5 Integrating WebLogic Cluster and Helidon Applications for Single Sign-On on OCI Using IDCS
The Oracle WebLogic Server (WebLogic Server) and
Helidon integration enables you to use the single sign-on (SSO) authentication mechanism
for applications deployed on WebLogic Server and Helidon by using OpenID Connect (OIDC)
with Oracle Identity Cloud Service (IDCS) in a Kubernetes environment. Using
SSO between WebLogic Server applications and Helidon microservices simplifies security
within a modernized application by sharing authentication while ensuring secure services.
You can implement SSO in different ways. A common approach is to use a token-based
authentication protocol such as OAuth or OIDC.
The WebLogic Server and Helidon integration in a Kubernetes cluster
enables SSO authentication to:
- Access the IDCS configured client application deployed in the WebLogic cluster.
- Access the Helidon REST endpoints configured with IDCS.
- Access the WebLogic Server application endpoints from the Helidon REST endpoints.
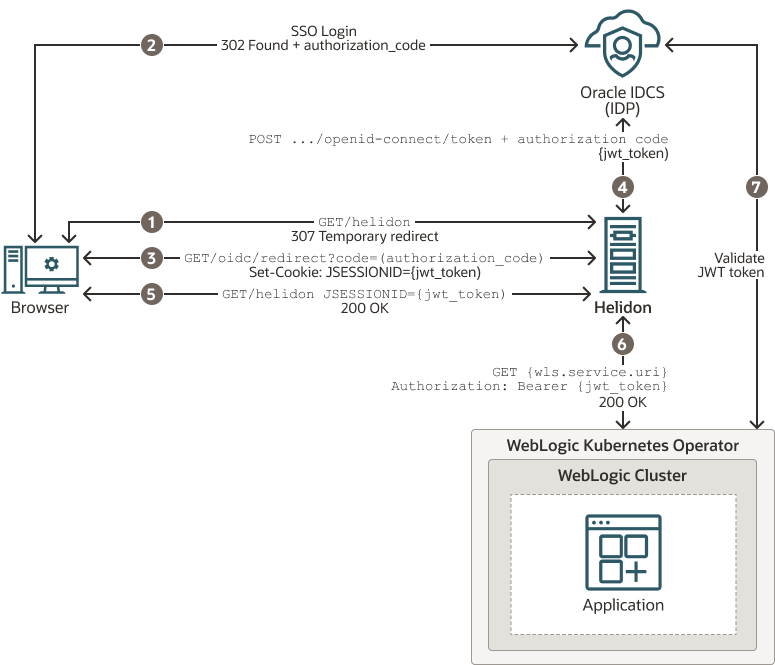
The following graphic illustrates the integration between WebLogic Server and Helidon for SSO using IDCS in an Oracle Cloud Infrastructure (OCI) environment:
Figure 5-1 WebLogic Cluster and Helidon Integration for SSO
The description of the steps in the illustration:
- The client uses a browser to call the protected Helidon resource without bearer token and gets redirected to the IDCS SSO login page.
- The client is redirected back to the Helidon application with an authorization code after a successful sign-in on the login page.
- When Helidon receives the authorization code, the JWT token is requested from IDCS, returned and saved as a JSESSIONID cookie.
- The JWT token is requested with a new authorization code, client id, and client secret.
- The last redirect leads back to the originally called resource, Helidon; this time with a valid bearer token in JSESSIONID.
- The bearer token is propagated to the client call for the WebLogic Server application resource.
- The WebLogic Server application resource is also secured with OIDC and validates the token against IDCS.
This chapter includes the following topics:
- Prerequisites
The prerequisites are based on WebLogic Server and Helidon integration in a Kubernetes cluster. The list may vary if you use any other supported platforms. - Setting Up the WebLogic Cluster Integration with Helidon for Single Sign-On
To facilitate the integration between WebLogic cluster and Helidon, WebLogic Server is deployed using the WebLogic Server Kubernetes Operator (Operator), in a Kubernetes cluster. The Helidon container is also deployed within the same Kubernetes cluster.
Prerequisites
The prerequisites are based on WebLogic Server
and Helidon integration in a Kubernetes cluster. The list may vary if you use any other
supported platforms. See Preparing the Kubernetes Cluster for WebLogic Server and Helidon Integration.
Ensure that you have the following:
- A local machine with
kubectlsetup to access the Kubernetes cluster. For more information about this setup, see Set Up the kubeconfig File for the Cluster and Verify kubectl and Kubernetes Dashboard Access to the Cluster in the Create a Cluster with Oracle Cloud Infrastructure Container Engine for Kubernetes Tutorial. - A WebLogic Kubernetes Operator (Operator) setup. See Operator Quick Start.
- An OCI load balancer with a public IP and
the load balancer rules applied according to the WebLogic Server and Helidon application
URL pattern. The following example shows the application of
rules:
--- apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: cquotes namespace: sample-domain1-ns spec: routes: - kind: Rule match: PathPrefix(`/<WLS application url>) services: - kind: Service name: sample-domain1-cluster-cluster-1 port: 8001 sticky: cookie: httpOnly: true name: cookie secure: false sameSite: none --- apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: helidon-quickstart-mp namespace: default spec: routes: - kind: Rule match: PathPrefix(`/<helidon rest url>`) services: - kind: Service name: helidon-quickstart-mp port: 8080 --- apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: helidon-oidc namespace: default spec: routes: - kind: Rule match: PathPrefix(`/oidc`) services: - kind: Service name: helidon-quickstart-mp port: 8080 - Access to IDCS with privileges to register applications. For instructions to create a user, see Create User Accounts in Administering Oracle Identity Cloud Service.
- Supported JDK (for example JDK 8 or later) and Maven (if required) to build the WebLogic cluster client applications.
- For deploying Helidon, see:
- A basic understanding of OpenID Connect (OIDC). See OpenID.
Setting Up the WebLogic Cluster Integration with Helidon for Single Sign-On
To facilitate the integration between WebLogic
cluster and Helidon, WebLogic Server is deployed using the WebLogic Server Kubernetes
Operator (Operator), in a Kubernetes cluster. The Helidon container is also deployed
within the same Kubernetes cluster. The default OCI load balancer with a
public IP is used to access the WebLogic Server Administration Console, the client
applications (deployed in the WebLogic cluster), and the Helidon REST endpoints (exposed by
the Helidon microservice application). The Helidon microservice application communicates
with the WebLogic cluster applications through the REST endpoints that are integrated with
Oracle Identity Cloud Service for authentication and authorization using SSO.
To set up the integration: