Design an Oracle Analytics Cloud DR Topology with Oracle Cloud Infrastructure Full Stack Disaster Recovery Service
A well-architected disaster recovery (DR) plan enables you to recover quickly from disasters and continue to provide services to your users.
DR is the process of preparing for and recovering from a disaster. A disaster can be any event that puts your applications at risk, such as network outages, equipment and application failures, or natural disasters.
Oracle Analytics Cloud provides the Availability Service Level Agreement (SLA) at least 99.9%. Despite having SLA on Oracle Analytics Cloud availability, for certain organizations, it is a statutory or audit obligation to have a DR instance. Hence, you are responsible for DR planning.
Oracle Cloud Infrastructure (OCI) provides highly available and scalable infrastructure and services that enable you to design a DR topology.
This reference guide provides you with architecture and guidelines for Oracle Analytics Cloud instances using Oracle Cloud Infrastructure Full Stack Disaster Recovery Service in the case of DR.
Architecture
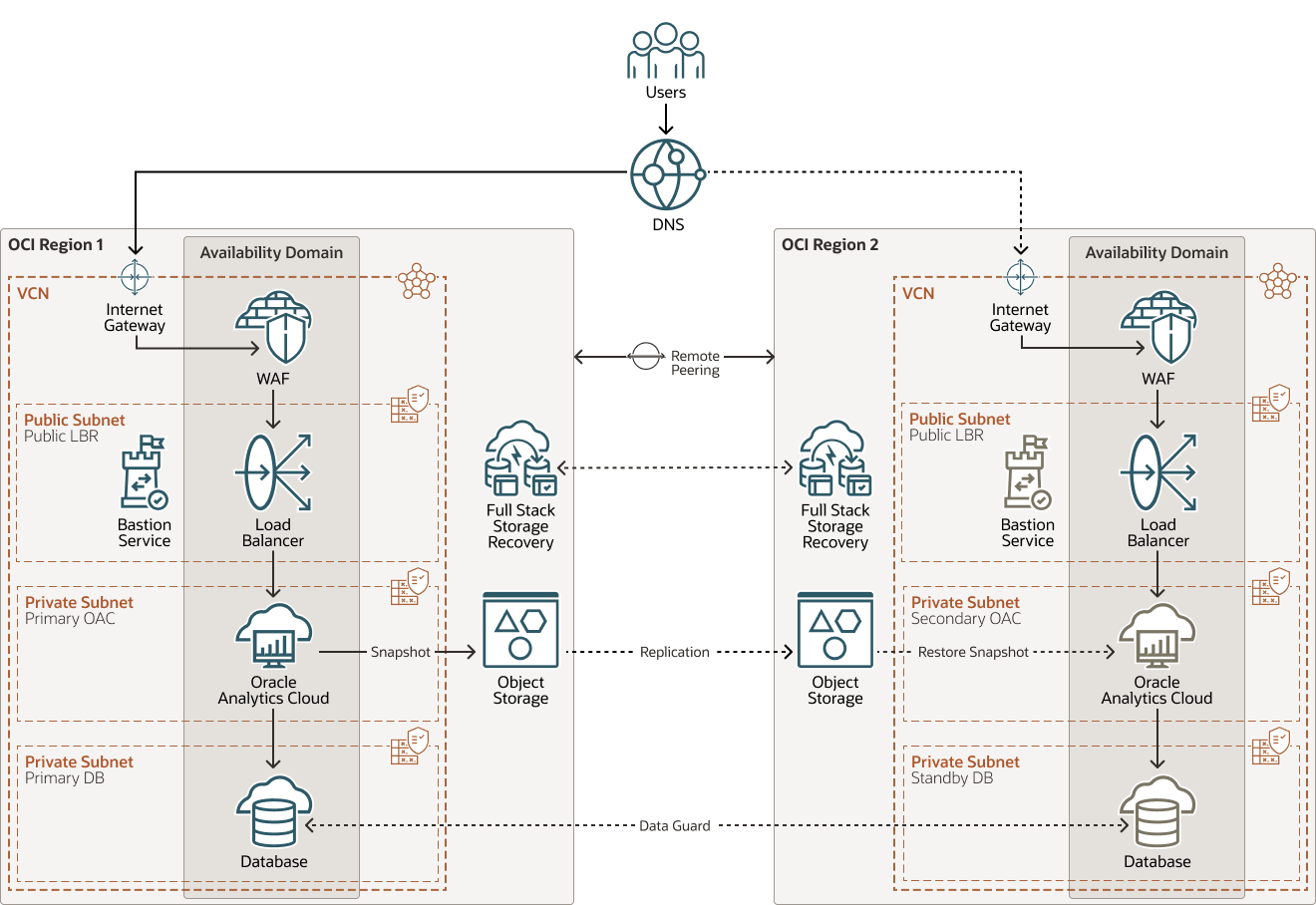
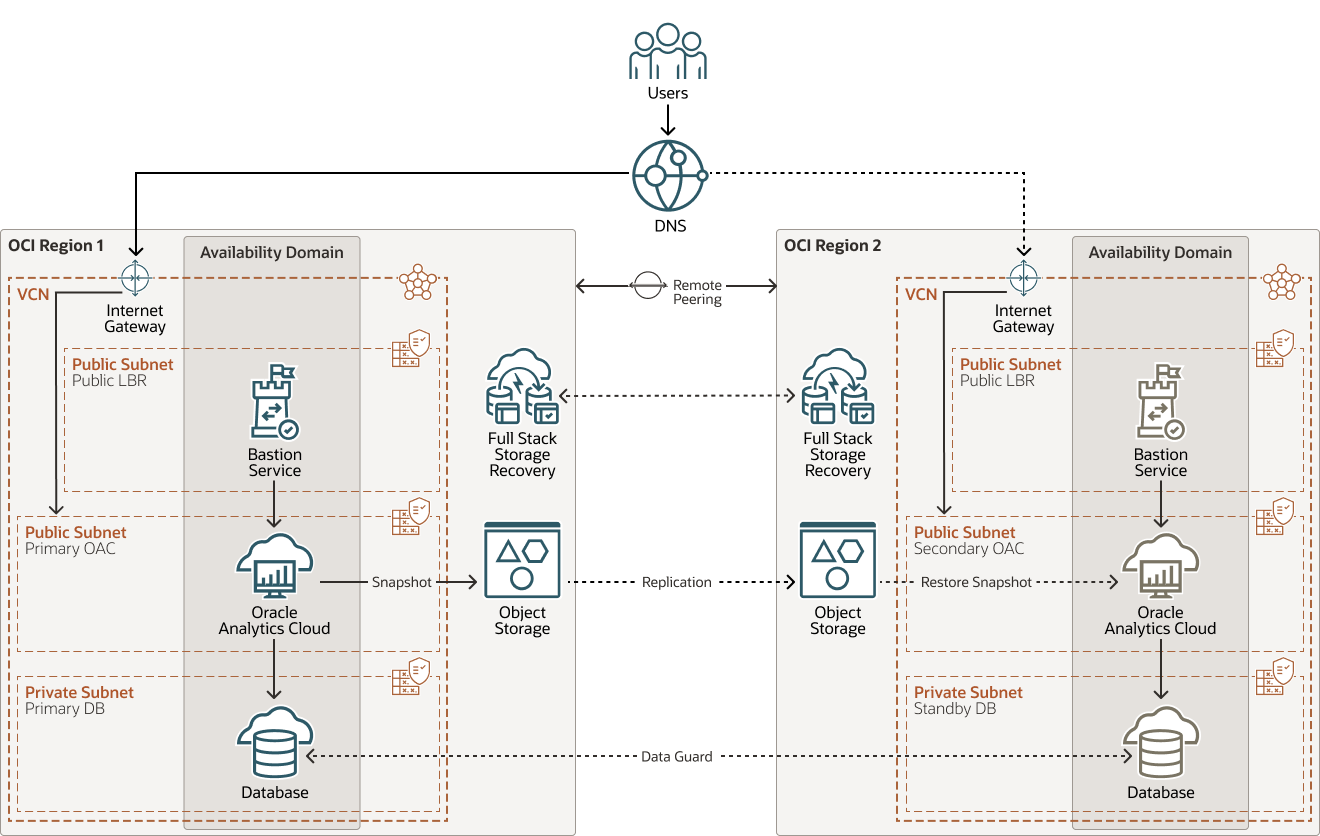
This architecture shows a multi-tier topology that has redundant resources distributed across two OCI regions.
The following diagrams illustrate this reference architecture.
An Oracle Analytics Cloud private instance can't be accessed from the public internet so it requires an OCI public load balancer to facilitate the access. The public load balancer's IP address will be added to the DNS registrar.
oci-fullstack-dr-private-oac-x-region-topology-oracle.zip
An Oracle Analytics Cloud public instance can be accessed directly from the internet. The Oracle Analytics Cloud public IP address will be directly configured with the DNS registrar.
oci-fullstack-dr-public-oac-x-region-topology-oracle.zip
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Compartment
Compartments are cross-regional logical partitions within an Oracle Cloud Infrastructure tenancy. Use compartments to organize, control access, and set usage quotas for your Oracle Cloud resources. In a given compartment, you define policies that control access and set privileges for resources.
- Availability domains
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain shouldn't affect the other availability domains in the region.
- Fault domains
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Network
address translation (NAT) gateway
A NAT gateway enables private resources in a VCN to access hosts on the internet, without exposing those resources to incoming internet connections.
- Service
gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and does not traverse the internet.
- Cloud Guard
You can use Oracle Cloud Guard to monitor and maintain the security of your resources in Oracle Cloud Infrastructure. Cloud Guard uses detector recipes that you can define to examine your resources for security weaknesses and to monitor operators and users for certain risky activities. When any misconfiguration or insecure activity is detected, Cloud Guard recommends corrective actions and assists with taking those actions, based on responder recipes that you can define.
- Security zone
Security zones ensure Oracle's security best practices from the start by enforcing policies such as encrypting data and preventing public access to networks for an entire compartment. A security zone is associated with a compartment of the same name and includes security zone policies or a "recipe" that applies to the compartment and its sub-compartments. You can't add or move a standard compartment to a security zone compartment.
- Object storage
Oracle Cloud Infrastructure Object Storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- FastConnect
Oracle Cloud Infrastructure FastConnect provides an easy way to create a dedicated, private connection between your data center and Oracle Cloud Infrastructure. FastConnect provides higher-bandwidth options and a more reliable networking experience when compared with internet-based connections.
- Local
peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
- Full Stack Disaster Recovery Service
OCI Full Stack Disaster Recovery Service is an OCI disaster recovery orchestration and management service that provides comprehensive disaster recovery capabilities for all layers of an application stack, including infrastructure, middleware, database, and application.
- Bastion service
Oracle Cloud Infrastructure Bastion provides restricted and time-limited secure access to resources that don't have public endpoints and that require strict resource access controls, such as bare metal and virtual machines, Oracle MySQL Database Service, Autonomous Transaction Processing (ATP), Oracle Cloud Infrastructure Kubernetes Engine (OKE), and any other resource that allows Secure Shell Protocol (SSH) access. With OCI Bastion service, you can enable access to private hosts without deploying and maintaining a jump host. In addition, you gain improved security posture with identity-based permissions and a centralized, audited, and time-bound SSH session. OCI Bastion removes the need for a public IP for bastion access, eliminating the hassle and potential attack surface when providing remote access.
- Autonomous Database
Oracle Autonomous Database is a fully managed, preconfigured database environment that you can use for transaction processing and data warehousing workloads. You do not need to configure or manage any hardware, or install any software. Oracle Cloud Infrastructure handles creating, backing up, patching, upgrading, and tuning the database.
- Analytics
Oracle Analytics Cloud is a scalable and secure public cloud service that empowers business analysts with modern, AI-powered, self-service analytics capabilities for data preparation, visualization, enterprise reporting, augmented analysis, and natural language processing and generation. With Oracle Analytics Cloud, you also get flexible service management capabilities, including fast setup, easy scaling and patching, and automated lifecycle management.
- Data Guard
Oracle Data Guard and Oracle Active Data Guard provide a comprehensive set of services that create, maintain, manage, and monitor one or more standby databases and that enable production Oracle databases to remain available without interruption. Oracle Data Guard maintains these standby databases as copies of the production database by using in-memory replication. If the production database becomes unavailable due to a planned or an unplanned outage, Oracle Data Guard can switch any standby database to the production role, minimizing the downtime associated with the outage. Oracle Active Data Guard provides the additional ability to offload read-mostly workloads to standby databases and also provides advanced data protection features.
- Dynamic routing gateway
(DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Web Application
Firewall (WAF)
Oracle Cloud Infrastructure Web Application Firewall (WAF) is a payment card industry (PCI) compliant, regional-based and edge enforcement service that is attached to an enforcement point, such as a load balancer or a web application domain name. WAF protects applications from malicious and unwanted internet traffic. WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer's applications.
Recommendations
- VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources that you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don't overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
- Cloud Guard
Clone and customize the default recipes provided by Oracle to create custom detector and responder recipes. These recipes enable you to specify what type of security violations generate a warning and what actions are allowed to be performed on them. For example, you might want to detect Object Storage buckets that have visibility set to public.
Apply Cloud Guard at the tenancy level to cover the broadest scope and to reduce the administrative burden of maintaining multiple configurations.
You can also use the Managed List feature to apply certain configurations to detectors.
- Security Zones
For resources that require maximum security, Oracle recommends that you use security zones. A security zone is a compartment associated with an Oracle-defined recipe of security policies that are based on best practices. For example, the resources in a security zone must not be accessible from the public internet and they must be encrypted using customer-managed keys. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates the operations against the policies in the security-zone recipe, and denies operations that violate any of the policies.
- Network security groups (NSGs)
You can use NSGs to define a set of ingress and egress rules that apply to specific VNICs. We recommend using NSGs rather than security lists, because NSGs enable you to separate the VCN's subnet architecture from the security requirements of your application.
- Load balancer bandwidth
While creating the load balancer, you can either select a predefined shape that provides a fixed bandwidth, or specify a custom (flexible) shape where you set a bandwidth range and let the service scale the bandwidth automatically based on traffic patterns. With either approach, you can change the shape at any time after creating the load balancer.
- DNS resolution
By default, the internet and VCN resolver does not let instances resolve the hostnames of hosts in your on-premises network connected to your VCN by site-to-site VPN or OCI FastConnect. That functionality is achieved either by using a custom resolver or by configuring the VCN’s private DNS resolver.
- Snapshot backup
Oracle recommends that you take snapshots at significant checkpoints; for example, before you make a major change to your content or environment. In addition, Oracle recommends that you take regular daily snapshots or at your own defined frequency based on the rate of change of your environment and rollback requirements or recovery point objective (RPO) timelines. You are advised to keep the snapshot files in OCI Object Storage.
Considerations
Consider the following points when deploying this reference architecture.
- Performance
When planning the RPO and RTO, consider the time required for volume backups to be copied across regions. It is essential to note that Oracle Analytics Cloud service is not yet part of OCI Full Stack Disaster Recovery Service. You can orchestrate only the steps involved in the DR process in a single-click DR execution.
- Availability
You can use custom DNS domain settings to redirect client traffic to the current production region after a failover.
- Cost
In the event of a failover from the primary to the standby region, you can save substantial costs (approximately 80%) on the secondary instance. A secondary instance can be in pause mode.
- Database source
Your source databases are synchronized using Data Guard and automatically taken care of by OCI Full Stack Disaster Recovery Service.
- Vanity URL
You have prerequisites for vanity URLs, such as custom domains and certificates.
- Configurations
The following configurations in the primary and secondary instances need to synchronize based on your change management process, as they will not be carried on the snapshot backup.
- Virus scanner configuration
- Mail server configuration
- Other saved snapshots in the source environment
- Users (and groups)
- Identity management configuration (for example, SSO)
- Network configuration
- Database connection
Your RPD DB connection to the primary and secondary databases should be the same.
Deploy
The reference Bash scripts are available in GitHub.
- Go to GitHub.
- Clone or download the repository to your local computer.
- Follow the instructions in the
READMEdocument. - See also Full Stack DR: Automate Recovery Operations for Oracle Analytics Cloud Service.
Explore More
Learn more about OCI Full Stack Disaster Recovery Service.
Review these additional resources:
- Disaster Recovery Plan for Oracle Analytics Cloud using Manual Switchover Method
- Disaster Recovery Configuration for Oracle Analytics Cloud
- Set Up a Vanity URL for Oracle Analytics Cloud on OCI Gen 2
- Overview of Full Stack Disaster Recovery
- Administering Oracle Analytics Cloud on Oracle Cloud Infrastructure (Gen 2)