19 Managing Users and Groups
The following topics describe how to configure these elements by using the command-line utilities and by using the Oracle Unified Directory Services Manager (OUDSM) interface:
For information about user passwords, see Managing Password Policies.
19.1 Managing User Accounts
User accounts are essentially user entries that you create, modify, or remove in your directory. You can manage user accounts and passwords by using command-line utilities.
Before you begin to manage user accounts, ensure that you have the appropriate password policies set up on the directory server. For more information, see Managing Password Policies.
The following topics describe how to manage user accounts and passwords by using the manage-account and ldappasswordmodify command-line utilities:
19.1.1 Changing Passwords
Directory administrators are often asked to create, reset, or remove passwords for other users. Changing passwords can be done by using ldappasswordmodify utility.
The ldappasswordmodify utility enables you to change or reset a user's password with the LDAP password modify extended operation. You can specify authorization IDs with the --authzid option by prefixing dn:, u:, or by specifying the full DN.
The following topics describe how to manage passwords:
19.1.1.1 Changing the Directory Manager's Password
To change the Directory Manager’s password, use the ldappasswordmodify command.
Use the ldappasswordmodify command, as shown in the following example:
$ ldappasswordmodify -h localhost -p 1389 \ --authzID "dn:cn=Directory Manager" \ --currentPassword password --newPassword mynewpassword The LDAP password modify operation was successful.
19.1.1.2 Resetting and Generating a New Password for a User
This example assumes that the user does not remember the existing password.
Use the ldappasswordmodify command, as shown in the following example:
$ ldappasswordmodify -h localhost -p 1389 -D "cn=Directory Manager" \ -j pwd-file --authzID u:jvedder The LDAP password modify operation was successful Generated Password: evx07npv
19.1.1.3 Changing a User's Password
This example assumes that the user remembers the existing password. The new password is passed to the server in a specified file.
Use the ldappasswordmodify command, as shown in the following example:
$ ldappasswordmodify -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \ --authzID uid=jvedder,ou=People,dc=example,dc=com \ --currentPassword password --newPasswordFile pwdFile The LDAP password modify operation was successful
19.1.2 Managing a User's Account Information
The manage-account command is used to display information about the user's account and any password policy that is applied to the user.
You can also use manage-account command to enable or disable a user's account. The manage-account command accesses the server over SSL through the administration port. For more information, see Managing Administration Traffic to the Server.
The following topics describe how to manage a user's account information:
19.1.2.1 Viewing a User's Account Information
Use manage-account command to view a User’s account information.
The manage-account command returns the DN of the password policy in effect on a user account, as well as the account status, and password and login related information.
19.1.2.2 Viewing Account Status Information
To assess whether an account is enabled or disabled, use the manage-account command.
Use the manage-account command with the get-account-is-disabled subcommand, as shown in the following example:
$ manage-account -D "cn=directory manager" -j pwd-file get-account-is-disabled \ --targetDN "uid=kvaughan,ou=People,dc=example,dc=com" Account Is Disabled: false
19.1.2.3 Disabling an Account
To disable an account, use manage-account command.
To disable an account, use the manage-account command with the set-account-is-disabled subcommand, as shown in the following example:
$ manage-account -h localhost -p 4444 -D "cn=directory manager" -j pwd-file -X \ set-account-is-disabled --operationValue true \ --targetDN "uid=kvaughan,ou=People,dc=example,dc=com" Account Is Disabled: true
19.1.2.4 Enabling an Account
To enable an account, use manage-account command.
To enable an account, use the manage-account command with the clear-account-is-disabled subcommand, as shown in the following example:
$ manage-account -D "cn=directory manager" -j pwd-file clear-account-is-disabled \ --targetDN "uid=kvaughan,ou=People,dc=example,dc=com" Account Is Disabled: false
19.1.3 Assigning Resource Limits on a User Account
Assigning resource limits on a user account is done by adding specific operational attributes to the user entry.
The following topics provide conceptual description of the resource limits and describe how to set those limits on a user account:
19.1.3.1 About Resource Limits on a User Account
You can control search operations on the server for each client account by assigning resource limits to the entry. Resource limits are assigned by adding specific operational attributes to the user entry. The directory server then enforces the limits based on the account that the client uses to bind to the directory.
The resource limits that you set on specific user accounts take precedence over the resource limits set in the server-wide configuration. For details of all the configurable resource limit properties, see "Global Configuration" in the Configuration Reference for Oracle Unified Directory.
The following limits can be set:
-
Look-through limit. Specifies the maximum number of entries examined for a search operation. Use the
ds-rlim-lookthrough-limitoperational attribute. -
Size limit. Specifies the maximum number of entries returned in response to a search operation. use the
ds-rlim-size-limitoperational attribute. -
Time limit. Specifies the maximum time spent processing a search operation. Use the
ds-rlim-time-limitoperational attribute.
Note:
The Directory Manager can use unlimited resources by default.
19.2 Configuring Root Users
Configuring root users is done by using the command-line utilities and OUDSM interface.
19.2.1 About Root Users
A root user is a special user whose account can bypass access controls and other restrictions that might be enforced for regular users.
You can define multiple root users, each with their own set of credentials, to control access at a fine-grained level. For example, you can assign privileges to a user who needs root access for a particular task, but does not need the full set of root user privileges. Oracle Unified Directory enables you to configure each root user to have his own strong authentication mechanism (such as GSSAPI SASL), his own specific password policy, and his own resource limits.
A set of global root user privileges is defined by default. These privileges apply to all configured root users, including the default root user, unless you modify the privilege in the root user entry. You can change the global root user privileges that are inherited by all root users.
During the setup process, a default root user with full administrative rights is created. The DN proposed by the setup for this root user is "cn=directory manager", so if you do not change the defaults proposed by the setup, a root user with the DN "cn=directory manager,cn=Root DNs,cn=config" is configured.
19.2.2 Configuring Root Users Using the Command-Line Utilities
You can view and edit the global root user properties by using command-line utilities.
To view and edit the global root user properties use the dsconfig command. To create and manage additional root users, you must use the ldapmodify command to add the user entries to the server configuration. The following sections describe how to manage root users by using the command line.
19.2.2.1 Changing the Global Root User Privileges
You can change the global Root user privileges by using dsconfig command.
To display the global root user privileges, run the following dsconfig command:
$ dsconfig -h localhost -p 4444 -D "cn=directory manager" -j pwd-file -X -n \
get-root-dn-prop
Property : Value(s)
----------------------------:--------------------------------------------------
default-root-privilege-name : backend-backup, backend-restore, bypass-acl,
: bypass-lockdown, cancel-request, config-read,
: config-write, disconnect-client, ldif-export,
: ldif-import, modify-acl, password-reset,
: privilege-change, server-restart,
: server-shutdown, subentry-write,
: unindexed-search, update-schema
To change the global root user privileges, run the following dsconfig command run the dsconfig set-root-dn-prop command with the --add or --remove option.
The following example removes the default privilege of root users to perform a backup or restore operation on the server.
$ dsconfig -h localhost -p 4444 -D "cn=directory manager" -j pwd-file -X -n \ set-root-dn-prop --remove default-root-privilege-name:backend-backup \ --remove default-root-privilege-name:backend-restore
For a complete list of the privileges and an explanation of each privilege, see Understanding Privilege Subsystem.
19.2.2.2 Creating a New Root User
You can create a new Root user using an entry in an LDIF file.
To create a new root user, create the user entry in an LDIF file, then use the ldapmodify command to add the entry to the cn=Root DNs,cn=config branch in the server configuration.
Note:
The cn=config suffix is an administrative suffix and, as such, must be accessed using the administration connector. For more information see Managing Administration Traffic to the Server.
Suppose, for example, that you want to give a particular user the right to backup and restore a database, but no other administrative privileges.
For a complete list of the privileges and an explanation of each privilege, see Understanding Privilege Subsystem.
19.2.2.3 Editing an Existing Root User Using ldapmodify Command
You can edit an existing root user using ldapmodify command.
To edit an existing root user, use the ldapmodify command to change the attributes of the user entry under the cn=Root DNs,cn=config branch in the server configuration.
Note:
The cn=config suffix is an administrative suffix and, as such, must be accessed using the administration connector. For more information see Managing Administration Traffic to the Server.
The following example removes the capability of the root user created in the previous example to perform a restore operation.
$ ldapmodify -h localhost -p 4444 -D "cn=directory manager" -j pwd-file \ --useSSL -X dn: cn=backup-admin,cn=root DNs,cn=config changetype: modify delete: ds-privilege-name ds-privilege-name: backend-restore
19.2.3 Configuring Root Users Using OUDSM
You can view and edit the default root user, and create and manage additional root users, by using the OUDSM interface.
The following topics describe how to configure root users by using OUDSM interface:
19.2.3.1 Configuring the Global Root User Privileges
A set of global root user privileges is defined by default. These privileges apply to all configured root users, unless you modify the privilege in the root user entry.
To modify the global root user privileges by using OUDSM:
19.2.3.2 Creating a New Root User
You can create a new Root user using OUDSM.
To create a new root user by using OUDSM:
-
Connect to the directory server from OUDSM, as described in Connecting to the Server Using OUDSM.
-
Select the Configuration tab.
-
From the Create menu, select Root User.
-
In the General Properties region, enter the following details:
-
In the Name field, type a name for the root user that you want to create.
-
In the Alternative Bind DNs region, click Add to specify one or more alternative DNs that can be used when this root users binds to the server.
For example, the alternative bind DN for the default root user is
"cn=Directory Manager". This allows you to bind as"cn=Directory Manager"instead of having to use"cn=Directory Manager,cn=Root DNs,cn=config", which is the actual entry DN.The alternative bind DN must be unique among all root users.
If you do not want to specify an alternative bind DN for the new root user, leave the table empty.
-
In the Password field, enter a password for the root user.
-
In the Confirm Password field, retype the password for the root user.
-
-
In the Privileges region, select the settings for the different privileges that must be applied to this new root user.
For each privilege, you can select one of the following:
-
Enable. The privilege is enabled for this root user. -
Disable. The privilege is disabled for this root user. -
Default Privilege (enable)orDefault Privilege (disable. The user inherits the default setting for this privilege, as defined in the global privilege configuration
-
-
Click Create.
The following confirmation message appears:
Root User created successfully.
19.3 Defining Groups
You can define groups using Oracle Unified Directory.Oracle Unified Directory supports groups, which are collections of entries that are manageable as a single object. Typically, directory administrators configure groups of printers, groups of software applications, groups of employees, and so forth.
Groups are especially useful when assigning special access privileges to a set of users. For example, you could configure a group of access managers and assign privileges that enables them to view confidential employee data, but restricts anyone else in the company from accessing that data.
The following group types are supported:
-
Static groups. For more information, see Defining Static Groups.
-
Dynamic groups. For more information, see Defining Dynamic Groups.
-
Virtual static groups. For more information, see Defining Virtual Static Groups.
This section also describes about nested groups. For more information, see Defining Nested Groups.
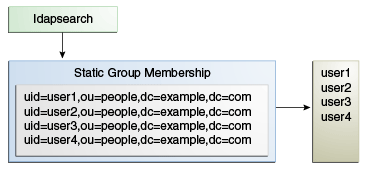
19.3.1 Defining Static Groups
A static group defines its membership by providing explicit sets of distinguished names (DNs) using the groupOfNames, groupOfUniqueNames, or groupOfEntries object class. Static groups are well supported by external clients and provide good performance.
This section contains the following topics:
19.3.1.1 Overview of Static Group
A static group is one whose entry contains a membership list of explicit DNs. Many clients support static groups, but static groups are difficult to manage as the number of members in a group increases in size.
For example, if you have a member entry that requires a DN change, then you must change that user's DN for each group to which that user belongs.
The directory server supports the following three types of static groups, divided according to the object class they use:
-
groupOfNames. You can define a static group by using thegroupOfNamesobject class and by explicitly specifying the member DNs using thememberattribute.Note:
RFC 4519 (
https://www.ietf.org/rfc/rfc4519.txt) requires that thememberattribute be mandatory within thegroupOfNamesobject class. This membership requirement has traditionally caused data management problems when an administrator attempted to delete the last member in the group. The directory server solves this problem by allowing thememberattribute to be optional. The optional membership requirement allows you to have an empty object class when you delete the last member of the group.dn: cn=Example Static Group 1,ou=Groups,dc=example,dc=com objectClass: top objectClass: groupOfNames member: uid=user1,ou=People,dc=example,dc=com member: uid=user2,ou=People,dc=example,dc=com cn: Example Static Group 1
-
groupOfUniqueNames. You can define a static group by using thegroupOfUniqueNamesobject class and by explicitly specifying the member DNs using theuniqueMemberattribute. ThegroupOfUniqueNamesobject class differs from thegroupOfNamesobject class in that you can enumerate the group's members by specifying a unique DN plus an optional identifier. The identifier ensures that the unique objects can be identified when adding, deleting, or renaming any object.For example, you could delete or move an employee (
cn=Tom Smith) and add a new employee who has the same name (cn=Tom Smith) to the directory. To distinguish the two, you must add a separate identifier by using a bit string. The following example shows two users with the same name, but the seconduniqueMemberhas an optional identifier.uniqueMember: uid=tsmith,ou=People,dc=example,dc=com uniqueMember: uid=tsmith,ou=People,dc=example,dc=com#'0111101'B
Note:
Few LDAP applications actually use the optional UID identifier.
RFC 4519 (
https://www.ietf.org/rfc/rfc4519.txt) requires that theuniqueMemberattribute be mandatory within thegroupOfUniqueNamesobject class. This membership requirement has historically caused data management problems when an administrator tried to delete the last member in the group. Oracle Unified Directory solves this problem by allowing theuniqueMemberattribute to be optional. The optional membership requirement allows you to have an empty object class when you delete the last member of the group.dn: cn=Example Static Group 2,ou=Groups,dc=example,dc=com objectClass: top objectClass: groupOfUniqueNames uniqueMember: uid=user1,ou=People,dc=example,dc=com uniqueMember: uid=user2,ou=People,dc=example,dc=com cn: Example Static Group 2
-
groupOfEntries. You can define a static group using thegroupOfEntriesobject class. Based on the original specifications (RFC 4519 (http://www.rfc-editor.org/rfc/rfc4519.txt) anddraft-findlay-ldap-groupofentries-00.txt, which expired in March, 2008), thegroupOfEntriesobject class differs from thegroupOfNamesandgroupOfUniqueNamesobject classes in that attributes are optional, which enables you to specify an empty object class without any members.Note:
Oracle Unified Directory supports the
groupOfEntriesdraft but also allows emptygroupOfNamesandgroupOfUniqueNamesobject classes. As a result, you can create empty groups of any type (groupOfEntries,groupOfNames, andgroupOfUniqueNames).dn: cn=Example Static Group 3,ou=Groups,dc=example,dc=com objectClass: top objectClass: groupOfEntries cn: Example Static Group 3
19.3.1.2 Creating a Static Group With groupOfNames
This procedure describes how to reate a static group with groupOfNames command.
To create a static group with groupOfNames as object class:
19.3.1.3 Creating a Static Group With groupOfUniqueNames
This procedure describes how to create a static group with groupOfUniqueNames as object class.
To create a static group with groupOfUniqueNames as object class:
19.3.1.4 Creating a Static Group With groupOfEntries
This procedure describes how to create a static group with groupOfEntries as object class.
To create a static group with groupOfEntries as object class:
19.3.1.5 Viewing All Members of a Static Group
Use the isMemberOf virtual attribute to search for a group. The attribute is added to the user entry at the start of the search and then removed after the search has finished. This functionality provides easy management of groups with fast read access.
Use the ldapsearch command with the virtual attribute isMemberOf.
This example searches for all users who are members of the group "Accounting Managers."
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \
-b dc=example,dc=com \
"(isMemberOf=cn=Accounting Managers,ou=Groups,dc=example,dc=com)"
dn: uid=scarter,ou=People,dc=example,dc=com
objectClass: person
objectClass: inetOrgPerson
objectClass: top
objectClass: organizationalPerson
ou: Accounting
ou: People
sn: Carter
facsimiletelephonenumber: +1 408 555 9751
roomnumber: 4612
userpassword: {SSHA}3KiJ51sx2Ug7DxZoq0vA9ZY6uaomevbJUBm7OA==
l: Sunnyvale
cn: Sam Carter
telephonenumber: +1 408 555 4798
givenname: Sam
uid: scarter
mail: scarter@example.com
dn: uid=tmorris,ou=People,dc=example,dc=com
objectClass: person
objectClass: inetOrgPerson
objectClass: top
objectClass: organizationalPerson
ou: Accounting
ou: People
sn: Morris
facsimiletelephonenumber: +1 408 555 8473
roomnumber: 4117
userpassword: {SSHA}bjFFHv6k1kbI6fZoCEfqmTj9XOZxWR06gxpKpQ==
l: Santa Clara
cn: Ted Morris
telephonenumber: +1 408 555 9187
givenname: Ted
uid: tmorris
mail: tmorris@example.com19.3.1.6 Viewing All Static Groups of Which a User Is a Member
This procedure describes how to view all the static groups of which a user is a member of.
Search using ldapsearch and the virtual attribute cn=IsMemberOf, as shown in the following example:
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \ -b dc=example,dc=com "(uid=scarter)" isMemberOf dn: uid=scarter,ou=People,dc=example,dc=com isMemberOf: cn=Accounting Managers,ou=groups,dc=example,dc=com
19.3.1.7 How to Find Whether a User is a Member of a Group
You can find out whether a user is a member of a group by using ldapsearch command.
Search using ldapsearch, as shown in the following example:
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \ -b "cn=Account Managers,ou=Groups,dc=example,dc=com" \ "(&(objectclass=groupOfUniqueNames) \ (uniquemember=uid=scarter,ou=People,dc=example,dc=com))" dn: cn=Accounting Managers,ou=groups,dc=example,dc=com objectClass: groupOfUniqueNames objectClass: top ou: groups description: People who can manage accounting entries cn: Accounting Managers uniquemember: uid=scarter, ou=People, dc=example,dc=com uniquemember: uid=tmorris, ou=People, dc=example,dc=com
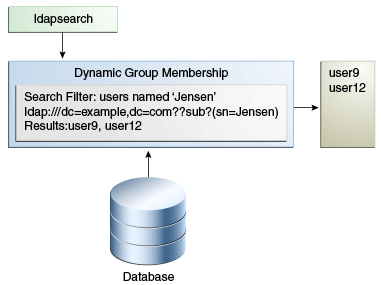
19.3.2 Defining Dynamic Groups
A dynamic group defines its membership using a set of search criteria in the form of an LDAP URL, using the groupOfUrls object class. Dynamic groups handle large numbers of members well (millions of entries). As entries are updated, all parent groups are updated automatically.
A disadvantage of dynamic groups is that not all clients support them. Performance also is adversely affected if you must query the whole list of entries. Thus, dynamic groups are best suited for groups with a very large number of entries or for clients that need to determine specific group membership for an entry.
This section describes the following topics:
19.3.2.1 Overview of Dynamic Group
A dynamic group is one whose membership, rather than being maintained explicitly in a list, is determined by search criteria using an LDAP URL.
For example, suppose that you want to send an email to all managers in the dc=example,dc=com naming context. To do this, you create a dynamic group in which you specify cn=Managers,ou=Groups,dc=example,dc=com. You further specify that you want only email addresses returned. When the email application queries the directory for that particular group, the directory server computes the membership dynamically and returns the corresponding list of email addresses.
Dynamic groups use the groupOfURLs object class and the memberURL attribute to define LDAP URLs with the criteria (search base, scope, and filter) to be used for determining members of the group. The mechanism for determining whether a user is a member of a dynamic group is a constant-time operation, so it is just as efficient for groups with millions of members as it is for a group with only a few members. However, care must be taken when specifying the search criteria as it can adversely affect performance if searching over a large set of data.
19.3.2.2 Creating a Dynamic Group
This procedure describes how to create a dynamic group.
To create a Dynamic Group:
19.3.2.3 Viewing All Members of a Dynamic Group
This procedure illustrates the use of the virtual attribute isMemberOf. Do not use this procedure for very large groups, because it adversely affects the directory server's performance
Search using ldapsearch and the virtual attribute isMemberOf.
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \
-b "dc=example,dc=com" \
"(isMemberOf=cn=cupertinoEmployees,ou=Groups,dc=example,dc=com)"
dn: uid=abergin,ou=People,dc=example,dc=com
objectClass: person
objectClass: inetOrgPerson
objectClass: top
objectClass: organizationalPerson
ou: Product Testing
ou: People
sn: Bergin
facsimiletelephonenumber: +1 408 555 7472
roomnumber: 3472
userpassword: {SSHA}YcDl0pHLxkd/ouW2jslAk1XaT5SiY4ium5qh8w==
l: Cupertino
cn: Andy Bergin
telephonenumber: +1 408 555 8585
givenname: Andy
uid: abergin
mail: abergin@example.com
...(more entries)...19.3.2.4 Viewing All Dynamic Groups of Which a User Is a Member
This procedure describes how to view all dynamic groups of which a user is a member, using ldapsearch command.
Search using ldapsearch and the virtual attribute isMemberOf.
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \ -b dc=example,dc=com "(uid=abergin)" isMemberOf dn: uid=abergin,ou=People,dc=example,dc=com isMemberOf: cn=QA Managers,ou=groups,dc=example,dc=com isMemberOf: cn=cupertinoEmployees,ou=Groups,dc=example,dc=com
19.3.2.5 How to Find Whether a User Is a Member of a Dynamic Group
Use ldapsearch command to find whether a user is a member of a dynamic group.
Search using ldapsearch and the virtual attribute isMemberOf, as shown below:
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \
-b dc=example,dc=com \
"(&(uid=abergin)(isMemberOf=cn=cupertinoEmployees,ou=Groups,dc=example,dc=com))"
dn: uid=abergin,ou=People,dc=example,dc=com
objectClass: person
objectClass: inetOrgPerson
objectClass: top
objectClass: organizationalPerson
ou: Product Testing
ou: People
sn: Bergin
facsimiletelephonenumber: +1 408 555 7472
roomnumber: 3472
userpassword: {SSHA}YcDl0pHLxkd/ouW2jslAk1XaT5SiY4ium5qh8w==
l: Cupertino
cn: Andy Bergin
telephonenumber: +1 408 555 8585
givenname: Andy
uid: abergin
mail: abergin@example.com19.3.3 Defining Virtual Static Groups
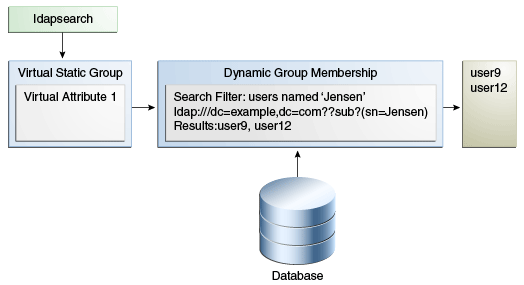
A virtual static group appears and behaves like a static group to external clients, except that each member is represented by a virtual attribute that defines its membership as needed from another dynamic group.
The following topics describe virtual static groups:
19.3.3.1 Overview of Virtual Static Group
A virtual static group allows access to dynamic groups by clients that can only support static groups.
In a virtual static group, each entry behaves like a static group entry by using virtual attributes. The virtual attributes are dynamically determined when invoked, and the operations that determine group membership are passed to another group, such as a dynamic group.
Virtual static groups should include either the groupOfNames or groupOfUniqueNames object class but should not include the member or uniqueMember attribute. Virtual static groups should also contain the ds-virtual-static-group auxiliary object class and the ds-target-group-dn attribute. The ds-target-group-dn attribute is used to reference the actual group to mirror as a virtual static group and is used in place of the member or uniquemember attribute. For example:
dn: cn=Example Virtual Static Group,ou=Groups,dc=example,dc=com objectClass: top objectClass: groupOfUniqueNames objectClass: ds-virtual-static-group cn: Example Virtual Static Group ds-target-group-dn: cn=Example Real Group,ou=Groups,dc=example,dc=com
Virtual static groups are most efficient when the application issues a search targeted at the membership attribute but does not actually retrieve the entire set of members. It is common for applications to use a filter such as the following to attempt to determine whether a user is a member of a given group:
(&(objectClass=groupOfUniqueNames)(uniqueMember=uid=john.doe,\ ou=People,dc=example,dc=com))
For applications that retrieve the set of members, virtual static groups might not be ideal because the process of constructing the entire member list can be expensive.
19.3.3.2 Creating a Virtual Static Group
This procedure describes how to create a virtual static group.
To create a Virtual Static Group:
19.3.3.3 Viewing All Members of a Virtual Static Group
Virtual static groups are best used in cases where the search is targeted at the membership attribute. This procedure is therefore not recommended but is included to show how to access the list.
This example uses the dynamic group, cupertinoEmployees that was created in the previous example.
Search using ldapsearch and the virtual attribute cn=virtualStatic.
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \
-b dc=example,dc=com "(isMemberOf=cn=virtualStatic,ou=Groups,dc=example,dc=com)"
dn: cn=virtualStatic,ou=Groups,dc=example,dc=com
objectClass: groupOfUniqueNames
objectClass: ds-virtual-static-group
objectClass: top
cn: Virtual Static
uniqueMember: uid=abergin,ou=People,dc=example,dc=com
ds-target-group-dn: cn=cupertinoEmployees,ou=Groups,dc=example,dc=com
ou: Product Testing
ou: People
sn: Bergin
facsimiletelephonenumber: +1 408 555 7472
roomnumber: 3472
userpassword: {SSHA}YcDl0pHLxkd/ouW2jslAk1XaT5SiY4ium5qh8w==
l: Cupertino
cn: Andy Bergin
telephonenumber: +1 408 555 8585
givenname: Andy
uid: abergin
mail: abergin@example.com
...(more entries)...19.3.3.4 Viewing All Virtual Static Groups of Which a User Is a Member
This procedure describes how to view all the virtual static groups of which a user is a member, using ldapsearch command.
Search using ldapsearch and the virtual attribute isMemberOf:
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \ -b dc=example,dc=com "(uid=abergin)" isMemberOf dn: uid=abergin,ou=People,dc=example,dc=com isMemberOf: cn=QA Managers,ou=groups,dc=example,dc=com isMemberOf: cn=cupertinoEmployees,ou=Groups,dc=example,dc=com isMemberOf: cn=virtualStatic,ou=Groups,dc=example,dc=com
19.3.3.5 How to Find Whether a User is a Member of a Virtual Static Group
This procedure describes how to find whether a user is a member of a virtual static group.
Search using ldapsearch and the uniqueMember attribute.
$ ldapsearch -h localhost -p 1389 -D "cn=Directory Manager" -j pwd-file \ -b "cn=virtualStatic,ou=Groups,dc=example,dc=com" \ "(&(objectclass=groupOfUniqueNames) \ (uniquemember=uid=abergin,ou=People,dc=example,dc=com))" dn: cn=virtualStatic,ou=Groups,dc=example,dc=com objectClass: groupOfUniqueNames objectClass: top objectClass: ds-virtual-static-group ou: Groups ds-target-group-dn: cn=cupertinoEmployees,ou=Groups,dc=example,dc=com cn: Virtual Static cn: virtualStatic
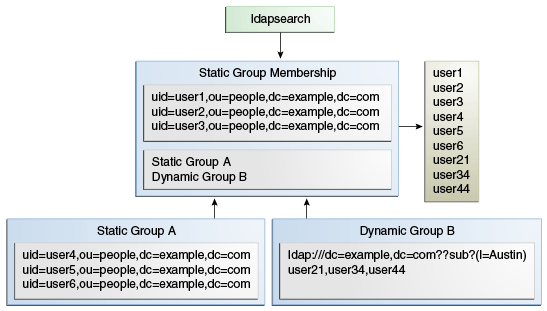
19.3.4 Defining Nested Groups
Groups can be nested, where one group is defined as a child group entry whose DN is listed within another group, its parent.
The following topics provide a conceptual description of nested group and the procedure how to create a nested group:
19.3.4.1 About Nested Group
The nesting of groups allows you to set up inherited group memberships when performance is not a priority.
Groups can be nested, where one group is defined as a child group entry whose DN is listed within another group, its parent. The nesting of groups allows you to set up inherited group memberships when performance is not a priority. You can add zero or more member attributes with their values set to the DNs of nested child groups, including both static and dynamic groups.
19.4 Maintaining Referential Integrity
Referential integrity is a database mechanism for ensuring that all references are properly maintained after delete, rename, or move operations. For example, if an entry is removed from the directory, the directory server also removes the entry from any groups of which the entry is listed as a member.
The referential integrity mechanism is configured as a plug-in the directory server and can be enabled using the dsconfig command. For more information, see Managing the Server Configuration Using dsconfig.
The following topics describe about referential integrity plug-in:
19.4.1 Overview of the Referential Integrity Plug-In
By default, the referential integrity plug-in is disabled. When you enable the plug-in by using dsconfig, it performs integrity updates on the member and uniquemember attributes after a delete, rename, or move operation.
Referential integrity plug-in can be configured to do the processing either in background or in foreground mode based on update-interval configuration parameter. See “Referential Integrity Plugin” in Configuration Reference for
Oracle Unified Directory for more information. By default, the value of update-interval is 0. If the update-interval value is 0, then the updates are made synchronously in the foreground. If update-interval value is set to > 0, then it runs in the background mode.
When referential integrity plug-in is configured to run in the background mode, if you delete, rename, or move a user or group entry in the directory, the operation is logged to the referential integrity log file, INSTANCE_DIR/OUD/logs/referint.
After a specified time, known as the update-interval, the server performs a search on the specified attributes and matches the results with the DNs of the deleted or modified entries recorded in the log. Then the server modifies the attributes based on the result of the match. The referint log is only updated when the value of update-interval is > 0. The DN log is removed after the update-interval time elapses and then the user DN is removed from other entries based on the referential integrity plug-in parameter config.
You can configure the following referential integrity plug-in properties to suit your requirements:
-
Enabled. Turn on the referential integrity plug-in.
-
plugin type. By default, the delete, rename, and move operations are set. You can change a plug-in type to only delete, for example.
-
Attribute type. By default, the attribute types are set to
member,uniquememberbut can be changed to some other attribute. If you use or define attributes containing DN values, you can use the referential integrity plug-in to monitor these attributes. -
Base-DN. By default, the scope is to use all public naming contexts but this can be changed to a specific context.
-
Log file. By default,
logs/referintis the log file. You can record the referential integrity updates in a different file. For example, if you want to record changes in a replicated environment, you can write to the changelog file on a replication server, so that it can be replicated to a consumer server. -
Update-interval. By default, the
update-intervalis set to 0 seconds, which will run referential integrity immediately after a delete, rename, or move operation. To minimize the impact of the updates on system performance, increase the amount of time between updates. Typical update intervals are as follows:-
0 seconds, update immediately
-
90 seconds (updates every 90 seconds)
-
3600 seconds (updates every hour)
-
10,800 seconds (updates every 3 hours)
-
28,800 seconds (updates every 8 hours)
-
86,400 seconds (updates once a day)
-
604,800 seconds (updates once a week)
-
19.4.2 Enabling the Referential Integrity Plug-In
To enable referential integrity by using dsconfig, set the enabled property of the plug-in to true.
This procedure describes how to enable the referential integrity plug-in:
as shown below:
$ dsconfig -h localhost -p 4444 -D "cn=directory manager" -j pwd-file -n \ set-plugin-prop --plugin-name "Referential Integrity" --set enabled:true
19.5 Simulating ODSEE Roles in an Oracle Unified Directory Server
You can configure Oracle Unified Directory to simulate Oracle Directory Server Enterprise Edition (ODSEE) roles to satisfy grouping mechanism.
19.5.1 About ODSEE Roles in an Oracle Unified Directory Server
Oracle Directory Server Enterprise Edition (ODSEE) includes a roles subsystem that is used to provide a specialized type of grouping mechanism. This capability is not included directly in Oracle Unified Directory, because it is based on nonstandard functionality, uses Netscape-proprietary schema elements, and is not widely used in LDAP-enabled applications.
However, Oracle Unified Directory does provide all of the functionality offered by ODSEE roles, and this functionality is available for use with standard grouping mechanisms. If you have an application that was specifically written to rely on the roles functionality available in ODSEE and cannot work with standard grouping mechanisms, you can configure Oracle Unified Directory to simulate ODSEE roles to satisfy such applications.
Note:
If your application needs to create and destroy role entries (for example, an entry containing one of the subordinates of the nsRoleDefinition object class), that functionality is currently not available in Oracle Unified Directory.
19.5.2 Determining Whether a User is a Member of a Role
If the application only needs to determine whether a user is a member of a given role, it should only need to look at the nsRole attribute in the target user's entry to determine whether the DN of the appropriate role is present. In this case, you can simulate role functionality by following the steps described in this section.
After completing these steps are completed, the nsRole virtual attribute appears as an operational attribute in user entries, and should include the DNs of all groups in which that user is a member.
Note:
The nsRole attribute is an operational attribute, and you must explicitly request that it returned in search results. You must also ensure that the authenticated user has permission to see that attribute.
-
Update the directory server to include the necessary schema for the ODSEE roles implementation.
This schema is provided in the LDIF file,
03-dsee-roles.ldif, as follows:# CDDL HEADER START # # The contents of this file are subject to the terms of the # Common Development and Distribution License, Version 1.0 only # (the "License"). You may not use this file except in compliance # with the License. # # You can obtain a copy of the license at # trunk/opends/resource/legal-notices/OpenDS.LICENSE # or https://OpenDS.dev.java.net/OpenDS.LICENSE. # See the License for the specific language governing permissions # and limitations under the License. # # When distributing Covered Code, include this CDDL HEADER in each # file and include the License file at # trunk/opends/resource/legal-notices/OpenDS.LICENSE. If applicable, # add the following below this CDDL HEADER, with the fields enclosed # by brackets "[]" replaced with your own identifying information: # Portions Copyright [yyyy] [name of copyright owner] # # CDDL HEADER END # # # This file contains schema definitions required to simulate DSEE role # functionality in OpenDS. dn: cn=schema objectClass: top objectClass: ldapSubentry objectClass: subschema attributeTypes: ( 2.16.840.1.113730.3.1.574 NAME 'nsRole' DESC 'Sun ONE defined attribute type' SYNTAX 1.3.6.1.4.1.1466.115.121.1.12 NO-USER-MODIFICATION USAGE directoryOperation X-ORIGIN 'Sun ONE Directory Server' ) attributeTypes: ( 2.16.840.1.113730.3.1.575 NAME 'nsRoleDN' DESC 'Sun ONE defined attribute type' SYNTAX 1.3.6.1.4.1.1466.115.121.1.12 USAGE directoryOperation X-ORIGIN 'Sun ONE Directory Server' )
-
Either copy the file into the
config/schemadirectory of the directory server implementation and restart the server, or -
Use the
add schema filetask to cause the server to load the schema file into a running server instance.
-
-
Create a static or dynamic group to define role membership.
Ensure that the group has an appropriate set of members.
-
Create a new instance of the
isMemberOfvirtual attribute to provide thensRolevirtual attribute.The
nsRoleattribute will include a list of the DNs of all groups in which the target user is a member. Use thedsconfigcommand to create the virtual attribute, as follows:$ dsconfig -h localhost -p 4444 -D "cn=directory manager" -j pwd-file -n \ create-virtual-attribute \ --type is-member-of --name nsRole --set attribute-type:nsRole --set enabled:true
19.5.3 Altering Membership Using the nsRoleDN Attribute
If the application you are using expects to be able to alter membership by placing the name of the corresponding role in the nsRoleDN virtual attribute in a user's entry.
After these steps are completed, any user entry that contains an nsRoleDN value of "cn=Test Role,ou=Roles,dc=example,dc=com" also has that DN present in the nsRole operational attribute.