Learn About Protecting Microservices-Based Web Applications from Cyberattacks
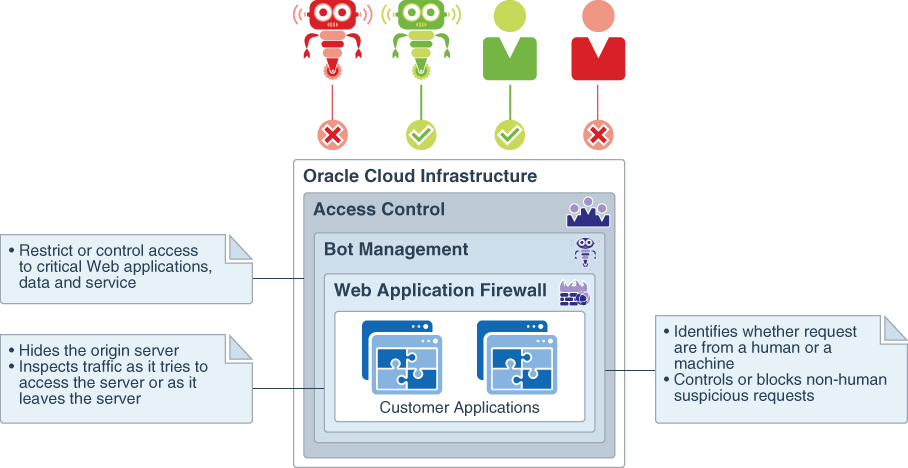
When applications are deployed in the public cloud, it is necessary to protect and secure them at every level. The WAF service on Oracle Cloud Infrastructure provides a layered approach to securing applications against cyberattacks. Some of the features include but not limited to:
- Over 250 predefined Open Web Access Security Project (OWASP), application, and compliance-specific protection rules
- Aggregated thread intelligence from multiple sources, including Webroot BrightCloud®
- Advanced Bot management with JavaScript verification, CAPTCHA challenge, whitelisting, device fingerprinting, and human interaction algorithms
- Rule-based access control including HTTP headers, URL patterns, geolocation, and IP address characteristics
- Layer 7 distributed denial-of-service (DDoS) attack protection
The following image lists the security features of WAF on Oracle Cloud Infrastructure.
Before You Begin
Architecture
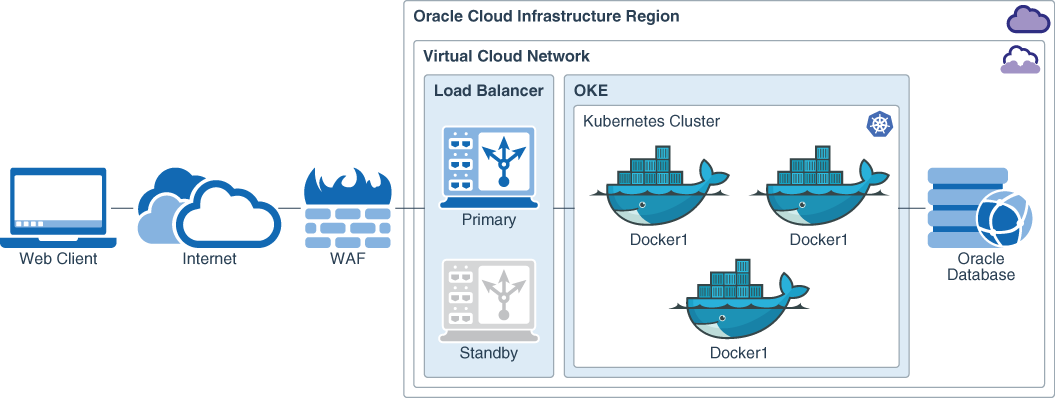
This architecture diagram shows the completed RESTful Java microservices application that is secured by using WAF.
Each microservice consists of the application running in multiple Docker containers in a Kubernetes cluster. The application traffic is routed through the Internet-facing, WAF service, usually through a Domain Name System (DNS). WAF is configured to forward request traffic to the application through a load balancer. The load balancer selects which application instance is used to process a request. The number of application instances is controlled by the Kubernetes cluster and can be scaled up or down automatically. Use this architecture for deploying similar microservices applications.
- The RESTFul web service client application, written in HTML/CSS/JavaScript, is used to access the application.
- The client connects to the application through the Internet-facing, WAF service, usually through a DNS.
- WAF is configured to forward request traffic to the application through a load balancer by using the load balancer IP address, in this case.
- The back-end application is a set of Docker containers in a Kubernetes cluster. Typically, more than one copy of the application is deployed and the load balancer is used to select which application instance the client communicates with.
- The application uses Oracle Cloud Infrastructure Database for persistence. Any stored data is pushed to the database. No state is saved in the Kubernetes cluster.
About Required Services and Roles
This solution requires the following services:
- Oracle Cloud Infrastructure Database
- Oracle Cloud Infrastructure Container Engine for Kubernetes
- Oracle Cloud Infrastructure Registry
To use Oracle Cloud
Infrastructure WAF, you must have sufficient privileges defined in waas-policy. If you try to perform an action and get a message that you don't have permission or are unauthorized, confirm with your administrator the type of access you've been granted and which compartment you should work in.
To allow a specific user group to manage policies in WAF:
Allow group <GroupName> to manage waas-policy in compartment <CompartmentName>Allow group <GroupName> to read waas-work-request in compartment <CompartmentName>See Learn how to get Oracle Cloud services for Oracle Solutions to get the cloud services you need.