Secure Your Application Using WAF
Once your application is routed through Web Application Firewall (WAF), secure your application by using the various security features offered by WAF.
You can secure your application by:
- Configuring protection rules
- Using Bot management
- Adding access rules
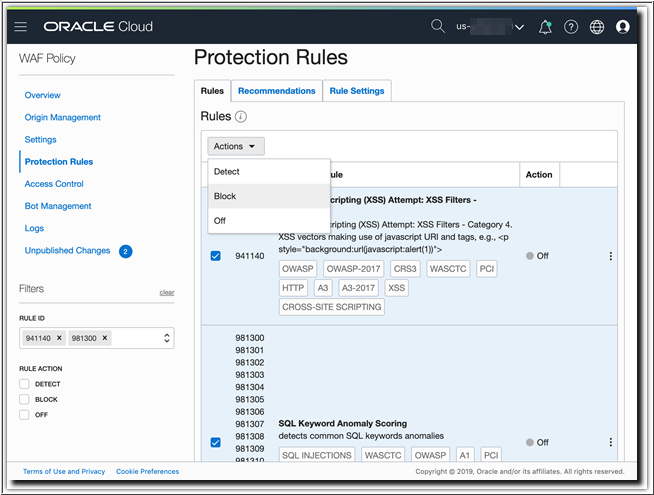
Configure Protection Rules
You can secure the application with rules to block Cross Site Scripting (XSS) and SQL Injection (SQLi) attacks.
Verify Protection Rules
Block action several times. Now, return to the WAF policy details in the Oracle Cloud
Infrastructure console to inspect the logs.
- Open the Employee Demo Policy.
- Click Logs.
- Select a date/time range that spans the time when you attempted the SQLi and XSS attacks.
- Identify the items with
Action: Block, expand the row details on a blocked request, and then click View JSON. - View the messages listed as
protectionRuleDetectionsand other request details.
Use Bot Management
Another feature of the Oracle Cloud Infrastructure Web Application Firewall (WAF) service is its Bot management capabilities.
In many cases, non-human traffic constitutes the largest percentage of traffic to a site. While certain "good" Bots are favorable, other "bad" Bots may attempt content scraping, spamming, brute force attacks, or application layer DDoS attacks.
For example, you may want to whitelist certain well-known Bots for Search Engine Optimization (SEO) and content ranking purposes, but limit verification of a human user for certain interactions. This type of scenario is easily accomplished with the WAF policy Bot management settings.
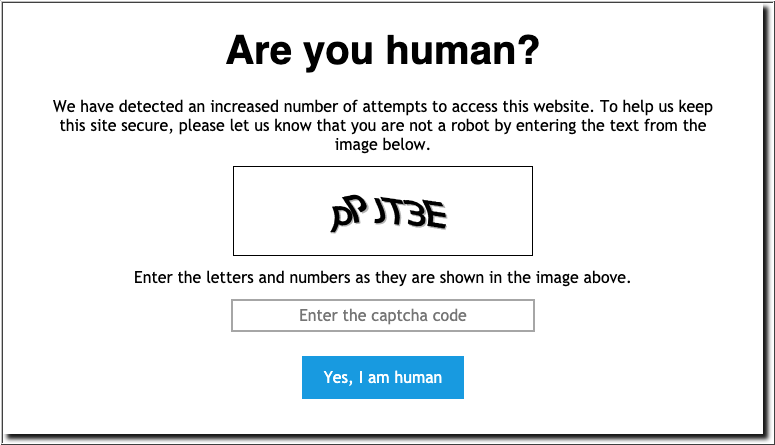
Add a CAPTCHA Challenge
One of the salient features of Bot management is CAPTCHA. The use of CAPTCHA provides a simple means of user verification that ensure human interaction, without requiring any changes to the underlying application.
After entering the correct code, you enter the website without any further challenges for a period corresponding to the Session Duration value in the challenge configuration.
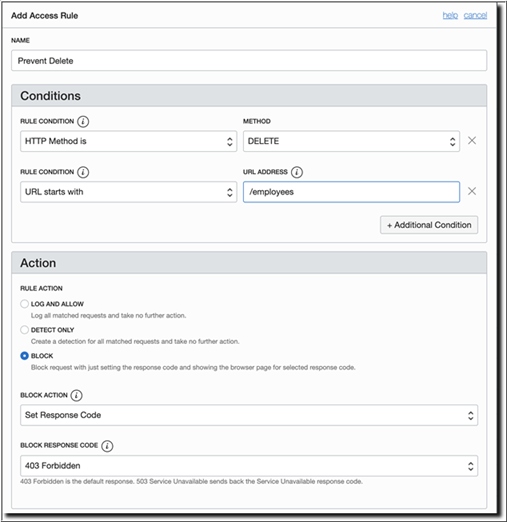
Add an Access Control Rule
WAF access control provides an additional layer of security by restricting or blocking access to the data and services available within an application.
- HTTP headers
- URL patterns
- IP addresses
- Geolocation
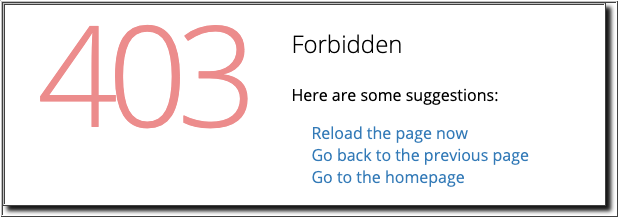
In the sample Employee application, you've the ability to delete employee details from the database. You may need to restrict the use of the Delete feature for security purpose. You can create and apply an access rule to block the delete requests.
After the changes are published and the WAF policy resumes in the ACTIVE state:
- Open the Network tab from your browser's Developer Tools page.
- Access the sample employee application,
http://employee.<example.com>/public/, from your browser. - Select an employee record, and then click the Delete button.
In the Network tab of your broswer Developer Tools section, you'll notice that WAF has intercepted this request and blocked it with a 403 Forbidden response.
The features of Oracle Cloud Infrastructure WAF discussed in this solution focus on securing a basic example application. The usage scenarios will be unique to each application, and you can configure WAF accordingly.