3 Configuring the SAP User Management Engine Connector
While creating a target application, you must configure connection-related parameters that the connector uses to connect Oracle Identity Governance with your target system and perform connector operations. In addition, you can view and edit attribute mappings between the process form fields in Oracle Identity Governance and target system columns, predefined correlation rules, situations and responses, and reconciliation jobs.
3.1 Basic Configuration Parameters
These are the connection-related parameters that Oracle Identity Governance requires to connect to target applications.
Table 3-1 Parameters in the Basic Configuration Section for the SAP UME Connector with SoD
| Parameters | Mandatory? | Description |
|---|---|---|
| Connector Server Name | No | If you created an IT resource of the type "Connector
Server," then enter its name.
Note: Enter a value for this parameter only if you have deployed the SAP UME connector in the Connector Server. |
| changePwdFlag | Yes | For accounts created through Oracle Identity Governance,
password management can be configured by using the changePwdFlag and
dummyPassword parameters of the basic configuration parameters.
Default value: See Configuring Password Changes for Newly Created Accounts for more information about this parameter. |
| dummyPassword | Yes | Enter the dummy password that you want the connector to use during a Create User provisioning operation. The connector first sets the password as this value and then changes it to the password specified on the process form. |
| enableDate | Yes | Enter the date in the YYYY-MM-DD format to enable a user
with end date as default value.
Default value:
|
| logSPMLRequst | No | Enter yes to specify that the SPML
requests being sent to the target system be written to the log file.
Otherwise, enter no.
|
| logonNameInitialSubstring | Yes | Enter the set of characters to support full
reconciliation for the English language. For other languages, enter all
characters of that language.
Sample value:
|
| pwdHandlingSupport | Yes | If SAP User Management Engine is configured with an
LDAP-based data source in writable mode, then SSL configuration between
SAP User Management Engine and the LDAP-based data source is mandatory
for password management. In such a scenario, if SSL is not configured
between SAP User Management Engine and the LDAP-based data source and
password need not be maintained from SAP User Management Engine, then
set the value of this parameter to no. Otherwise,
set the value of this parameter to yes.
Default value: yes |
| TopologyName | No | Name of the topology of the target system host computer. |
| umePassword | Yes | Enter the password of the target system user account
that you create for connector operations.
See Creating a Target System User Account for Connector Operations for more information. |
| umeUrl | Yes |
Sample value:
|
| umeUserId | Yes | Enter the user ID of the target system user account that
you create for connector operations.
See Creating a Target System User Account for Connector Operations for more information. |
Table 3-2 Parameters in the Basic Configuration Section for the SAP AC UME Connector
| Parameters | Mandatory? | Description |
|---|---|---|
| Connector Server Name | No | If you created an IT resource of the type "Connector Server," then enter its name.
Note: Enter a value for this parameter only if you have deployed the SAP UME connector in the Connector Server. |
| changePwdFlag | Yes | For accounts created through Oracle Identity Governance, password management can be configured by using the changePwdFlag and dummyPassword parameters of the basic configuration parameters.
Default value: See Configuring Password Changes for Newly Created Accounts for more information about this parameter. |
| dummyPassword | Yes | Enter the dummy password that you want the connector to use during a Create User provisioning operation. The connector first sets the password as this value and then changes it to the password specified on the process form. |
| enableDate | Yes | Enter the date in the YYYY-MM-DD format to enable a user with end date as default value.
Default value: |
| logSPMLRequst | No | Enter yes to specify that the SPML requests being sent to the target system be written to the log file. Otherwise, enter no.
|
| logonNameInitialSubstring | Yes | Enter the set of characters to support full reconciliation for the English language. For other languages, enter all characters of that language.
Sample value: |
| pwdHandlingSupport | Yes | If SAP User Management Engine is configured with an LDAP-based data source in writable mode, then SSL configuration between SAP User Management Engine and the LDAP-based data source is mandatory for password management. In such a scenario, if SSL is not configured between SAP User Management Engine and the LDAP-based data source and password need not be maintained from SAP User Management Engine, then set the value of this parameter to no. Otherwise, set the value of this parameter to yes.
Default value: yes |
| TopologyName | No | Name of the topology of the target system host computer. |
| umePassword | Yes | Enter the password of the target system user account that you create for connector operations.
See Creating a Target System User Account for Connector Operations for more information. |
| umeUrl | Yes |
Sample value: |
| umeUserId | Yes | Enter the user ID of the target system user account that you create for connector operations.
See Creating a Target System User Account for Connector Operations for more information. |
|
grcLanguage |
Yes |
This parameter defines the language in which we are sending requests to SAP GRC system. Value: Note: This parameter is applicable only to the SAP AC UME connector. |
|
grcPassword |
Yes |
This parameter holds the password for accessing the SAP GRC system. Note: This parameter is applicable only to the SAP AC UME connector. |
|
grcUsername |
Yes |
This parameter holds the user name for accessing the SAP GRC system. Note: This parameter is applicable only to the SAP AC UME connector. |
3.2 Advanced Setting Parameters
These are the configuration-related entries that the connector uses during reconciliation and provisioning operations.
Table 3-3 Advanced Setting Parameters for the SAP UME Connector with SoD
| Parameter | Mandatory? | Description |
|---|---|---|
| Bundle Name | No | This parameter holds the name of the connector bundle package.
Default Value: |
| Bundle Version | No | This parameter holds the version of the connector bundle class. Do not modify this parameter.
Default Value: |
| Connector Name | No | This parameter holds the name of the connector class. Do not modify this parameter.
Default Value: |
| ConnectorImplType | No |
Enter the value |
| Group attribute name | No | This parameter holds the name of the role duty type used in SIL.
Default Value: |
| Group form names | Yes | This value is used to get the group child form names in SIL Layer. Do not modify this value.
Default Value: |
| Role attribute name | No | Name of the role duty type used in SIL.
Default Value: |
| Role form names | Yes | This value is used to get the role child form names from the SIL Layer. Do not modify this value.
Default Value: |
| RoleAttributeLabel | No | Label name of the role ID field in the child form.
Default Value: |
|
entitlementRiskAnalysisAccessURL |
No |
This parameter holds the WSDL URL for the Entitlement Risk Analysis web service. Default Value: Note: This parameter is applicable only to the SAP UME with SoD |
|
wsdlFilePath |
No |
Enter the absolute path of the directory containing the following file: GRAC_RISK_ANALYSIS_WOUT_NO_WS.WS D |
|
entitlementRiskAnalysisWS |
Yes |
Web service client class to perform risk analysis without request number. Default Value: Note: This parameter is applicable only to the SAP UME with SoD |
|
SODSystemKey |
Yes |
Name of the RFC destination/Connector used for connecting GRC with portal. Default Value: Note: This parameter is applicable only to the SAP UME with SoD |
Table 3-4 Advanced Setting Parameters for the SAP AC UME Connector
| Parameter | Mandatory? | Description |
|---|---|---|
|
appLookupAccessURL |
No |
WSDL URL for Application Lookup web service. Default Value: |
|
appLookupWS |
No |
Web service client class to get all applications configured in SAP GRC. Default Value: |
|
assignRoleReqType |
No |
This entry holds the name of the request type that is used for assign role request in SAP GRC. The format of the decode value is as follows: Default Value: |
|
auditLogsAccessURL |
No |
WSDL URL for Audit Logs web service. Default Value: |
|
auditLogsWS |
No |
Web service client class to get audit logs. Default Value: |
|
Bundle Name |
No |
Name of the connector bundle package. Default Value: |
|
Bundle Version |
No |
This parameter holds the version of the connector bundle class. Do not modify this parameter. Default Value: |
|
Connector Name |
No |
This parameter holds the name of the connector class. Do not modify this parameter. Default Value: |
|
ConnectorImplType |
No |
Enter the value Default Value: |
|
createUserReqType |
No |
Name of the request type that the connector must use for the create user request in SAP GRC. Default Value: |
|
deleteUserReqType |
No |
Name of the request type that the connector must use for the delete user request in SAP GRC. Default Value: |
|
ignoreOpenStatus |
No |
Specify whether the connector must send the new request for a particular user even if the last request for the user is in the Open status. Default Value: |
|
lockUserReqType |
No |
This parameter holds the name of the request type to use to lock user request in SAP GRC. Default Value: |
|
logAuditTrial |
No |
Specify whether the connector must log complete audit trails whenever status request web service is invoked. Default Value: |
|
modifyUserReqType |
No |
This parameter holds the name of the request type to use for modify user request in SAP GRC. Default Value: |
|
otherLookupAccessURL |
No |
URL for other lookup web service areas such as Business Process, Funcational Area. Default Value: |
|
otherLookupWS |
No |
Web service client class to get other lookup field details such as Business Process, Function Area, and so on. Default Value: |
|
provActionAttrName |
No |
Name of the attribute in the target system that contains the details required for performing provisioning operations to a specific backend system. Default Value: |
|
provItemActionAttrName |
No |
Name of the attribute in the target system that contains the details required for performing provisioning roles. Default Value: |
|
removeRoleReqType |
No |
Name of the request type to use for remove user request in SAP GRC. Default Value: |
|
requestStatusAccessURL |
No |
WSDL URL for Status Request web service. Default Value: |
|
requestStatusValue |
No |
The value that get updated in the AC Request Status field on the process form. Default Value: |
|
requestStatusWS |
No |
Web service client class to get status of provisioning request. Default Value: |
|
requestTypeAttrName |
No |
Name of the request type parameter used to differentiate request flows from the SAPUMCREATE adapter. Default Value: |
|
riskLevel |
No |
In SAP GRC, each business risk is assigned a criticality level. You can control the risk analysis data returned by SAP GRC by specifying a risk level. Default Value: |
|
Role form names |
No |
This value is used to get the role child form names in SIL Layer. Do not modify this value. Default Value: |
|
roleLookupAccessURL |
No |
WSDL URL for Role Lookup web services. Default Value: |
|
roleLookupWS |
No |
Web service client class to get all roles. Default Value: |
|
unlockUserReqType |
No |
Name of the request type to use for unlock user request in SAP GRC. Default Value: |
|
userAccessAccessURL |
No |
WSDL URL for User Access web service. Default Value: |
|
userAccessWS |
No |
Web service client class to get status of user access. Default Value: |
|
wsdlFilePath |
No |
File path where the WSDL files are available in local machine. Default Value: Note: If you are using a Connector Server, copy the WSDL File on the system running the Connector Server. Location of the WSDL files is available in the local machine that is running the Connector Server. |
3.3 Attribute Mappings
The attribute mappings on the Schema page vary depending on whether you are using the SAP UME or SAP AC UME connector.
3.3.1 Attribute Mappings for the SAP UME Connector
The Schema page for an SAP UME target application displays the default schema (provided by the connector) that maps Oracle Identity Governance attributes to target system attributes. The connector uses these mappings during reconciliation and provisioning operations.
SAP UME User Account Attributes
Table 3-5 lists the user-specific attribute mappings between the process form fields in Oracle Identity Governance and SAP UME attributes. The table also lists whether a specific attribute is used during provisioning or reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit these attribute mappings by adding new attributes or deleting existing attributes on the Schema page as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-5 Default Attribute Mappings for the SAP UME User Account
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Provision Field? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|---|
|
Logon Name |
_NAME_ |
String |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Password |
_PASSWORD_ |
String |
No |
Yes |
No |
No |
No |
|
First Name |
firstname |
String |
No |
Yes |
Yes |
No |
No |
|
Last Name |
lastname |
String |
Yes |
Yes |
Yes |
No |
No |
|
E Mail Address |
|
String |
No |
Yes |
Yes |
No |
No |
|
Fax |
fax |
String |
No |
Yes |
Yes |
No |
No |
|
Mobile |
mobile |
String |
No |
Yes |
Yes |
No |
No |
|
Telephone |
telephone |
String |
No |
Yes |
Yes |
No |
No |
|
Department |
department |
String |
No |
Yes |
Yes |
No |
No |
|
Name |
displayname |
String |
No |
Yes |
Yes |
No |
No |
|
Title |
title |
String |
No |
Yes |
Yes |
No |
No |
|
Form of Address |
salutation |
String |
No |
Yes |
Yes |
No |
No |
|
Postion |
jobtitle |
String |
No |
Yes |
Yes |
No |
No |
|
Start Date of Account Validity (date) |
validfrom |
String |
No |
Yes |
Yes |
No |
No |
|
End Date of Account Validity (date) |
validto |
String |
No |
Yes |
Yes |
No |
No |
|
Street |
streetaddress |
String |
No |
Yes |
Yes |
No |
No |
|
Language |
locale |
String |
No |
Yes |
Yes |
No |
No |
|
Timezone |
timezone |
String |
No |
Yes |
Yes |
No |
No |
|
State |
state |
String |
No |
Yes |
Yes |
No |
No |
|
City |
city |
String |
No |
Yes |
Yes |
No |
No |
|
Zip |
zip |
String |
No |
Yes |
Yes |
No |
No |
|
User Account Locked |
islocked |
String |
No |
Yes |
Yes |
No |
No |
|
Security Policy |
securitypolicy |
String |
No |
Yes |
Yes |
No |
No |
|
Unique ID |
_UID_ |
String |
No |
Yes |
Yes |
No |
No |
|
Country |
country |
String |
No |
Yes |
Yes |
No |
No |
|
SoDCheckStatus |
String |
No |
Yes |
Yes |
No |
No |
|
|
SoDCheckResult |
String |
No |
Yes |
Yes |
No |
No |
|
|
SoDCheckEntitlement |
String |
No |
Yes |
Yes |
No |
No |
|
|
SoDCheckTimestamp |
String |
No |
Yes |
Yes |
No |
No |
|
|
Status |
_Enable_ |
String |
No |
Yes |
Yes |
No |
No |
Figure 3-1 shows the default User account attribute mappings.
Figure 3-1 Default Attribute Mappings for the SAP UME User Account
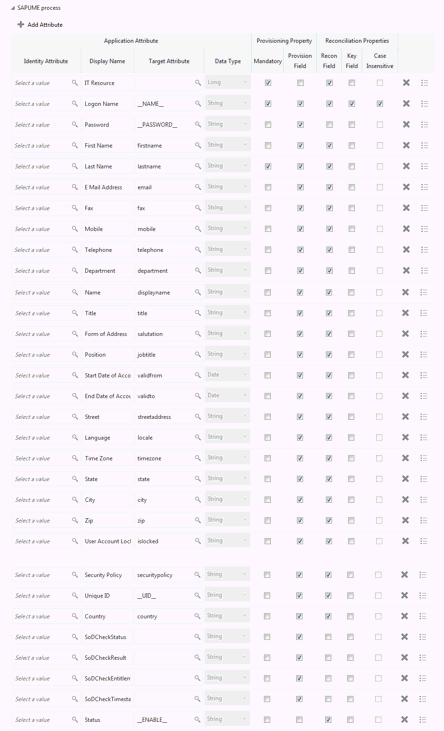
Description of "Figure 3-1 Default Attribute Mappings for the SAP UME User Account"
Group Entitlement Attributes
Table 3-6 lists the group-specific attribute mappings between the process form fields in Oracle Identity Governance and SAP UME attributes. The table lists whether a given attribute is mandatory during provisioning. It also lists whether a given attribute is used during reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit these attributes mappings by adding new attributes or deleting existing attributes on the Schema page as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-6 Default Attribute Mappings for Group Entitlement
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|
|
Datasource |
Datasource |
String |
No |
No |
No |
No |
|
Group |
assignedgroups |
String |
Yes |
Yes |
Yes |
No |
Figure 3-2 shows the group entitlement mappings.
Figure 3-2 Default Attribute Mappings for Group Entitlement
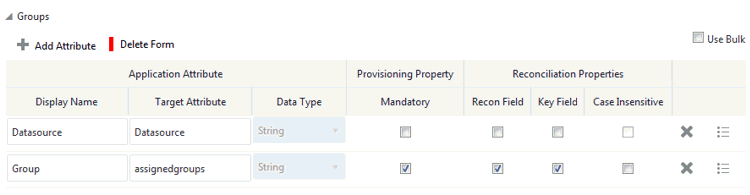
Description of "Figure 3-2 Default Attribute Mappings for Group Entitlement"
Role Entitlement Attributes
Table 3-7 lists the role-specific attribute mappings between the process form fields in Oracle Identity Governance and SAP UME attributes. The table lists whether a given attribute is mandatory during provisioning. It also lists whether a given attribute is used during reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit these attribute mappings by adding new attributes or deleting existing attributes on the Schema page as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-7 Default Attribute Mappings for a Role Entitlement
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|
|
Datasource |
Datasource |
String |
No |
No |
No |
No |
|
role |
assignedroles |
String |
Yes |
Yes |
Yes |
No |
Figure 3-3 Default Attribute Mappings for a Role Entitlement
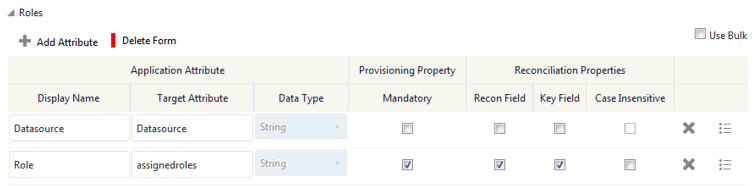
Description of "Figure 3-3 Default Attribute Mappings for a Role Entitlement"
3.3.2 Attribute Mapping for the SAP AC UME Connector
The Schema page for an SAP AC UME target application displays the default schema (provided by the connector) that maps Oracle Identity Governance attributes to target system attributes. The connector uses these mappings during reconciliation and provisioning operations.
SAP AC UME User Account Attributes
Table 3-8 lists the user-specific attribute mappings between the process form fields in Oracle Identity Governance and SAP AC UME attributes. The table also lists whether a specific attribute is used during provisioning or reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit these attribute mappings by adding new attributes or deleting existing attributes on the Schema page as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-8 Default Attribute Mappings for the SAP AC UME User Account
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Provision Field? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|---|
| logon Name | UserId;UserInfo | String | Yes | Yes | Yes | Yes | Yes |
| Password | _PASSWORD_ | String | No | No | No | No | No |
| First Name | fname;UserInfo | String | No | No | Yes | No | No |
| Last Name | Iname;UserInfo | String | No | No | Yes | No | No |
| E Mail Address | email;Userinfo | String | No | No | Yes | No | No |
| Fax | fax;UserInfo | String | No | No | Yes | No | No |
| Mobile | personnelno;UserInfo | String | No | No | Yes | No | No |
| Telephone | telnumber;UserInfo | String | No | No | Yes | No | No |
| Department | department;UserInfo | String | No | No | Yes | No | No |
| Name | displayname | String | No | No | Yes | No | No |
| Form of Address | personnelarea;UserInfo | String | No | No | Yes | No | No |
| Position | empposition;UserInfo | String | No | No | Yes | No | No |
| Start Date of Account Validity (date) | validFrom;UserInfo | Date | No | No | Yes | No | No |
| End Date of Account Validity (date) | validTo;UserInfo | Date | No | No | Yes | No | No |
| Street | streetaddress | String | No | No | Yes | No | No |
| Language | logonLang;Userinfo | String | No | No | Yes | No | No |
| Time Zone | timezone | String | No | No | Yes | No | No |
| State | state | String | No | No | Yes | No | No |
| City | city | String | No | No | Yes | No | No |
| Zip | zip | String | No | No | Yes | No | No |
| User Account Locked | userLocak;None | String | No | No | Yes | No | No |
| Security Policy | securitypolicy | String | No | No | Yes | No | No |
| Unique ID | _UID_ | String | No | No | Yes | No | No |
| Country | country | String | No | No | Yes | No | No |
| AC Request Id | RequestId | String | No | No | Yes | No | No |
| AC Request Status | RequestStatus | String | No | No | Yes | No | No |
| AC Request Type | RequestType | String | No | No | Yes | No | No |
| AC Manager | manager;UserInfo | String | No | No | No | No | No |
| AC Manager email | manager;UserInfo | String | No | No | No | No | No |
| AC Manager First Name | managerFirstname;Userinfo | String | No | No | No | No | No |
| AC Manager Last Name | managerLastname;Userinfo | String | No | No | No | No | No |
| AC Priority | priority;Header | String | No | No | No | No | No |
| AC Request Reason | requestreason;Header | String | No | No | No | No | No |
| AC Request Due Date (Date) | reqDueDate;Header | Date | No | No | No | No | No |
| AC System | reqInitSystem;Header | String | No | No | No | No | No |
| AC Functional Area (Lookup) | funcarea;Header | String | No | No | No | No | No |
| AC Business Process (Lookup) | bproc;Header | String | No | No | No | No | No |
| AC Requestor ID | requestorId:Header | String | No | No | No | No | No |
| AC Requestor email | email;Header | String | No | No | No | No | No |
| Status | _ENABLE_ | String | No | No | Yes | No | No |
Figure 3-4 shows the default User account attribute mappings.
Figure 3-4 Default Attribute Mappings for an SAP AC UME Account
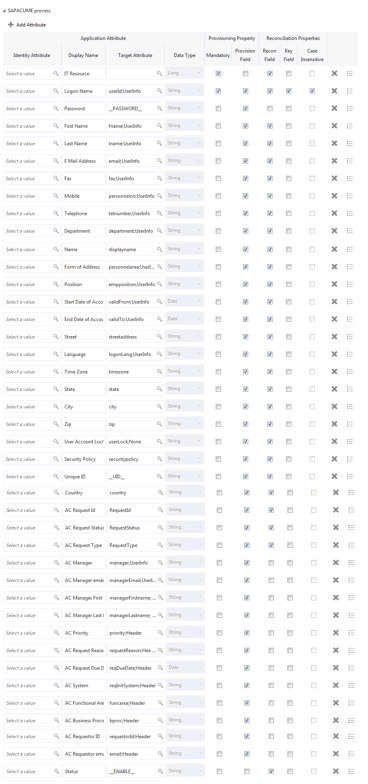
Description of "Figure 3-4 Default Attribute Mappings for an SAP AC UME Account"
Group Entitlement Attributes
Table 3-9 lists the group-specific attribute mappings between the process form fields in Oracle Identity Governance and SAP AC UME attributes. The table lists whether a given attribute is mandatory during provisioning. It also lists whether a given attribute is used during reconciliation and whether it is a matching key field for fetching records during reconciliation.
If required, you can edit these attribute mappings by adding new attributes or deleting existing attributes on the Schema page as described in Creating a Target Application of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-9 Default Attribute Mappings for a Group Entitlement
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|
|
Datasource |
String |
No |
No |
No |
No |
|
|
Group |
umegroup;itemnameReqLineItem |
String |
Yes |
Yes |
Yes |
No |
Figure 3-5 shows the default group entitlement mapping.
Figure 3-5 Default Attribute Mapping for a Group Entitlement
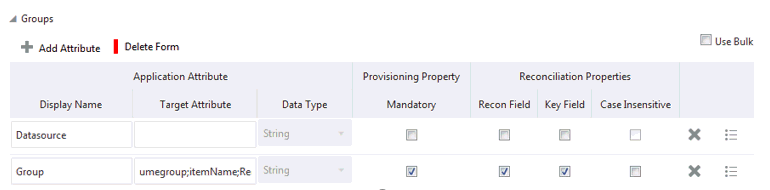
Description of "Figure 3-5 Default Attribute Mapping for a Group Entitlement"
Role Entitlement Attributes
Table 3-10 lists the role-specific attribute mappings between the process form fields in Oracle Identity Governance and SAP AC UME attributes. The table lists whether a given role is mandatory during provisioning. It also lists whether a given attribute is used during reconciliation and whether it is a matching key field for fetching records during reconciliation.
Table 3-10 Default Attribute Mappings for a Role Entitlement
| Display Name | Target Attribute | Data Type | Mandatory Provisioning Property? | Recon Field? | Key Field? | Case Insensitive? |
|---|---|---|---|---|---|---|
| Datasource | String | No | No | No | No | |
| role | umerole;itemnameReqLineItem | String | Yes | Yes | Yes | No |
Figure 3-6 Default Attribute Mappings for a Role Entitlement
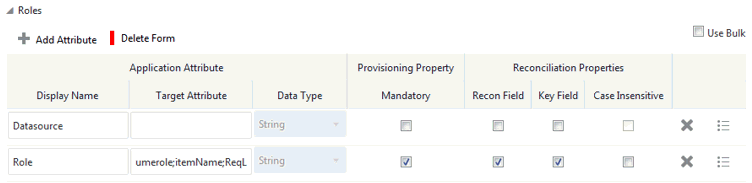
Description of "Figure 3-6 Default Attribute Mappings for a Role Entitlement"
3.4 Correlation Rules
Learn about the predefined rules, responses and situations for target and authoritative applications. The connector uses these rules and responses for performing reconciliation.
3.4.1 Rules, Situations, and Responses for the SAP UME Connector
The connector uses correlation rules to determine the identity to which Oracle Identity Governance must assign a resource.
Predefined Identity Correlation Rules
By default, the SAP UME connector provides a simple correlation rule when you create a Target application. The connector uses this correlation rule to compare the entries in Oracle Identity Governance repository and the target system repository, determine the difference between the two repositories, and apply the latest changes to Oracle Identity Governance.
Table 3-11 lists the default simple correlation rule for the SAP UME connector. If required, you can edit the default correlation rule or add new rules. You can create complex correlation rules also. For more information about adding or editing simple or complex correlation rules, see Updating Identity Correlation Rule of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-11 Predefined Identity Correlation Rule for the SAP UME Connector
| Target Attribute | Element Operator | Identity Attribute | Case Sensitive? |
|---|---|---|---|
|
__NAME__ |
Equals |
User Login |
No |
-
__NAME__ is a single-valued attribute on the target system that identifies the user account.
-
User Login is the field on the OIG User form.
Figure 3-7 shows the simple correlation rule for the SAP UME Connector.
Figure 3-7 Simple Correlation Rule for the SAP UME Connector
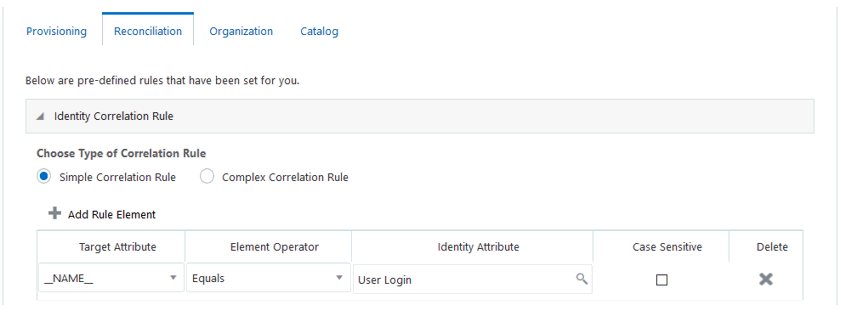
Description of "Figure 3-7 Simple Correlation Rule for the SAP UME Connector"
Predefined Situations and Responses
The SAP UME connector provides a default set of situations and responses when you create a Target application. These situations and responses specify the action that Oracle Identity Governance must take based on the result of a reconciliation event.
Table 3-12 lists the default situations and responses for the SAP UME connector. If required, you can edit these default situations and responses or add new ones. For more information about adding or editing situations and responses, see Updating Situations and Responses of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-12 Predefined Situations and Responses for the SAP UME Connector
| Situation | Response |
|---|---|
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Figure 3-8 Predefined Situations and Responses for the SAP UME Connector
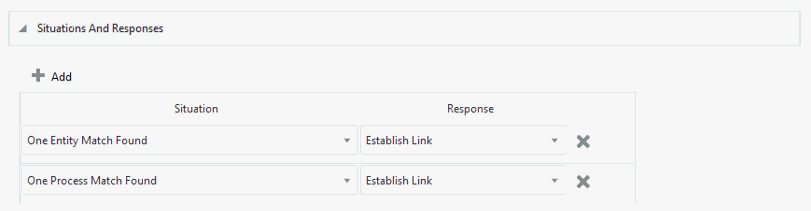
Description of "Figure 3-8 Predefined Situations and Responses for the SAP UME Connector"
3.4.2 Rules, Situations, and Responses for the SAP AC UME Connector
The connector uses correlation rules to determine the identity to which Oracle Identity Governance must assign a resource.
Predefined Identity Correlation Rules
By default, the SAP AC UME connector provides a simple correlation rule when you create a Target application. The connector uses this correlation rule to compare the entries in Oracle Identity Governance repository and the target system repository, determine the difference between the two repositories, and apply the latest changes to Oracle Identity Governance.
Table 3-13 lists the default simple correlation rule for the SAP AC UME connector. If required, you can edit the default correlation rule or add new rules. You can create complex correlation rules also. For more information about adding or editing simple or complex correlation rules, see Updating Identity Correlation Rule of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-13 Predefined Identity Correlation Rule for the SAP AC UME Connector
| Target Attribute | Element Operator | Identity Attribute | Case Sensitive? |
|---|---|---|---|
|
userId;UserInfo |
Equals |
User Login |
No |
-
userId;UserInfo is a single-valued attribute on the target system that identifies the user ID of the user account.
-
User Login is the field on the OIG User form.
Figure 3-9 shows the simple correlation rule for the SAP AC UME Connector.
Figure 3-9 Simple Correlation Rule for the SAP AC UME Connector
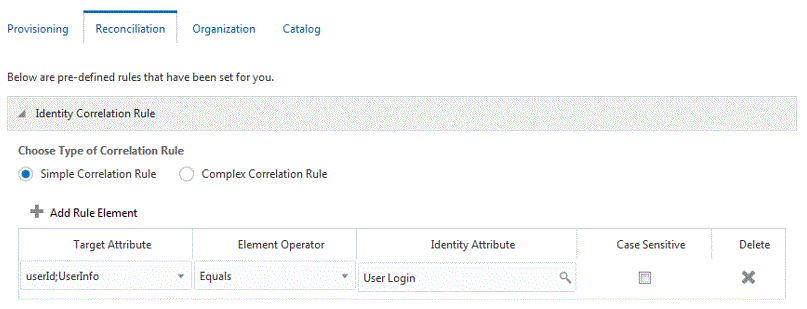
Description of "Figure 3-9 Simple Correlation Rule for the SAP AC UME Connector"
Predefined Situations and Responses
The SAP AC UME connector provides a default set of situations and responses when you create a Target application. These situations and responses specify the action that Oracle Identity Governance must take based on the result of a reconciliation event.
lists the default situations and responses for the SAP AC UME connector. If required, you can edit these default situations and responses or add new ones. For more information about adding or editing situations and responses, see Updating Situations and Responses of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Table 3-14 Predefined Situations and Responses for the SAP AC UME Connector
| Situation | Response |
|---|---|
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |
Figure 3-10 shows the situations and responses that the connector provides by default.
Figure 3-10 Predefined Situations and Responses for the SAP AC UME Connector

Description of "Figure 3-10 Predefined Situations and Responses for the SAP AC UME Connector"
3.5 Reconciliation Jobs
These are the reconciliation jobs that the connector creates after you create your application.
3.5.1 Reconciliation Jobs for the SAP UME Connector
These are the reconciliation jobs that are automatically created in Oracle Identity Governance after you create the application for your target system.
You can either use these predefined jobs or edit them to meet your requirements. Alternatively, you can create custom reconciliation jobs. For information about editing these predefined jobs or creating new ones, see Updating Reconciliation Jobs in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Note:
All of the jobs are prefixed with an application name when you create an application. For example, For SAPUMEAPP SAP UME Group Lookup Reconciliation where SAPUMEAPP is the application name.Full User Reconciliation Job
The SAP UME Target User Reconciliation job is used to fetch all user records from the target system.
Table 3-15 Parameters of the SAP UME Target User Reconciliation Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Sample value: |
|
Filter |
Enter the expression for filtering records that the scheduled job must reconcile. Sample value: Default value: For information about the filters expressions that you can create and use, see ICF Filter Syntax in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance. |
|
Object Type |
Enter the type of object you want to reconcile. Default value: |
User Delete Reconciliation Job
The SAP UME Target User Delete Reconciliation job is used to reconcile data about deleted user accounts from a target application.
Table 3-16 Parameters of the SAP UME Target User Delete Reconciliation Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. Sample value: |
| Object Type | Enter the type of object you want to reconcile.
Sample Value: |
Reconciliation Jobs for Entitlements
The following jobs are available for reconciling entitlements:
-
SAP UME Group Lookup Reconciliation: This reconciliation job is used to synchronize group lookup fields in Oracle Identity Governance with group-related data in the target system.
-
SAP UME Role Lookup Reconciliation: This reconciliation job is used to synchronize role lookup fields in Oracle Identity Governance with role-related data in the target system.
The parameters for both the reconciliation jobs are the same.
Table 3-17 Parameters of the Reconciliation Jobs for Entitlements of the SAP UME Connector
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. Default value: |
|
Lookup Name |
This parameter holds the name of the lookup definition that maps each lookup definition with the data source from which values must be fetched. Depending on the reconciliation job you are using, the default values are as follows:
|
|
Object Type |
Enter the type of object whose values must be synchronized. Depending on the scheduled job you are using, the default values are as follows:
|
|
Code Key Attribute |
Enter the name of the connector or target system attribute that is used to populate the Code Key column of the lookup definition (specified as the value of the Lookup Name attribute). Depending on the scheduled job you are using, the default values of Code Key Attribute is as follows:
|
|
Decode Attribute |
Enter the name of the connector or target system attribute that is used to populate the Decode Attribute column of the lookup definition (specified as the value of the Lookup Name attribute). Depending on the scheduled job you are using, the default values of Decode Attribute is as follows:
|
3.5.2 Reconciliation Jobs for the SAP AC UME Connector
These are the reconciliation jobs that are automatically created in Oracle Identity Governance after you create the application for the SAP AC UME target system.
You can either use these predefined jobs or edit them to meet your requirements. Alternatively, you can create custom reconciliation jobs. For information about editing these predefined jobs or creating new ones, see Updating Reconciliation Jobs in Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Governance.
Note:
All of the jobs are prefixed with an application name when you create an application. For example, For SAPACUMEAPP SAP AC UME BusinessProcess Lookup Reconciliation where SAPACUMEAPP is the application name.Full User Reconciliation Job
The SAP AC UME Target User Reconciliation job is used to fetch all user records from the target system.
Table 3-18 Parameters of the SAP AC UME Target User Reconciliation Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Sample value: |
|
Filter |
Enter the expression for filtering records that the scheduled job must reconcile. For information about the filters expressions that you can create and use, see ICF Filter Syntax in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance. |
|
Object Type |
Type of object you want to reconcile. Default value: |
User Delete Reconciliation Job
The SAP AC UME Target User Delete Reconciliation job is used to reconcile data about deleted user accounts from a target application.
Table 3-19 Parameters of the SAP AC UME Target User Delete Reconciliation Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. Sample value: |
|
Object Type |
Type of object you want to reconcile. Default value: |
|
SAP AC UME User Delete Recon |
You can use the SAP AC UME Target User Delete Reconciliation scheduled job to reconcile data about deleted users from the target system. During a reconciliation run, for each deleted user account on the target system, the SAP AC UME resource is revoked for the corresponding OIG User.
Default value: |
SAP AC UME Request Status Job
SAP AC UME Request Status Reconciliation job is used to reconcile request status from SAP BusinessObjects AC target system.
Table 3-20 Parameters of the SAP AC UME Request Status Reconciliation Job
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Do not modify this value. |
|
Object Type |
Type of object you want to reconcile. Default value: |
|
Custom Lookup Name |
Name of the lookup definition. Default value:
|
|
Resource Object Name |
Name of the resource object against which reconciliation runs must be performed. Default value: |
|
IT Resource Name |
Name of the IT resource instance that the connector must use to reconcile data. Default value: |
|
Scheduled Task Name |
Name of the scheduled task. Default value: |
Note:
To run the SAP AC UME Request Status reconciliation job, you must update Application Name and IT Resource Name parameters based on the name created while configuring the connector. For example, if the name of the connector is SAPACUME, then ensure to update the Application name asSAPACUME and the IT Resource Name as
SAPACUME.
Reconciliation Jobs for Entitlements
The following jobs are available for lookup field synchonizations. You can configure these scheduled jobs for lookup field synchronization and reconciliation:
-
SAP AC UME BusinessProcess Lookup Reconciliation
-
SAP AC UME FunctionalArea Lookup Reconciliation
-
SAP AC UME Group Lookup Reconciliation
-
SAP AC UME ItemProvAction Lookup Reconciliation
-
SAP AC UME Priority Lookup Reconciliation
-
SAP AC UME ReqInitSystem Lookup Reconciliation
-
SAP AC UME Request Type Lookup Reconciliation
-
SAP AC UME Role Lookup Reconciliation
The parameters for all the reconciliation jobs are the same.
Table 3-21 Parameters of the Reconciliation Jobs for Entitlements of the SAP AC UME Connector
| Parameter | Description |
|---|---|
|
Application Name |
Name of the application you created for your target system. This value is the same as the value that you provided for the Application Name field while creating your target application. Sample Value: |
|
Code Key Attribute ` |
Enter the name of the connector or target system attribute that is used to populate the Code Key column of the lookup definition (specified as the value of the Lookup Name attribute). Depending on the scheduled job you are using, the default values are as follows:
|
|
Decode Attribute |
Enter the name of the connector or target system attribute that is used to populate the Code Key column of the lookup definition (specified as the value of the Lookup Name attribute). Depending on the scheduled job you are using, the default values are as follows:
|
|
Lookup Name |
This parameter holds the name of the lookup definition that maps each lookup definition with the data source from which values must be fetched. Depending on the reconciliation job you are using, the default values are as follows:
|
|
Object Class |
Enter the class of object whose values must be synchronized. Depending on the scheduled job you are using, the default values are as follows:
|
|
Object Type |
Enter the type of object whose values must be synchronized. Depending on the scheduled job you are using, the default values are as follows:
|