About Connecting OCI Serbia Realm to another OCI Commercial region
Oracle has opened the Oracle Cloud Jovanovac Region located in Kragujevac, Serbia. This region is unique among Oracle commercial regions as it exists within a unique realm.
Realms are implemented in the Oracle Cloud design to section off a region, or group of regions, for data sovereignty, compliance or security reasons. A realm is a logical collection of cloud regions that are isolated from each other and do not allow customer content to traverse realm boundaries to a region outside that realm. Each realm is accessed separately.
Oracle does not provide the tools to connect regions across a realm boundary via our network backbone. There are use cases where a customer may wish to connect their Oracle Cloud presence across the realm boundary. In this solution playbook, we will explore how to interconnect the Oracle Cloud Jovanovac Region with an Oracle Cloud commercial region across the realm boundary using a third-party provider from the Oracle Cloud Infrastructure FastConnect location.
Before You Begin
In order to perform the tasks described in this solution playbook, you need to have a basic understanding of networking and be familiar with Oracle Cloud Infrastructure (OCI). Before you begin, complete the following prerequisites.
- VCNs – A VCN in Serbia region/realm with 172.16.0.0/16 CIDR and another VCN in the Frankfurt region with 10.1.0.0/16 CIDR with all subnets, routing and Security List/Network Security Groups to allow connectivity between Serbia and Frankfurt CIDR Blocks, as well as your on-premises CIDRs blocks.
- DRGs – One DRG in Serbia and one DRG in Frankfurt with VCN attachments and routing in place to allow traffic between the Serbia VCN and the Frankfurt VCN.
- Oracle Cloud Infrastructure Identity and Access Management (OCI IAM) permissions - An OCI account, with at least one user with appropriate OCI IAM permissions. For example, an user in the Administrators group.
- Prerequisite data needed to configure this solution:
- Use non-overlapping IP CIDR blocks - In this solution playbook, we are using 172.16.0.0/16 for Serbia, 10.1.0.0/16 for Frankfurt, and 100.64.0.0/16 for the customer on-premises datacenter.
- A private Border Gateway Protocol (BGP) Autonomous System Number (ASN) - You can pick any ASN from 64512 - 65533.
- A minimum (3) /30 subnets - For your point-to-point FastConnect links. In this solution playbook, we are using 192.168.0.0/30, 192.168.0.4/30, and 192.168.0.8/30.
- For connection to a third-party provider: At least one physical connection with the provider for each of the respective links (i.e., one physical connection for Serbia, one physical connection for Frankfurt).
- Network equipment - CPE devices that support Layer-3 routing using BGP.
- Account limits - If you intend to colocate with Oracle, you
must ask Oracle to increase your account limits for cross-connects.
Note:
The default limits are initially set to 0, and without a specific request for limit increase, you won't be able to create a valid cross-connect. For instructions on placing this request, see Requesting a Service Limit Increase. In your request, indicate the region where you need the resources. It can take a couple of business days for the limit increase to take effect.
Architecture
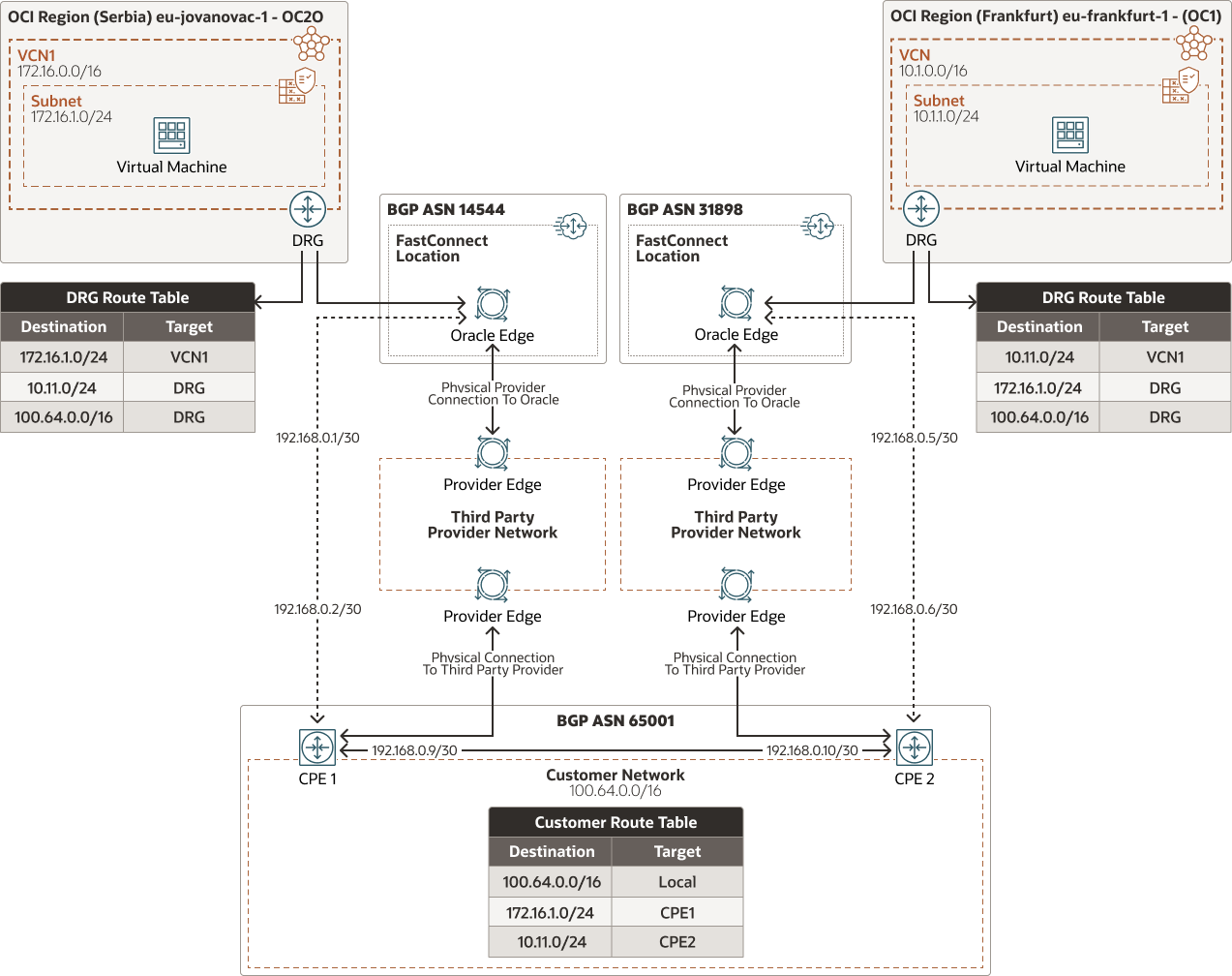
In this architecture, we will use two FastConnect setups using your network as the connection point between the two OCI Realms.
A customer on-premises location is connected to both the Serbia Realm (eu-jovanovac-1) and the Frankfurt region (eu-frankfurt-1) in our Commercial Realm. The connection process for the customer involves the following key points:
- Use a third-party telecom provider to provision Layer-2 connectivity from the on-premises CPE1 all the way up to the Oracle Edge Router in the Oracle FastConnect location in Serbia.
- Use a third-party telecom provider to provision Layer-2 connectivity from the on-premises CPE2 all the way up to the Oracle Edge Router in the Oracle FastConnect location in Frankfurt.
- Establish a Layer-3 BGP peering connection from CPE1 to the Oracle Edge Router in the OCI Serbia FastConnect location.
- Establish a Layer-3 BGP peering connection from CPE2 to the Oracle Edge Router in the OCI Frankfurt FastConnect location.
- Provide Layer-3 network connectivity inside their own network to allow traffic from the Serbia OCI Realm to reach the Frankfurt region, and vice versa.
oci-serbia-realm-arch-oracle.zip
This architecture supports the following components:
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Virtual cloud network (VCN) and subnet
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
Considerations
When implementing this solution, consider the following design best practices.
- Avoid Single Points of Failure - It is recommended that you use diverse CPE connections (a router for connectivity to Serbia, and a separate router for connectivity to Frankfurt). This reduces the chances of an outage due to a single point of failure.
- Use VPN as a backup to FastConnect - Oracle recommends using
Site-to-Site VPN as a backup for your FastConnect connection. Ensure that the
Site-to-Site VPN IPSec tunnels are configured to use BGP routing with a route-based
VPN. Within your existing on-premises network, manipulate the routing to prefer
routes learned through FastConnect over routes learned through Site-to-Site VPN. For
example, use
AS_Path Prependto influence egress traffic from Oracle, and use local preference to influence egress traffic from your network. If you use VPN backup, review Oracle's BGP routing behavior in the table shown in Using AS_PATH to prefer routes from Oracle to your on-premises network. - Influencing traffic from Oracle Cloud to On-Premises (AS_PATH) - If you want traffic from Oracle Cloud to prefer one path over the other as it comes back to your on-premises location,
you can take advantage of using the BGP
AS_PATHattribute to allow you to prefer routes from Oracle Cloud to your on-premises network. - Influencing traffic from On-Premises to Oracle Cloud (Local Preference) - If you want traffic from your on-premises location to prefer one path over the other as it goes to your Oracle Cloud, you can take advantage of BGP Local Preference to influence egress traffic that leaves your on-premises network towards Oracle Cloud.