The software described in this documentation is either in Extended Support or Sustaining Support. See https://www.oracle.com/us/support/library/enterprise-linux-support-policies-069172.pdf for more information.
Oracle recommends that you upgrade the software described by this documentation as soon as possible.
This section describes recommended architectures for deploying Oracle products with secure Internet access.
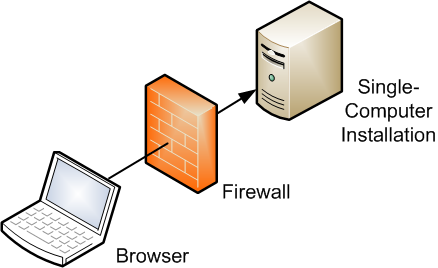
Figure 1.1, “Simple Firewall Deployment Configuration” shows a simple deployment architecture.
This single-computer deployment may be cost effective for small organizations. However, it cannot provide high availability because all components are stored on the same computer.
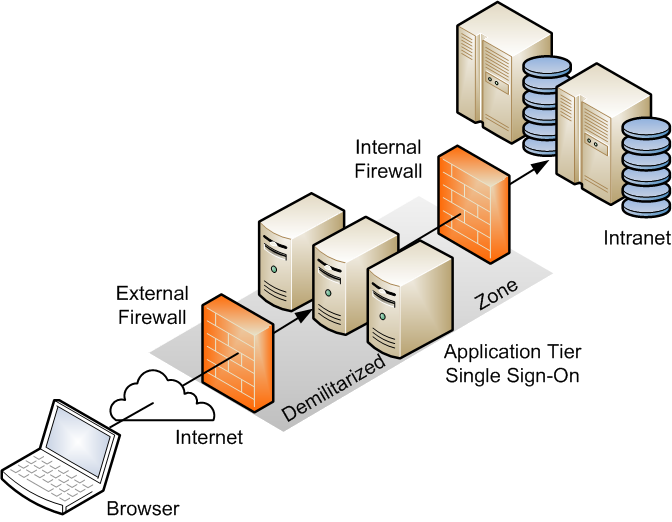
Figure 1.2, “DMZ Deployment Configuration” shows the recommended configuration, which uses the well-known and generally accepted Internet-Firewall-DMZ-Firewall-Intranet architecture.
A demilitarized zone (DMZ) refers to a server that is isolated by firewalls from both the Internet and the intranet, and which acts a buffer between them. The firewalls that separate DMZ zones provide two essential functions:
Block any traffic types that are not permitted.
Provide intrusion containment in the event that successful intrusions take over processes or processors.