Workload Governance Lifecycle
Workload governance involves scoping the workload and various characteristics associated with the workload to design governance using the governance model. Workload governance progresses in the following four phases:
- Workload Scoping and Assessment: Identifies the scope of the resources, processes, budgets, and security requirements specific to the workload in question.
- Workload Governance Design and Deployment: Identifies workload-specific guardrails across disciplines specific to security, governance, and budgeting.
- Workload Onboarding: Workloads are onboarded into the environment with the appropriate governance guardrails in place
- Workload Governance Monitoring and Offboarding: Offboarding of assets according to the defined lifecycle of the workload
Scope and Assess Workload
As a first step, you must scope the workload in the gating and review process for teams deploying new workloads into OCI.
Scoping ensures that sufficient business drivers and sponsorship and that the appropriate guardrails are in place to securely accommodate the new workload. Assess the workload to determine if it requires governance and how much governance it requires based on how sensitive and business critical the workload is.
Design Your Workload Governance
Use the data obtained in the initial assessment to design your Tenancy for workload governance.
You assess your workload and make decisions based on the answers to certain questions and determine your required organizational outcomes. You begin with the compartment structure you set up during Baseline governance.
The design process of Workload governance follows the governance model similar to Baseline governance. The following are some examples of the thought process involved in designing your workload governance.
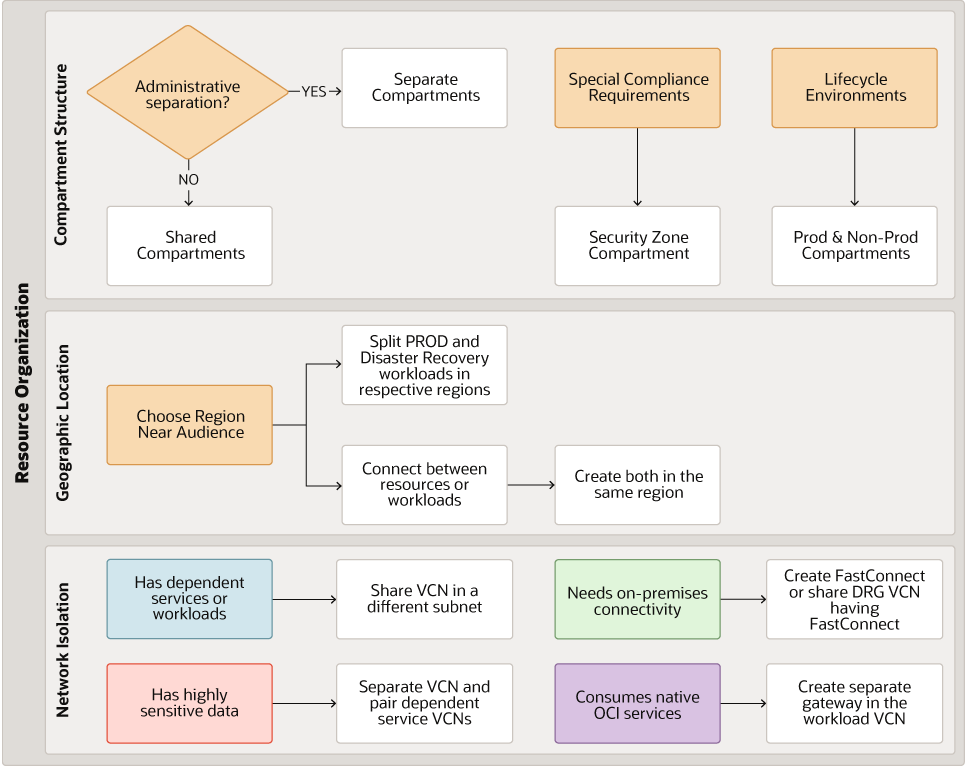
Description of the illustration oci-resource-organization-workflow.png
Organize Workload Resources
You initially organize your resource workloads based on the requirements for compartment structure, geographic location, and network isolation.
Consider the answers to these questions for designing your compartment structure.
- Does the workload need administrative separation?
- Yes: Create a new compartment for your workload resources
- No: Share your workload compartment with an existing compartment
- Does your workload have special compliance requirements such as HIPAA or FedRamp?
- Yes: Create a security zone compartment
- Does the workload have lifecycle environments?
- Yes: Create separate Prod and Non-Prod compartments
Consider the answers to these questions for selecting your workload geographic location.
- Where is your target audience located?
- Choose a region close to your target audience
- How to separate your workload for production and disaster recovery?
- Split the production and disaster recovery workloads in the designated production and disaster recovery regions
- Does the workload need connectivity to other workloads?
- Yes: Create the workloads in the same region
Consider the answers to these questions for deciding your workload network isolation.
- Does the workload have any dependent services or workloads?
- Yes: Share the VCN in a different subnet
- Does the workload have highly sensitive data?
- Yes: Create a separate VCN and pair dependent services VCNs
- Does the workload need connectivity with on-premises workloads?
- Yes: Create Fastconnect setup or share the Dynamic Routing Gateway (DRG) with the VCN that has FastConnect set up
- Does the workload consume native OCI services?
- Yes: Create a service gateway in the workload VCN
Manage Workload Cost
Managing workload costs includes tracking and controlling costs to avoid overspending due to suboptimal resource usage. You can make decisions to save costs when you set up your workloads and track usage against budgets and control costs based on how you organize your workloads in compartments.
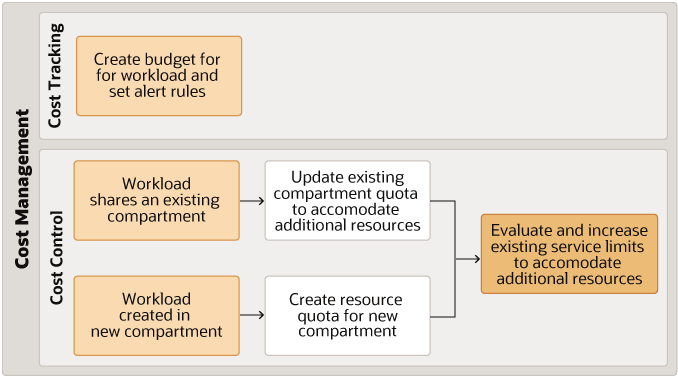
Description of the illustration oci-cost-management-workflow.png
Cost tracking includes setting up budgets and analyzing costs based on resource usage. Create a budget and set up alert rules to notify management or administrators when spending is nearing the budget by setting up limits, quotas, and usage in the Governance section in the OCI Console.
When you are alerted about the spending nearing the budget, you can set up cost control measures based on answers to these questions:
- Does the workload share an existing compartment?
- Yes: Update the compartment quota to accommodate any additional resources
- Is the workload is created in a new compartment?
- Yes: Create resources quotas in the new compartment
- Do your current service limits meeting your organizational needs?
- Yes: Re-evaluate existing service limits and update them to accommodate additional resources
Govern Access
Governing access requires the following steps:
- Identity provisioning
- Identity federation
- Administrative groups and IAM policies
- Privileged account management (PAM)
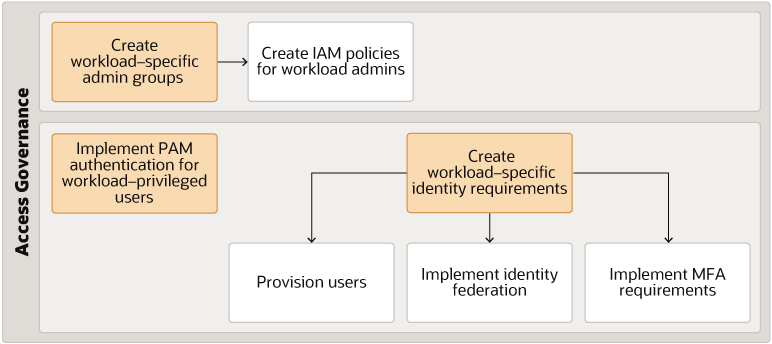
Description of the illustration oci-access-governance-workflow.png
You can implement access governance by creating workload-specific admin groups and then creating IAM policies for workload administrators. You can also implement PAM authentication for workload-privileged users.
If you have workload-specific identity requirements then do the following:
- Provision any workload-specific users
- Implement workload-specific identity federation
- Implement workload-specific MFA requirements
Secure Workloads
Securing your workloads is essential to keep off malicious activity and suspicious events from critical customer data. You can implement workload security by following these steps:
- Enable Cloud Guard
- Enable the Vulnerability Scanning service
- Set up notifications to monitor for suspicious events and create notification rules
Secure Data
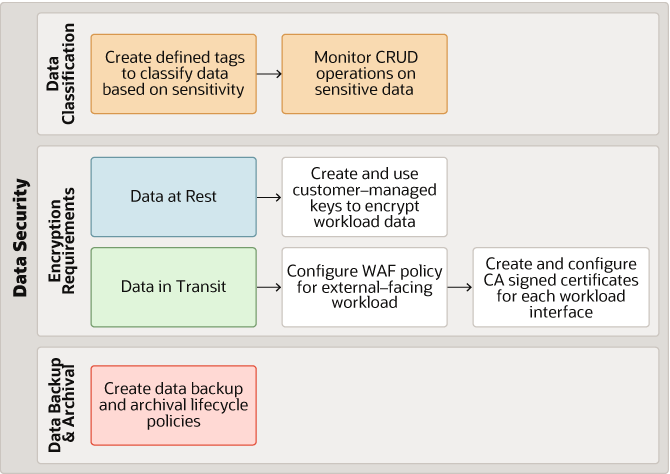
Description of the illustration oci-data-security-workflow.png
Securing critical customer data requires secure practices during implementation to ensure customer data is safe as well as recoverable in the event of data loss. You can secure customer data by following these steps:
- Classify different types of data
- Create defined tags to classify data based on sensitivity
- Monitor Create, Read, Update, and Delete (CRUD) operations on sensitive data
- Identify data encryption requirements for both at-rest and in-transit data
- For data at rest, create and use customer-managed keys to encrypt workload data
- For data in transit, do the following:
- Configure WAF policies for external-facing workloads
- Create and configure CA signed certificates for every workload interface
- Set up data backup and archival lifecycle policies
- Plan to set up policies for data backup and archival
Deploy Your Workload
Once you decide on the governance controls specific to your new workload you can do one of the following:
- Codify it using Terraform
- Utilize the OCI command line interface
- Implement your changes using the OCI Console
Monitor, Support, and Offboard Workloads
Setting up your workloads for monitoring and logging for audit purposes is key to implementing observability of your cloud implementation. Follow these steps to implement observability in your cloud implementation.
- Enable workload monitoring and alerting
- Integrate audit logs with SIEM solution
- Enable service and custom logs to set up logging analytics or SIEM
You can continue to leverage Cloud Guard and other security controls to monitor risky configurations of the OCI control plane related to the workload.
Leverage Drift Detection to ensure that what you deployed in the workload's compartment remains consistent with what you defined in the DevSecOps pipeline. Offboard resources when decommissioning workloads using the DevSecOps pipeline.
You can install and use the OCI Cost Governance and Performance Insights Solution app from Oracle Cloud Marketplace linked in the Explore More section.