46 Enabling Security with Policies and Message Encryption
This chapter includes the following sections:
46.1 Introduction to Policies
Oracle Fusion Middleware uses a policy-based model to manage and secure Web services across an organization. Policies apply security to the delivery of messages. Policies can be managed by both developers in a design-time environment and system administrators in a runtime environment.
Policies are comprised of one or more assertions. A policy assertion is the smallest unit of a policy that performs a specific action. Policy assertions are executed on the request message and the response message, and the same set of assertions is executed on both types of messages. The assertions are executed in the order in which they appear in the policy.
Table 46-1 describes the supported policy categories.
Table 46-1 Supported Policy Categories
| Category | Description |
|---|---|
|
Message Transmission Optimization Mechanism (MTOM) |
Ensures that attachments are in MTOM format. This format enables binary data to be sent to and from web services. This reduces the transmission size on the wire. |
|
Reliability |
Supports the WS-Reliable Messaging protocol. This guarantees the end-to-end delivery of messages. |
|
Addressing |
Verifies that simple object access protocol (SOAP) messages include WS-Addressing headers in conformance with the WS-Addressing specification. Transport-level data is included in the XML message rather than relying on the network-level transport to convey this information. |
|
Security |
Implements the WS-Security 1.0 and 1.1 standards. They enforce authentication and authorization of users. identity propagation, and message protection (message integrity and message confidentiality). |
|
Management |
Logs request, response, and fault messages to a message log. Management policies can also include custom policies. |
Within each category there are one or more policy types that you can attach. For example, if you select the reliability category, the following types are available for selection:
-
oracle/no_reliable_messaging_policy
Supports the disabling of reliable messaging configured at a higher scope
-
oracle/no_wsrm_policy
Supports the disabling of a globally attached Web Services Reliable Messaging policy
-
oracle/reliable_messaging_policy
Supports the enabling of Web services reliable messaging
-
oracle/wsrm10_policy
Supports version 1.0 of the Web Services Reliable Messaging protocol
-
oracle/wsrm11_policy
Supports version 1.1 of the Web Services Reliable Messaging protocol
For more information about available policies, details about which ones to use in your environment, and global policies, see Securing Web Services and Managing Policies with Oracle Web Services Manager.
46.2 Attaching Policies to Binding Components and Service Components
You can attach or detach policies to and from service binding components, service components, and reference binding components in a SOA composite application. Use Oracle JDeveloper to attach policies for testing security in a design-time environment. When your application is ready for deployment to a production environment, you can attach or detach runtime policies in Oracle Enterprise Manager Fusion Middleware Control.
For more information about runtime management of policies, see Administering Oracle SOA Suite and Oracle Business Process Management Suite.
46.2.1 How to Attach Policies to Binding Components and Service Components
To attach policies to binding components and service components:
46.2.1.1 To attach a policy to a service component:
-
Right-click a service component.
-
Select Configure SOA WS Policies.
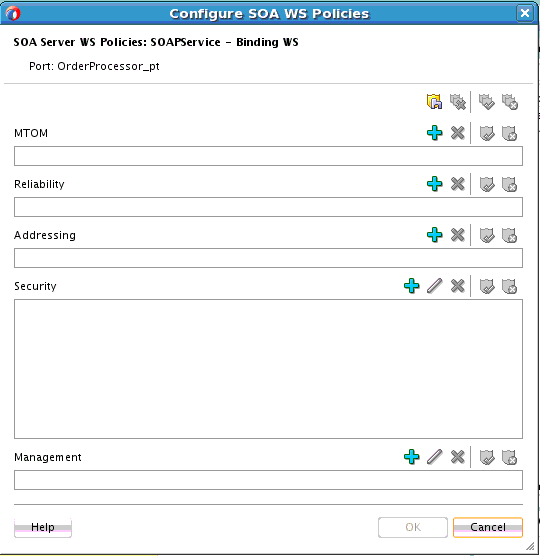
The Configure SOA WS Policies dialog shown in Figure 46-6 appears.
Figure 46-6 Configure SOA WS Policies Dialog
Description of "Figure 46-6 Configure SOA WS Policies Dialog" -
Click the Add icon next to the type of policy to attach.
-
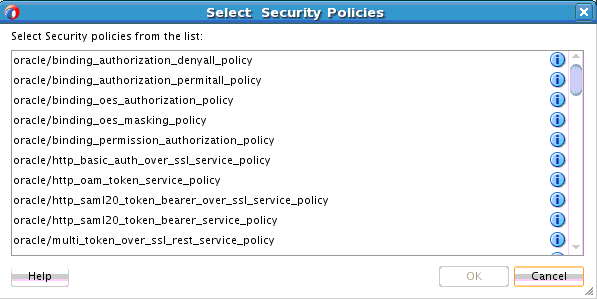
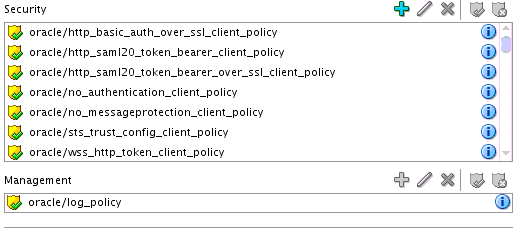
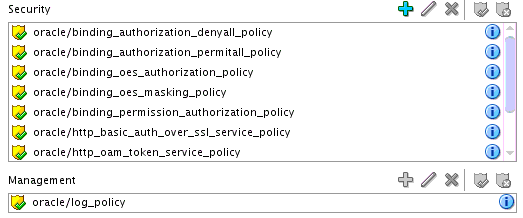
Security
-
Management
The dialog for your selection appears.
-
-
Select the type of policy to attach.
-
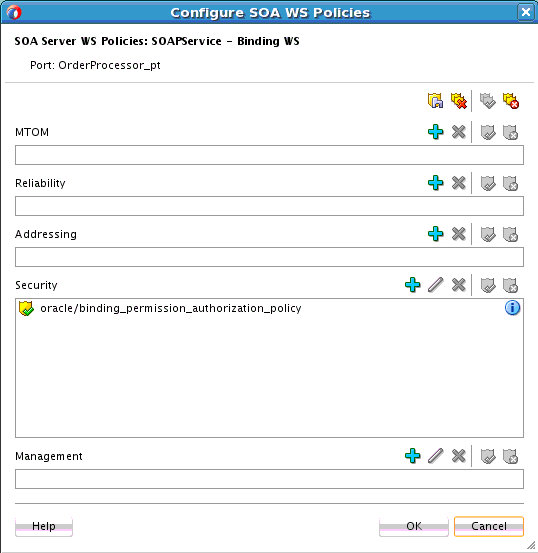
Click OK.
-
If necessary, add additional policies.
-
When complete, click OK in the Configure SOA WS Policies dialog.
For information about attaching policies during runtime in Oracle Enterprise Manager Fusion Middleware Control, see Administering Oracle SOA Suite and Oracle Business Process Management Suite.
46.2.2 How to Override Policy Configuration Property Values
Your environment may include multiple clients or servers with the same policies. However, each client or server may have their own specific policy requirements. You can override the policy property values based on your runtime requirements.
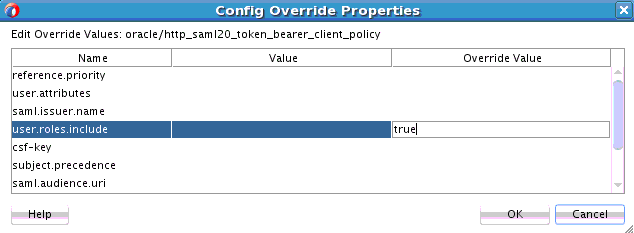
46.2.2.1 Overriding Client Configuration Property Values
You can override the default values of client policy configuration properties on a per client basis without creating new policies for each client. In this way, you can override client policies that define default configuration values and customize those values based on your runtime requirements.
For more information about overriding policy settings, see Securing Web Services and Managing Policies with Oracle Web Services Manager.
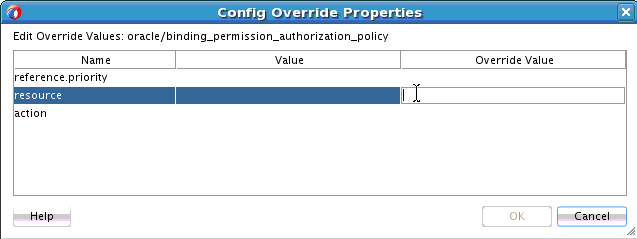
46.2.2.2 Overriding Server Configuration Property Values
You can override the default values of server policy configuration properties on a per server basis without creating new policies for each server. In this way, you can override server policies that define default configuration values and customize those values based on your runtime requirements.
To override server configuration property values:
46.3 Encrypting and Decrypting Specific Fields of Messages
You can encrypt and decrypt fields of a message to protect sensitive data (known as personally identifiable information (PII)) flowing in web services and JCA adapters in Oracle SOA Suite and Oracle Service Bus. This feature provides for the obfuscation of certain fields (for example, SSNs) to prevent this data from appearing in administration consoles in clear text.
Figure 46-11 shows an incoming message being encrypted when entering the SOA composite application in a service binding component and an outgoing message being decrypted when exiting the SOA composite application in a reference binding component. Messages outside the composite can be protected with other message protection policies (WS-Security/SSL).
Figure 46-11 Message Encryption and Decryption in a SOA Composite Application
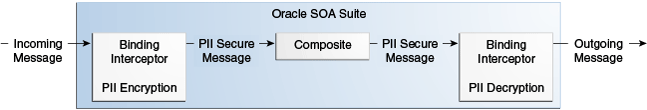
Description of "Figure 46-11 Message Encryption and Decryption in a SOA Composite Application"
The following code shows an example of an unencrypted message. The PII fields are name and driversLicense.
<person> <name>John</name> <driversLicense>B1234</driversLicense> <ssn>123-456-789</ssn> </person>
The following code shows an example of the encrypted message with the name and driversLicense fields in encrypted format.
<person> <name>John</name> <driversLicense>encrypted:fdslj[lmsfwer09fsn;keyname=pii-csf-key</driversLicense> <ssn>encrypted:gdf45md%mfsd103k;keyname=pii-csf-key</ssn> </person>
The encryption format is as follows:
encrypted:<CIPHER_TEXT>;keyname:<CSF_KEY_NAME>
Note:
If both a PII policy and authorization policy are attached to a SOA composite application, the authorization policy is executed before the PII policy. This is because the PII policy may encrypt the field used for authorization.
If the authorization policy is attached to a component and it requires an already-encrypted field, authorization fails.
46.3.1 How to Encrypt and Decrypt Specific Fields of Messages
Note:
-
You must decrypt PIIs when an encrypted message leaves the composite. If you attach a PII policy to a service binding component and do not attach a PII policy to a reference binding component, PIIs in the outbound message are not decrypted. This is not a recommended practice, and you receive a runtime error.
-
PIIs encrypted in one SOA composite application cannot be decrypted in another SOA composite application.
To encrypt and decrypt specific fields of messages: