About Network Connectivity Options for Integrating Oracle Utilities Cloud Services with External Applications
In order to integrate Oracle Utilities Cloud Services with an application hosted externally—either in your data center or in a third party data center—you need to understand the networking, authentication and protocol requirements for outbound and inbound communication from and to Oracle Utilities Cloud Services.
Note:
You must have thorough understanding of general networking concepts along with appropriate Oracle Cloud Infrastructure (OCI) certification or equivalent experience, to analyse this playbook, plan, and set up the required networking for integration with Oracle Utilities Cloud Services.Architecture
You can select any of three architectural options for integrating Oracle Utilities Cloud services with an application hosted in your data center or in a third party data center.
Architecture 1: Integrating an external application with Oracle Utilities Cloud services through public (internet) web service APIs

Description of the illustration pub-inet-opt.png
In its simplest form integration between application’s hosted in your private/corporate network and Oracle Utilities Cloud services can be achieved over the public internet. The REST APIs on the Oracle Utilities Cloud services are exposed securely to the public internet, so if an on-premise application needs to access the REST APIs, it can do so, as long as the application has access to the public internet. Similarly, Oracle Utilities Cloud services can access web service end points that are exposed to the public internet (public IP) i.e., if the on-premise application’s web service end points are exposed to the public internet, then these can be consumed by Oracle Utilities Cloud services. A firewall in your corporate network may be configured to expose any application’s private end points to the public internet. Although this forms the simplest possible communication channel, transiting over the public internet requires close consideration of the security, availability and reliability that the public internet can provide.
Architecture 2. Integrating an external application with Oracle Utilities Cloud services through VPN Connect for private webservice APIs
Forward Flow—Set up outbound communication:
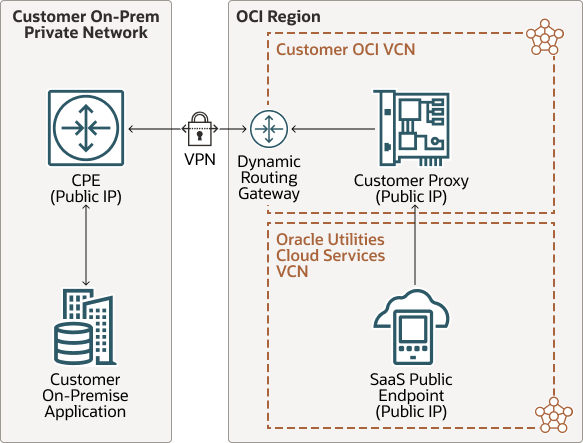
Description of the illustration vpn-connect-forward.png
Reverse Flow:
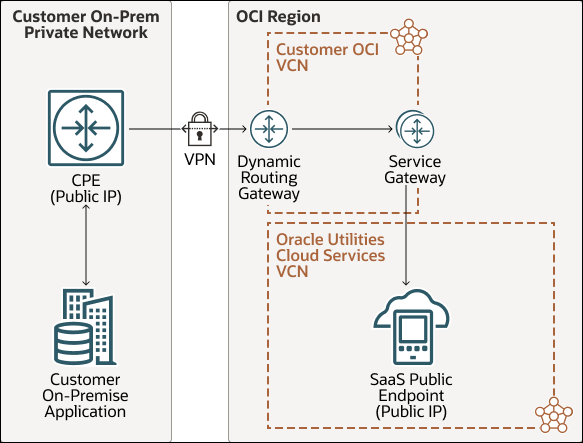
Description of the illustration vpn-connect-reverse.png
In this architecture, the external application makes private webservice API calls through the public internet, protected by an extended VPN, which creates a secured connection between your corporate private network and your VCN on Oracle Cloud Infrastructure (OCI). Within OCI networking, communication between Oracle Utilities Cloud services’ VCN (Virtual Cloud Network) and your VCN uses the service gateway. VPN Connect requires setting up of CPE (Customer Premise Equipment), which interfaces with VPN DRG (Dynamic Routing Gateway) creating a IPSEC Encryption Tunnel over the internet, securing all information flowing through the tunnel. Authentication is provided by Oracle Identity Cloud Service.
In turn, the Oracle Utilities Cloud service makes webservice calls to the external application by using Oracle Utilities Cloud service supported authentication methods such as basic authentication/OAuth client credentials, through the VPN. Note that Oracle Utilities Cloud services can make API calls only to public IP addresses, if the external APIs are private, you need the appropriate set up to ensure that the external APIs have public IPs; for example: a reverse/customer proxy mentioned in the preceding architecture diagram to expose your private API end points through public IP. The external application posts data to OCI object storage by using REST APIs.
If your external application’s digital certificates are not issued by a certification authority, you can use a single reverse proxy, with signed certificate, to proxy for multiple applications in your data center. You can set up the reverse proxy described in the preceding example either in your data center or within your VCN in OCI.
Architecture 3. Integrating an external application with Oracle Utilities Cloud services through FastConnect for private webservice APIs
Forward Flow—Set up outbound communication:
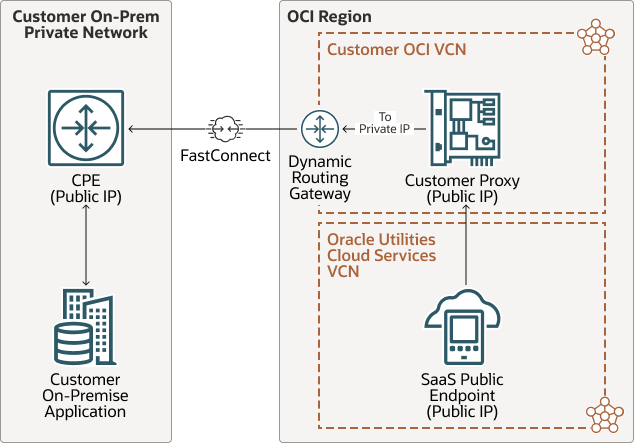
Description of the illustration fastconnect-opt-forward.png
Reverse Flow:
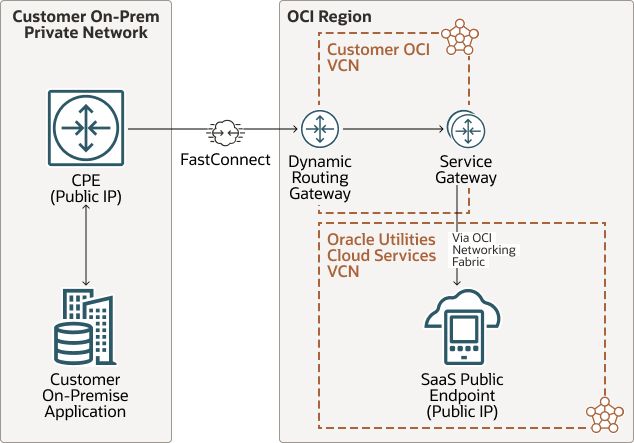
Description of the illustration fastconnect-reverse.png
Alternately, another private routing option of FastConnect may also be used to connect your private/corporate network with OCI network(OCI VCN). FastConnect provides an entry point in to OCI for a dedicated private line between your data center and the OCI to enable high bandwidth data transfer over a highly secured channel. FastConnect communication requires FastConnect DRG to be setup on your OCI VCN along with a dedicated line that can connect the CPE with the FastConnect DRG to be set up, which in turn interfaces with the service gateway or the proxy (if available) within you VCN, depending on the direction of the communication. Within OCI networking, communication between Oracle Utilities Cloud Service’s VCN (Virtual Cloud Network) and your VCN uses the service gateway or your proxy depending on the direction of the API Call.
Note:
For forward flow (in the applicable scenarios), you can route the communication from Oracle Utilities Cloud Service VCN to the Customer Proxy hosted in Customer’s OCI VCN with public IP through the internet.Understand Networking Scenarios
This playbook describes four different networking scenarios, based on the above three networking architectures, any of which you might consider when integrating Oracle Utilities Cloud Services with an application hosted externally. To assist you in choosing the appropriate network topology, here we provide a description and pro/con discussion of each scenario.
Use the following table and associated topics to help you decide which networking option best fits your needs.
| Scenario | Description | Security | High Availability | Throughput | Cost |
| 1 | Connectivity over public internet without VPN or FastConnect | TLS only | Relies on connectivity over the internet | Limited | Low setup cost; Low setup cost; OCI data transfer charges may apply |
| 2 | Connectivity over public internet with VPN Connect and without FastConnect | IPSec, Encrypted | Limited | Typically <250Mbps | Low setup cost; Low setup cost; OCI data transfer charges may apply |
| 3 | Connectivity over FastConnect without VPN (VPN may reduce the throughput) | TLS over dedicated private line – Not Encrypted | Redundancy supported - Refer to High Redundancy Best Practices | Port speeds in 1 Gbps, 10 Gbps or 100 Gbps increments | Prominent setup cost; OCI data transfer charges do not apply |
| 4 | Connectivity over public internet with VPN (as a fallback) and FastConnect | Depending on the path used for communication (Fast Connect -Not Encrypted; VPN -Encrypted) | Redundancy by Design - Refer to Redundancy Best Practices | Depending on the path used for data transfer | Prominent setup cost; OCI data transfer fees may apply, depending on the path of communication |
Although connecting to Oracle Utilities Cloud Service via the internet is the cheaper option to setup, due to its limited security and availability, when transferring secured information as part of product integrations, it might also be the riskier option. Also, the OCI data transfer charges should be taken into consideration when evaluating the networking options.. To ensure utmost security and availability, the FastConnect option with a redundant setup of VPN over public internet may be preferred.
The following topics discuss these options in greater detail.
Scenario 1: Connect Over Public Internet Without VPN or FastConnect
You can consider connecting over the public Internet without a VPN or FastConnect when the integration with on-premises application doesn’t need high bandwidth or high levels of security.
Note these considerations:
| Pre-requisites (To be done by the customer) |
|
| Working |
|
| Pros | Simple setup, lower cost. |
| Cons |
|
Considerations for Setting Up Scenario 1
Scenario 1 involves direct connectivity over public internet and is the simplest scenario to set up.
- Forward flow: Configure the firewall of the external data centre to allow
traffic from Oracle Utilities Cloud Services, if not already done.
Create a support ticket for adding the external DNS address to the allow list of Oracle Utilities Cloud Service so that communication going out of Oracle Utilities Cloud Services is allowed. See “Understand Allow List” elsewhere in this playbook for more information on the allow-list options.
- Reverse flow: Configure and use the public IP of the application/applications in the external data centre to route traffic from Oracle Utilities Cloud Services. The IP address can be used as the outbound address by configuring in the corresponding Oracle Utilities Cloud Service.
See “Understand Available Integration Channels” elsewhere in this playbook for more information on supported channels and for additional requirements for integration with external systems.
Scenario 2: Connect Over Public Internet With VPN but Without FastConnect
Connect over the public internet with a VPN Connect but without FastConnect when the integration with on-premises applications doesn’t need high bandwidth but needs higher levels of security, with private APIs for integration. Because FastConnect involves additional cost, you can use this scenario when cost is a factor but network throughput isn’t.
Note these considerations:
| Pre-requisite setup (To be planned and setup by the customer) |
|
| Working |
|
| Pros |
|
| Cons |
|
Considerations for Setting Up Scenario 2
Scenario 2 involves extending the private network of the external data centre into OCI by using VPN Connect. VPN Connect lets you create a secured IPSec tunnel through the public internet between the external data center and your VCN on OCI.
- Forward flow: Set up outbound communication from Oracle
Utilities Cloud Services to external applications:
- Set up the site-to-site VPN. Refer to “When to Use VPN
Connect” and subsequent sections of this playbook to understand and
setup VPN between external data centre and your OCI VCN. Oracle
Utilities Cloud services outbound communication can be done only to APIs
with public IP addresses. To enable outbound communication from Oracle
Utilities Cloud Services to external applications through the VPN, an
appropriate setup and configuration needs to be done so that the private
IP addresses of external applications are proxied through public IP
addresses, to which Oracle Utilities Cloud Services can send
communication as part of the forward flow.
There may be several ways in which this can be done. Networking expert in your IT team should be able to list and evaluate possible options to proxy the private IP addresses of the external application through public IP addresses and choose the best possible solution.
An example of one such option is the use of reverse proxy mentioned in the architecture diagram.
Example setup for reverse proxy:
A reverse proxy could be setup to proxy the external APIs that are private, using public IP addresses.
- Set up the Customer proxy (Reverse proxy). The reverse proxy can be setup to proxy for the private end points of the external applications that are being integrated using the option of extending external data centre’s private network through VPN Connect. The reverse proxy could be configured so it proxies for the private end points using public IP addresses. The outbound communication from Oracle Utilities Cloud Services to the external applications can be routed through this reverse proxy and then through the IP Sec tunnel setup using VPN Connect.
- You can set up the proxy by using a separately provisioned OCI VM in your OCI VCN.
- You can install and configure an appropriate reverse proxy software on this VM so it can accept requests coming in from Oracle Utilities Cloud Services and then forward these to the external applications. The reverse proxy should be set up with a public IP address, so Oracle Utilities Cloud Service can send outbound communication to the reverse proxy.
- Configure Oracle Utilities Cloud Service’s outbound communication with appropriate details so it can send outbound messages to the configured/setup APIs.
- Create a support ticket for adding the external DNS address to the allow list of Oracle Utilities Cloud Service so that communication going out of Oracle Utilities Cloud Services is allowed. Refer to “Understand Allow List” section of this playbook for more information on allow-list options.
- Set up the site-to-site VPN. Refer to “When to Use VPN
Connect” and subsequent sections of this playbook to understand and
setup VPN between external data centre and your OCI VCN. Oracle
Utilities Cloud services outbound communication can be done only to APIs
with public IP addresses. To enable outbound communication from Oracle
Utilities Cloud Services to external applications through the VPN, an
appropriate setup and configuration needs to be done so that the private
IP addresses of external applications are proxied through public IP
addresses, to which Oracle Utilities Cloud Services can send
communication as part of the forward flow.
- Reverse flow: Set up inbound communication to Oracle Utilities Cloud
Services from external applications:
- Set up inbound communication by using the same site-site VPN setup that you did for the preceding forward flow.
- Set up the Service Gateway. Service Gateway is one of the available gateways in OCI VCN that allows for traffic to be routed between two VCNs within OCI. See “Access to Oracle Services: Service Gateway”, elsewhere in this playbook to understand and configure service gateway. The inbound traffic will be routed through the VPN between the external data center and your VCN on OCI, and then be routed through the service gateway to Oracle Utilities Cloud Services.
- Create a support ticket for adding VCN OCID to the allow list of Oracle Utilities Cloud Service so that communication coming into Oracle Utilities Cloud Services from the VCN’s service gateway is allowed.
- “Understand Allow List” for more information on allow-list options.
- “Understand Reverse Proxy” for more information on reverse proxy example.
- “Understand Available Integration Channels” to understand the supported channels and additional requirements for integration to external systems.
Scenario 3: Connect Over FastConnect Without VPN
Connect over FastConnect without a VPN when the integration with an on-premises application requires high bandwidth; for example, when you need to transfer large files.
Note these considerations:
| Prerequisites setup (to be planned and setup by the customer)s |
|
| Working |
|
| Pros | High bandwidth; secure line. |
| Cons | Cost of setting up the FastConnect private line and the cost of setting up the intermediary (such as a proxy). |
Considerations for Setting Up Scenario 3
Scenario 3 requires setting up a dedicated private line between the external data center and OCI.
- Set up a FastConnect private line between an external data center and OCI. See “Understand OCI FastConnect” elsewhere in this playbook to understand and set up FastConnect.
- Follow the instructions in Scenario 2 to complete the rest of the
setup/configuration for this scenario.
Note:
You need to familiarize yourself with FastConnect public peering in order to evaluate various options for integrating public APIs for outbound communication from Oracle Utilities Cloud Services.
Scenario 4: Connect Over Public Internet with VPN and FASTConnect
Connect over the public internet with a VPN Connect and FASTConnect when the integration with an on-premises application requires not only high bandwidth, but also needs a fallback mechanism to ensure close to 100% availability. While the fallback mechanism in this case has a lower bandwidth, it ensures that connectivity persists.
Note these considerations:
| Pre-requisites: |
|
| Working: |
|
| Pros | High bandwidth, high availability, and secure. |
| Cons |
|