Subaru and Centroid: Migrate and Scale the MySubaru Telematics Platform on Oracle Cloud
With record numbers of drivers demanding 24/7 access to its MySubaru mobile app, the New Jersey-based car company and its managed service provider, Centroid, decided to move the application's on-premises infrastructure to Oracle Cloud Infrastructure (OCI).
From its OCI tenancy, Subaru is now able to run its Java-based in-vehicle telematics platform at scale, helping more than 2 million subscribers process hundreds of thousands of daily service requests for roadside assistance, service appointments, in-vehicle climate controls, and more. While the MySubaru app works for all Subaru models, many advanced features, such as remote start, lock, unlock, and locate can only be accessed with a Starlink Safety and Security Plus subscription.
Founded in 1968 as a subsidiary of Subaru Corporation of Japan, Subaru of America (hereafter referred to as Subaru) is headquartered in Camden New Jersey, employs ~6,000 people, and operates a zero-landfill assembly plant in Lafayette, Indiana. Subaru has 3 regional offices, 8 regional distribution offices, 12 zone offices, and more than 600 dealers across the US.
After Centroid helped move the MySubaru application's infrastructure to OCI, Subaru has been able to:
- Boost availability of its telematics services, using a two-node RAC configuration of Oracle Database Cloud Service, Oracle Data Guard, and a full replication of this infrastructure in a disaster recovery site
- Tighten security for users, databases, and the application by using firewalls, security lists, network security groups, multiple, isolated virtual cloud networks (VCNs), and public and private subnets
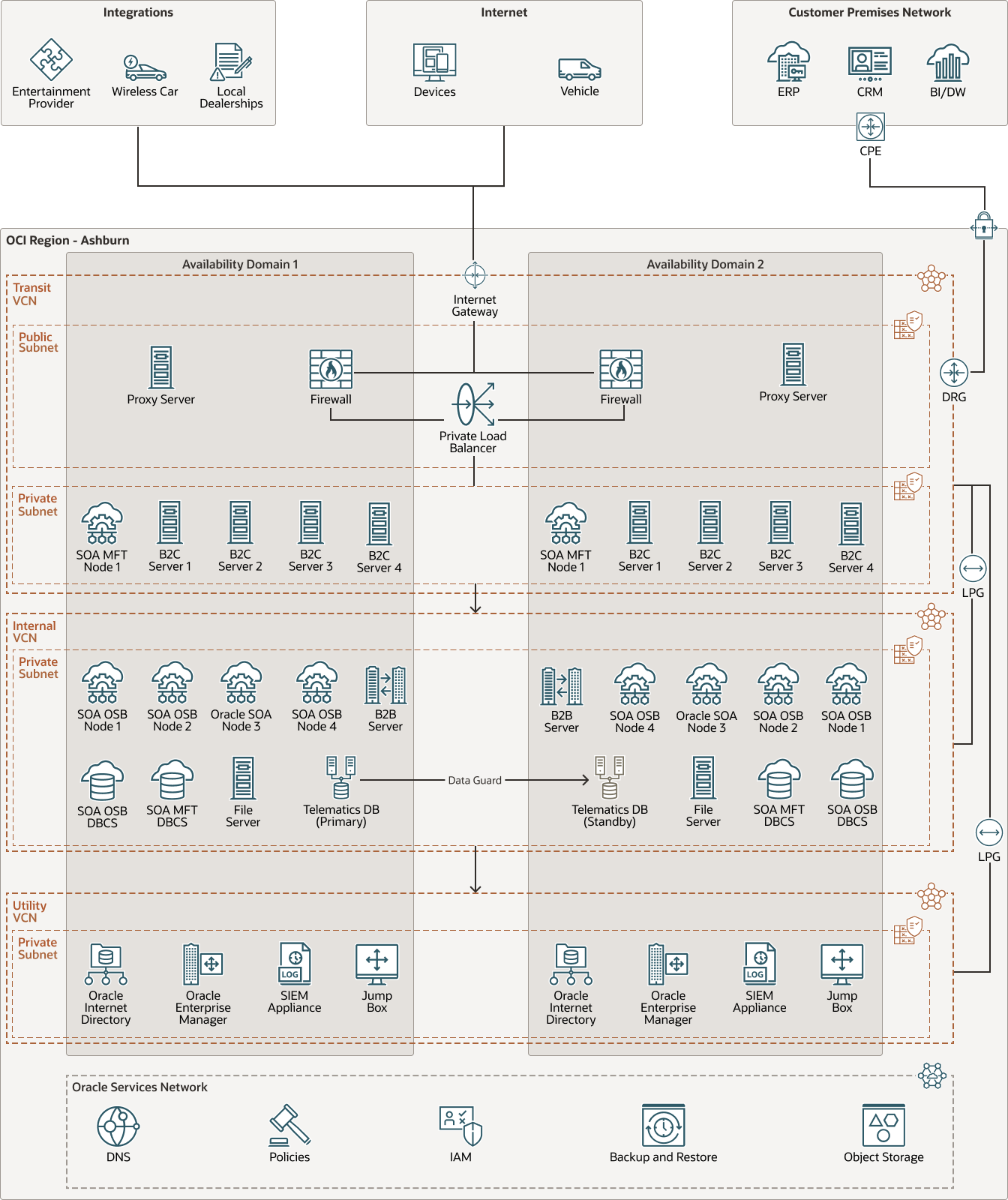
Architecture
The mobile application deployed in this architecture is supported by the open source Spring Framework, using the Oracle Java Development Kit (JDK) 8+.
The application runs on Oracle Cloud Infrastructure (OCI) in multiple availability domains (ADs): Ashburn Availability Domain 1 is the primary domain, Ashburn Availability Domain 2 is the standby domain, and Phoenix Availability Domain 1 is the disaster recovery site.
The following diagram illustrates the networking and disaster recovery architecture:
subaru-centroid-oci-arch-oracle.zip
Multiple virtual cloud networks (VCNs) isolate the network for security. The Transit VCN is used for edge network communications and contains a pair of firewalls in an active-active configuration, load balancers, backend business-to-consumer (B2C) servers, and the Oracle Service Oriented Architecture (SOA) Managed File Transfer nodes. The Internal VCN contains a private subnet and holds the Oracle SOA Service Bus (OSB) and Business Processing Execution Language (BPEL) for web services instances, business-to-business servers (B2B), and Oracle Databases. The third VCN is the Utility VCN, which handles non-application related capabilities, such as authentication and identity management provided by Oracle Internet Directory (OID), observability & management provided by Oracle Enterprise Manager (OEM), remote access (jump server), and logging (SEIM Appliance). Authentication is performed by replicating a read-only copy of user identities from Subaru's on-premises environment through the OID nodes located in VCNs in each of the availability domains. All of the authorizations are configured in the IaaS and PaaS instances.
All of these VCNs are connected with local peering gateways (LPG) in Ashburn. A hub and spoke topology is used, with the Transit VCN acting as the hub and the Internal and Utility VCNs acting as spokes. Remote peering using dynamic routing gateways (DRG) connects the Ashburn and Phoenix regions. The DR region in Phoenix mirrors the primary region by using the same configuration of VCNs connected using LPGs. IPsec tunnels are used to secure connectivity from the customer's on-premises networks to OCI, using DRGs in each of the regions.
The frontend of the application is accessed from the MySubaru website or from a driver's MySubaru app, which can be downloaded from either the App Store or Google Play. Subaru owners must first create a user account on the MySubaru website and then log in to the MySubaru app on their smart phones. A pair of firewall instances are deployed to the edge in the Transit VCN on a public subnet. To ensure high availability, these instances are configured in an active-active cluster, one in each availability domain. The firewall provides end-to-end security and real-time "defense in depth" of the infrastructure. Users access the backend by using an internet gateway in the Transit VCN. Traffic is inspected by the firewal instance, is then forwarded to an internal load balancer, and then sent to the B2C servers instances. The B2C servers run Apache Tomcat instances and support user service requests from the backend of the MySubaru app. User profiles and authentication information is stored on the OID instance, located in the Utility VCN for the mobile application app.
The telematics data collection follows the same user path from the vehicle to the B2C servers and then to the telematics database located in the Internal VCN on a private subnet. In Ashburn Availability Domain 1, the telematics database is hosted on Oracle Database Cloud Service (DBCS), using a two-node Oracle Real Application Clusters (RAC) configuration. For additional availability, the telematics database uses Oracle Data Guard to replicate to two additional standby instances, one located in Ashburn Availability Domain 2, and the other in Phoenix Availability Domain 1. To distribute the application traffic and to maintain high availability, application users are load-distributed to a region or availability domain for backend access (B2C servers) and the B2C servers use the active database in Ashburn Availability Domain 1. If the active database were to be unavailable, a standby database can then be made active in either Ashburn Availabilty Domain 2 or Phoenix Availability Domain 1. This configuration provides load distribution and high availability of backend servers and high availability for the database configured across multiple availability domains and regions. The Subaru team has successfully performed disaster recovery exercises to cover failover scenarios. OCI native backup and restore to object storage is used to maintain backups of systems.
The architecture processes millions of vendor transactions every day using the B2B servers and OCI's Oracle SOA Platform as a Service (PaaS). Oracle SOA Managed File Transfer instances and databases are deployed into each availability domain, providing Subaru with a file transfer system for managing integrations with partners and vendors. The application ecosystem integrates with partners and vendors for wireless car functions, entertainment providers, and local car dealerships.
A set of Oracle SOA and OSB nodes process data that's received from vendors and partners. These Oracle SOA components also integrate with systems that are currently hosted on-premise such as a customer relationship management (CRM) system, Oracle E-Business Suite for enterprise resource planning (ERP), and Oracle Analytics Server (OAS) for cost and usage analysis of OCI with business intelligence and data warehousing (BI/DW). The Oracle SOA components and SOA databases are then deployed into each availability domain as a standalone architecture. The Oracle SOA databases take advantage of Oracle Database Cloud Service virtual machine instances.
Developers access the system by using a jump box in the Utility VCN. A Jenkins server is deployed for push-button deployment of code. Oracle Cloud Infrastructure Identity and Access Management (IAM) and policies are used for separation of roles. Console access is restricted by policy to only those who require console access.
Systems administrators have service accounts, which limit how much compute or other resources can be consumed in the OCI tenancy. While some of Centroid's systems administrators have full root access, others are only allowed to manage the application or database, depending on their roles. Security logging information is forwarded to an alternative location for security review. There is a separate security team that monitors vulnerability scanning and performs penetration testing.
The architecture has the following components:
- Region
An Oracle Cloud Infrastructure region is a localized geographic area that contains one or more data centers, called availability domains. Regions are independent of other regions, and vast distances can separate them (across countries or even continents).
- Availability domain
Availability domains are standalone, independent data centers within a region. The physical resources in each availability domain are isolated from the resources in the other availability domains, which provides fault tolerance. Availability domains don’t share infrastructure such as power or cooling, or the internal availability domain network. So, a failure at one availability domain is unlikely to affect the other availability domains in the region.
- Identity and Access Management (IAM)
Oracle Cloud Infrastructure Identity and Access Management (IAM) is the access control plane for Oracle Cloud Infrastructure (OCI) and Oracle Cloud Applications. The IAM API and the user interface enable you to manage identity domains and the resources within the identity domain. Each OCI IAM identity domain represents a standalone identity and access management solution or a different user population.
- Policy
An Oracle Cloud Infrastructure Identity and Access Management policy specifies who can access which resources, and how. Access is granted at the group and compartment level, which means you can write a policy that gives a group a specific type of access within a specific compartment, or to the tenancy.
- DNS
Oracle Cloud Infrastructure Domain Name System (DNS) service is a highly scalable, global anycast domain name system (DNS) network that offers enhanced DNS performance, resiliency, and scalability, so that end users connect to customers’ application as quickly as possible, from wherever they are.
- Virtual cloud network (VCN) and subnets
A VCN is a customizable, software-defined network that you set up in an Oracle Cloud Infrastructure region. Like traditional data center networks, VCNs give you complete control over your network environment. A VCN can have multiple non-overlapping CIDR blocks that you can change after you create the VCN. You can segment a VCN into subnets, which can be scoped to a region or to an availability domain. Each subnet consists of a contiguous range of addresses that don't overlap with the other subnets in the VCN. You can change the size of a subnet after creation. A subnet can be public or private.
- Route table
Virtual route tables contain rules to route traffic from subnets to destinations outside a VCN, typically through gateways.
- Security list
For each subnet, you can create security rules that specify the source, destination, and type of traffic that must be allowed in and out of the subnet.
- Site-to-Site VPN
Site-to-Site VPN provides IPSec VPN connectivity between your on-premises network and VCNs in Oracle Cloud Infrastructure. The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
- Internet gateway
The internet gateway allows traffic between the public subnets in a VCN and the public internet.
- Dynamic routing gateway (DRG)
The DRG is a virtual router that provides a path for private network traffic between VCNs in the same region, between a VCN and a network outside the region, such as a VCN in another Oracle Cloud Infrastructure region, an on-premises network, or a network in another cloud provider.
- Local peering gateway (LPG)
An LPG enables you to peer one VCN with another VCN in the same region. Peering means the VCNs communicate using private IP addresses, without the traffic traversing the internet or routing through your on-premises network.
- Remote peering
Remote peering allows the VCNs' resources to communicate using private IP addresses without routing the traffic over the internet or through your on-premises network. Remote peering eliminates the need for an internet gateway and public IP addresses for the instances that need to communicate with another VCN in a different region.
- Load balancer
The Oracle Cloud Infrastructure Load Balancing service provides automated traffic distribution from a single entry point to multiple servers in the back end.
- Data Guard
Oracle Data Guard provides a comprehensive set of services that create, maintain, manage, and monitor one or more standby databases to enable production Oracle databases to remain available without interruption. Oracle Data Guard maintains these standby databases as copies of the production database. Then, if the production database becomes unavailable because of a planned or an unplanned outage, Oracle Data Guard can switch any standby database to the production role, minimizing the downtime associated with the outage.
- Compute
The Oracle Cloud Infrastructure Compute service enables you to provision and manage compute hosts in the cloud. You can launch compute instances with shapes that meet your resource requirements for CPU, memory, network bandwidth, and storage. After creating a compute instance, you can access it securely, restart it, attach and detach volumes, and terminate it when you no longer need it.
- Object storage
Object storage provides quick access to large amounts of structured and unstructured data of any content type, including database backups, analytic data, and rich content such as images and videos. You can safely and securely store and then retrieve data directly from the internet or from within the cloud platform. You can seamlessly scale storage without experiencing any degradation in performance or service reliability. Use standard storage for "hot" storage that you need to access quickly, immediately, and frequently. Use archive storage for "cold" storage that you retain for long periods of time and seldom or rarely access.
- SOA with SB and Oracle B2B
Oracle Service Bus (SB) and Oracle B2B are service types of Oracle SOA Suite.
Oracle Service Bus connects, mediates, and manages interactions between heterogeneous services, not just Web services, but also Java and .Net, messaging services and legacy endpoints.
Oracle B2B is an e-commerce gateway that enables the secure and reliable exchange of business documents between an enterprise and its trading partners. Oracle B2B supports business-to-business document standards, security, transports, messaging services, and trading partner management. With Oracle B2B used as a binding component within an Oracle SOA Suite composite application, end-to-end business processes can be implemented.
You can provision Oracle B2B with the SOA with SB & B2B Cluster service type.
- Oracle Managed File Transfer (MFT)
Oracle MFT is a high performance, standards-based, end-to-end managed file gateway. It features design, deployment, and monitoring of file transfers using a lightweight web-based design-time console that includes transfer prioritization, file encryption, scheduling, and embedded FTP and sFTP servers.
You can provision Oracle MFT with the MFT Cluster service type.
- Oracle Database Cloud Service
Oracle Database Cloud Service lets you easily build, scale, and secure Oracle databases in the cloud. You create databases on DB Systems, as a virtual machines with block volumes, both of which provide high performance and cost-efficient pricing. The service also enables support for 'cloud-first' Oracle RAC implementation on virtual machine servers at the virtual cloud network layer.
Get Featured in Built and Deployed
Want to show off what you built on Oracle Cloud Infrastructure? Care to share your lessons learned, best practices, and reference architectures with our global community of cloud architects? Let us help you get started.
- Download the template (PPTX)
Illustrate your own reference architecture by dragging and dropping the icons into the sample wireframe.
- Watch the architecture tutorial
Get step by step instructions on how to create a reference architecture.
- Submit your diagram
Send us an email with your diagram. Our cloud architects will review your diagram and contact you to discuss your architecture.
Explore More
Learn more about the features of this architecture and about related architectures.