36 Configuring WS-Security
This chapter describes how to set up WS-Security for WebCenter Portal and Portal Framework applications and related services and components based on your topology.
This chapter covers the following configurations:
-
A simple topology, with the WebCenter Portal or Portal Framework applications and all components sharing the same domain
-
A typical topology, with the WebCenter Portal or Portal Framework applications and components divided across two domains
-
A complex topology, with the WebCenter Portal or Portal Framework applications and components divided across multiple domains
Within these three topologies, configuration is described for the WebCenter Portal or Portal Framework applications, discussions, worklists, and WSRP producers. These configurations and the steps for securing applications consuming the WebCenter Portal API are covered in the following sections:
-
Section 36.1, "Configuring WS-Security for a Simple Topology"
-
Section 36.2, "Configuring WS-Security for a Typical Topology"
-
Section 36.3, "Configuring WS-Security for a Complex Topology"
Permissions:
To perform the tasks in this chapter, you must be granted the WebLogic ServerAdmin role through the Oracle WebLogic Server Administration Console. Users with the Monitor or Operator roles can view security information but cannot make changes.
See also, Section 1.8, "Understanding Administrative Operations, Roles, and Tools."
36.1 Configuring WS-Security for a Simple Topology
This section describes how to configure WS-Security for a topology where the WebCenter Portal and Portal Framework applications, the BPEL server, and WSRP producers share the same domain (Figure 36-1).
Figure 36-1 WS-Security for a Simple Configuration
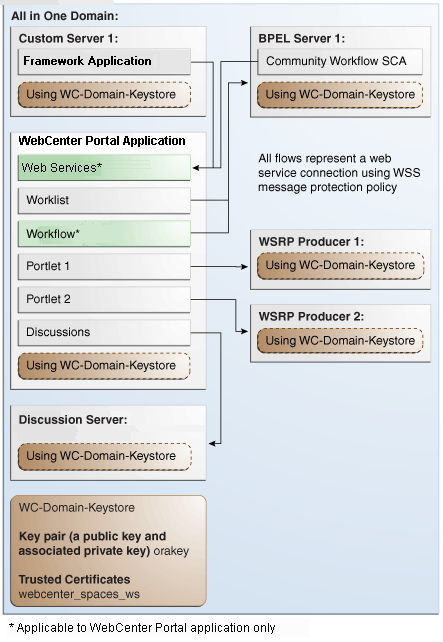
Description of ''Figure 36-1 WS-Security for a Simple Configuration''
The steps to configure WS-Security for a simple single-domain topology are described in the following sections:
-
Section 36.1.1, "Roadmap to Configuring WS-Security for a Simple Topology"
-
Section 36.1.2, "Setting Up the WebCenter Portal Domain Keystore"
-
Section 36.1.3, "Configuring the Discussions Server for a Simple Topology"
36.1.1 Roadmap to Configuring WS-Security for a Simple Topology
The flow chart (Figure 36-1) and table (Table 36-1) in this section provide an overview of the prerequisites and tasks required to configure WS-Security for a simple single-domain topology.
Figure 36-2 Configuring WS-Security for a Simple Topology
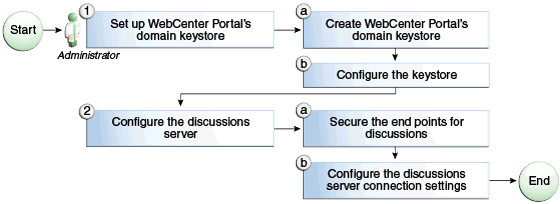
Description of ''Figure 36-2 Configuring WS-Security for a Simple Topology''
Table 36-1 shows the tasks and sub-tasks to configure WS-Security for a simple topology.
36.1.2 Setting Up the WebCenter Portal Domain Keystore
The security credentials of the WebCenter Portal application, discussions server, BPEL server, and WSRP producers can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See Security and Administrator's Guide for Web Services for information about JKS.
This section contains the following subsections:
-
Section 36.1.2.1, "Creating the WebCenter Portal Domain Keystore"
-
Section 36.1.2.3, "Configuring the Keystore Using Fusion Middleware Control"
36.1.2.1 Creating the WebCenter Portal Domain Keystore
This section describes how to create a keystore and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create the WebCenter Portal domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias orakey -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer. This can be any string as long as it's in the correct format (for example,cn=spaces,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystoreis the keystore name, (for example,default-keystore.jks) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias orakey -keystore keystore -storepass keystore_password -rfc -file orakey.cer
Where:
-
keystoreis the keystore name, (for example,default-keystore.jks) -
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the certificate with the alias
webcenter_spaces_ws(choose Yes when prompted whether to overwrite the existing certificate with the aliasorakey):keytool -importcert -alias webcenter_spaces_ws -file orakey.cer -keystore default-keystore.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
-
Continue by configuring the keystore using either WLST as described in Section 36.1.2.2, "Configuring the Keystore with WLST," or using Fusion Middleware Control as described in Section 36.1.2.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 36-2 shows the keystore contents you should wind up with after creating and configuring the keystore.
Table 36-2 Portal Domain Keystore Contents for a Simple Topology
Key Alias Description orakeyKey pair used to sign and encrypt outbound messages from WebCenter Portal. This key is used by both OWSM (portlets and worklist) and discussions.
webcenter_spaces_wsCertificate containing the public key for the
orakeyprivate key used in the WebCenter Portal domain. The certificate is used to encrypt outbound Web service messages from the workflow application on BPEL Server1 in the WebCenter Portal domain, to the Web service API on WebCenter Portal domain.
36.1.2.2 Configuring the Keystore with WLST
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either Fusion Middleware control, as described in Section 36.1.2.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the credential store:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider:<serviceInstance name="keystore" provider="keystore.provider" location="./default-keystore.jks"> <description>Default JPS Keystore Service</description> -
Make sure that the
default-keystore.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and that the location is specified as./default-keystore.jks:<serviceInstance name="keystore" provider="keystore.provider" location="./default-keystore.jks"> <description>Default JPS Keystore Service</description> -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password=keystore_password, desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="orakey", password=private_key_password, desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="orakey", password=private_key_password, desc="Signing key")
Where:
-
keystore_passwordis the keystore password specified in step 2 of Section 36.1.2.1, "Creating the WebCenter Portal Domain Keystore," (for example,MyPassword) -
private_key_passwordis the private key password specified in step 2 of Section 36.1.2.1, "Creating the WebCenter Portal Domain Keystore," (for example,MyPassword)
Example 36-4 Updating the Credential Store
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="orakey", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="orakey", password="MyPassword", desc="Signing key")
-
-
Restart all servers.
36.1.2.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either WLST, as described in Section 36.1.2.2, "Configuring the Keystore with WLST," or using Fusion Middleware control as described below.
To configure the keystore provider:
-
Ensure that the
default-keystore.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./default-keystore.jks. -
Open Fusion Middleware Control and log in to the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter Portal domain (
wc_domainby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays.
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./default-keystore.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
orakey -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
orakey -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.1.3 Configuring the Discussions Server for a Simple Topology
In a simple topology, the discussions server is in the same domain as the WC_Spaces server and consequently no extra keystore configuration is needed since the keystore configured for the WebCenter Portal domain is used for the discussions as well. However, for production environments you should protect the discussions Web service endpoints with an OWSM policy and configure the discussions server connection settings. These configuration steps are described in the following subsections:
Note:
Discussions-specific Web services messages sent by WebCenter Portal and Portal Framework applications to the discussions server are not encrypted. For message confidentiality, the discussions server URL must be accessed over Secure Socket Layer (SSL). For more information, see Chapter 35, "Configuring SSL."36.1.3.1 Attaching Security Policies for WebCenter Portal and Discussions Web Service Endpoints
In a new or patched WebCenter Portal instance, the assigned security policy configuration is set to "no security policy." You must attach Oracle Web Services Manager (OWSM) security policies for the WebCenter Portal Web service endpoint and the discussions authenticated Web service endpoint. For a production environment, continue by hardening the security by following the steps in Section 36.1.3.2, "Securing the Discussions End Points."
Note:
In a patched WebCenter Portal instance, you must determine the policy names before you patch, then attach the policies after you patch. For required steps, see the "Patching Oracle WebCenter Portal" section in Patching Guide.To attach the Web service security policy configuration in a new instance:
Note:
For clustered environments, repeat these steps for each of the managed servers where WebCenter Portal and discussions are deployed.-
Ensure that the
WC_SpacesandWC_Collaborationmanaged servers are running. -
Run the following WLST command to attach an OWSM policy on the WebCenter Portal Web service endpoint:
attachWebServicePolicy(application='webcenter', moduleName='webcenter', moduleType='web', serviceName='SpacesWebService', subjectName='SpacesWebServiceSoapHttpPort', policyURI='oracle/wss11_saml_token_with_message_protection_service_policy')
-
Run the following WLST command to attach an OWSM policy on the discussions Web service endpoint:
attachWebServicePolicy(application='owc_discussions', moduleName='owc_discussions', moduleType='web', serviceName='OWCDiscussionsServiceAuthenticated', subjectName='OWCDiscussionsServiceAuthenticated', policyURI='oracle/wss10_saml_token_service_policy')
-
Restart the
WC_SpacesandWC_Collaborationmanaged servers.
36.1.3.2 Securing the Discussions End Points
The discussions Web service endpoints require user identity to be propagated for calls originating from WebCenter Portal. For a production environment, the Web service endpoints must be secured with OWSM policies to ensure that messages are not tampered with, and can't be viewed by others while in transit. To do this, both the public access Web service endpoint and authenticated user access endpoint should be secured with the appropriate OWSM policies using either Fusion Middleware Control or WLST.
This section contains the following subsections:
-
Section 36.1.3.2.1, "Securing the Discussions Server End Points Using Fusion Middleware Control"
-
Section 36.1.3.2.2, "Securing the Discussions Server End Points Using WLST"
36.1.3.2.1 Securing the Discussions Server End Points Using Fusion Middleware Control
To secure the discussions end points using Fusion Middleware Control, follow the steps below:
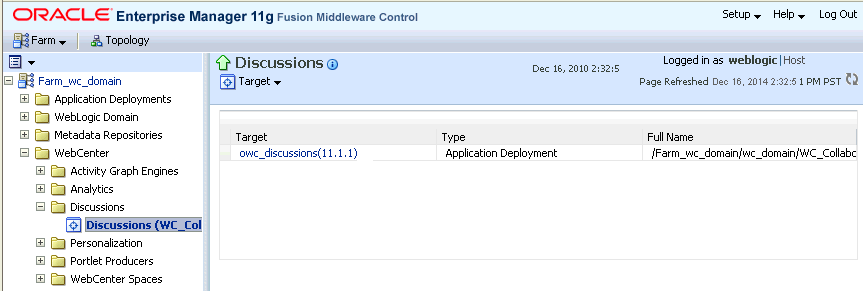
-
Log in to Fusion Middleware Control and from the Navigation pane, expand WebCenter> Portal> Discussions and click
Discussions(WC_Collaboration).The discussions home page displays (see Figure 36-3).
-
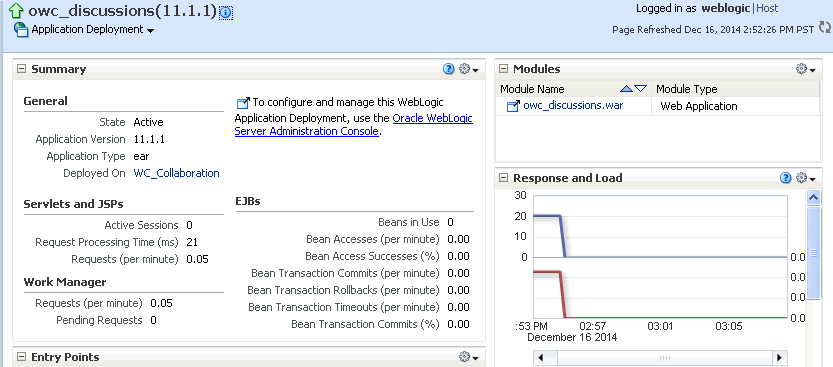
Click the
owc_discussionstarget.The home page for the
owc_discussionsapplication displays (see Figure 36-4). -
From the Application Deployment menu, select Web Services.
The Web Services page for the
owc_discussionsapplication displays (see Figure 36-5).Figure 36-5 Web Services Page for owc_discussions
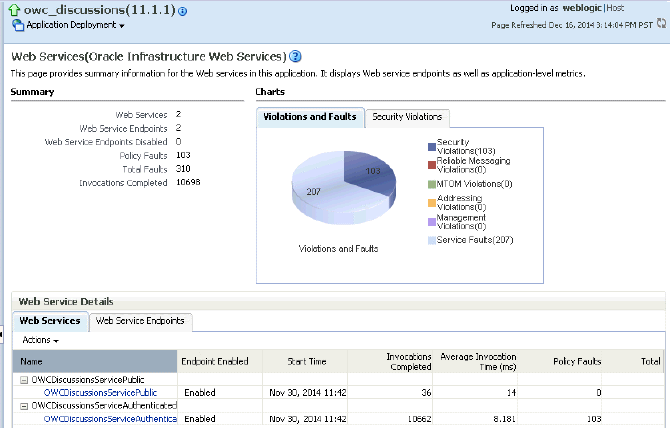
Description of ''Figure 36-5 Web Services Page for owc_discussions''
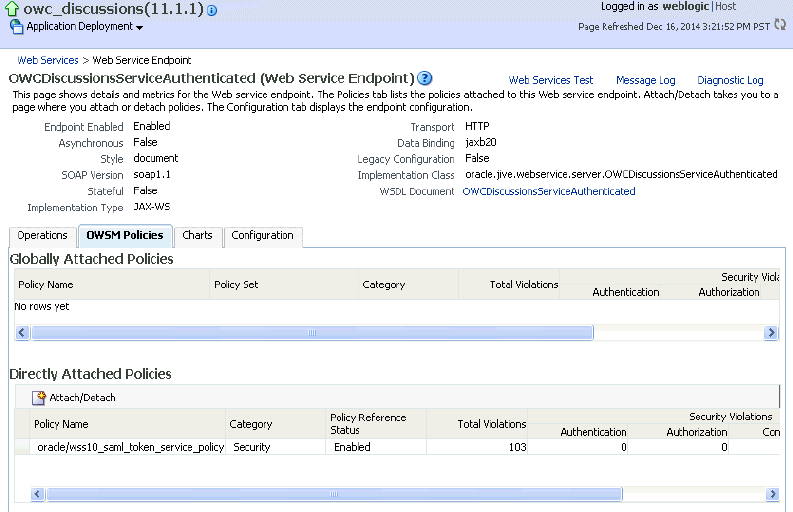
-
Open the Web Services tab, and click the
OWCDiscussionsServiceAuthenticatedWeb Service end point.The Web Service Endpoint page for owc_discussions displays (see Figure 36-6).
-
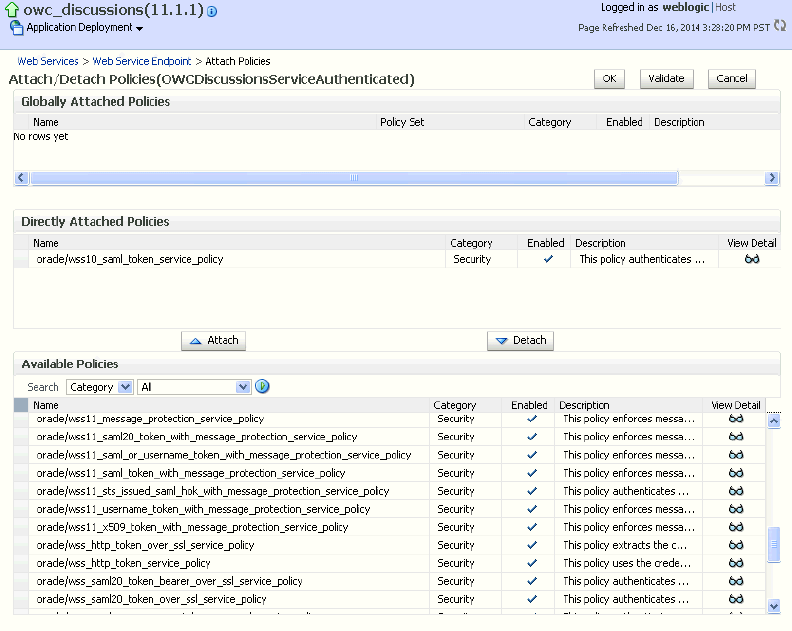
Click Attach/Detach.
The Attach Policy page displays (see Figure 36-7).
-
Use the Attach and Detach buttons to attach
oracle/wss11_saml_token_with_message_protection_service_policyand detachoracle/wss10_saml_token_service_policy. -
Click OK.
36.1.3.2.2 Securing the Discussions Server End Points Using WLST
To secure the discussions server endpoints using WLST, detach the wss10_saml_token_service_policy and attach the wss11_saml_token_with_message_protection_service_policy using the following WLST commands:
detachWebServicePolicy(application='owc_discussions', moduleName='owc_discussions', moduleType='web', serviceName='OWCDiscussionsServiceAuthenticated', subjectName='OWCDiscussionsServiceAuthenticated', policyURI='oracle/wss10_saml_token_service_policy')
attachWebServicePolicy(application='owc_discussions', moduleName='owc_discussions', moduleType='web', serviceName='OWCDiscussionsServiceAuthenticated', subjectName='OWCDiscussionsServiceAuthenticated', policyURI='oracle/wss11_saml_token_with_message_protection_service_policy')
36.1.3.3 Configuring the Discussions Server Connection Settings
You must supply the WS-Security client certificate information within the discussions server connection that is configured for your WebCenter Portal or Portal Framework application, as described in Section 12.3, "Registering Discussions Servers." Figure 36-8 shows example connection detail settings for the Edit Discussions and Announcement Connection page.
Figure 36-8 Edit Discussions and Announcement Connection Page
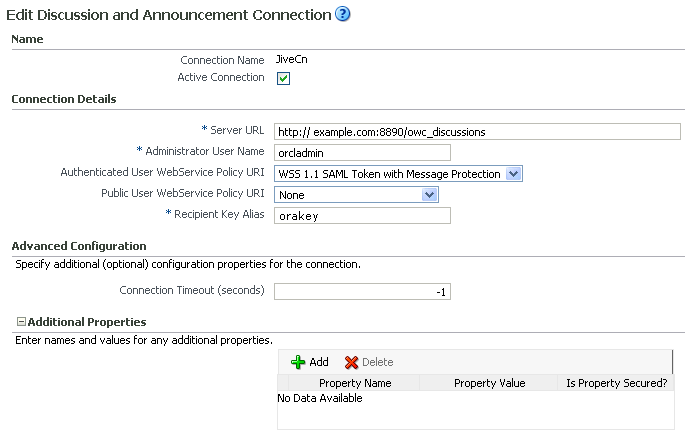
Description of ''Figure 36-8 Edit Discussions and Announcement Connection Page''
36.1.4 Command Summary for a Simple Topology
Use the following command summary to quickly configure the keystore for a simple topology.
Use the following keytool commands to generate the keystore, replacing the values in bold with those for your local environment:
keytool -genkeypair -keyalg RSA -dname "cn=spaces,dc=example,dc=com" -alias orakey
-keypass MyPassword -keystore default-keystore.jks -storepass MyPassword -validity 1064
keytool -exportcert -v -alias orakey -keystore default-keystore.jks -storepass MyPassword -rfc -file orakey.cer
keytool -importcert -alias webcenter_spaces_ws -file orakey.cer
-keystore default-keystore.jks -storepass MyPassword
When prompted that the certificate already exists, say yes.
keytool -importcert -alias df_orakey_public -file orakey.cer -keystore owc_discussions.jks -storepass MyPassword
Copy the default-keystore.jks file to your domain_home/config/fmwconfig directory.
Using WLST, connect to the WebCenter Portal domain as an administrator and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="orakey", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="orakey", password="MyPassword", desc="Signing key")
36.2 Configuring WS-Security for a Typical Topology
This section describes how to configure WS-Security for a topology where the WebCenter Portal application and the WSRP producers share the same domain, but the BPEL server is in an external domain - the SOA domain (see Figure 36-9).
Figure 36-9 WS-Security for a Typical Configuration
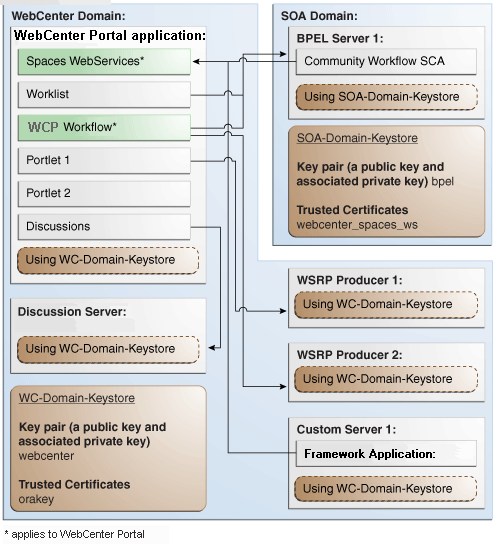
Description of ''Figure 36-9 WS-Security for a Typical Configuration''
The steps to configure WS-Security for a typical two domain topology are described in the following sections:
-
Section 36.2.1, "Roadmap to Configuring WS-Security for a Typical Topology"
-
Section 36.2.2, "Setting Up the WebCenter Portal Domain Keystore"
-
Section 36.2.3, "Configuring the Discussions Server for a Typical Topology"
36.2.1 Roadmap to Configuring WS-Security for a Typical Topology
The flow chart (Figure 36-10) and table (Table 36-3) in this section provide an overview of the prerequisites and tasks required to configure WS-Security for a typical two domain topology.
Figure 36-10 Configuring WS-Security for a Typical Topology

Description of ''Figure 36-10 Configuring WS-Security for a Typical Topology''
Table 36-3 shows the tasks and sub-tasks to configure WS-Security for a typical two domain topology.
36.2.2 Setting Up the WebCenter Portal Domain Keystore
The security credentials of a WebCenter Portal application, discussions server, BPEL server (in a separate domain), and WSRP producers can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See Security and Administrator's Guide for Web Services for information about JKS.
This section contains the following subsections:
-
Section 36.2.2.1, "Creating the WebCenter Portal Domain Keystore"
-
Section 36.2.2.3, "Configuring the Keystore Using Fusion Middleware Control"
36.2.2.1 Creating the WebCenter Portal Domain Keystore
This section describes how to create a keystore and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create the WebCenter Portal domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias webcenter -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=spaces,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias webcenter -keystore keystore -storepass keystore_password -rfc -file webcenter_public.cer
Where:
-
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Continue by configuring the keystore using either WLST, as described in Section 36.2.2.2, "Configuring the Keystore Using WLST," or Fusion Middleware Control, as described in Section 36.2.2.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 36-4 shows the keystore contents you should wind up with after creating and configuring the keystore.
Table 36-4 WebCenter Portal Domain Keystore Contents for a Typical Topology
Key Alias Description webcenterKey pair used to sign and encrypt outbound messages from WebCenter Portal. This key is used by both OWSM (portlets and worklist) and discussions.
orakeyCertificate containing the public key for the
BPELprivate key used in the SOA domain. The certificate is used to encrypt outbound Web service messages from the workflow application on BPEL Server1 in the WebCenter Portal domain, to the worklist component to the SOA server on the SOA domain.
36.2.2.2 Configuring the Keystore Using WLST
After creating the WebCenter Portal domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this either using Fusion Middleware Control, as described in Section 36.2.2.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password=keystore_password, desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password=private_key_password, desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password=private_key_password, desc="Signing key")
Where:
-
keystore_passwordis the keystore password specified in step 2 of Section 36.2.2.1, "Creating the WebCenter Portal Domain Keystore," (for example,MyPassword) -
private_key_passwordis the private key password specified in step 2 of Section 36.2.2.1, "Creating the WebCenter Portal Domain Keystore," (for example,MyPassword)
Example 36-7 Updating the Credential Store
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="MyPassword", desc="Signing key")
-
-
Restart all servers.
36.2.2.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this either using WLST, as described in Section 36.2.2.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter Portal domain (
wc_domainby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays.
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./webcenter.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
webcenter -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
webcenter -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.2.3 Configuring the Discussions Server for a Typical Topology
Configuring the discussions server for a typical topology is exactly the same as for a simple topology. For more information, see Section 36.1.3, "Configuring the Discussions Server for a Simple Topology."
36.2.4 Setting Up the SOA Domain
This section describes how to set up the SOA domain keystore and contains the following subsections:
36.2.4.1 Creating the SOA Domain Keystore
This section describes how to create a SOA domain keystore and keys using a Java Keystore (JKS).
To create the SOA domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Create a keystore by importing the public certificate (
webcenter_public.cer) from the WebCenter Portal domain:keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass keystore_password
Where:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Using keytool, create a keypair to be used in the SOA domain for signing and encrypting messages:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias bpel -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=bpel,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystoreis the keystore name, (for example,bpel.jks) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate so it can be imported in the WebCenter Portal domain using the
orakeyalias:keytool -exportcert -v -alias bpel -keystore keystore -storepass keystore_password -rfc -file orakey.cer
Where:
-
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the certificate with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
orakey):keytool -importcert -alias orakey -file orakey.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
36.2.4.2 Configuring the Keystore Using WLST
After creating the SOA domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this either with Fusion Middleware Control, as described in Section 36.2.4.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
bpel.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./bpel.jks. -
Use the following WLST commands to configure the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.2.4.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this either with WLST, as described in Section 36.2.4.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the SOA domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the SOA domain.
-
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays.
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./bpel.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
bpel -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
bpel -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.2.5 Command Summary for a Typical Topology
Use the following command summary to quickly configure the keystore for a typical topology.
Use the following keytool commands to generate the keystore, replacing the values in bold with those for your local environment:
keytool -genkeypair -keyalg RSA -dname "cn=spaces,dc=example,dc=com" -alias
webcenter -keypass MyPassword -keystore webcenter.jks -storepass MyPassword -validity 1064
keytool -exportcert -v -alias webcenter -keystore webcenter.jks
-storepass MyPassword -rfc -file webcenter_public.cer
keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer
-keystore bpel.jks -storepass MyPassword
When prompted that the certificate already exists, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=bpel,dc=example,dc=com" -alias bpel
-keypass MyPassword -keystore bpel.jks -storepass MyPassword -validity 1024
keytool -exportcert -v -alias bpel -keystore bpel.jks -storepass MyPassword
-rfc -file orakay.cer
keytool -importcert -alias orakey -file orakay.cer -keystore webcenter.jks
-storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -importcert -alias df_webcenter_public -file webcenter_public.cer -keystore owc_discussions.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
Copy the webcenter.jks file to your domain_home/config/fmwconfig directory, and the bpel.jks file to your soa_domain_home/config/fmwconfig directory.
Configure the WebCenter Portal Domain Keystore
Follow the steps below to configure the service instance reference for the WebCenter Portal domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
webcenter.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./webcenter.jks. -
Using WLST, connect to the WebCenter Portal domain as an admin user and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="MyPassword", desc="Signing key")
Configure the SOA Domain Keystore
Follow the steps below to configure service instance reference for the SOA domain:
-
Navigate to the
<SOA_DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
bpel.jksto the<SOA_DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./bpel.jks. -
Using WLST, connect to the SOA domain as an admin user and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="MyPassword", desc="Signing key")
36.3 Configuring WS-Security for a Complex Topology
This section describes how to configure WS-Security for a complex topology where the WebCenter Portal application, the discussions server, and a WSRP producer are in the same domain, two BPEL servers are in separate SOA domains, and one WSRP producer is in an external portlet domain (see Figure 36-11).
Figure 36-11 WS-Security for a Complex Configuration
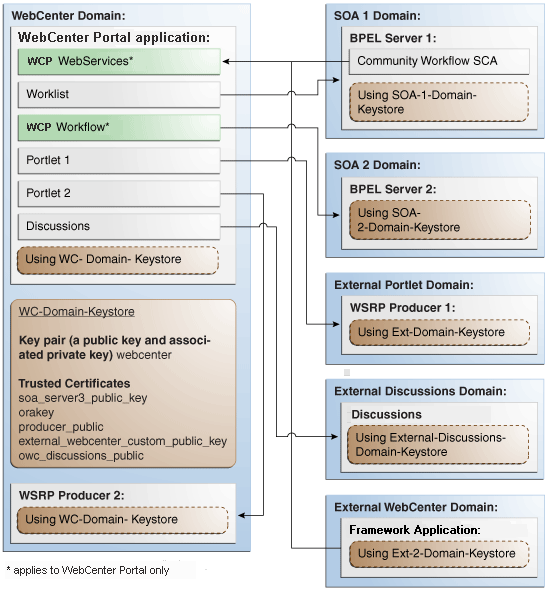
Description of ''Figure 36-11 WS-Security for a Complex Configuration''
The steps to configure WS-Security for a complex topology with multiple domains are described in the following sections:
-
Section 36.3.1, "Roadmap to Configuring WS-Security for a Complex Topology"
-
Section 36.3.2, "Setting Up the WebCenter Portal Domain Keystores"
-
Section 36.3.3, "Configuring the Discussions Server for a Complex Topology"
-
Section 36.3.6, "Setting Up the External Portlet Domain Keystore"
-
Section 36.3.7, "Setting Up the External WebCenter Domain Keystore"
36.3.1 Roadmap to Configuring WS-Security for a Complex Topology
The flow chart (Figure 36-12) and table (Table 36-5) in this section provide an overview of the prerequisites and tasks required to configure WS-Security for a complex multiple-domain topology.
Figure 36-12 Configuring WS-Security for a Complex Topology
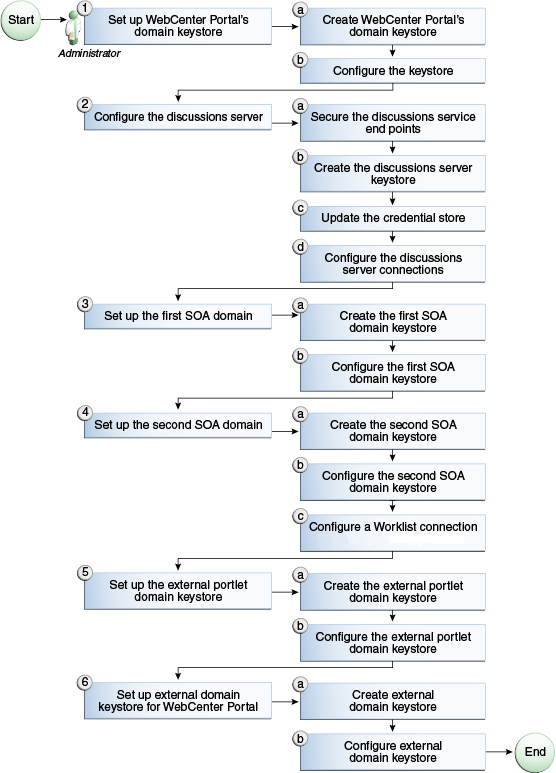
Description of ''Figure 36-12 Configuring WS-Security for a Complex Topology''
Table 36-5 shows the tasks and sub-tasks to configure WS-Security for a complex topology.
Table 36-5 Configuring WS-Security for a Complex Topology
| Actor | Task | Sub-task | Notes |
|---|---|---|---|
|
Administrator |
|||
|
. |
|||
|
. |
|||
|
6.b Configure external domain keystore for the Portal Framework application |
36.3.2 Setting Up the WebCenter Portal Domain Keystores
The security credentials of WebCenter Portal, discussions server, BPEL servers (in separate domains), and WSRP producers (also in separate domains) can be retrieved and managed using a Java Keystore (JKS). A keystore is a file that provides information about available public and private keys. Keys are used for a variety of purposes, including authentication and data integrity. User certificates and the trust points needed to validate the certificates of peers are also stored securely in the wallet or keystore. See Security and Administrator's Guide for Web Services for information about JKS.
This section contains the following subsections:
-
Section 36.3.2.1, "Creating the WebCenter Portal Domain and Framework Keystores"
-
Section 36.3.2.3, "Configuring the Keystore Using Fusion Middleware Control"
36.3.2.1 Creating the WebCenter Portal Domain and Framework Keystores
This section describes how to create the keystores and keys using a Java Keystore (JKS). JKS is the proprietary keystore format defined by Sun Microsystems. To create and manage the keys and certificates in the JKS, use the keytool utility that is distributed with the Java JDK 6.
To create the WebCenter Portal domain and Framework keystores:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair for the
webcenterkeystore:keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias webcenter -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=spaces,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias webcenter -keystore wecenter.jks -storepass keystore_password -rfc -file webcenter_public.cerWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the
orakeycertificate:keytool -importcert -alias orakey -file orakey.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Continue by configuring the keystore using either WLST, as described in Section 36.3.2.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control, as described in Section 36.3.2.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 36-6 shows the keystore contents you should wind up with after creating and configuring the keystore.
Table 36-6 WebCenter Portal Domain Keystore Contents for a Complex Topology
Key Alias Description webcenterKey pair used to sign and encrypt outbound messages from WebCenter Portal. This key is used by both OWSM (portlets and worklist) and discussions.
orakeyCertificate containing the public key for the
BPELprivate key used in the SOA 1 domain. The certificate is used to encrypt outbound messages from the worklist component to SOA_Server3 in the SOA 1 domain.soa_server3_public_keyCertificate containing the public key for the soa_server3 private key used in the SOA 2 domain. The certificate is used to encrypt outbound messages from the worklist component to BPEL Server2 in SOA 2 domain.
producer_public_keyCertificate containing public key for the producer private key used in the external portlet domain that hosts the WSRP Producer 1 application. This certificate is used to encrypt outbound messages from WebCenter Portal to WSRP Producer 1 registered in the WebCenter Portal application.
external_webcenter_custom_public_keyCertificate containing the public key for the external_webcenter_custom private key used in the external WebCenter domain that hosts the Portal Framework application that makes Web service calls to the WebCenter Portal Web service. This certificate is used to encrypt outbound messages from WebCenter Portal to Portal Framework applications in the external WebCenter domain.
owc_discussions_publicCertificate containing public key for the external owc_discussions private key used in the external discussions domain that hosts discussions. This certificate is used by WebCenter Portal and Portal Framework applications make Web service calls to the discussions Web service.
36.3.2.2 Configuring the Keystore Using WLST
After creating the WebCenter Portal domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for thekeystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.3.2.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter Portal domain (
wc_domainby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
The Security Provider Configuration page displays (see Figure 36-13).
Figure 36-13 Security Provider Configuration Page
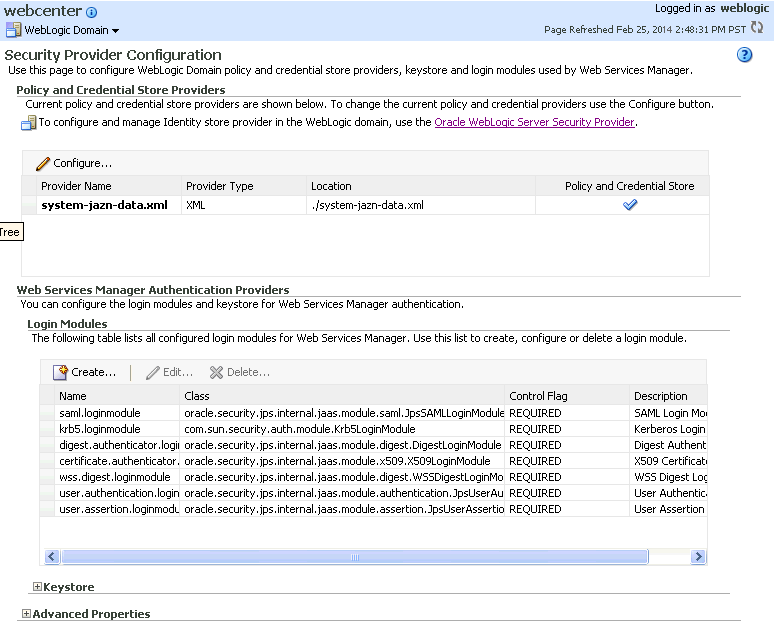
Description of ''Figure 36-13 Security Provider Configuration Page''
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 36-14).
Figure 36-14 Keystore Configuration Page
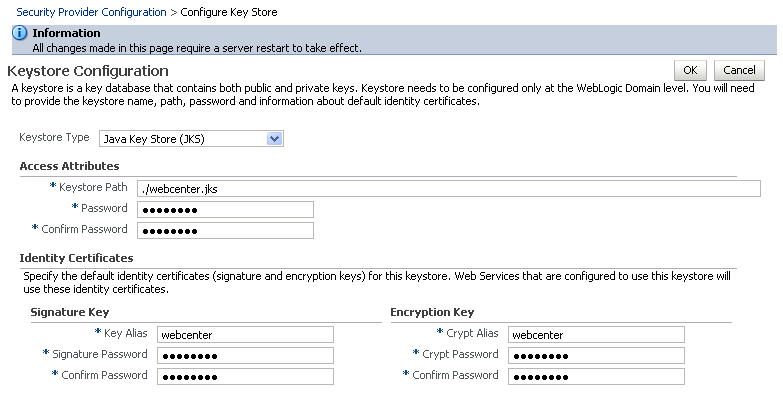
Description of ''Figure 36-14 Keystore Configuration Page''
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./webcenter.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
webcenter -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
webcenter -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.3.3 Configuring the Discussions Server for a Complex Topology
In a complex topology, the discussions server is in a different domain than WebCenter Portal and consequently you will need to create and configure a keystore for the discussions server and export the certificate containing the public key and import it into the WebCenter Portal domain. For production environments you will also need to protect the discussions Web service end points with an OWSM policy and configure the discussions server connection settings. These configuration steps are described in the following subsections:
-
Section 36.3.3.1, "Securing the Discussions Service End Points"
-
Section 36.3.3.2, "Creating the Discussions Server Keystore"
-
Section 36.3.3.4, "Configuring the Discussions Server Connection Settings"
Note:
Discussions-specific Web service messages sent by Portal Framework applications to the discussions server are not encrypted. For message confidentiality, the discussions server URL must be accessed over Secure Socket Layer (SSL). For more information, see Chapter 35, "Configuring SSL."36.3.3.1 Securing the Discussions Service End Points
The discussions Web service end points require user identity to be propagated for calls originating from WebCenter Portal. Follow the steps in Section 36.1.3.2, "Securing the Discussions End Points" to secure the endpoints using either Fusion Middleware Control or WLST.
36.3.3.2 Creating the Discussions Server Keystore
This section describes how to create a keystore for the discussions server that contains the key pair used by OWSM, and export the certificate containing the public key so it can be imported into the WebCenter Portal domain.
To create the owc_discussions keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate a key pair for the
owc_discussionskeystore:keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias owc_discussions -keypass key_password -keystore keystore -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=owc_discussions,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystoreis the keystore name, (for example,owc_discussions.jks) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate containing the public key:
keytool -exportcert -v -alias owc_discussions -keystore owc_discussions.jks -storepass keystore_password -rfc -file owc_discussions_public.cerWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the
webcenter_publiccertificate:keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore owc_discussions.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the
owc_discussions_publiccertificate:keytool -importcert -alias owc_discussions_public -file owc_discussions_public.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Continue by updating the credential store using WLST as described in Section 36.3.3.3, "Updating the Credential Store."
36.3.3.3 Updating the Credential Store
After creating the WebCenter Portal domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for thekeystore.providerProvider:<!-- KeyStore Service Instance --> <serviceInstance name="keystore" provider="keystore.provider" location="./default-keystore.jks"> <description>Default JPS Keystore Service</description> -
Make sure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks.<serviceInstance name="keystore" provider="keystore.provider" location="./webcenter.jks"> <description>Default JPS Keystore Service</description> -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="owc_discussions", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="owc_discussions", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.3.3.4 Configuring the Discussions Server Connection Settings
You must supply the WS-Security client certificate information within the discussions server connection that is configured for WebCenter Portal or your Portal Framework application, as described in Section 12.3, "Registering Discussions Servers." Figure 36-15 shows example connection detail settings for the Edit Discussions and Announcement Connection page.
Figure 36-15 Edit Discussions and Announcement Connection Page

Description of ''Figure 36-15 Edit Discussions and Announcement Connection Page''
36.3.4 Setting Up the First SOA Domain
This section describes how to set up the SOA domain keystore and contains the following subsections:
36.3.4.1 Creating the SOA Domain Keystore
This section describes how to create a SOA domain keystore and keys using a Java Keystore (JKS).
To create the SOA domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Create a keystore by importing the public certificate (
webcenter_public.cer) from the WebCenter Portal domain:keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Using keytool, create a keypair to be used in the SOA domain for signing and encrypting messages:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias bpel -keypass key_password -keystore bpel.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=bpel,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate so it can be imported in the WebCenter Portal domain using the
orakeyalias:keytool -exportcert -v -alias bpel -keystore bpel.jks -storepass keystore_password -rfc -file orakey.cerWhere:
-
keystore_passwordis the keystore password (for example,MyPassword)
-
-
Import the certificate to the WebCenter Portal domain again with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
orakey):keytool -importcert -alias orakey -file orakey.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,MyPassword)
-
-
Import the certificate to the into the SOA domain:
keytool -importcert -alias soa_server3_public_key -file soa_server3_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,MyPassword)
-
-
Continue by configuring the keystore using either WLST, as described in Section 36.3.4.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described in Section 36.3.4.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 36-7 shows the keystore contents you should wind up with after creating and configuring the SOA 1 domain keystore.
Table 36-7 SOA 1 Domain Keystore Contents for a Complex Topology
Key Alias Description bpelPrivate key used to sign outbound messages from the SOA 1 domain servers. This key is used by the Worklist application deployed on the SOA 1 domain's SOA server.
webcenter_spaces_wsCertificate containing the public key for the
webcenterprivate key used in the WebCenter Portal domain. The certificate is used to encrypt outbound workflow messages on BPEL Server1 in the SOA 1 domain to Web service API on the WebCenter Portal domain.
36.3.4.2 Configuring the Keystore Using WLST
After creating the SOA domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either Fusion Middleware Control, as described in Section 36.3.4.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
bpel.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./bpel.jks. -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.3.4.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either WLST, as described in Section 36.3.4.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the SOA domain.
-
From the SOA Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 36-16).
Figure 36-16 Keystore Configuration Page
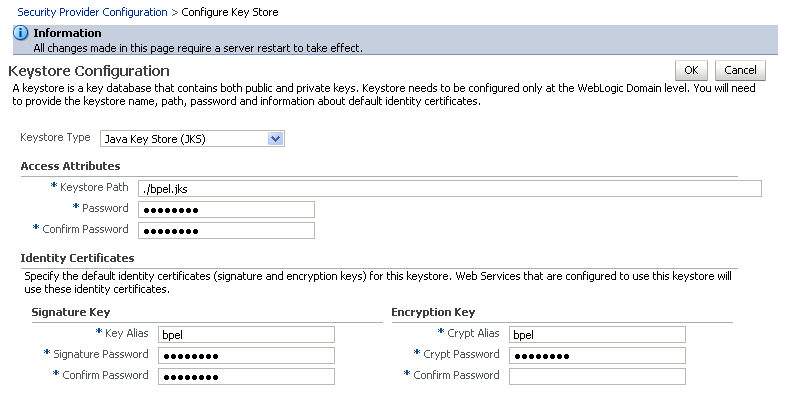
Description of ''Figure 36-16 Keystore Configuration Page''
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./bpel.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
bpel -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
bpel -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.3.5 Setting Up the Second SOA Domain
This section describes how to set up a second SOA domain keystore and contains the following subsections:
-
Section 36.3.5.3, "Configuring the Keystore Using Fusion Middleware Control"
-
Section 36.3.5.4, "Configuring the Worklist Connection for the Second SOA Server"
36.3.5.1 Creating the SOA Domain Keystore
This section describes how to create a SOA domain keystore and keys using a Java Keystore (JKS).
To create the SOA domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, create a keypair to be used in the SOA domain for signing and encrypting messages:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias soa_server3 -keypass key_password -keystore soa_server3.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=soa_server3,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate so it can be imported in the WebCenter Portal domain using the
orakeyalias:keytool -exportcert -v -alias soa_server3 -keystore soa_server3.jks -storepass keystore_password -rfc -file soa_server3_public_key.cerWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the certificate to the WebCenter Portal domain with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
soa_server3_public_key):keytool -importcert -alias soa_server3_public_key -file soa_server3_public_ key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,MyPassword)
-
-
Import the
soa_server3_public_keycertificate:keytool -importcert -alias soa_server3_public_key -file soa_server3_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the
producer_public_keycertificate:keytool -importcert -alias producer_public_key -file producer_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the
external_webcenter_custom_public_keycertificate:keytool -importcert -alias external_webcenter_custom_public_key -file external_webcenter_custom_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Continue by configuring the keystore using either WLST, as described in Section 36.3.5.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described in Section 36.3.5.3, "Configuring the Keystore Using Fusion Middleware Control."
Table 36-8 shows the keystore contents you should wind up with after creating and configuring the SOA 2 domain keystore.
Table 36-8 SOA 2 Domain Keystore Contents for a Complex Topology
Key Alias Description webcenterKey pair used to sign and encrypt outbound messages from WebCenter Portal. This key is used by both OWSM (portlets and worklist) and discussions.
orakeyCertificate containing the public key for the
BPELprivate key used in the SOA 1 domain. The certificate is used to encrypt outbound messages from the worklist component to SOA_Server3 in the SOA 1 domain.soa_server3_public_keyCertificate containing the public key for the soa_server3 private key used in the SOA 2 domain. The certificate is used to encrypt outbound messages from the worklist component to BPEL Server2 in SOA 2 domain.
producer_public_keyCertificate containing public key for the producer private key used in the external portlet domain that hosts the WSRP Producer 1 application. This certificate is used to encrypt outbound messages from WebCenter Portal to WSRP Producer 1 registered in the WebCenter Portal application.
external_webcenter_custom_public_keyCertificate containing the public key for the external_webcenter_custom private key used in the external WebCenter domain that hosts the Portal Framework application that makes Web service calls to the WebCenter Portal Web service. This certificate is used to encrypt outbound messages from WebCenter Portal to Portal Framework applications in the external WebCenter domain.
36.3.5.2 Configuring the Keystore Using WLST
After creating the second SOA domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either Fusion Middleware Control, as described in Section 36.3.5.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
soa_server3.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./soa_server3.jks. -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="soa_server3", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="soa_server3", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.3.5.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either WLST, as described in Section 36.3.5.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the SOA domain.
-
From the SOA Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 36-17).
Figure 36-17 Keystore Configuration Page
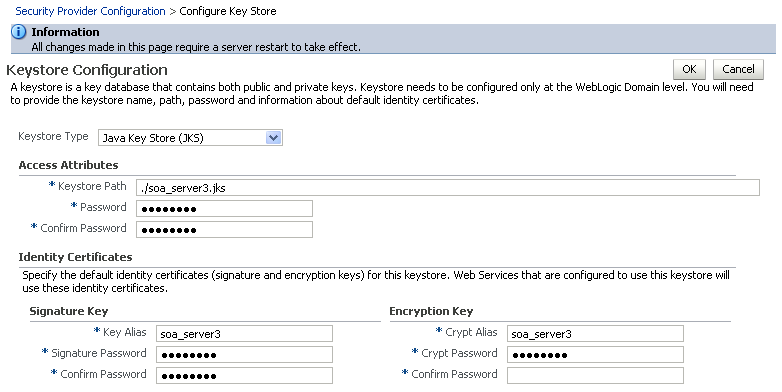
Description of ''Figure 36-17 Keystore Configuration Page''
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./soa_server3.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
soa_server3 -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
soa_server3 -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.3.5.4 Configuring the Worklist Connection for the Second SOA Server
Ordinarily, the worklist connection uses the oracle/wss10_saml_token_with_message_protection_client_policy policy to secure outbound SOAP messages to SOA Server. However, in a complex deployment where the WebCenter Portal domain uses two or more worklist connections simultaneously we need to create an additional OWSM policy and configure it so that the recipient key alias matches the alias of the certificate of the intended SOA server on the WebCenter Portal side.
Follow the steps below to use multiple worklist connections simultaneously:
-
Export the certificate from the external SOA domain and import it into the WebCenter Portal domain under a new alias (
soa_server3_keyin the following example). -
Use Fusion Middleware Control to create a new OWSM policy, and override the recipient key alias to use the same alias as above.
-
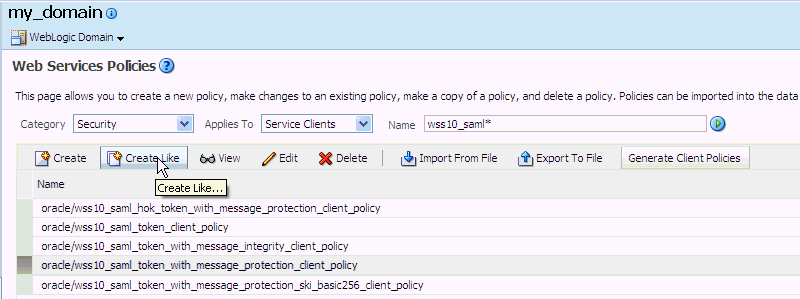
In Fusion Middleware Control, from the WebLogic domain menu select Web Services -> Policies.
The Web Services Policies page displays (see Figure 36-18).
-
Select a client policy to use as a base for creating the new policy and click Create Like.
The Create Policy page displays (see Figure 36-19).
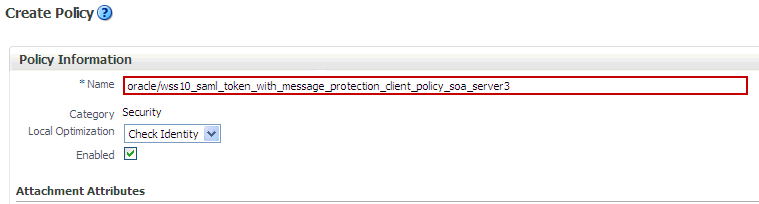
-
Enter a name for the new policy (for example,
oracle_wss10_saml_token_with_message_protection_client_policy_soa_server3) and click Save.The new policy should now be listed on the Web Services Policies page.
-
From the Web Services Policy page, select the new policy and click Edit.
-
On the Edit Policy page, open the Configuration tab and click Edit.
-
Override the recipient key alias with the value
soa_server3_keyand click Save.
-
-
Create the BPEL connection to set the security policy to the policy created above using the following WLST command:
setBPELConnection(appName='webcenter', name='WebCenter-Worklist-SOAServer3',url='<your_url>', policy='oracle/wss10_saml_token_with_message_protection_client_policy_soa_server3')
36.3.6 Setting Up the External Portlet Domain Keystore
This section describes how to set up the keystore for the external portlet domain used by one of the WSRP producers for this complex topology.
This section contains the following subsections:
-
Section 36.3.6.1, "Creating the External Portlet Domain Keystore"
-
Section 36.3.6.3, "Configuring the Keystore Using Fusion Middleware Control"
36.3.6.1 Creating the External Portlet Domain Keystore
To create the external portlet domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate the keystore by importing the WebCenter Portal domain's public certificate:
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore producer.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
-
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias producer -keypass key_password -keystore producer.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=producer,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystoreis the keystore name, (for example,webcenter.jks) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate containing the public key so that it can be imported into the WebCenter Portal domain's keystore:
keytool -exportcert -v -alias producer -keystore producer.jks -storepass keystore_password -rfc -file producer_public_key.cerWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the certificate to the WebCenter Portal domain with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias
producer_public_key):keytool -importcert -alias producer_public_key -file producer_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,MyPassword)
-
-
Continue by configuring the keystore using either WLST as described in Section 36.3.6.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described in Section 36.3.6.3, "Configuring the Keystore Using Fusion Middleware Control."
36.3.6.2 Configuring the Keystore Using WLST
After creating the external portlet domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either Fusion Middleware Control, as described in Section 36.3.6.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
producer.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./producer.jks. -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="producer", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="producer", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.3.6.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either WLST, as described in Section 36.3.6.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log in to the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter Portal domain (
wc_domainby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 36-20).
Figure 36-20 Keystore Configuration Page
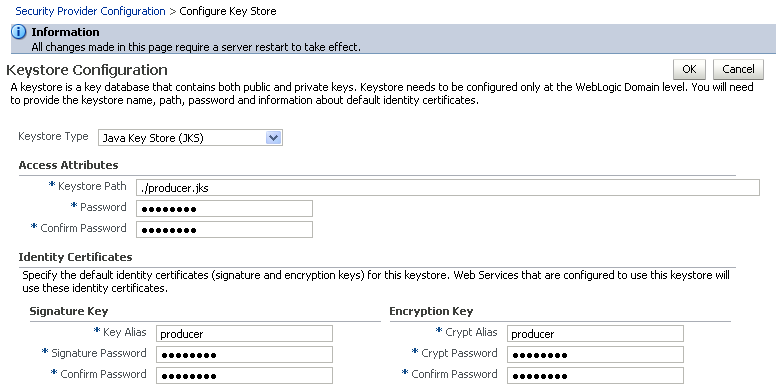
Description of ''Figure 36-20 Keystore Configuration Page''
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./producer.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
producer -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
producer -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.3.7 Setting Up the External WebCenter Domain Keystore
This section describes how to set up an external WebCenter domain used by a Portal Framework application making WebCenter Portal Web service calls.
This section contains the following subsections:
-
Section 36.3.7.1, "Creating the External WebCenter Domain Keystore"
-
Section 36.3.7.3, "Configuring the Keystore Using Fusion Middleware Control"
36.3.7.1 Creating the External WebCenter Domain Keystore
To create the external WebCenter domain keystore:
-
Go to
JDK_HOME/jdk/binand open a command prompt. -
Using keytool, generate the keystore by importing the WebCenter domain's public certificate:
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore external_webcenter_custom.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password
-
-
Using keytool, generate a key pair:
keytool -genkeypair -keyalg RSA -dname "consumer_dname" -alias external_webcenter_custom -keypass key_password -keystore external_webcenter_custom.jks -storepass keystore_password -validity days_valid
Where:
-
consumer_dnameis the name of the consumer (for example,cn=external_webcenter_custom,dc=example,dc=com) -
key_passwordis the password for the new public key, (for example,MyPassword) -
keystore_passwordis the keystore password, (for example,MyPassword) -
days_validis the number of days for which the key password is valid (for example,1064).
Note:
You must use the-keyalgparameter and specifyRSAas its value as shown above as the default algorithm (DSA) used bykeytoolfor generating the key is incompatible with Oracle Web Services Security Manager requirements. -
-
Export the certificate containing the public key so that it can be imported into the WebCenter Portal domain's keystore:
keytool -exportcert -v -alias external_webcenter_custom -keystore external_ webcenter_custom.jks -storepass keystore_password -rfc -file external_ webcenter_custom_public_key.cerWhere:
-
keystore_passwordis the keystore password, (for example,MyPassword)
-
-
Import the certificate to the WebCenter Portal domain with a different alias (choose Yes when prompted whether to overwrite the existing certificate with the alias external_webcenter_custom_public_key):
keytool -importcert -alias external_webcenter_custom_public_key -file external_webcenter_custom_public_key.cer -keystore webcenter.jks -storepass keystore_passwordWhere:
-
keystore_passwordis the keystore password (for example,MyPassword)
-
-
Continue by configuring the keystore using either WLST as described in Section 36.3.7.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described in Section 36.3.7.3, "Configuring the Keystore Using Fusion Middleware Control."
36.3.7.2 Configuring the Keystore Using WLST
After creating the external WebCenter domain keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either Fusion Middleware Control, as described in Section 36.3.7.3, "Configuring the Keystore Using Fusion Middleware Control," or using WLST as described below.
To configure the keystore service:
-
Go to the
<DOMAIN_HOME>/config/fmwconfigdirectory, and open the filejps-config.xmlin an editor. -
Locate the
<serviceInstancenode for the keystore.providerProvider -
Ensure that the
webcenter.jkskeystore file is copied to the<DOMAIN_HOME>/config/fmwconfigdirectory, and then specify the location as./webcenter.jks. -
Use the following WLST commands to update the credential store:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="external_webcenter_custom", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="external_webcenter_custom", password="MyPassword", desc="Signing key")
-
Restart all servers.
36.3.7.3 Configuring the Keystore Using Fusion Middleware Control
After creating the keystore, configure the keystore service and update the credential store so that OWSM can read the keystore and keys correctly. You can do this using either WLST, as described in Section 36.3.7.2, "Configuring the Keystore Using WLST," or using Fusion Middleware Control as described below.
To configure the keystore provider:
-
Open Fusion Middleware Control and log into the WebCenter Portal domain.
For information on logging in to Fusion Middleware Control, see Chapter 6, "Starting Enterprise Manager Fusion Middleware Control."
-
In the Navigation pane, expand the WebLogic Domain node and click the WebCenter Portal domain (
wc_domainby default). -
From the WebLogic Domain menu, select Security -> Security Provider Configuration.
-
Expand the Keystore section on the Security Provider Configuration page.
-
Click Configure.
The Keystore Configuration page displays (see Figure 36-21).
Figure 36-21 Keystore Configuration Page
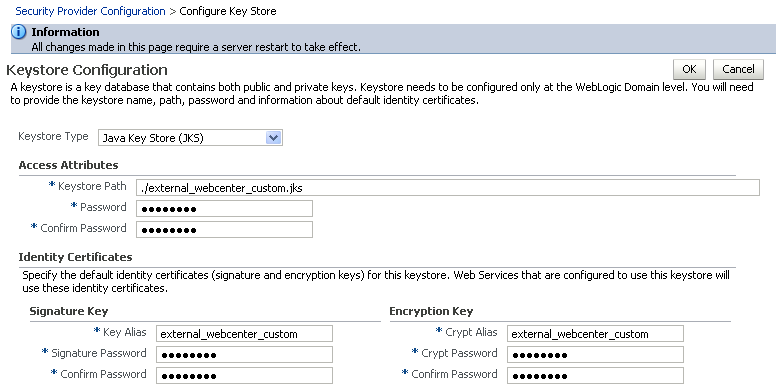
Description of ''Figure 36-21 Keystore Configuration Page''
-
Use the following settings to specify the location of the keystore that contains the certificate and private key, and the signature key and encryption key aliases:
-
Keystore Path:
./external_webcenter_custom.jks -
Password: Enter and confirm the password for the keystore.
-
Key Alias:
external_webcenter_custom -
Signature Password: Enter and confirm the password for the signature key.
-
Crypt Alias:
external_webcenter_custom -
Crypt Password: Enter and confirm the password for the encryption key.
-
-
Click OK to save your settings.
-
Restart the Administration server for the domain.
36.3.8 Command Summary for a Complex Topology
Use the following command summary to quickly configure the keystore and DF properties for a complex topology.
Use the following keytool commands to generate the keystore, replacing the values in bold with those for your local environment:
keytool -genkeypair -keyalg RSA -dname "cn=spaces,dc=example,dc=com" -alias
webcenter -keypass MyPassword -keystore webcenter.jks -storepass MyPassword -validity 1064
keytool -exportcert -v -alias webcenter -keystore webcenter.jks -storepass
MyPassword -rfc -file webcenter_public.cer
keytool -importcert -alias df_webcenter_public -file webcenter_public.cer
-keystore owc_discussions.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -importcert -alias webcenter_spaces_ws -file webcenter_public.cer -keystore bpel.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=bpel,dc=example,dc=com" -alias bpel
-keypass MyPassword -keystore bpel.jks
keytool -exportcert -v -alias bpel -keystore bpel.jks -storepass MyPassword -rfc -file orakay.cer
keytool -importcert -alias orakey -file orakay.cer -keystore webcenter.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=soa_server3,dc=example,dc=com" -alias
soa_server3 -keypass MyPassword -keystore soa_server3.jks -storepass MyPassword
-validity 1024
keytool -exportcert -v -alias soa_server3 -keystore soa_server3.jks -storepass
MyPassword -rfc -file soa_server3_public_key.cer
keytool -importcert -alias soa_server3_public_key -file soa_server3_public_key.cer
-keystore webcenter.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -importcert -alias webcenter_public -file webcenter_public.cer -keystore producer.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=producer,dc=example,dc=com" -alias
producer -keypass MyPassword -keystore producer.jks -storepass MyPassword -validity 1024
keytool -exportcert -v -alias producer -keystore producer.jks
-storepass MyPassword -rfc -file producer_public_key.cer
keytool -importcert -alias webcenter_public -file webcenter_public.cer
-keystore external_webcenter_custom.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -genkeypair -keyalg RSA -dname "cn=external_webcenter_custom,dc=example,dc=com"
-alias external_webcenter_custom -keypass MyPassword -keystore external_webcenter_custom.jks
-storepass MyPassword -validity 1024
keytool -exportcert -v -alias external_webcenter_custom -keystore
external_webcenter_custom.jks -storepass MyPassword -rfc -file
external_webcenter_custom_public_key.cer
keytool -importcert -alias producer_public_key -file producer_public_key.cer
-keystore webcenter.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
keytool -importcert -alias external_webcenter_custom_public_key -file external_webcenter_custom_public_key.cer -keystore webcenter.jks -storepass MyPassword
When prompted to trust the certificate, say yes.
Copy webcenter.jks to your domain_home/config/fmwconfig directory, bpel.jks to your SOA1_domain_home/config/fmwconfig directory, soa_server3.jks to your SOA_2_domain_home/config/fmwconfig directory, producer.jks to your External_Portlet_domain_home/config/fmwconfig directory, and external_webcenter_custom.jks to your External_WebCenter_domain_home/config/fmwconfig directory.
Configure the WebCenter Portal Domain Keystore
Follow the steps below to configure the service instance reference for the WebCenter Portal domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
webcenter.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./webcenter.jks. -
Using WLST, connect to the WebCenter Portal domain as an administrator and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="webcenter", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="webcenter", password="MyPassword", desc="Signing key")
Configure the External Discussions Server Domain Keystore
Follow the steps below to configure the service instance reference for the discussions server:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
webcenter.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./owc_discussions.jks. -
Using WLST, connect to the WebCenter Portal domain as an administrator and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="owc_discussions", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="owc_discussions", password="MyPassword", desc="Signing key")
Configure the SOA1 Domain Keystore
Follow the steps below to configure the service instance reference for the SOA1 domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
bpel.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./bpel.jks. -
Using WLST, connect to the SOA1 domain as an admin user and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="bpel", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="bpel", password="MyPassword", desc="Signing key")
Configure the SOA2 Domain Keystore
Follow the steps below to configure the service instance reference for the SOA2 domain:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory. -
Copy
soa_server3.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./soa_server3.jks. -
Using WLST, connect to the SOA2 domain as an admin user and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="soa_server3", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="soa_server3", password="MyPassword", desc="Signing key")
Configure the External Portlet Producer Domain Keystore
Follow the steps below to configure the service instance reference for the External Portlet Producer and External WebCenter domain keystores:
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory of the External Portlet Producer domain. -
Copy
producer.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./producer.jks. -
Using WLST, connect to the External Portlet Producer domain as an administrator and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="producer", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="producer", password="MyPassword", desc="Signing key")
-
Navigate to the
<DOMAIN_HOME>/config/fmwconfigdirectory of the External WebCenter domain. -
Copy
producer.jksto the<DOMAIN_HOME>/config/fmwconfigdirectory if you haven't done already done so. -
Open
jps-config.xmlin an editor. -
Locate
<serviceInstance node for keystore.provider Provider. -
Specify the location as
./external_webcenter_custom.jks. -
Using WLST, connect to the External Portlet Producer domain as an administrator and run the following commands:
updateCred(map="oracle.wsm.security", key="keystore-csf-key", user="owsm", password="MyPassword", desc="Keystore key") updateCred(map="oracle.wsm.security", key="enc-csf-key", user="external_webcenter_custom", password="MyPassword", desc="Encryption key") updateCred(map="oracle.wsm.security", key="sign-csf-key", user="external_webcenter_custom", password="MyPassword", desc="Signing key")
Configure the Discussions Server Connection
Supply the WS-Security client certificate information within the discussions server connection that is configured for WebCenter Portal or your Portal Framework application, as described in Section 12.3, "Registering Discussions Servers." Also see Section 36.3.3.4, "Configuring the Discussions Server Connection Settings" for example connection detail settings for the Edit Discussions and Announcement Connection page.
36.4 Securing WebCenter Portal for Applications Consuming WebCenter Portal Client API with WS-Security
This section describes the administrator tasks required to configure WS-Security for WebCenter Portal so that the communication between the an application exposing the WebCenter Portal API (the consumer) and WebCenter Portal (the producer) is secure, and that the identity of the user invoking the API is protected.
For information about the developer tasks for developing applications that consume the WebCenter Portal client API, see the "How to Set Up Your Framework Application to Use the WebCenter Portal API" section in Developing Portals with Oracle WebCenter Portal and Oracle JDeveloper.
This section includes the following subsections:
36.4.1 Configuring a Simple Topology for Applications Consuming WebCenter Portal Client API
If your client application is part of the same domain as WebCenter Portal, you only need to specify the following for the GroupSpaceWSContext():
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("orakey");
If your client application is JDeveloper and you have access to the WebCenter Portal server's configured keystore, copy the same keystore to JDeveloper's DefaultDomain/config/fmwconfig/dir and configure the JDeveloper domain to use this keystore. The steps here would be exactly same as those in Section 36.1.2.2, "Configuring the Keystore with WLST," and you would then also need to specify the following on your client stub:
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("orakey");
36.4.2 Configuring a Typical Topology for Applications Consuming WebCenter Portal Client API
If your client application is part of the same domain as WebCenter Portal, you only need to specify the following for the GroupSpaceWSContext():
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("webcenter");
If your client application is JDeveloper and you have access to the WebCenter Portal server's configured keystore, copy the same keystore to JDeveloper's DefaultDomain/config/fmwconfig/dir and configure the JDeveloper domain to use this keystore. The steps here would be exactly same as those in Section 36.2.2.2, "Configuring the Keystore Using WLST," and you would then also need to specify the following on your client stub:
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("webcenter");
36.4.3 Configuring a Complex Topology for Applications Consuming WebCenter Portal Client API
If your client application is part of the same domain as WebCenter Portal, you only need to specify the following for the GroupSpaceWSContext():
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("webcenter");
If your client application is JDeveloper, copy the same keystore to JDeveloper's DefaultDomain/config/fmwconfig/dir and configure the JDeveloper domain to use this keystore. The steps here would be exactly same as those in Section 36.3.2.2, "Configuring the Keystore Using WLST," and you would then also need to specify the following on your client stub:
GroupSpaceWSContext context = new GroupSpaceWSContext();
context.setRecipientKeyAlias("webcenter");