ReadyNetworks: Deploy Six.One Virtual Desktop Infrastructure (VDI) on Oracle Cloud
With tens of millions of people working remotely, a $60 billion market for virtual desktop infrastructure (VDI) services has emerged.
ReadyNetworks has created Six.One, a desktop-as-a-service (DaaS) solution built on a VDI platform on Oracle Cloud Infrastructure (OCI). Whether clients want to scale their workloads across hybrid, multicloud, or private virtual networks, ReadyNetworks provides a subscription-based hosted service that’s accessible from anywhere in the world. Six.One allows customers secure and instant access to applications from anywhere, on any device.
Because Six.One integrates with Oracle applications such as Oracle Enterprise Resource Planning Cloud, JD Edwards EnterpriseOne, and PeopleSoft, Six.One users can save up to 25% when accessing Oracle ERP applications from their OCI tenancies. Six.One users can also create personal (dedicated), shared, or pooled desktops on OCI and provision varying levels of compute and storage services while running on either Microsoft Windows or Linux virtual desktops.
Architecture
Currently, Six.One is configured in a multicloud configuration: the Six.One portal is located in Microsoft Azure and the desktop-as-a-service (DaaS) infrastructure is located on Oracle Cloud Infrastructure (OCI).
The diagrams below show the infrastructure location in OCI Region - Ashburn, however Six.One is flexible and can be hosted in any of OCI's regions globally. Users access the Six.One portal to provision and configure their resources. After they are provisioned, users use a remote desktop (RDP) gateway that points them to the correct desktop session, creating a secure connection on OCI.
Six.One is offered in two deployment models. The first deployment model is a managed service deployment model, in which Six.One manages the infrastructure in a Six.One-owned tenancy. The second deployment model is a hybrid deployment model, in which the infrastructure is deployed in its entirety into a customer's new or existing OCI tenancy.
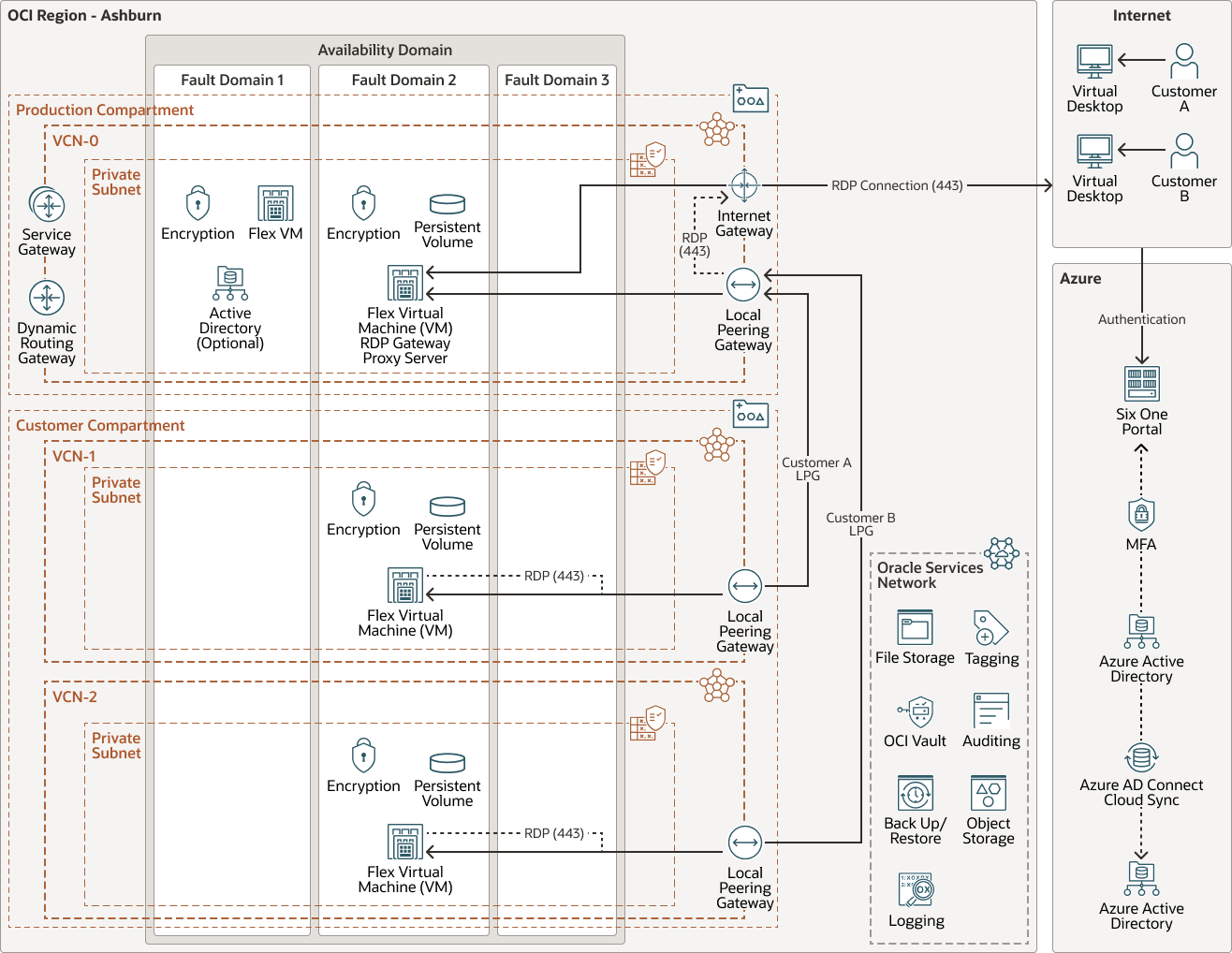
In the managed service model, Six.One uses two compartments for security and isolation: a compartment for its production/shared infrastructure and a compartment for its customers. Multiple virtual cloud networks (VCNs) are then created to separate the production infrastructure from the customer infrastructures. Each customer infrastructure is then isolated by VCNs to isolate the customers from each other, creating a security boundary. Network traffic is controlled by using security lists.
The production VCNs within the same tenancy are then connected to the customer VCNs by using local peering, which allows for VCN-to-VCN connectivity. Customers that choose to be in a different OCI region are connected either by using a dynamic routing gateway (DRG) connection or by using remote peering. Six.One uses the Azure availability domain for authorization access and authorization to the Six.One portal as well as for desktop access and authentication. All of the Six.One components are deployed by using end-to-end automation.
The following diagram illustrates the reference architecture for the Six.One managed service deployment.
six-one-architecture-oracle.zip
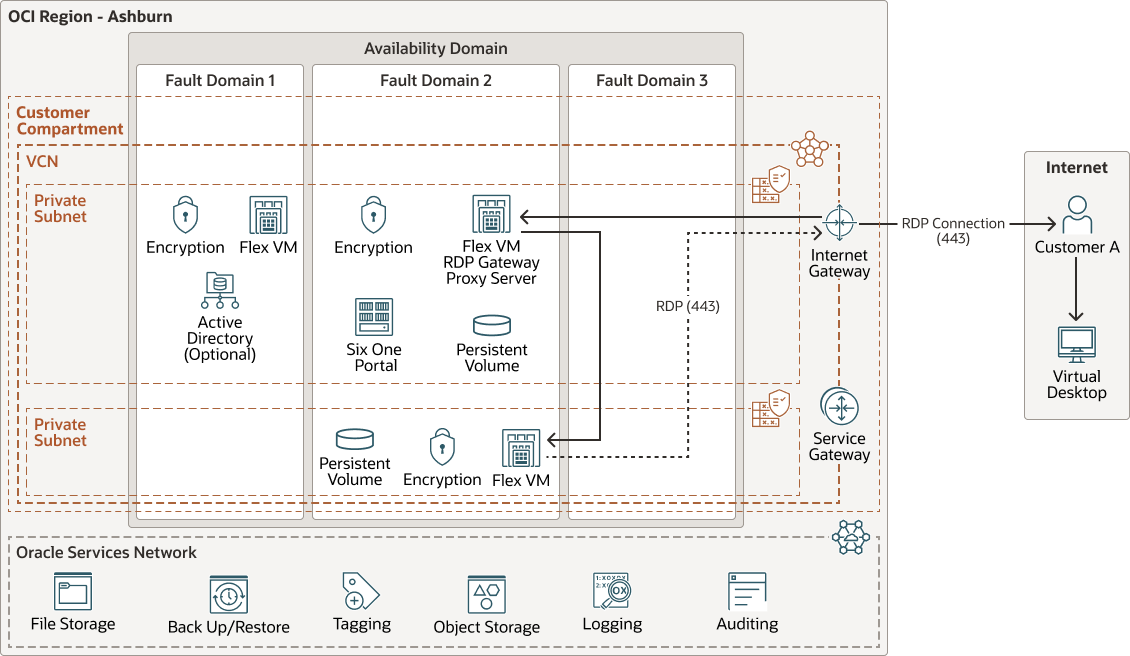
In the hybrid model, the entire infrastructure is secured and isolated within the customer's tenancy. The customer chooses a VCN in their own tenancy, and then automation is invoked by Six.One to deploy the infrastructure required to run data as a service (DaaS) from the customer tenancy. The Six.One user experience is the same whether you use Six.One VDI in a managed service model or in a hybrid model. In a hybrid deployment, customers can route VDI traffic from their OCI tenancy through OCI FastConnect to on-premises user devices, without egress charges. Instead, there is a monthly charge for all ingress and egress traffic. This can allow customers with large VDI deployments to save on egress traffic charges.
The following diagram illustrates the reference architecture for the Six.One hybrid deployment.
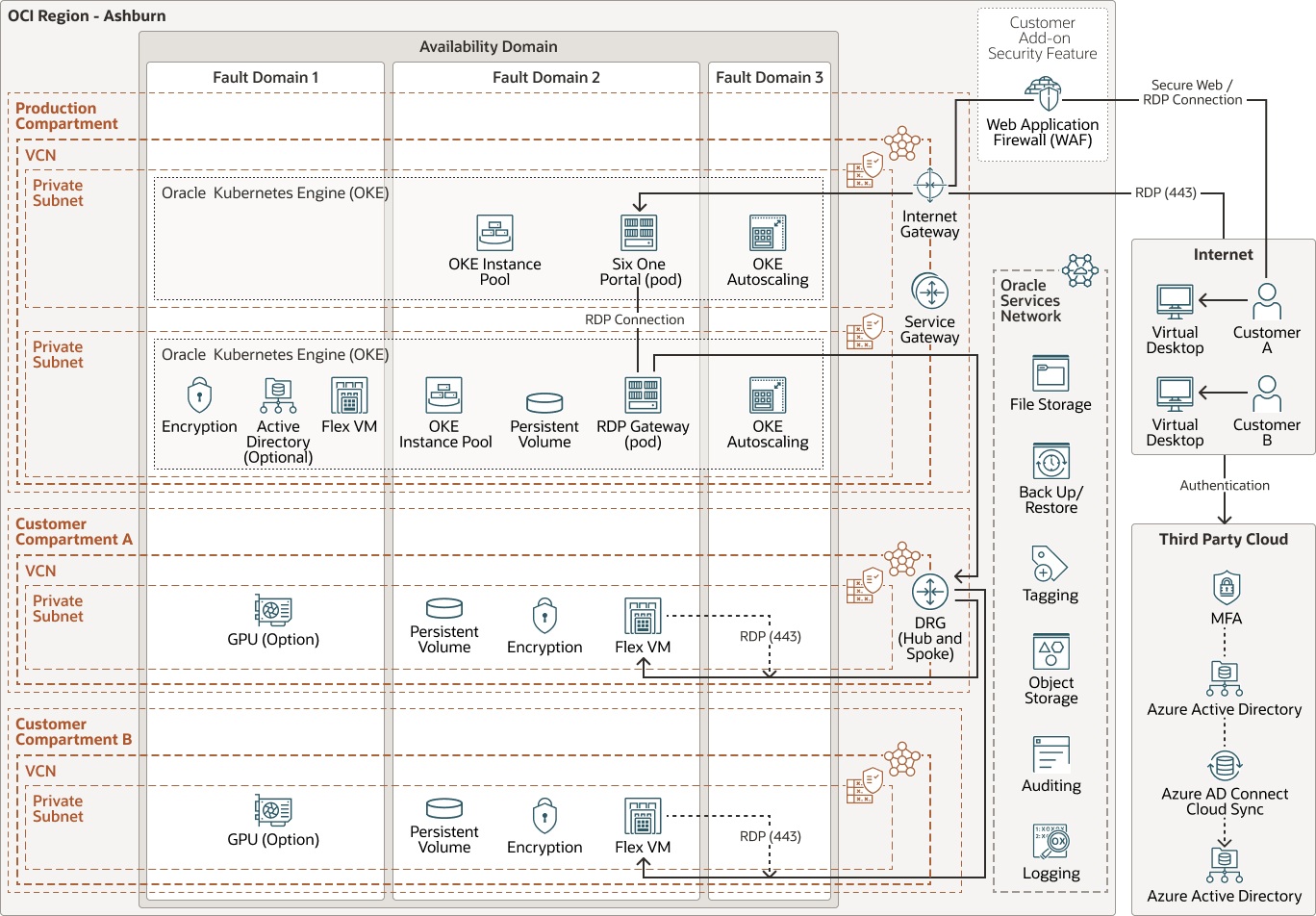
Six.One plans to enhance the current architecture. For additional scaling, Six.One plans to transform the Six.One infrastructure by using Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE). They also plan to move the RDP gateway into an OKE application. Moving services to OKE will allow Six.One to better monitor, scale, and shorten the time to market for new features and enhancements. Six.One also plans to separate and isolate customer infrastructures by compartment and VCN. This will allow for more granular configurations of the policies governing the infrastructures. To take advantage of OCI dynamic routing gateway (DRG) features, Six.One will move away from the use of local peering gateways (LPGs) and move to a hub and spoke topology for VCN connections. The Production VCN will serve as the hub and each customer VCN will be part of a spoke. A single DRG can have up to 300 local VCNs attached to it. This will allow Six.One to scale their networking to support more customers without having to create additional production infrastructure environments. As an additional security feature, customers can choose to used Oracle Cloud Infrastructure Web Application Firewall (WAF).
The following diagram illustrates the future reference architecture for the Six.One future.
The architecture has the following components:
- Tenancy
A tenancy is a secure and isolated partition that Oracle sets up within Oracle Cloud when you sign up for Oracle Cloud Infrastructure. You can create, organize, and administer your resources in Oracle Cloud within your tenancy. A tenancy is synonymous with a company or organization. Usually, a company will have a single tenancy and reflect its organizational structure within that tenancy. A single tenancy is usually associated with a single subscription, and a single subscription usually only has one tenancy.
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Fault domain
A fault domain is a grouping of hardware and infrastructure within an availability domain. Each availability domain has three fault domains with independent power and hardware. When you distribute resources across multiple fault domains, your applications can tolerate physical server failure, system maintenance, and power failures inside a fault domain.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Service gateway
The service gateway provides access from a VCN to other services, such as Oracle Cloud Infrastructure Object Storage. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- Block volume
With block storage volumes, you can create, attach, connect, and move storage volumes, and change volume performance to meet your storage, performance, and application requirements. After you attach and connect a volume to an instance, you can use the volume like a regular hard drive. You can also disconnect a volume and attach it to another instance without losing data.
- Audit
The Oracle Cloud Infrastructure Audit service automatically records calls to all supported Oracle Cloud Infrastructure public application programming interface (API) endpoints as log events. Currently, all services support logging by Oracle Cloud Infrastructure Audit.
- LoggingLogging is a highly scalable and fully managed service that provides access to the following types of logs from your resources in the cloud:
- Audit logs: Logs related to events emitted by the Audit service.
- Service logs: Logs emitted by individual services such as API Gateway, Events, Functions, Load Balancing, Object Storage, and VCN flow logs.
- Custom logs: Logs that contain diagnostic information from custom applications, other cloud providers, or an on-premises environment.
Get Featured in Built and Deployed
Want to show off what you built on Oracle Cloud Infrastructure? Care to share your lessons learned, best practices, and reference architectures with our global community of cloud architects? Let us help you get started.
- Download the template (PPTX)
Illustrate your own reference architecture by dragging and dropping the icons into the sample wireframe.
- Watch the architecture tutorial
Get step by step instructions on how to create a reference architecture.
- Submit your diagram
Send us an email with your diagram. Our cloud architects will review your diagram and contact you to discuss your architecture.