1 About the Microsoft Active Directory User Management Connector
Note:
In this guide, the connector that is deployed using the Applications option on the Manage tab of Identity Self Service is referred to as an AOB application. The connector that is deployed using the Manage Connector option in Oracle Identity System Administration is referred to as a CI-based connector (Connector Installer-based connector).Application onboarding is the process of registering or associating an application with Oracle Identity Governance and making that application available for provisioning and reconciliation of user information.
The following sections provide a high-level overview of the connector:
Note:
At some places in this guide, Microsoft Active Directory and Microsoft AD LDS are referred to as target systems.Certified Components
These are the software components and their versions required for installing and using the Active Directory connector. The target system can be Microsoft Active Directory or Microsoft AD LDS.
Table 1-1 Certified Components
| Component | AOB Application Requirement for Microsoft Active Directory | AOB Application Requirement for Microsoft AD LDS | CI-Based Connector Requirement for Microsoft Active Directory | CI-Based Connector Requirement for Microsoft AD LDS |
|---|---|---|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases:
|
Oracle Identity Governance 12c(12.2.1.3.0) Oracle Identity Governance 12c (12.2.1.4.0) |
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
Target systems and target system host platforms |
The target system can be any one of the following:
|
The target system can be any one of the following:
|
The target system can be any one of the following:
|
The target system can be any one of the following:
|
|
Connector Server |
Depending on the target system version that you are using, you can use one of the following Connector Server versions:
|
11.1.2.1.0 or 12.2.1.3.0 |
Depending on the target system version that you are using, you can use one of the following Connector Server versions:
|
11.1.2.1.0 or 12.2.1.3.0 |
|
Other software (Software used for establishing or securing communication between Oracle Identity Manager and target system.) |
Certificate Services IIS Web Server |
Certificate Services IIS Web Server Note: You must configure SSL for the connector to perform all connector operations as expected. |
Certificate Services IIS Web Server |
Certificate Services IIS Web Server Note: You must configure SSL for the connector to perform all connector operations as expected. |
|
Microsoft .NET framework |
3.5, 4, 4.5, or higher version Note: If you are using Microsoft .NET Framework 3.5, then apply the following patch to prevent a memory leak issue: http://support.microsoft.com/kb/981575 |
3.5, 4, 4.5, or higher version Note: If you are using Microsoft .NET Framework 3.5, then apply the following patch to prevent a memory leak issue: http://support.microsoft.com/kb/981575 |
3.5, 4, 4.5, or higher version Note: If you are using Microsoft .NET Framework 3.5, then apply the following patch to prevent a memory leak issue: http://support.microsoft.com/kb/981575 |
3.5, 4, 4.5, or higher version Note: If you are using Microsoft .NET Framework 3.5, then apply the following patch to prevent a memory leak issue: http://support.microsoft.com/kb/981575 |
Usage Recommendation
These are the recommendations for the Microsoft Active Directory User Management connector versions that you can deploy and use depending on the Oracle Identity Governance or Oracle Identity Manager version that you are using.
-
If you are using Oracle Identity Governance 12c (12.2.1.3.0), then use the latest 12.2.1.x version of this connector. Deploy the connector using the Applications option on the Manage tab of Identity Self Service.
-
If you are using Oracle Identity Manager release 11g Release 2 PS3 (11.1.2.3.0), as listed in the “CI-Based Connector Requirement for Microsoft Active Directory” or “CI-Based Connector Requirement for Microsoft AD LDS or ADAM” columns of Table 1-1, then use the 11.1.x version of the Microsoft Active Directory User Management connector. If you want to use the 12.2.1.x version of this connector with Oracle Identity Manager 11g Release 2 PS3 (11.1.2.3.0), then you can install and use the it only in the CI-based mode. If you want to use the AOB application, then you must upgrade to Oracle Identity Governance release 12.2.1.3.0.
Note:
If you are using the latest 12.2.1.x version of the Microsoft Active Directory User Management connector in the CI-based mode, then see Oracle Identity Manager Connector Guide for Microsoft Active Directory User Management, Release 11.1.1 for complete details on connector deployment, usage, and customization. -
If you are using an Oracle Identity Manager release that is later than release 9.1.0.1 and earlier than Oracle Identity Manager 11g Release 1 (11.1.1.5.6), then you must use the 9.1.1 version of this connector.
Certified Languages
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English
-
Finnish
-
French
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
Supported Connector Operations
These are the list of operations that the connector supports for your target system.
Table 1-2 Supported Connector Operations
| Operation | Supported? |
|---|---|
|
User Management |
|
|
Create user |
Yes |
|
Update user |
Yes |
|
Delete user |
Yes |
|
Enable user |
Yes |
|
Disable user |
Yes |
|
Group Management |
|
|
Create group |
Yes |
|
Delete group |
Yes |
|
Organizational Unit Management |
|
|
Create organizational unit |
Yes |
|
Delete organizational unit |
Yes |
|
Entitlement Grant Management |
|
|
Add group |
Yes |
|
Remove group |
Yes |
Note:
All the connector artifacts required for managing groups and organizational units (for example groups and organizational attribute mappings, reconciliation rules, jobs, and so on) are not visible in the Applications UI in Identity Self Service. However, all the required information is available in the predefined application templates of the connector installation package. For more information about the artifacts related to groups and organizational units, see Connector Objects Used for Groups Management and Connector Objects Used for Organizational Units Management.Connector Architecture
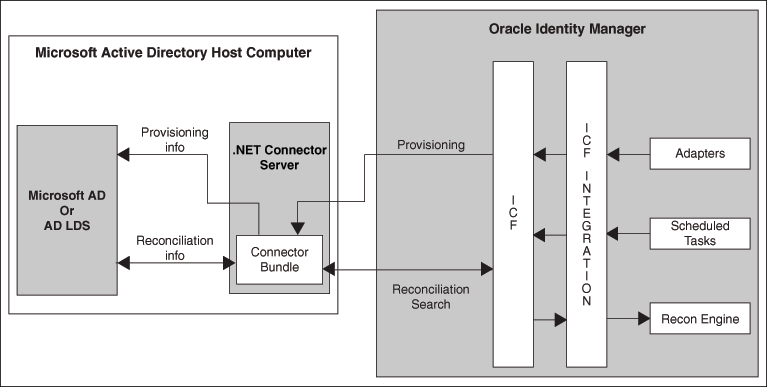
The Microsoft Active Directory User Management connector enables management of accounts through Oracle Identity Governance, and is implemented using the Identity Connector Framework (ICF).
Figure 1-1 shows the architecture of the connector.
The Microsoft Active Directory User Management connector is built on top of System.DirectoryServices, a collection of classes managed by .NET that makes using Microsoft Active Directory easy and convenient. In the .NET Framework, classes for managing directory objects are contained within the System.DirectoryServices namespace. The classes in System.DirectoryServices wrap Active Directory Services Interfaces (ADSI) functionality.
ADSI is a built-in component of Microsoft Windows and shipped with different providers to access directories such as WinNT for local account management, NDS for accessing Novell eDirectory (formally known as Novell Directory Services), and LDAP for accessing any directory that supports Lightweight Directory Access Protocol (LDAP) v3. This connector uses the LDAP provider to access Microsoft Active Directory.
The earlier version of this connector represented a high-level connector with many configuration settings and lookup definitions that were used to customize the provisioning process. In addition, using SSL certificate for securing communication between Oracle Identity Governance and the target system was mandatory. In contrast, the current version of the connector provides low-level operations by using the Connector Framework and the consumer application is responsible for setting up the provisioning process. By using the internal mechanism of ADSI and the .NET Framework, the default communication between the .NET Connector Server and Microsoft Active Directory is "secure." However, if you are using Microsoft AD LDS as the target system, then you must configure SSL between Oracle Identity Manger and the target system.
Note:
For performing password reset provisioning operations, the communication with the target system must be secure. If you are using Microsoft AD as the target system, there is no need to enable SSL between the .NET Connector Server and the target system. This is because the default communication between the .NET Connector Server and the target system is "secure."
However, in the case of Microsoft AD LDS, the default communication between the .NET Connector Server and Microsoft AD LDS is not "secure." Therefore, it is required to configure SSL between the .NET Connector Server and Microsoft AD LDS for the password reset functionality to work as expected.
As the current version of this connector provides low-level provisioning functionality, an integration code called Integrated Common Framework (ICF) Common is used.
Instead of communicating directly with the native API, ICF Common communicates with the connector framework through its API, and then calls SPI operations on a specific version of this connector. Between the Java ICF and the connector, the .NET Connector Framework resides (in the context of which the connector is running) and bridges the Java ICF and .NET connector. The connector is deployed in the .NET connector framework.
Oracle Identity Governance communicates with a .NET Connector Server over the network. The .NET Connector Server serves as a proxy to provide any authenticated application access to the current version of the connector deployed within the .NET Connector Server. Note that the Connector Server need not be on the domain controller on which the target system is running. Connector Server can be configured on any machine in the Microsoft Active Directory domain.
The Microsoft Active Directory User Management connector is a .NET connector that supports provisioning to and reconciliation from Microsoft Windows servers running, Microsoft Active Directory Domain Services (AD DS) and Microsoft Active Directory Lightweight Directory Services (AD LDS).
The Microsoft Active Directory User Management connector is implemented using the ICF. The ICF provides a container that separates the connector bundle from the application (for example, Oracle Identity Governance or Oracle Waveset). The ICF is a component that provides basic reconciliation and provisioning operations that are common to all Oracle Identity Governance connectors. In addition, ICF provides common features that developers would otherwise need to implement on their own, such as connection pooling, buffering, time outs, and filtering. The ICF is shipped along with Oracle Identity Governance. Therefore, you need not configure or modify the ICF.
See Also:
Understanding the Identity Connector Framework in Developing and Customizing Applications for Oracle Identity Governance for more information about the ICF
The connector can be configured to run in one of the following modes:
-
Identity reconciliation
Identity reconciliation is also known as authoritative or trusted source reconciliation. In this form of reconciliation, OIM Users are created or updated corresponding to the creation of and updates to users on the target system. The identity reconciliation mode also supports reconciliation of objects like groups and organizations (OUs) created on the target system.
In the identity reconciliation mode, depending on the data that you want to reconcile, you use different scheduled tasks. For example, you use the Active Directory User Trusted Recon scheduled job to reconcile user data from the target system. See Reconciliation Jobs for an Authoritative Application for more information about scheduled tasks used in this mode.
-
Account Management
Account management is also known as target resource management. This mode of the connector enables the following operations:
-
Provisioning
Provisioning involves creating, updating, or deleting users on the target system through Oracle Identity Governance. When you allocate (or provision) a Microsoft Active Directory resource to an OIM User, the operation results in the creation of an account on Microsoft Active Directory for that user. In the Oracle Identity Governance context, the term "provisioning" is also used to mean updates (for example enabling or disabling) made to the target system account through Oracle Identity Governance.
Users and organizations are organized in hierarchical format on the target system. Before you can provision users to (that is, create users in) the required organizational units (OUs) on the target system, you must fetch into Oracle Identity Governance the list of OUs used on the target system. This is achieved by using a lookup synchronization scheduled job.
Similarly, before you can provision users to the required groups on the target system, you must fetch into Oracle Identity Governance the list of all groups used on the target system. This is also achieved by using a lookup synchronization scheduled job.
The connector enables group assignment provisioning operations in which you set or change the target system group membership profiles of users. The connector also supports provisioning (updating) of the Windows Terminal Services Profile attributes. Accessing these attributes involves the use of components that are native to the Microsoft Windows platform.
-
Target resource reconciliation
To perform target resource reconciliation, the Active Directory User Target Recon scheduled job is used. The connector applies filters to locate users to be reconciled from the target system and then fetches the attribute values of these users.
Depending on the data that you want to reconcile, you use different scheduled jobs. For example, you use the Active Directory User Target Recon scheduled job to reconcile user data in the target resource mode. For more information about scheduled jobs used in this mode, see Reconciliation Jobs for a Target Application.
-
Password Synchronization
This connector cannot propagate password changes from Microsoft Active Directory to Oracle Identity Governance.
To implement this feature, you must install the Microsoft Active Directory password synchronization connector. See Deploying the Connector in Oracle Identity Manager Connector Guide for Microsoft Active Directory Password Synchronization for more information about scenarios in which both the password synchronization connector and this connector are deployed.
Supported Connector Features Matrix
Provides the list of features supported by the AOB application and CI-based connector.
Table 1-3 Supported Connector Features Matrix
| Feature | AOB Connector | CI-Based Connector |
|---|---|---|
|
Full reconciliation |
Yes |
Yes |
|
Incremental reconciliation |
Yes |
Yes |
|
Limited reconciliation |
Yes |
Yes |
|
Batched reconciliation |
Yes |
Yes |
|
Connection pooling |
Yes |
Yes |
|
Use connector server |
Yes |
Yes |
|
Deleted groups reconciliation |
Yes |
Yes |
|
Transformation and validation of account data |
Yes |
Yes |
|
Perform reconciliation and provisioning operations across domains |
Yes |
Yes |
|
Perform connector operations on user-defined object classes |
No |
Yes |
|
Add dynamic auxiliary object classes |
No |
Yes |
|
Add and include the Group Name (pre-Windows 2000) attribute in connector operations |
Yes |
Yes |
|
Provision groups of the Security Group - Universal type |
Yes |
Yes |
|
Add custom object categories in connector operations |
Yes |
Yes |
|
Compatibility with high-availability target system environments |
Yes |
Yes |
|
Test connection |
Yes |
No |
Connector Features
The features of the connector include support for connector server, transformation and validation of account data, full, incremental, limited, and batched reconciliation, high-availability configuration and so on.
The following are features of this connector:
Full and Incremental Reconciliation
After you create the application, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Governance.
After the first full reconciliation run, incremental reconciliation is automatically enabled. In incremental reconciliation, user accounts that have been added or modified since the last reconciliation run are fetched into Oracle Identity Governance.
You can perform a full reconciliation run at any time.
See Performing Full Reconciliation and Incremental Reconciliation for more information.
Limited Reconciliation
You can set a reconciliation filter as the value of the Filter attribute of the user reconciliation job. This filter specifies the subset of added and modified target system records that must be reconciled.
See Performing Limited Reconciliation for more information.
Batched Reconciliation
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
See Performing Batched Reconciliation for more information.
Reconciliation of Deleted Groups
You can configure the connector for reconciling information about groups deleted in the target system.
In target resource mode, if a group is deleted on the target system, then the corresponding group is revoked from Oracle Identity Governance.
See Active Directory Group Delete Recon for more information about the scheduled job used for reconciling deleted groups.
Transformation and Validation of Account Data
You can configure transformation and validation of account data that is brought into or sent from Oracle Identity Governance during reconciliation and provisioning operations by writing Groovy scripts while creating your application.
For more information, see Validation and Transformation of Provisioning and Reconciliation Attributes in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Support for Connector Server
Connector Server is a component provided by ICF. By using one or more connector servers, the connector architecture permits your application to communicate with externally deployed bundles. In other words, a connector server enables remote execution of an Oracle Identity Governance connector.
The Active Directory User Management connector is written using Microsoft .NET. A .NET environment is required for the execution of this connector code. Therefore, it is mandatory to deploy this connector on the .NET Connector Server shipped along with the connector package. The Active Directory User Management connector operates in the context of the .NET Connector Framework, which in turn requires an application to execute. Therefore, by default, Oracle provides the .NET Connector Server to run the Active Directory User Management connector.
For information about installing, configuring, and running the Connector Server, and then installing the connector in a Connector Server, see Using an Identity Connector Server in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance.
Connection Pooling
A connection pool is a cache of objects that represent physical connections to the target. Oracle Identity Governance connectors can use these connections to communicate with target systems.
At run time, the application requests a connection from the pool. If a connection is available, then the connector uses it and then returns it to the pool. A connection returned to the pool can again be requested for and used by the connector for another operation. By enabling the reuse of connections, the connection pool helps reduce connection creation overheads like network latency, memory allocation, and authentication.
One connection pool is created for each set basic configuration parameters that you provide while creating an application. For example, if you have three applications for three installations of the target system, then three connection pools will be created, one for each target system installation.
For more information about the parameters that you can configure for connection pooling, see Advanced Settings Parameters.
Support for Connector Operations Across Domains
The connector supports reconciliation and provisioning operations across domains.
This means that, for example, you can assign a user in one domain to a group in another domain. You can also reconcile a user record even if the user and the user's manager belong to different domains.
See Enabling Reconciliation and Provisioning Operations Across Multiple Domains for more information.
Support for Adding the Group Name (pre-Windows 2000) Attribute
You add the Group Name (pre-Windows 2000) attribute to Oracle Identity Governance and then include it for reconciliation and provisioning operations.
During group provisioning, by default, the value that you specify for the Group Name field on the OIM process form, is entered as the value of the Group Name and Group Name (pre-Windows 2000) attributes of the target system. If you want to specify different values for the Group Name and Group Name (pre-Windows 2000) attributes in the target system, then you must create the Group Name (pre-Windows 2000) field on the OIM process form.
See Adding the Group Name (pre-Windows 2000) Attribute for more information.
Support for Provisioning Groups of the Security Group - Universal Group Type
The connector lets you create a group of the type Security Group - Universal.
For more information, see Configuring the Connector for Provisioning Groups of the Security Group - Universal Group Type.
Support for Scripting Languages
The connector supports any scripting language that has a script executor in the ICF. Currently, the connector supports two script executor implementations: a Windows shell script executor (batch scripts) and a Boo script executor.
Although Visual Basic scripts are not directly supported, a Visual Basic script can be called using a shell script.
For more information, see Action Scripts.
Support for High-Availability Configuration of the Target System
You can configure the connector for compatibility with high-availability target system environments.
It can read information about backup target system hosts from the Backup Host Names parameter of the Basic Configuration section and apply this information when it is unable to connect to the primary host.
For more information about the Backup Host Names parameter, see Basic Configuration Parameters.