Understand the Migration Process
Migrating a Siebel Enterprise by using Oracle Cloud Infrastructure's BYOI feature, as detailed in this playbook involves these steps:
- Preparing/exporting the source Siebel server image on-premises to create an instance in OCI.
- Performing Post VM Migration Tasks.
- Undeploying the Siebel profiles from SMC and redeploying them.
- Updating Siebel CRM to the latest version
Bring Your Own Image
The BYOI feature enables you to bring your own versions of an operating system to the cloud, as long as the underlying hardware supports it. The services do not depend on the OS you run.
- Enables virtual machine cloud migration projects.
- Supports both old and new operating systems.
- Encourages experimentation.
- Increases infrastructure flexibility.
Learn About Limitations and Considerations
Be aware of the following limitations and considerations:
- Licensing requirements: You must comply with all licensing requirements when you upload and start instances, based on OS images that you supply.
- The maximum image size is 400 GB.
- Service limits and compartment quotas apply to custom images although you can request a service limit increase. For more information, see Service Limits, which you can access from the Explore More topic of this playbook.
Understand Launch Modes
You can launch imported Linux VMs in either a paravirtualized mode or an emulated mode. On AMD and Arm-based shapes, Oracle Linux Cloud Developer images, and Windows images, imported images are supported in paravirtualized mode, only.
Paravirtualized mode offers better performance than emulated mode. Oracle recommends that you use paravirtualized mode if your OS supports it. Linux-based operating systems running the kernel version 3.4 or later support paravirtualized drivers. You can verify your system's kernel version using the uname command.
If your image supports paravirtualized drivers, you can convert your existing emulated mode instances into paravirtualized instances. After you complete the conversion, instances created from the image are launched in paravirtualized mode.
Learn Which Windows Images Support Custom Image Import
These Windows versions support custom image import:
- Windows Server 2012 Standard, Datacenter
- Windows Server 2012 R2 Standard, Datacenter
- Windows Server 2016 Standard, Datacenter
- Windows Server 2019 Standard, Datacenter
See These Additional References
- For steps to import a Windows image, see Importing Custom Windows Images.
- Bring your own license (BYOL) for Windows Server is not permitted when launching a VM instance on a shared host. For more information about BYOL and the licensing requirements for Windows images, see Licensing Options for Microsoft Windows and Microsoft Licensing on Oracle Cloud Infrastructure.
- For further information on Linux images and their support details, please refer to BYOI official Oracle documentation.
Migrate Your Image
Migrating an image by using OCI's BYOI feature is a five-stage process, as described in the following flow diagram.
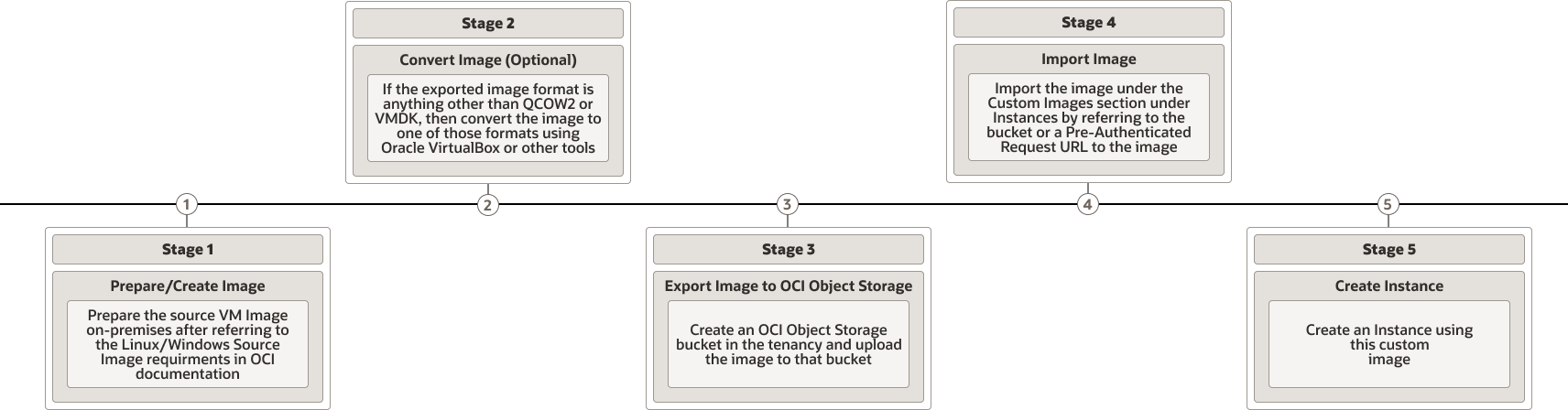
Description of the illustration byoi-sequence-flow.png
The five stages in the process are:
Complete Siebel VM Post Migration Tasks
Once you've migrated the image, you need to complete the following series of post-migration tasks before you can undeploy and deploy the Siebel profiles from the SMC.
Edit hosts and tnsnames.ora Files
In OCI, both the Database Server and the Siebel server VMs have new
hostnames. To bring up the application as-is and to gracefully undeploy the profiles in the
migrated VM, you need to edit the hosts file
(%windir%\system32\drivers\etc\hosts) and
tnsnames.ora
(ORACLE_HOME\network\admin).
- Go to
C:\Windows\System32\drivers\etc\hosts. - To edit the hosts file, first copy it to the desktop because the original path might not allow editing.
- Add hostnames and IP of the old database, new DB host (if required), and the on-premises Siebel server.
- Edit the Oracle Database Client 's
tnsnames.orato reflect the new TNS entries.
Add Windows User to the Administrators’ Group
Now, add to the administrators’ group in Computer Management the Windows account on which you're going to install the image and perform other activities. This ensures you don’t run into any privilege issues while updating via the Siebel Install wizard.
- Launch Computer Management from the control panel.
- Expand Local Users and Groups, click Groups, and then, from the list, double click Administrators.
- Click Add. If the value is a domain user, enter the username with the domain name; otherwise, just enter the username.
- Click OK.
Disable User Account Control in Windows
As described in the My Oracle Support (MOS) note, Doc ID 2502825.1 and Doc ID 2472250.2, disable User Account Control (UAC) in Windows so that necessary changes to the operating system, system files, and registry by the Siebel install wizard can occur seamlessly. However, for security reasons, once the update is done, re-enable it.
Note:
You can find links to both of these MOS notes in the Explore More topic elsewhere in this playbook.%windir%\System32\cmd.exe /k %windir%\System32\reg.exe ADD HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f %windir%\System32\cmd.exe /k %windir%\System32\reg.exe ADD HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f Validate Database Connectivity by Using SQLPlus and ODBC
Next, useSQLPlus and ODBC to ensure proper database connectivity.
Remove and Recreate Siebel Gateway Security Profile
In OCI, the hostname of the DB has changed. As a result, you need to accommodate this change by deleting and recreating the Siebel Gateway Security profile. Refer to MOS Doc ID 2371577.1.
Note:
See the Explore More topic elsewhere in this playbook for a link to the aforementioned MOS note.Siebel 19.11 and above introduced a new functionality called Safe Mode, which enables administrators to preemptively set up a safe mode user in SMC with which they can log in in the future if the DB’s hostname changes. Ensure the Siebel Gateway Registry Service is up and running and that the version-2 folder is backed up before proceeding.