Deploy IBM Maximo on Oracle Cloud Infrastructure
Deploy the IBM Maximo Application Suite (MAS) 8.x on Red Hat OpenShift solution on Oracle Cloud Infrastructure (OCI) for asset monitoring, management, predictive maintenance, and reliability planning.
IBM consulting in partnership with Oracle NA Cloud Engineering created the IBM Maximo Application Suite 8 (Asset Management) offering on OCI with easy-to-implement health scoring at scale with up to 30% in cost savings. Customers can choose to deploy this solution on the cloud or on-premises.
Consider these design decisions:
- Versions
- Determine your version of Maximo Application Suite (MAS).
- Determine the version of Red Hat Linux.
- Determine the version of OpenShift and VMware.
- Determine the version of the database.
- Network
- Determine the dependencies with other applications and their latency requirements.
- Determine if external users (non-employees) connect to the MAS system.
- Database
- Determine which database to use (Oracle Database or MySQL).
- Other
- Determine how many MAS worker nodes and control machines are needed.
- Determine the sizes of the virtual machines (VMs).
Architecture
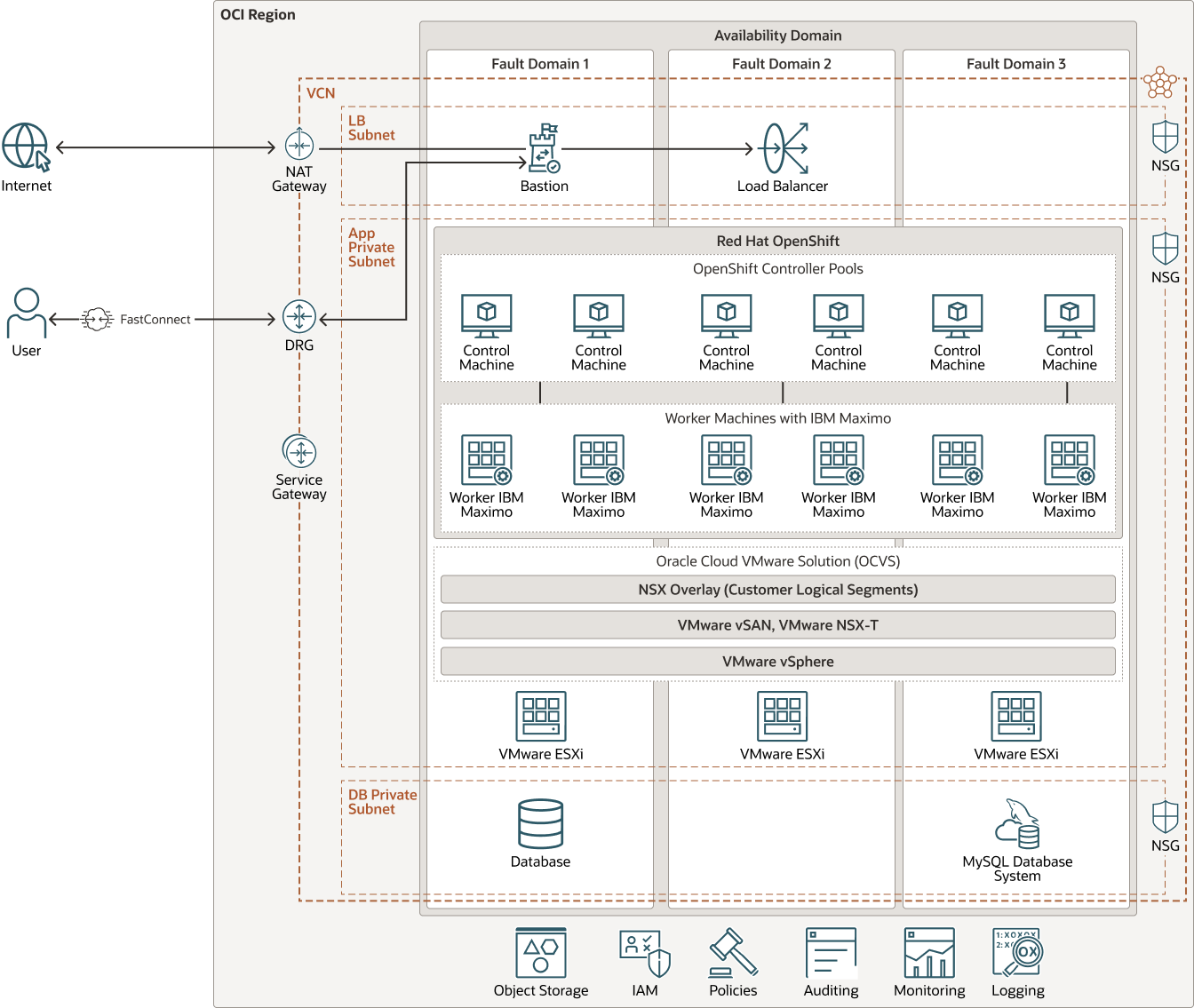
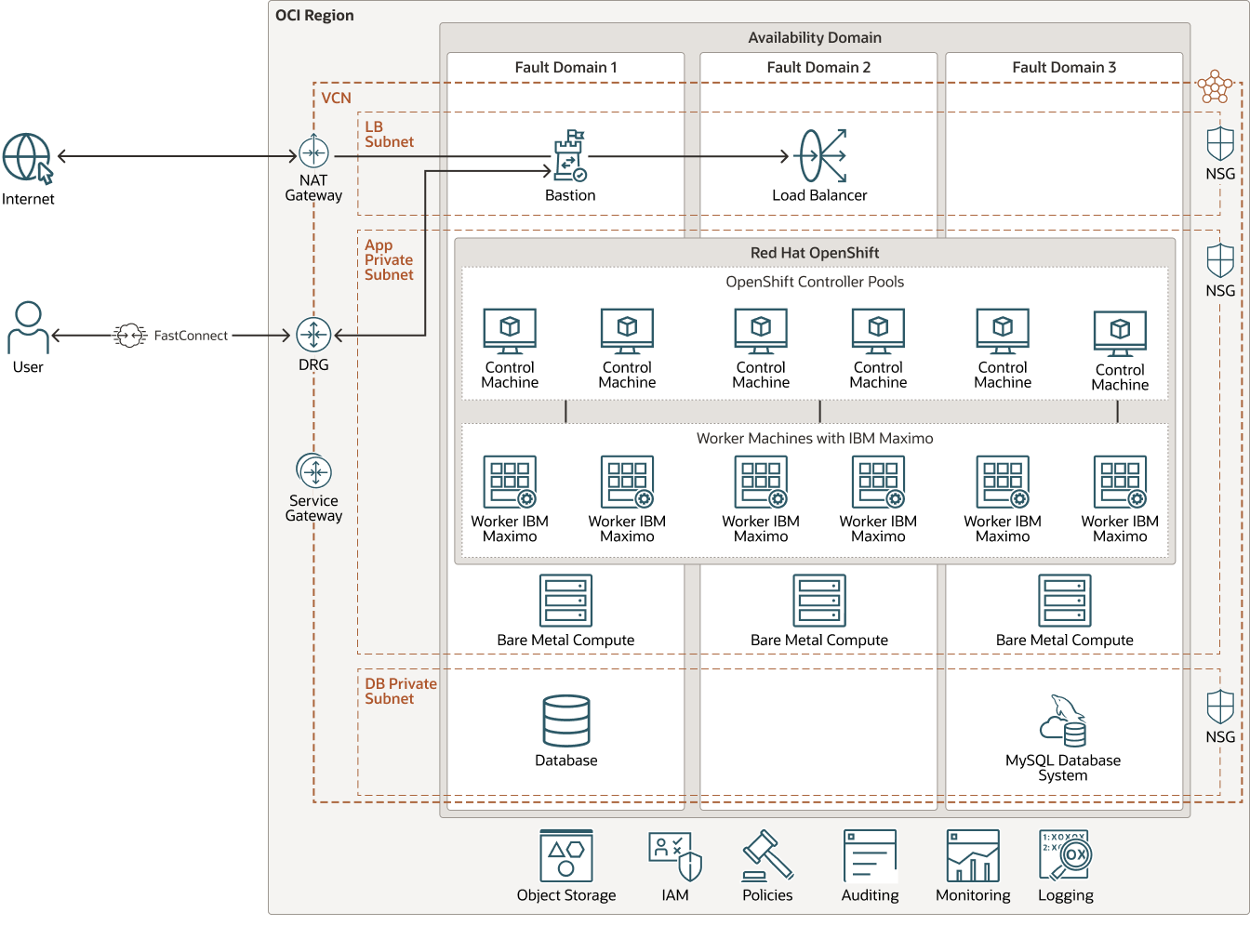
This architecture shows deployment options for IBM MAS, and follows the best practices for OCVS and IBM MAS.
The following options outline the deployment of IBM MAS on OCI.
- IBM MAS on Red Hat OpenShift on Oracle Cloud VMware Solution:
Oracle Cloud VMware Solution provides a customer-managed, native VMware-based cloud environment, installed in a cloud tenancy. It offers complete control, using familiar VMware tools, allowing you to build a resilient, reliable, and high-performance Red Hat OpenShift implementation with Oracle Cloud VMware Solution, providing a robust platform to deploy IBM Maximo.
- IBM MAS on Red Hat OpenShift on Oracle Cloud bare metal instances:
Red Hat OpenShift can be deployed on OCI bare metal instances. Our customers take advantage of OCI’s high-performance bare metal instances to run the most demanding applications.
In both the deployment options, the customer must have a current subscription for Red Hat Enterprise Linux, and Red Hat OpenShift is required for Red Hat support.
The following diagrams illustrate this reference architecture.
IBM MAS on Red Hat OpenShift on Oracle Cloud VMware Solution
maximo-oci-ocvs-diagram-oracle.zip
IBM MAS on Red Hat OpenShift on Oracle Cloud bare metal instances
maximo-oci-bare-metal-diagram-oracle.zip
The architecture has the following components:
- Red Hat OpenShift infrastructure nodes
A minimum of three controllers and workers are required for Red Hat OpenShift infrastructure nodes.
- Control plane or controller nodes
The control plane, which is composed of master machines, manages the Red Hat OpenShift Container Platform cluster. The control plane machines manage workloads on the compute machines, which are also known as worker machines. The controllers are deployed in the form of virtual machines (VMs) in Oracle Cloud VMware Solution and connected to the NSX overlay segment for networking services. The controller VMs are placed in vSAN Storage.
- Worker nodes
In a Kubernetes cluster, the worker nodes are where the actual workloads requested by Kubernetes users run and are managed. In the Red Hat OpenShift Container Platform, MachineSets control the worker machines. Machines with the worker role drive compute workloads that are governed by a specific machine pool that autoscales them. The workers are deployed in the form of VMs in Oracle Cloud VMware Solution and connected to the NSX overlay segment for networking services.
- Control plane or controller nodes
- Oracle Cloud VMware Solution
A minimum of three nodes of software-defined data centers (SDDC) are required to manage the Red Hat OpenShift deployment.
- vSphere
vSphere is VMware's virtualization platform for the unified management of the SDDC's CPU, storage, and networking infrastructure. Two key components of vSphere are VMware ESXi Hypervisor and vCenter Server.
- vSAN
Oracle Cloud VMware Solution SDDCs use VMware's vSAN storage technology, which provides a single shared data store for compute and management workload VMs. A vSAN offers enterprise-grade storage capabilities for Red Hat OpenShift infrastructure nodes and persistent volumes for containers. Persistent volumes requested by stateful containerized applications can be provisioned on VMware vSAN.
- NSX Data Center
NSX-T Data Center provides the SDDC with its virtual networking and security capabilities. The NSX-T deployment includes NSX Manager unified appliances with NSX-T Local Manager and NSX-T Controller, and NSX-T Edge nodes. VMware NSX-T Data Center provides advanced software-defined networking (SDN), security, and visibility to container environments that simplifies information technology operations and extends native Red Hat OpenShift Container Platform networking capabilities.
- vSphere
- Bare metal
Oracle’s bare metal servers provide isolation, visibility, and control by using dedicated compute instances. The servers support applications that require high core counts, large amounts of memory, and high bandwidth. They can scale up to 192 cores, 2.3 TB of RAM, and up to 1 PB of block storage. Customers can build cloud environments on Oracle’s bare metal servers with significant performance improvements over other public clouds and on-premises data centers.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain shouldn't affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Network
address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Dynamic routing gateway
(DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Service
gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and does not traverse the internet.
- Network security group
(NSG)
Network security group (NSG) acts as a virtual firewall for your cloud resources. With the zero-trust security model of Oracle Cloud Infrastructure, all traffic is denied, and you can control the network traffic inside a VCN. An NSG consists of a set of ingress and egress security rules that apply to only a specified set of VNICs in a single VCN.
- Object storage
Oracle Cloud Infrastructure Object Storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Bastion service
Oracle Cloud Infrastructure Bastion provides restricted and time-limited secure access to resources that don't have public endpoints and that require strict resource access controls, such as bare metal and virtual machines, Oracle MySQL Database Service, Autonomous Transaction Processing (ATP), Oracle Cloud Infrastructure Kubernetes Engine (OKE), and any other resource that allows Secure Shell Protocol (SSH) access. With OCI Bastion service, you can enable access to private hosts without deploying and maintaining a jump host. In addition, you gain improved security posture with identity-based permissions and a centralized, audited, and time-bound SSH session. OCI Bastion removes the need for a public IP for bastion access, eliminating the hassle and potential attack surface when providing remote access.
- Oracle VM Database system
Oracle VM Database System is an Oracle Cloud Infrastructure (OCI) database service that enables you to build, scale, and manage full-featured Oracle databases on virtual machines. A VM database system uses Oracle Cloud Infrastructure Block Volumes storage instead of local storage and can run Oracle Real Application Clusters (Oracle RAC) to improve availability.
- Oracle MySQL Database Service
Oracle MySQL Database Service is a fully managed Oracle Cloud Infrastructure (OCI) database service that lets developers quickly develop and deploy secure, cloud native applications. Optimized for and exclusively available in OCI, Oracle MySQL Database Service is 100% built, managed, and supported by the OCI and MySQL engineering teams.
Oracle MySQL Database Service has an integrated, high-performance analytics engine (HeatWave) to run sophisticated real-time analytics directly against an operational MySQL database.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Security lists
Use security lists to define ingress and egress rules that apply to the entire subnet.
- Network security groups (NSGs)
You can use NSGs to define a set of ingress and egress rules that apply to specific VNICs. We recommend using NSGs rather than security lists, because NSGs enable you to separate the VCN's subnet architecture from the security requirements of your application.
- Load balancer bandwidth
While creating the load balancer, you can either select a predefined shape that provides a fixed bandwidth, or specify a custom (flexible) shape where you set a bandwidth range and let the service scale the bandwidth automatically based on traffic patterns. With either approach, you can change the shape at any time after creating the load balancer.
- Bare metal
Oracle offers two types of bare metal servers.
- Dense shape: Dense shapes provide local NVMe storage and don't require block volume storage. vSAN converged storage technology replicates data across all the VMware ESXi hosts in the SDDC with no memory limit, network bandwidth limit, or VNIC count limit. Oracle recommends dense shape for IBM Maximo deployment.
- Standard shape: Standard shapes require block volume storage, limits for memory, bandwidth, and number of VNICs.
Considerations
Consider the following when deploying this reference architecture.
- Performance
To get the best performance, choose the correct compute shape with appropriate bandwidth.
- Availability
Global availability in all OCI regions (48 regions in 25 countries at the time of writing), including dedicated regions. Oracle Cloud VMware Solution incorporates the VMware-recommended best practices for high availability.
- Networking
OCI is the only solution to offer layer 2 with off-box network virtualization as opposed to layer 3 on AWS and Azure. Customers can migrate existing applications including IBM Maximo without substantial re-architecting, and Oracle Cloud VMware Solution can provide customers with unparalleled compatibility and control over their cloud VMware deployments.
- Cost
Save 40% on integration design and build using the more than 50 cloud-integration adapters to systems, including: ADP, IBM Maximo, Taleo, Concur, Blockchain, and all legacy Oracle platforms.
- Authentication
MAS supports Security Assertion Markup Language (SAML), which can be integrated and federated with OCI.
- Service level agreement (SLA)
IBM Maximo being an enterprise critical application, customers have a very high SLA requirement. Only Oracle Cloud offers end-to-end SLAs covering performance, availability, and manageability of services. See Explore More for SLA documentation, with relevant sections being:
| Component family | Component | Section |
|---|---|---|
| Networking | FastConnect | 3.6.32 |
| Networking | Load Balancer | 3.6.40 |
| Database | Oracle Base Database | 3.6.5 |
| Database | MySQL Database | 3.6.44 |
| Compute | VM Standard | 3.6.17 |
| Compute | Bare metal dense IO | 3.6.17 |
| Storage | Block storage | 3.6.15 |
| Storage | Object Storage | 3.6.47 |
| Oracle VMware Solution | Oracle VMware Solution | 3.6.58 |
Explore More
Review these additional resources to learn more about the features of this reference architecture.
Review these additional resources:
- Oracle Cloud Infrastructure Service Level Agreement (SLA)
- Oracle PaaS and IaaS Public Cloud Services Pillar Document (PDF download)
- Deploy Red Hat OpenShift on Oracle Cloud VMware Solution
- Installing Red Hat OpenShift using the Openshift-Install Tool
- IBM Maximo Transformation | Oracle Cloud and IBM Consulting offering