6 Extending the Functionality of the Microsoft Active Directory User Management Connector
You can extend the functionality of the connector to address your specific business requirements.
By default the connector is configured to perform a certain set of tasks. For addressing your specific business requirements, you can extend the functionality of the connector by performing the procedures described in the following sections:
-
Adding New Multivalued Fields for Target Resource Reconciliation
-
Adding Terminal Services Fields for Reconciliation and Provisioning
-
Enabling Reconciliation and Provisioning Operations Across Multiple Domains
-
About Using the Connector for Multiple Trusted Source Reconciliation
-
Creating a Home Directory After User Create Provisioning Operation
-
Configuring the Connector for Provisioning Groups of the Security Group - Universal Group Type
Adding Custom Fields for Target Resource Reconciliation
You can add additional fields for user, group, or organizational unit reconciliation.
-
Adding Custom Fields for Target Resource Reconciliation of Users
-
Adding Custom Fields for Target Resource Reconciliation of Groups and Organizational Units
Note:
Binary attributes are not supported. Connector supports
string, long, char,
double, float, int, and
bool attribute types of the Microsoft Active Directory
target system.
Adding Custom Fields for Target Resource Reconciliation of Users
You can add additional fields for user reconciliation.
Note:
This section describes an optional procedure. You need not perform this procedure if you do not want to add custom fields for reconciliation.
To add a custom field for target resource reconciliation for users:
- Log in to Identity Self Service as an administrator.
- Click the Manage tab, and then click the Applications box to open the Applications page.
- Search for and open the Active Directory Target application to which you want to add custom fields.
- Select Schema and then click Add Attribute.
- In the newly added row, add the new attribute name, the OIM Profile and target system attribute that it will map to, and so on. For example, enter values for the Display Name , Identity Attribute, Target Attribute , and Data Type fields. Then, select the Recon Field checkbox and any other reconciliation properties as required.
- Click Apply to save the changes.
- Log in to Oracle Identity System Administration as an administrator.
- Create and activate a sandbox.
- Select Form Designer.
- Create a new form with the following values and then click Create:
- In the Resource Type field, enter the Active Directory Target application to which you added custom fields.
- In the Form Name field, enter a form name. If you add attributes incrementally to the application, then you must create new forms every time you add new attributes. Therefore, it is recommended that you include a version number in the form name.
- Ensure that the newly created attribute is present in the list of attributes on the form and save the changes. Then, publish the sandbox.
- Navigate to Application Instances and the search for and open the application instance associated with the application to which you added the new attributes.
- From the Form dropdown, select the new version of the form you just created and then click Apply.
Adding Custom Fields for Target Resource Reconciliation of Groups and Organizational Units
You can add additional fields for group or organizational unit reconciliation.
Note:
This section describes an optional procedure. You need not perform this procedure if you do not want to add custom fields for reconciliation.
To add a custom field for target resource reconciliation:
-
Log in to the Oracle Identity Governance Design Console.
-
Add the custom field to the list of reconciliation fields in the resource object as follows:
-
Expand Resource Management and then double-click Resource Objects.
-
Search for and open one of the following resource objects:
For groups: AD Group
For organizational units: AD Organizational Unit
-
On the Object Reconciliation tab, click Add Field.
-
In the Add Reconciliation Field dialog box, enter the details of the field.
For example, enter
Descriptionin the Field Name field and select String from the Field Type list.Note that if you are adding a boolean field, then select String as the field type.
-
Click Save and close the dialog box.
-
Click Create Reconciliation Profile. This copies changes made to the resource object into MDS.
-
Click Save.
-
-
Create an entry for the field in the lookup definition for reconciliation as follows:
-
Expand Administration and then double-click Lookup Definition.
-
Search for and open one of the following lookup definitions:
For groups: Lookup.ActiveDirectory.GM.ReconAttrMap
For organizational units: Lookup.ActiveDirectory.OM.ReconAttrMap
-
Click Add and enter the Code Key and Decode values for the field. The Code Key value is the name of the field that you provide for the reconciliation field in Step 2.d. The Decode value is the name of the target system field.
For example, enter
Descriptionin the Code Key field and then enterdescriptionin the Decode field. -
Click Save.
-
-
Add the custom field on the process form as follows:
-
Expand Development Tools and then double-click Form Designer.
-
Search for and open one of the following process forms:
For groups: UD_ADGRP
For organizational units: UD_ADOU
-
Click Create New Version, and then click Add.
-
Enter the details of the field.
For example, if you are adding the Description field, enter
UD_ADGRP_DESCRIPTIONin the Name field, and then enter the rest of the details of this field. -
Click Save and then click Make Version Active.
-
-
If you are using Oracle Identity Governance release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form as follows:
-
Log in to Oracle Identity System Administration.
-
Create and active a sandbox. See Creating and Activating a Sandbox for more information.
-
Create a new UI form to view the newly added field along with the rest of the fields. See Creating a New UI Form for more information about creating a UI form.
-
Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 5.c), and then save the application instance.
-
Publish the sandbox. See Publishing a Sandbox for more information.
-
-
Create a reconciliation field mapping for the custom field in the provisioning process as follows:
-
Log in to the Design Console.
-
Expand Process Management and then double-click Process Definition.
-
Search for and open one of the following provisioning process:
For groups: AD Group
For organizational units: AD Organizational Unit
-
On the Reconciliation Field Mappings tab of the provisioning process, click Add Field Map.
-
In the Add Reconciliation Field Mapping dialog box, from the Field Name field, select the value for the field that you want to add.
For example, from the Field Name field, select Description.
-
Double-click the Process Data field, and then select UD_ADGRP_DESCRIPTION.
-
Click Save and close the dialog box.
-
Click Save.
-
Adding New Multivalued Fields for Target Resource Reconciliation
You can add new multivalued fields for user, group, or organizational unit during target resource reconciliation.
-
Adding New Multivalued Fields for Target Resource Reconciliation of Users
-
Adding New Multivalued Fields for Target Resource Reconciliation of Groups and Organizational Units
Note:
Binary attributes are not supported. Connector supports
string, long, char,
double, float, int, and
bool attribute types of the Microsoft Active Directory
target system.
Adding New Multivalued Fields for Target Resource Reconciliation of Users
You can add multivalued fields for user reconciliation between Oracle Identity Governance and the target system.
Note:
This procedure can be applied to add user fields only.
You must ensure that new fields you add for reconciliation contain only string-format data. Binary fields must not be brought into Oracle Identity Governance natively.
To add a new multivalued field for target resource reconciliation:
-
On the Application On-Boarding UI, select the Active Directory Target application.
-
Select Schema and then click Add Attribute.
-
In the newly added row, enter values for the Display Name and Target Attribute fields.
-
To select a value for the Data Type field, click the drop-down and select String.
-
Select the Recon Field checkbox.
-
Click Advanced Settings denoted by three horizontal lines at the end of the row and select the Lookup checkbox.
-
In the List of values field, enter the name of the lookup definition and click OK.
-
Click Apply.
Adding New Multivalued Fields for Target Resource Reconciliation of Groups and Organizational Units
You can add multivalued fields for reconciliation of groups and organizational units between Oracle Identity Governance and the target system.
Note:
This procedure can be applied to add either group or organizational unit fields.
You must ensure that new fields you add for reconciliation contain only string-format data. Binary fields must not be brought into Oracle Identity Governance natively.
To add a new multivalued field for target resource reconciliation:
-
Log in to the Oracle Identity Governance Design Console.
-
Create a form for the multivalued field as follows:
-
Expand Development Tools and double-click Form Designer.
-
Create a form by specifying a table name and description, and then click Save.
-
Click Add and enter the details of the field.
-
Click Save and then click Make Version Active. shows the multivalued field added on a new form.
Figure 6-1 Multivalued Field Added on a New Form
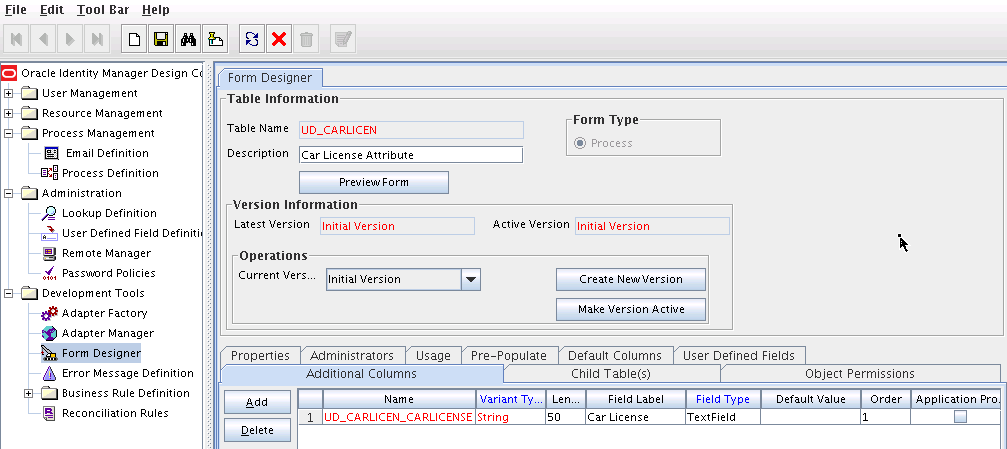
Description of "Figure 6-1 Multivalued Field Added on a New Form" -
-
Add the form created for the multivalued field as a child form of the process form as follows:
-
Search for and open one of the following process forms:
For groups: UD_ADGRP
For organizational units: UD_ADOU
-
Click Create New Version.
-
Click the Child Table(s) tab.
-
Click Assign.
-
In the Assign Child Tables dialog box, select the newly created child form, click the right arrow, and then click OK.
-
Click Save and then click Make Version Active.
-
-
If you are using Oracle Identity Governance release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form as follows:
-
Log in to Oracle Identity System Administration.
-
Create and active a sandbox. See Creating and Activating a Sandbox for more information.
-
Create a new UI form to view the newly added field along with the rest of the fields. See Creating a New UI Form for more information about creating a UI form.
-
Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 4.c), and then save the application instance.
-
Publish the sandbox. See Publishing a Sandbox for more information.
-
-
Add the new multivalued field to the list of reconciliation fields in the resource object as follows:
-
Log in to the Design Console.
-
Expand Resource Management and then double-click Resource Objects.
-
Search for and open one of the following resource objects:
For groups: AD Group
For organizational units: AD Organizational Unit
-
On the Object Reconciliation tab, click Add Field.
-
In the Add Reconciliation Fields dialog box, enter the details of the field.
For example, enter
carlicensesin the Field Name field and select Multi-Valued Attribute from the Field Type list. -
Click Save and then close the dialog box.
-
Right-click the newly created field and select Define Property Fields.
-
In the Add Reconciliation Fields dialog box, enter the details of the newly created field.
For example, enter
carlicensein the Field Name field and select String from the Field Type list. -
Click Save, and then close the dialog box. Figure 6-2 shows the new reconciliation field added in the resource object.
Figure 6-2 New Reconciliation Field Added in the Resource Object
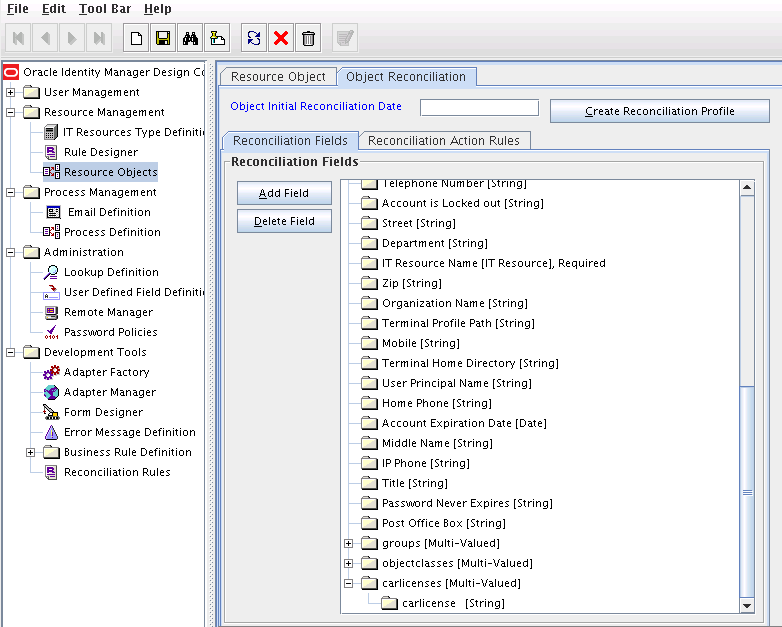
Description of "Figure 6-2 New Reconciliation Field Added in the Resource Object" -
Click Create Reconciliation Profile. This copies changes made to the resource object into the MDS.
-
-
Create an entry for the field in the lookup definition for reconciliation as follows:
-
Expand Administration and then double-click Lookup Definition.
-
Search for and open one of the following lookup definitions:
For groups: Lookup.ActiveDirectory.GM.ReconAttrMap
For organizational units: Lookup.ActiveDirectory.OM.ReconAttrMap
Note:
For the target system fields, you must use the same case (uppercase or lowercase) as given on the target system. This is because the field names are case-sensitive.
-
Cick Add and enter the Code Key and Decode values for the field, and then Click Save. The Code Key and Decode values must be in the following format:
Code Key: MULTIVALUED_FIELD_NAME~CHILD_RESOURCE_OBJECT_FIELD_NAME
Decode: Corresponding target system attribute.
For example, enter
carlicenses~carlicensein the Code Key field and then entercarlicensein the Decode field.
-
-
Create a reconciliation field mapping for the new field as follows:
-
Expand Process Management and double-click Process Definition.
-
Search for and open one of the following process definitions:
For groups: AD Group
For organizational units: AD Organizational Unit
-
On the Reconciliation Field Mappings tab of the AD Group or AD Organizational Unit process definition, click Add Table Map.
-
In the Add Reconciliation Table Mapping dialog box, select the field name and table name from the list, click Save, and then close the dialog box.
-
Right-click the newly created field, and select Define Property Field Map.
-
In the Field Name field, select the value for the field that you want to add.
-
Double-click the Process Data Field field, and then select UD_CARLICEN.
-
Select Key Field for Reconciliation Field Matching and click Save.
-
Adding Custom Fields for Provisioning
You can add additional fields while provisioning users, groups, or organizational units.
Note:
Binary attributes are not supported. Connector supports
string, long, char,
double, float, int, and
bool attribute types of the Microsoft Active Directory
target system.
Adding Custom Fields for Provisioning Users
You can add additional fields while provisioning users.
Note:
This section describes an optional procedure. You need not perform this procedure if you do not want to add custom fields for provisioning.
To add a custom field for provisioning users:
-
On the Application On-Boarding UI, select the Active Directory Target application.
-
Select Schema and then click Add Attribute.
-
In the newly added row, enter values for the Display Name and Target Attribute fields.
-
To select a value for the Data Type field, click the drop-down and select String.
-
Select the Provision Field checkbox.
-
Click Apply.
Adding Custom Fields for Provisioning Groups and Organizational Units
You can map additional attributes for provisioning apart from the default attributes.
To add a custom field for provisioning for groups and organizational units, perform the procedures listed in the following sections:
Adding a New Field on the Process Form
If you have added the field on the process form by performing Step 4 of Adding Custom Fields for Target Resource Reconciliation of Groups and Organizational Units, then you need not add the field again. If you have not added the field, then add it as follows:
Replicating Form Designer Changes to a New UI Form
If you are using Oracle Identity Governance release 11.1.2.x or later, then all changes made to the Form Designer of the Design Console must be done in a new UI form as follows:
- Log in to Oracle Identity System Administration.
- Create and active a sandbox. See Creating and Activating a Sandbox for more information.
- Create a new UI form to view the newly added field along with the rest of the fields. See Creating a New UI Form for more information about creating a UI form.
- Associate the newly created UI form with the application instance of your target system. To do so, open the existing application instance for your resource, from the Form field, select the form (created in Step 3.c), and then save the application instance.
- Publish the sandbox. See Publishing a Sandbox for more information.
Creating an Entry in the Provisioning Lookup Definition
Create an entry for the field in the lookup definition for provisioning as follows:
Enabling Update Provisioning Operations on the Custom Field
After adding the custom field, you must enable update provisioning operations on that field as follows:
-
In the provisioning process, add a new task for updating the field as follows:
-
Expand Process Management and then double-click Process Definition.
-
Search for and open one of the following provisioning process:
For groups: AD Group
For organizational units: AD Organizational Unit
-
Click Add and enter the task name and task description. The following are sample values:
Task Name:
Description UpdatedTask Description:
Process Task for handling update of the description field. -
In the Task Properties section, select the following fields:
Conditional
Allow Cancellation while Pending
Allow Multiple Instances
-
Click Save.
-
-
In the provisioning process, select the adapter name in the Handler Type section as follows:
-
Go to the Integration tab, click Add.
-
In the Handler Selection dialog box, select Adapter.
-
From the Handler Name column, select adpADIDCUPDATEATTRIBUTEVALUE.
-
Click Save and close the dialog box.
-
-
In the Adapter Variables region, click the procInstanceKey variable.
-
In the dialog box that is displayed, create the following mapping:
Variable Name:
procInstanceKeyMap To:
Process DataQualifier:
Process Instance -
Click Save and close the dialog box.
-
If you are enabling update provisioning operations for a Group custom field, then repeat Steps 3 through 5 for all the variables listed in the following table. This table lists values that you must select from the Map To, Qualifier, and Literal Value lists for each variable:
Variable Map To Qualifier Literal Value procInstanceKey
Process Data
Process Instance
NA
Adapter Return Variable
Response Code
NA
NA
itResourceFieldName
Literal
String
UD_ADGRP_SERVER
attrFieldName
Literal
String
CUSTOM_FIELD_NAME
objectType
Literal
String
Group
-
If you are enabling update provisioning operations for an Organizational Unit custom field, then repeat Steps 3 through 5 for all the variables listed in the following table. This table lists values that you must select from the Map To, Qualifier, and Literal Value lists for each variable:
Variable Map To Qualifier Literal Value procInstanceKey
Process Data
Process Instance
NA
Adapter Return Variable
Response Code
NA
NA
itResourceFieldName
Literal
String
UD_ADOU_SERVER
attrFieldName
Literal
String
CUSTOM_FIELD_NAME
objectType
Literal
String
organizationalUnit
-
On the Responses tab, click Add to add at least the SUCCESS response code, with Status
C.This ensures that if the custom task is successfully run, then the status of the task is displayed asCompleted. -
Click the Save icon and close the dialog box, and then save the process definition.
Updating the Request Dataset
When you add an attribute on the process form, you also update the XML file containing the request dataset definitions. To update a request dataset:
Clearing Content Related to Request Datasets from the Server Cache
Run the PurgeCache utility to clear content related to request datasets from the server cache.
See Running the PurgeCache Utility in Oracle Fusion Middleware Administering Oracle Identity Governance for more information about the PurgeCache utility.
Adding New Multivalued Fields for Provisioning
You can add new multivalued fields for user, group, or organizational unit during a provisioning operation.
Note:
Binary attributes are not supported. Connector supports
string, long, char,
double, float, int, and
bool attribute types of the Microsoft Active Directory
target system.
Adding New Multivalued Fields for Provisioning Users
You can add multivalued fields for provisioning users between Oracle Identity Governance and the target system.
Note:
This procedure can be applied to add user fields only.
You must ensure that new fields you add for reconciliation contain only string-format data. Binary fields must not be brought into Oracle Identity Governance natively.
To add a new multivalued field for provisioning:
-
On the Application On-Boarding UI, select the Active Directory Target application.
-
Select Schema and then click Add Attribute.
-
In the newly added row, enter values for the Display Name and Target Attribute fields.
-
To select a value for the Data Type field, click the drop-down and select String.
-
Select the Provision Field checkbox.
-
Click Advanced Settings denoted by three horizontal lines at the end of the row and select the Lookup checkbox.
-
In the List of values field, enter the name of the lookup definition and click OK.
-
Click Apply.
Adding New Multivalued Fields for Provisioning Groups and Organizational Units
You can add new multivalued fields for provisioning.
Note:
Before starting the following procedure, perform Steps1 through 4 as described in Adding New Multivalued Fields for Target Resource Reconciliation of Groups and Organizational Units. If these steps have been performed while adding new multivalued fields for target resource reconciliation, then you need not repeat the steps.
To add new multivalued fields for provisioning:
Creating an Entry in the Provisioning Lookup Definition
Create an entry for the field in the lookup definition for provisioning as follows:
Enabling Update Provisioning Operations on the Multivalued Field
Enable update provisioning operations on the multivalued field as follows:
Updating the Request Dataset
Note:
Perform the procedure described in this section only if you have enabled request-based provisioning.
When you add an attribute on the process form, you also update the XML file containing the request dataset definitions. To update a request dataset:
Clearing Content Related to Request Datasets from the Server Cache
Note:
Perform the procedure described in this section only if you have enabled request-based provisioning.
Run the PurgeCache utility to clear content related to request datasets from the server cache. See Purging Cache in Oracle Fusion Middleware Administering Oracle Identity Governance for more information about the PurgeCache utility.
Adding Terminal Services Fields for Reconciliation and Provisioning
You can add additional terminal services fields for reconciliation and provisioning operations.
Note:
The information in this section is applicable only to the Microsoft Active Directory target system and only if you are going to use the target system as a target resource.
Terminal Services fields are only supported for Microsoft Active Directory and not Microsoft AD LDS. Skip this section you are using Microsoft AD LDS as the target system.
By default, the following terminal services fields are readily available for reconciliation and provisioning:
-
AllowLogon
-
TerminalServicesProfilePath
-
TerminalServicesHomeDirectory
If required, you can add the following terminal services fields for reconciliation and provisioning operations:
-
TerminalServicesInitialProgram
-
TerminalServicesWorkDirectory
-
AllowLogon
-
MaxConnectionTime
-
MaxDisconnectionTime
-
MaxIdleTime
-
ConnectClientDrivesAtLogon
-
ConnectClientPrintersAtLogon
-
DefaultToMainPrinter
-
BrokenConnectionAction
-
ReconnectionAction
-
EnableRemoteControl
-
TerminalServicesProfilePath
-
TerminalServicesHomeDirectory
-
TerminalServicesHomeDrive
The procedure described in the following sections can be applied to add terminal services fields for reconciliation and provisioning. Note that the terminal field names in the preceding list must be used as the decode value in the Lookup.ActiveDirectory.UM.ProvAttrMap and Lookup.ActiveDirectory.UM.ReconAttrMap lookup definitions for provisioning and reconciliation, respectively.
Adding the Group Name (pre-Windows 2000) Attribute
You can add a group name (pre-Windows 200) attribute for reconciliation and provisioning.
This section discusses the following topics related to adding the Group Name (pre-Windows 2000 ) attribute for reconciliation and provisioning:
About the Group Name (pre-Windows 2000) Attribute
Group Name and Group Name (pre-Windows 2000) are two of the attributes specific to groups in the target system.
Oracle Identity Governance contains only the Group Name field in its process form. By default, during group provisioning, the value that you specify for the Group Name field in the OIM process form, is entered as the value of the Group Name and Group Name (pre-Windows 2000) attributes. If you want to specify different values for the Group Name and Group Name (pre-Windows 2000) attributes in the target system, then you must create the Group Name (pre-Windows 2000) field on the OIM process form. To do so, you must add a new field (Group Name Pre Windows) in Oracle Identity Governance for reconciliation and provisioning operations.
Adding the Group Name Pre Windows Field for Reconciliation
You can add the Group Name Pre Windows field for reconciliation.
To do so, perform the following procedure:
-
Log in to the Oracle Identity Governance Design Console.
-
Add the Group Name Pre Windows field to the list of reconciliation fields in the resource object as follows:
-
Expand Resource Management and then double-click Resource Objects.
-
Search for and open the AD Group resource object.
-
On the Object Reconciliation tab, click Add Field.
-
In the Add Reconciliation Field dialog box, enter
Group Name Pre Windowsin the Field Name field and select String from the Field Type list. -
Click Save and close the dialog box.
-
Click Create Reconciliation Profile. This copies changes made to the resource object into MDS.
-
Click Save.
-
-
Update the Lookup.ActiveDirectory.GM.ReconAttrMap lookup definition for reconciliation as follows:
-
Expand Administration and then double-click Lookup Definition.
-
Search for and open the Lookup.ActiveDirectory.GM.ReconAttrMap lookup definition.
-
Click Add to create an entry for the Group Name Pre Windows field.
-
In the Code Key column, enter
Group Name Pre Windows.In the Decode column, entersAMAccountName. -
In the Code Key column, locate Group Name and change its Decode value to
cn.Table 6-1 lists the updated list of entries in the Lookup.ActiveDirectory.GM.ReconAttrMap lookup definition.Table 6-1 Entries in the Updated Lookup.ActiveDirectory.GM.ReconAttrMap Lookup Definition
Group Field on Oracle Identity Governance Microsoft Active Directory Field Display Name
displayName
Group name
cn
Group Name Pre Windows
sAMAccountName
Group Type
groupType
OIM Org Name
sAMAccountName
Organization Name[LOOKUP]
ad_container
Org Name
sAMAccountName
Org Type
OIM Organization Type
Unique Id
__UID__
-
Click Save.
-
-
Add the Group Name Pre Windows field on the process form as follows:
-
Expand Development Tools and then double-click Form Designer.
-
Search for and open the UD_ADGRP process form.
-
Click Create New Version, and then click Add.
-
Enter the details of the new field. In the Name field, enter
UD_ADUSER_GROUPNAME_PREWINDOWS.In the Field Label column, enterGroup Name Pre Windows.Enter the rest of the details of this field. -
On the Properties tab, select the Group Name Pre Windows field, and then click Add Property. The Add Property dialog box displays.
-
From the Property Name list, select Required.
-
In the Property Value field, enter
True. -
Click the Save icon and close the dialog box.
-
Click Save and then click Make Version Active.
-
-
Create a reconciliation field mapping for the new field in the provisioning process as follows:
-
Expand Process Management and then double-click Process Definition.
-
Search for and open the AD Group provisioning process.
-
On the Reconciliation Field Mappings tab of the provisioning process, click Add Field Map.
-
In the Add Reconciliation Field Mapping dialog box, from the Field Name field, select Group Name Pre Windows.
-
Double-click the Process Data field, and then select UD_ADGRP_GROUPNAME_PREWINDOWS.
-
Click Save and close the dialog box.
-
Click Save.
-
-
Expand Resource Management and then double-click Resource Objects.
-
Click Create Reconciliation Profile.
Adding the Group Name Pre Windows Field for Provisioning
You can add the Group Name Pre Windows field for provisioning.
To do so, perform the following procedures:
Adding the Group Name Pre Windows Field
If you have added the field on the process form by performing Step 4 of Adding the Group Name Pre Windows Field for Reconciliation, then you need not add the field again. If you have not added the field, then:
- Log in to the Oracle Identity Governance Design Console.
- Expand Development Tools and then double-click Form Designer.
- Search for and open the UD_ADGRP process form.
- Click Create New Version, and then click Add.
- In the Name field, enter
UD_ADUSER_GROUPNAME_PREWINDOWS. - In the Field Label column, enter
Group Name Pre Windows.Then, enter values for the rest of the columns as listed for the Group Name field. - On the Properties tab, select the Group Name Pre Windows field, and then click Add Property. The Add Property dialog box displays.
- From the Property Name list, select Required.
- In the Property Value field, enter
True. - Click the Save icon and close the dialog box.
- Click Save and then click Make Version Active.
Updating the Lookup.ActiveDirectory.GM.ProvAttrMap Lookup Definition
Update the Lookup.ActiveDirectory.GM.ProvAttrMap lookup definition for provisioning as follows:
Enabling Update Provisioning Operations on the Group Name Pre Windows Field
Enable update provisioning operations on the Group Name Pre Windows field as follows:
-
In the provisioning process, add a new task for updating the field as follows:
-
Expand Process Management and then double-click Process Definition.
-
Search for and open the AD Group provisioning process.
-
Click Add and enter the task name and task description as follows:
Task Name:
Group Name Pre Windows UpdatedTask Description:
Process Task for handling update of the Group Name Pre Windows field. -
In the Task Properties section, select the Conditional, Allow Cancellation while Pending, and Allow Multiple Instances fields.
-
Click Save.
-
-
In the provisioning process, select the adapter name in the Handler Type section as follows:
-
Go to the Integration tab, click Add.
-
In the Handler Selection dialog box, select Adapter.
-
From the Handler Name column, select adpADIDCUPDATEATTRIBUTEVALUE.
-
Click Save and close the dialog box.
-
-
In the Adapter Variables region, click the procInstanceKey variable.
-
In the dialog box that is displayed, create the following mapping:
Variable Name:
procInstanceKeyMap To:
Process DataQualifier:
Process Instance -
Click Save and close the dialog box.
-
Repeat Steps 3 through 5 for all the variables listed in the following table. This table lists values that you must select from the Map To, Qualifier, and Literal Value lists for each variable:
Variable Map To Qualifier Literal Value procInstanceKey
Process Data
Process Instance
NA
Adapter Return Variable
Response Code
NA
NA
itResourceFieldName
Literal
String
UD_ADGRP_SERVER
attrFieldName
Literal
String
Group Name Pre Windows
objectType
Literal
String
Group
-
On the Responses tab, click Add to add at least the SUCCESS response code, with Status
C.This ensures that if the custom task is successfully run, then the status of the task is displayed asCompleted. -
Click the Save icon and close the dialog box, and then save the process definition.
Updating Adapters
If the Group Name Updated process task calls the adpADIDCUPDATEATTRIBUTEVALUES adapter, then:
Updating the Request Dataset
Note:
Perform the procedures described in this section only if you want to perform request-based provisioning.
When you add an attribute on the process form, you also update the XML file containing the request dataset definitions. To update a request dataset:
Running the PurgeCache Utility
Note:
Perform the procedures described in this section only if you want to perform request-based provisioning.
Run the PurgeCache utility to clear content related to request datasets from the server cache. See Purging Cache in Oracle Fusion Middleware Administering Oracle Identity Governance for more information about the PurgeCache utility.
Configuring Transformation and Validation Of Data
You can configure transformation and validation of data for users, groups, and organizations.
About Configuring Transformation and Validation of Data
Configure transformation and validation of user account data by writing Groovy script logic while creating your application.
You can configure transformation of reconciled single-valued user data according to your requirements. For example, you can use First Name and Last Name values to create a value for the Full Name field in Oracle Identity Governance.
Similarly, you can configure validation of reconciled and provisioned single-valued data according to your requirements. For example, you can validate data fetched from the First Name attribute to ensure that it does not contain the number sign (#). In addition, you can validate data entered in the First Name field on the process form so that the number sign (#) is not sent to the target system during provisioning operations.
To configure transformation or validation of user account data, you must write Groovy scripts while creating your application. For more information about writing Groovy script-based validation and transformation logic, see Validation and Transformation of Provisioning and Reconciliation Attributes of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Configuring Transformation of Data During Reconciliation for Groups and Organizational Units
You can configure transformation of reconciled single-valued account data according to your requirements. For example, you can use User Name and Last Name values to create a value for the Full Name field in Oracle Identity Governance.
Note:
This section describes an optional procedure. Perform this procedure only if you want to configure transformation of data during reconciliation.You can configure transformation of reconciled data according to your requirements. For example, you can automate the look up of the field name from an external system and set the value based on the field name.
To configure transformation of data:
-
Write a code that implements the required transformation logic in a Java class.
The only criteria for the class is that it should have a method with the following name and signature:
public Object transform(HashMap hmUserDetails, HashMap hmEntitlementDetails, String sField) {} -
Create a JAR file to hold the Java class.
-
Run the Oracle Identity Governance Upload JARs utility to post the JAR file to the Oracle Identity Governance database. This utility is copied into the following location when you install Oracle Identity Governance:
Note:
Before you use this utility, verify that the
WL_HOMEenvironment variable is set to the directory in which Oracle WebLogic Server is installed.-
For Microsoft Windows: OIM_HOME/server/bin/UploadJars.bat
-
For UNIX: OIM_HOME/server/bin/UploadJars.sh
When you run the utility, you are prompted to enter the login credentials of the Oracle Identity Governance administrator, URL of the Oracle Identity Governance host computer, context factory value, type of JAR file being uploaded, and the location from which the JAR file is to be uploaded. Specify 1 as the value of the JAR type.
-
-
Add an entry in the lookup definition for transformation as follows:
-
Log in to the Design Console.
-
Search for and open one of the following lookup definitions:
-
For groups: Lookup.ActiveDirectory.GM.ReconTransformation
-
For organizational units: Lookup.ActiveDirectory.OM.ReconTransformation
-
-
In the Code Key column, enter the reconciliation field name for the attribute on which you want to apply the transformation. For example:
First Name. -
In the Decode column, enter the name of the class file. For example:
com.transformationexample.MyTransformer. -
Save the changes to the lookup definition.
Note:
To configure the transformation of data during trusted source reconciliation, then add the following entries in the Lookup.ActiveDirectory.OM.Configuration.Trusted lookup definition:
-
Code Key value:
Recon Transformation Lookup -
Decode value:
Lookup.ActiveDirectory.OM.ReconTransformation
-
Configuring Validation of Data During Reconciliation and Provisioning for Groups and Organizational Units
You can configure validation of reconciled and provisioned single-valued data according to your requirements. For example, you can validate data fetched from the First Name attribute to ensure that it does not contain the number sign (#). In addition, you can validate data entered in the First Name field on the process form so that the number sign (#) is not sent to the target system during provisioning operations.
To configure validation of data:
-
Write code that implements the required validation logic in a Java class.
This validation class must implement the validate method.
-
Create a JAR file to hold the Java class.
-
Run the Oracle Identity Governance Upload JARs utility to post the JAR file to the Oracle Identity Governance database. This utility is copied into the following location when you install Oracle Identity Governance:
Note:
Before you use this utility, verify that the
WL_HOMEenvironment variable is set to the directory in which Oracle WebLogic Server is installed.-
For Microsoft Windows: OIM_HOME/server/bin/UploadJars.bat
-
For UNIX: OIM_HOME/server/bin/UploadJars.sh
When you run the utility, you are prompted to enter the login credentials of the Oracle Identity Governance administrator, URL of the Oracle Identity Governance host computer, context factory value, type of JAR file being uploaded, and the location from which the JAR file is to be uploaded. Specify 1 as the value of the JAR type.
-
-
If you created the Java class for validating a process form field for reconciliation, then:
-
Log in to the Design Console.
-
Search for and open one of the following lookup definitions:
-
For groups: Lookup.ActiveDirectory.GM.ReconValidation
-
For organizational units: Lookup.ActiveDirectory.OM.ReconValidation
-
-
In the Code Key column, enter the resource object field name. In the Decode column, enter the class name (for example:
com.validate.MyValidation). -
Save the changes to the lookup definition.
-
Search for and open one of the following lookup definitions:
-
For groups: Lookup.ActiveDirectory.GM.Configuration
-
For organizational units: Lookup.ActiveDirectory.OM.Configuration
-
-
Ensure that the value of the Recon Validation Lookup entry is set to one of the following:
-
For groups:
Lookup.ActiveDirectory.GM.ReconValidation. -
For organizational units:
Lookup.ActiveDirectory.OM.ReconValidation.
-
-
Save the changes to the lookup definition.
-
-
If you created the Java class for validating a process form field for provisioning, then:
-
Log in to the Design Console.
-
Search for and open one of the following lookup definitions:
-
For groups: Lookup.ActiveDirectory.GM.ProvValidation
-
For organizational units: Lookup.ActiveDirectory.OM.ProvValidation
-
-
In the Code Key column, enter the process form field name. In the Decode column, enter the class name (for example:
com.validate.MyValidation). -
Save the changes to the lookup definition.
-
Search for and open one of the following lookup definitions:
-
For groups: Lookup.ActiveDirectory.GM.Configuration
-
For organizational units: Lookup.ActiveDirectory.OM.Configuration
-
-
Ensure that the value of the Provisioning Validation Lookup entry is set to one of the following:
-
For groups:
Lookup.ActiveDirectory.GM.ProvValidation. -
For organizational units:
Lookup.ActiveDirectory.OM.ProvValidation.
-
-
Save the changes to the lookup definition.
-
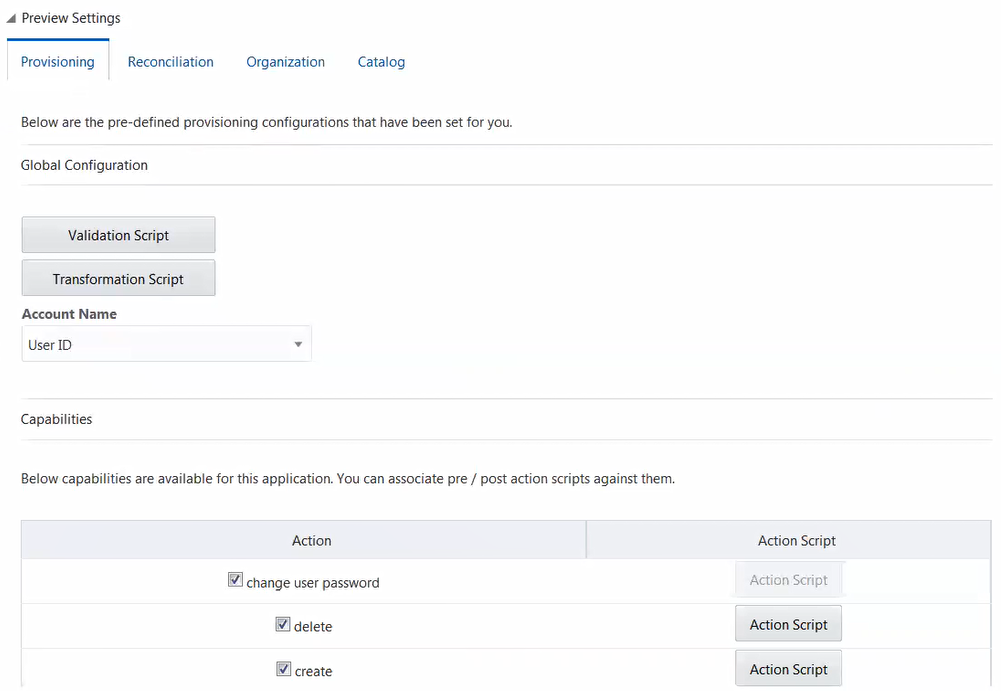
Action Scripts
Actions are scripts that you can configure to run before or after the create, update, or delete an account provisioning operations.
For example, you can configure a script to run before every user creation. Similarly, you can run custom PowerShell scripts before or after creating, updating, or deleting a mailbox.
The following are topics pertaining to action scripts:
Action Scripts for Users
The following are topics pertaining to action scripts for users:
About Configuring Action Scripts for Users
You can configure Action Scripts by writing your own PowerShell scripts while creating your application.
These scripts can be configured to run before or after the create, update, or delete an account provisioning operations. For example, you can configure a script to run before every user creation operation.
For information on adding or editing action scripts, see Updating the Provisioning Configuration in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Note:
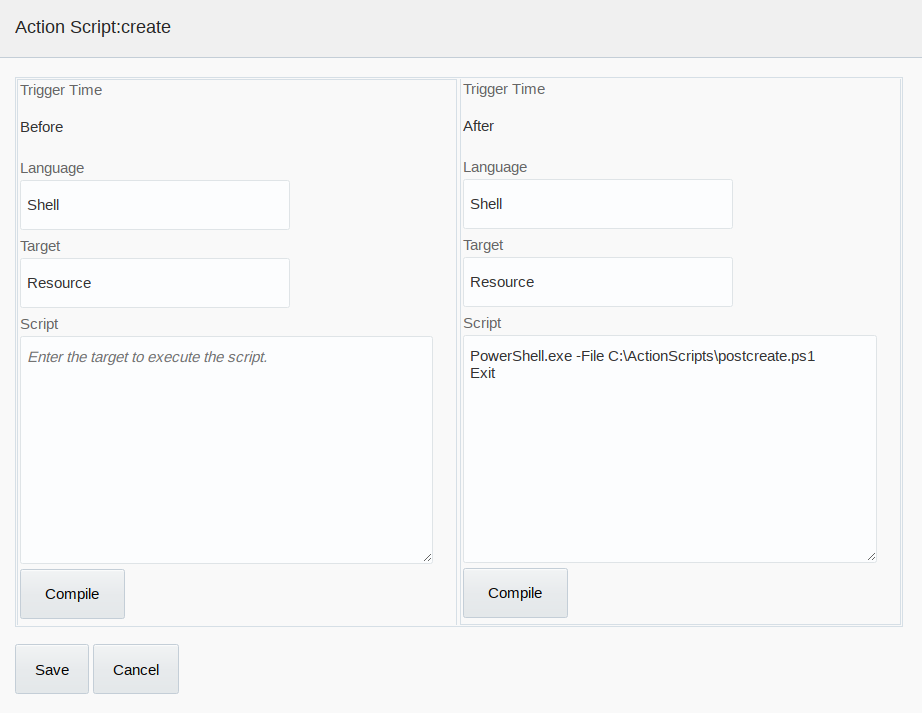
The scripting language used is PowerShell.Running a Custom PowerShell Script for Users
As an example, the following procedure describes the steps to run a custom PowerShell script before a create operation:
Running Actions Using Visual Basic Scripts for Users
The following is an example procedure for running actions using Visual Basic scripts that consumes data dynamically from the process form. This is an example procedure for an After Create action, which requires creating a user in an organizational unit in addition to the one in which the user is provisioned to.
Important Notes on Running Actions Scripts for Users
The following are important notes on running actions scripts:
-
Any errors encountered while running action scripts are ignored and are not propagated to Oracle Identity Governance.
-
During create operations, all attributes part of process form are available to the script.
-
During update operations, only the attribute that is being updated is available to the script.
-
During delete operations, only the __UID__ (GUID) attribute is available to the script.
Guidelines on Creating Scripts for Users
The following are the guidelines that you must apply or be aware of while configuring action scripts:
-
All field names used in the scripts must be enclosed within %%.
-
You can call any VB script from a shell and pass the process form fields.
-
You cannot include the Password field in the script. This is because password is stored as a guarded string. Therefore, we do not get the exact password when we fetch values for the Password field.
-
Addition of child table attributes belongs to the 'Update' category and not 'Create.'
Action Scripts for Groups and Organizational Units
The following are topics pertaining to action scripts for groups and organizational units:
-
About Configuring Action Scripts for Groups and Organizational Units
-
Running a Custom PowerShell Script for Groups and Organizational Units
-
Running Actions Using Visual Basic Scripts for Groups and Organizational Units
-
Important Notes on Running Actions Scripts for Groups and Organizational Units
-
Guidelines on Creating Scripts for Groups and Organizational Units
About Configuring Action Scripts for Groups and Organizational Units
You can configure Action Scripts by writing your own PowerShell scripts while creating your application.
These scripts can be configured to run before or after the create, update, or delete an account provisioning operations. For example, you can configure a script to run before every user creation operation.
Note:
The scripting language used is PowerShell.Running a Custom PowerShell Script for Groups and Organizational Units
As an example, the following procedure describes the steps to run a custom PowerShell script before a create operation:
Note that you can pass process form fields to scripts that call the before or after action scripts. These process form fields must be present in Lookup.ActiveDirectory.GM.ProvAttrMap or Lookup.ActiveDirectory.OU.ProvAttrMap lookup definitions and be mapped to a corresponding target system attribute. For example, you can pass the First Name process form field (present in Lookup.ActiveDirectory.GM.ProvAttrMap or Lookup.ActiveDirectory.OU.ProvAttrMap lookup definitions) to an action script by specifying "givenName," which is the name of the corresponding attribute in the target system.
Note:
Process form fields marked as IGNORE are not sent to the connector.
Running Actions Using Visual Basic Scripts for Groups and Organizational Units
The following is an example procedure for running actions using Visual Basic scripts that consumes data dynamically from the process form. This is an example procedure for an After Create action, which requires creating a user in an organizational unit in addition to the one in which the user is provisioned to.
Important Notes on Running Actions Scripts for Groups and Organizational Units
The following are important notes on running actions scripts:
-
Any errors encountered while running action scripts are ignored and are not propagated to Oracle Identity Governance.
-
During create operations, all attributes part of process form are available to the script.
-
During update operations, only the attribute that is being updated is available to the script.
If other attributes are also required, then a new adapter calling
ICProvisioningManager# updateAttributeValues(String objectType, String[] labels)must be created and used. During adapter mapping in process task, add the form field labels of the dependent attributes. -
During delete operations, only the __UID__ (GUID) attribute is available to the script.
Guidelines on Creating Scripts for Groups and Organizational Units
The following are the guidelines that you must apply or be aware of while configuring action scripts:
-
Your script file can contain scripts that include attributes present in the decode column of any of the following lookup definitions:
-
Lookup.ActiveDirectory.GM.ProvAttrMap
-
Lookup.ActiveDirectory.OM.ProvAttrMap
-
-
All field names used in the scripts must be enclosed within %%.
-
You can call any VB script from a shell and pass the process form fields.
-
You cannot include the Password field in the script. This is because password is stored as a guarded string. Therefore, we do not get the exact password when we fetch values for the Password field.
-
Addition of child table attributes belongs to the 'Update' category and not 'Create.'
Enabling Reconciliation and Provisioning Operations Across Multiple Domains
The Microsoft Active Directory User Management connector supports reconciliation and provisioning operations across multiple domains in a single forest.
Note:
The information in this section is applicable only if you are using Microsoft Active Directory as the target system. Enabling reconciliation and provisioning operations across multiple domains is not supported if you are using Microsoft AD LDS as the target system.
Reconciliation runs are performed by using the Global Catalog Server and provisioning operations are performed by using LDAP referrals.
If you want to enable reconciliation and provisioning across multiple domains, then perform the procedure described in the following sections:
Understanding Enabling Reconciliation Across Multiple Domains
This following sections help you understand enabling reconciliation across multiple domains:
About Enabling Reconciliation Across Multiple Domains
To perform reconciliation across multiple domains, this connector uses both the domain controller and the Global Catalog Server for fetching records from the target system.
During reconciliation, records from the Global Catalog Server are fetched to the connector. After a record is fetched into the connector, the distinguishedName and uSNChanged attribute values are read. By using the distinguishedName, the connector performs an LDAP query on the domain controller that contains the actual data (referrals are used here). This approach is used for reconciliation because the Global Catalog Server has only partial set of records. Complete data can only be fetched from the domain controller.
After all records are fetched into Oracle Identity Governance, the reconciliation engine updates the Latest Token attribute of the scheduled job with the maximum value of the uSNChanged attribute of a domain controller on which the Global Catalog Server is running. From the next reconciliation run onward, only records whose uSNChanged attribute values are greater than current value in the Latest Token attribute are fetched from the Global Catalog Server. Therefore, any updates made to a record on the target system must update the uSNChanged attribute of that record in the Global Catalog Server so that the connector can detect records that have been updated since the last reconciliation run and then fetch them into Oracle Identity Governance.
Enabling Reconciliation Across Multiple Domains
To enable reconciliation across multiple domains:
- Set the value of the Search Child Domains parameter of Advanced Settings Parameters to
yes. - Specify the name of the domain controller that is hosting the Global Catalog Server as the value of the Global Catalog Server parameter of the Basic Configuration Parameters section.
Note:
-
If the value of the Search Child Domains parameter is set to
yesand no value is specified for the Global Catalog Server parameter, then the connector determines the Global Catalog Server on its own. It is strongly recommended that you specify a value for the Search Child Domains parameter in the Advanced Settings Parameters and the Global Catalog Server parameter in the Basic Configuration Parameters. -
While performing group reconciliation in a cross-domain environment, the connector fetches only those groups of the account that are visible to the domain controller on which the account is present.
-
It is recommended to not enter any value for LDAP Host Name parameter of the Basic Configuration Parameters section. The connector will automatically find the right domain controller to fetch complete user information after obtaining the distinguished name from the global catalog server. If you specify a value for the LDAP Host Name parameter, then the connector ignores it and determines the appropriate domain controller (for fetching user information) by using the ADSI referrals feature.
Understanding Enabling Provisioning Across Multiple Domains
In a parent-child deployment environment of the target system, before performing provisioning operations across multiple domains, it is expected that the target system IT resource is configured with the parent domain. In a replication environment of the target system, before performing provisioning operations across multiple domains, it is expected that the target system IT resource is configured with any of the domain controllers.
This scenario is illustrated by the following example:
Suppose a parent-child domain environment in which the parent domain is dc1 and child domain is dc2. The target system IT resource is configured to include dc1 as the value of the LDAP Host Name parameter and the name of the parent domain as the value of the DomainName parameter.
During provisioning, if we select an organization that belongs to the child domain, multiple groups that span across domains, and the manager from the parent domain, then LDAP referrals are internally used by ADSI (Active Directory Service Interfaces). This is because all connectors operations are leveraged to ADSI, which enables creation of an account in the child domain even without providing any details of the child domain in the IT resource.
All this information is internally calculated depending upon the organization that is selected during the provisioning operation. In the connector, the referral chasing option is set to All, which means that all referrals are chased when any referral is provided by the domain controller. Therefore, no explicit configuration procedure is required to enable provisioning across multiple domains.
See Also:
The ADSI documentation for more information about LDAP referrals
About Using the Connector for Multiple Trusted Source Reconciliation
You can use the connector for more than one trusted source reconciliation.
The following are examples of scenarios in which there is more than one trusted source for user data in an organization:
-
One of the target systems is a trusted source for data about employees. The second target system is a trusted source for data about contractors. The third target system is a trusted source for data about interns.
-
One target system holds the data of some of the identity fields that constitute an OIM User. Two other systems hold data for the remaining identity fields. In other words, to create an OIM User, data from all three systems would need to be reconciled.
If the operating environment of your organization is similar to that described in either one of these scenarios, then this connector enables you to use the target system as one of the trusted sources of user data in your organization.
Multiple Installations of the Target System
You can use the Active Directory User Management connector in an environment containing multiple target systems.
The following are topics related to multiple target system installations:
About Multiple Installations of the Target System
You must create copies of configurations of your base application to configure it for multiple installations of the target system.
Note:
The information in this section also applies to Microsoft AD LDS.
-
If you are upgrading from 11.1.2.x to 12.2.1.3.0, then:
Perform the procedure described in this section if your environment has multiple installations of the target system, which share the same schema managed by this connector. In such a scenario, if you are using Oracle Identity Governance release 12.2.1.3.0, then only the IT resource information must be changed. If you are using Oracle Identity Governance release 12.2.1.3.0, then the IT resource information must be changed and application instances must be created.
In addition, irrespective of the Oracle Identity Governance release that you are using, scheduled tasks must be replicated, but the underlying workflow and process form is shared across all installations of the target system.
If your environment has multiple installations of the target system and the schema differs (that is, different sets of attributes must be managed by using the connector. In other words, you need different process forms, workflows, and so on), then you must use the connector cloning feature.
-
If you are using Application On-Boarding, then:
Perform the procedure described in this section if your environment has multiple installations of the target system, which share the same schema managed by this connector. In such a scenario, if you are using Oracle Identity Governance release 12.2.1.3.0, then the basic configuration information must be changed and a new application must be created.
If your environment has multiple installations of the target system and the schema differs (that is, different sets of attributes must be managed by using the connector. In other words, you need different process forms, workflows, and so on), then you must create a new application.
You may want to configure the connector for multiple installations of Microsoft Active Directory. The following example illustrates this requirement:
The Tokyo, London, and New York offices of Example Multinational Inc. have their own installations of Microsoft Active Directory. The company has recently installed Oracle Identity Governance, and they want to configure Oracle Identity Governance to link all the installations of Microsoft Active Directory.
To meet the requirement posed by such a scenario, you must configure the connector for multiple installations of Microsoft Active Directory.
Configuring the Connector for Multiple Installations of the Target System
You can configure the connector for multiple installations of the target system by upgrading the connector from Oracle Identity Governance release 11.1.2.x to 112.2.1.3.0 or through application on-boarding.
To configure the connector for multiple installations of the target system, perform one of the procedures listed in the following sections:
Configuring the Connector for Multiple Installations of the Target System while Upgrading from Oracle Identity Governance release 11.1.2.x to 12.2.1.3.0
To configure the connector for multiple installations of the target system:
- Create IT resources of the Active Directory IT resource type so that there is one IT resource for each installation of the target system. If you are using Oracle Identity Governance release 12.2.1.3.0 or later, then in addition to creating the IT resource, you must create the application instance.
- Create copies of the reconciliation scheduled tasks for each installation of the target system. While creating a scheduled task, specify attribute values corresponding to the target system installation for which you are creating the scheduled task.
- Manually synchronize the lookup definitions in Oracle Identity Governance with the lookup field values on the target system.
Configuring the Connector for Multiple Installations of the Target System Using Application On-Boarding
To configure the connector for multiple installations of the target system:
- Create a new application using application on-boarding for multiple installation of the target system.
- Manually synchronize the lookup definitions in Oracle Identity Governance with the lookup field values on the target system.
Creating a Home Directory After User Create Provisioning Operation
You can initiate the process to update the home directory after the Create User provisioning operation.
To accomplish this task in Application On-Boarding, you must write a post-create Action Script and make the home directory creation changes in that script itself.
Configuring the Connector for Provisioning Groups of the Security Group - Universal Group Type
You can create a group of type Security Group - Universal by adding this group type to the Lookup.ActiveDirectory.GroupTypes lookup definition.
There are six types of groups that you can create in the target system. By default, this connector is shipped with only five group types that you can select for the group that you create through Oracle Identity Governance. If you want to create a group of type Security Group - Universal, then you must add this group type to the Lookup.ActiveDirectory.GroupTypes lookup definition as follows: