Use AWS Endpoint Service to Securely Connect Applications to Oracle Autonomous Database
Applications that are deployed on AWS can leverage all the benefits of Oracle Autonomous Database running in Oracle Cloud Infrastructure (OCI) by deploying a multicloud, split-stack architecture.
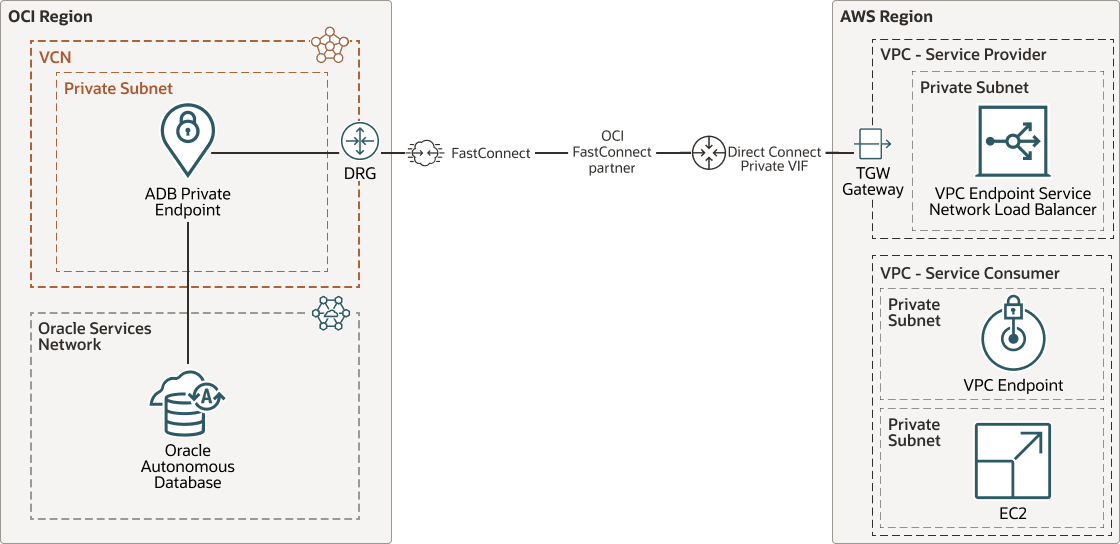
This reference architecture shows how to create an AWS endpoint service for an Autonomous Database running in OCI, and how AWS endpoints permit sharing the Autonomous Database securely within AWS.
Architecture
The multicloud topology in this reference architecture has Oracle Autonomous Database with a private endpoint in an Oracle Cloud Infrastructure (OCI) region serving an Amazon Web Services (AWS) region.
By using AWS endpoint service, applications hosted in AWS need only connect to the endpoint. The network load balancer behind the AWS endpoint service is responsible for reaching the private endpoint of the Autonomous Database hosted on OCI.
This architecture represents a simplification for both routing and for the domain name system (DNS). The AWS endpoint service is responsible for connecting privately to the endpoint while providing a valid domain for resolving the Autonomous Database private endpoint IP.
- Use Oracle Cloud Infrastructure FastConnect connected to AWS DirectConnect by using an OCI FastConnect partner when workloads require a high-bandwidth and low-latency private connection between the two clouds.
- Use a site-to-site VPN over internet when workloads don't require low latency and high bandwidth.
The following diagram illustrates this reference architecture.
adb-aws-endpoint-arch-oracle.zip
The architecture has the following Oracle components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Autonomous Database
Oracle Cloud Infrastructure Autonomous Database is a fully managed, preconfigured database environments that you can use for transaction processing and data warehousing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating the database, as well as backing up, patching, upgrading, and tuning the database.
The architecture has the following AWS components:
- Virtual private cloud (VPC)
A VPC is a virtual network that you create in an AWS region.
- Private link
Your own private link-powered services are also known as endpoint services
AWS PrivateLink is a highly available, scalable technology that enables you to privately connect your VPC to services as if they were in your VPC. You do not need to use an internet gateway, a NAT device, a public IP address, an AWS Direct Connect connection, or an AWS Site-to-Site VPN connection to allow communication with the service from your private subnets. You control the specific API endpoints, sites, and services that are reachable from your VPC.
- Route 53
Amazon Route 53 is a highly available and scalable Domain Name System (DNS) web service. Route 53 connects user requests to internet applications running on AWS or on-premises.
Recommendations
- Dedicated VPC acting as service provider
Create a dedicated VPC for hosting the Network Load Balancer and AWS endpoint service for Oracle Autonomous Database.
- Endpoint service acceptance settings
Configure the AWS endpoint service for Autonomous Database for requiring acceptance. This will permit control over which consumer VPC the endpoint is deployed.
- Endpoint security groups
Configure the endpoint security group following a deny all security posture and allow only the required connections.
- High availability
The architecture shows an AWS endpoint in a single Availability Zone. In a production deployment, it is recommended to configure endpoints in more than one Availability Zone.
- Performance
Select OCI and AWS regions aiming for the lowest latency possible. When connecting OCI and AWS, use a dedicated connection based on OCI FastConnect and AWS DirectConnect.
Considerations
Consider the following factors when deploying this reference architecture.
- Performance
Besides latency, another important factor that affects performance is the throughput available between components. For OCI FastConnect, AWS Direct Connect, and connectivity provider, select the sizes that cover the anticipated need.
- Cost
The total cost of deploying this architecture depends on the cost of the following resources:
- AWS
- AWS Endpoint
- AWS Transit Gateway
- Direct Connect
- Egress data transfer
- Oracle Cloud Infrastructure
- FastConnect ports
- Autonomous Database
- Connectivity partner
- AWS
Deploy
To share an Autonomous Database with private endpoint within an AWS region perform the following high-level steps.
The Explore More section provides links to supporting documentation for some of the steps.
- Deploy an Autonomous Database with Private Endpoint in an OCI region.
- Create a Network Load Balancer in AWS.
- Create a Network Load Balancer.
- Create a listener to TCP 1522.
- Create a Target Group with target type
IP addresses. - Register the Autonomous Database Private Endpoint as a target.
- Create an endpoint service in AWS.
- Create a service powered by AWS PrivateLink.
- Create an endpoint service by selecting the Network Load Balancer created in the previous step.
- Create the endpoint.
- Create the endpoint by selecting Other endpoint services and providing the Service name of the Autonomous Database endpoint service.
- Select the VPC where the endpoint will be created.
- Provide a custom domain name (optional).
- Create a Route 53 Private Hosted Zone for the custom zone.
- Associate the Hosted Zone with the endpoint VPC.
- Create an A-type record by selecting alias and selecting Autonomous Database VPC Endpoint.
Explore More
Review these additional resources to learn more about related architectures and about the features of this reference architecture.