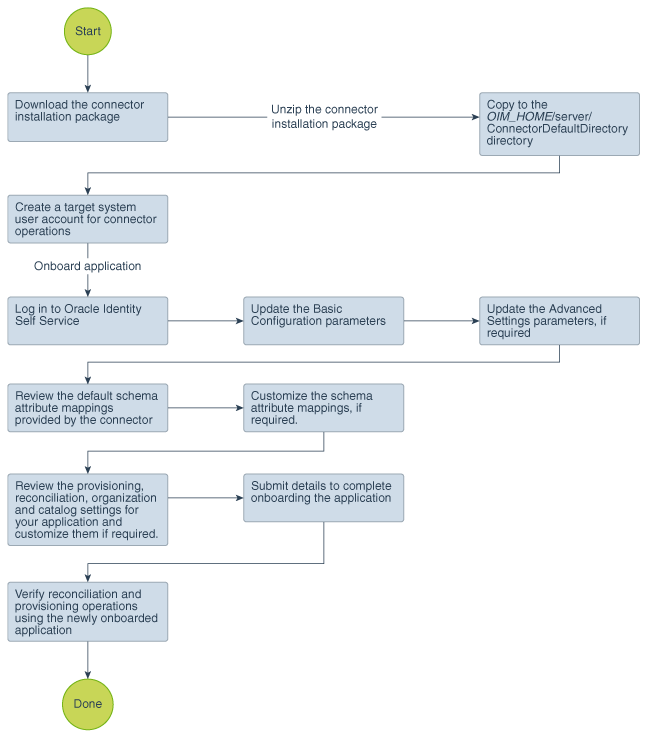
Description of "Figure 2-1 Overall Flow of the Process for Creating an Application By Using the Connector"
Prerequisites for Creating an Application By Using the Connector
Learn about the tasks that you must complete before you create the application.
Downloading the Connector Installation Package
You can obtain the installation package for your connector on the Oracle Technology Network (OTN) website.
Creating a Target System User Account for Connector Operations
Oracle Identity Governance requires a target system user account to access the target system during reconciliation and provisioning operations. You provide the credentials of this user account in the Basic Configuration section while creating an application.
Depending on the target system that you are using, perform the procedure described in one of the following sections:
Creating a User Account for Connector Operations in Microsoft Active Directory
You can use a Microsoft Windows 2008 Server (Domain Controller) administrator account for connector operations. Alternatively, you can create a user account and assign the minimum required rights to the user account.
To create the Microsoft Active Directory user account for connector operations:
See Also:
Microsoft Active Directory documentation for detailed information about performing this procedure
Creating a User Account for Connector Operations in Microsoft AD LDS
You must create and use a user account that belongs to the Administrators group for performing connector operations.
To create the Microsoft AD LDS user account for connector operations:
See Also:
Microsoft AD LDS documentation for detailed information about these steps
Assigning Permissions to Perform Delete User Reconciliation Runs
In order to enable the user account that you created for performing connector operations to retrieve information about deleted user accounts during delete reconciliation runs, you must assign permissions to the deleted objects container (CN=DeletedObjects) in the target system.
Note:
In a forest environment, if you are performing reconciliation by using the Global Catalog Server, then perform the procedure described in this section on all child domains.
Delegating Control for Organizational Units and Custom Object Classes
By default, user accounts that belong to the Account Operators group can manage only user and group objects. To manage organizational units or custom object classes, you must assign the necessary permissions to a user account. In other words, you must delegate complete control for an organizational unit or custom object class to a user or group object. In addition, you need these permissions to successfully perform provisioning of custom object classes.
This is achieved by using the Delegation of Control Wizard. An example for managing organizational units is creating organizational units.
To delegate control for an organizational unit or custom object class to a user account:
Note:
In a parent-child deployment environment or forest topology, perform this procedure on all the child domains.
Installing the Microsoft Active Directory User Management Connector in the Connector Server
Installation in the Connector Server consists of copying and extracting the connector bundle to the Connector Server and configuring the IT resource.
To copy and extract the connector bundle to the Connector Server:
Note:
-
For information about configure the IT resource for the Connector Server, see Configuring the IT Resource for the Connector Server.
-
For information about configuring the .NET Connector Server, see Configuring the .NET Connector Server.
Creating an Application By Using the Connector
You can onboard an application into Oracle Identity Governance from the connector package by creating a Target application. To do so, you must log in to Identity Self Service and then choose the Applications box on the Manage tab.
Note:
For detailed information on each of the steps in this procedure, see Creating Applications of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
- Create an application in Identity Self Service. The high-level steps are as follows:
- Verify reconciliation and provisioning operations on the newly created application.
Note:
You can verify and test connectivity using the Test Connection option only after the completion of following actions:- AOB installation
- Extracted bundle/ActiveDirectory.Connector-12.3.0.0.zip is copied to the Connector Server home directory
- IT Resource for the Connector Server is configured
- IT Resource for the Target System is configured
See Also:
-
Configuring the Microsoft Active Directory User Management Connector for details on basic configuration and advanced settings parameters, default user account attribute mappings, default correlation rules, and reconciliation jobs that are predefined for this connector
-
Configuring Oracle Identity Governance for details on creating a new form and associating it with your application, if you chose not to create the default form