Resolving User Login Authentication Failure Issues
This section helps you resolve some of the most common user login authentication failure issues encountered while using Oracle Business Intelligence Enterprise Edition 11g. It is not intended to be a comprehensive list of every possible scenario.
This appendix contains the following topics:
-
This section describes the basic concepts of authentication in Oracle Business Intelligence Enterprise Edition You must understand the concepts used throughout this guide as a prerequisite for using this section.
-
Identifying Causes of User Login Authentication Failure
This section provides a cause-and-effect diagram to use as a checklist for identifying authentication failure causes.
-
Resolving User Login Authentication Failures
This section provides reasons and solutions for login authentication failure.
Authentication Concepts
This section describes authentication concepts and helps to resolve login issues.
This section contains the following topics:
Authentication Defaults on Install
Immediately after install, Oracle Business Intelligence is configured to authenticate users against the WebLogic embedded LDAP server through the DefaultAuthenticator.
Default user accounts will have been set up, including a WebLogic Server administrator that uses the credentials entered during installation.
Using Oracle WebLogic Server Administration Console and Fusion Middleware Control to Configure Oracle Business Intelligence
You configure Oracle Business Intelligence using Oracle WebLogic Server Administration Console and Fusion Middleware Control.
See Using Tools to Configure Security in Oracle Business Intelligence.
You must log in to Oracle WebLogic Server Administration Console and Fusion Middleware Control with the user name and password that you specified for the administrator user during the install process, unless you have altered or removed that account or configured another account with the appropriate access, see Oracle Business Intelligence Key Login User Accounts.
WebLogic Domain and Log Locations
To diagnose and resolve user login authentication issues, you must know the locations of the WebLogic domain, and log files, as follows:
Note:
This section assumes that the install used the default locations. If you specified different install locations, you must modify the paths accordingly.
-
WebLogic domain where Oracle Business Intelligence is installed
ORACLE_HOME/user_projects/domains/bi/
-
WebLogic Administration Server logs
ORACLE_HOME/user_projects/domains/bi/servers/AdminServer/logs/
-
WebLogic Managed Server logs:
ORACLE_HOME/user_projects/domains/bi/servers/bi_server1/logs/
-
BI Server logs:
ORACLE_HOME/user_projects/domains/bi/servers/obis1/logs/
Oracle Business Intelligence Key Login User Accounts
This section describes the key login user accounts, and contains the following sections:
WebLogic Server Administrator User Account
The WebLogic Server administrator user account enables you to start the WebLogic Server, and to administer WebLogic Server using the Oracle WebLogic Server Administration Console and Fusion Middleware Control.
The WebLogic Server administrator account must have the WebLogic Server global role called Admin to enable adding WebLogic Server administrator accounts. The WebLogic Server Admin role is not an Oracle Business Intelligence application role.
Follow these steps to add or remove users to or from the global admin role using the Oracle WebLogic Server Administration Console.
Oracle Business Intelligence Login Overview
When a user logs in to Oracle Business Intelligence without Single Sign-On, authentication and user profile lookup occurs.
In a Single Sign-On (SSO) environment, authentication is performed outside the Oracle Business Intelligence system, and identity is asserted instead, but user profile lookup still occurs.
Authentication and identity assertion is performed by authentication providers and asserters respectively, and is configured using Oracle WebLogic Server Administration Console. The user profile is looked up within the Identity Store to retrieve various attributes, such as email, display name, description, language etc. Successful login to Oracle Business Intelligence requires that the first configured authentication provider contains your user population. See Configuring Oracle Business Intelligence to Use Alternative Authentication Providers.
The login process flow begins with the user credentials entered in the login screen, being sent to Presentation Services, and then to the BI Server. The BI Server attempts to authenticate the user credentials by calling the BI Security web service, deployed in the WebLogic Managed Server, and protected by a web service security policy. The call requires the BI Serverto authenticate itself to Oracle Web Services Manager, before it can be received by the BI Security Service.
Identifying Causes of User Login Authentication Failure
This section helps you to identify causes of authentication failure when logging in to Oracle Business Intelligence.
The diagrams below are cause and effect diagrams that you can use to identify possible causes of user login authentication failure. After identifying the likely cause of user login identification failure, see Resolving User Login Authentication Failures.
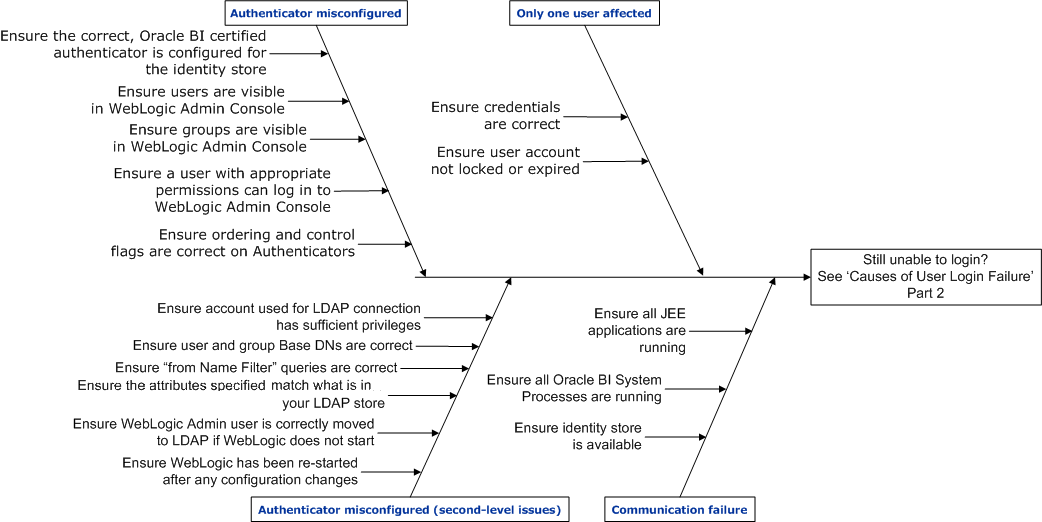
The following diagram shows: Causes of User Login Failure - Part 1
The description for the above diagram is as follows:
-
Authenticator misconfigured.
-
Ensure that the correct Oracle Business Intelligence certified authenticator is configured for the identity store.
-
Ensure that users are visible in the Oracle WebLogic Server Administration Console.
-
Ensure that groups are visible in the Oracle WebLogic Server Administration Console.
-
Ensure that a user with appropriate permissions can log in to Oracle WebLogic Server Administration Console.
-
Ensure that the ordering and control flags on authenticators are correct.
-
-
Authenticator misconfigured (second-level issues).
-
Ensure that WebLogic Server has been re-started after any configuration changes.
-
Ensure that the WebLogic Server administrator user is correctly moved to LDAP, if WebLogic Server does not start.
-
Ensure that the attributes specified match what is in your LDAP store.
-
Ensure that 'from Name Filter' queries are correct.
-
Ensure that user and group Base DN settings are correct.
-
Ensure that the account used for LDAP connection has sufficient privileges.
-
-
Only one user affected.
-
Ensure that correct credentials are used.
-
Ensure that the user account is not locked or expired.
-
-
Communication failure.
-
Ensure that the identity store is available.
-
Ensure that all BI System processes are running.
-
Ensure that all JEE applications are running.
-
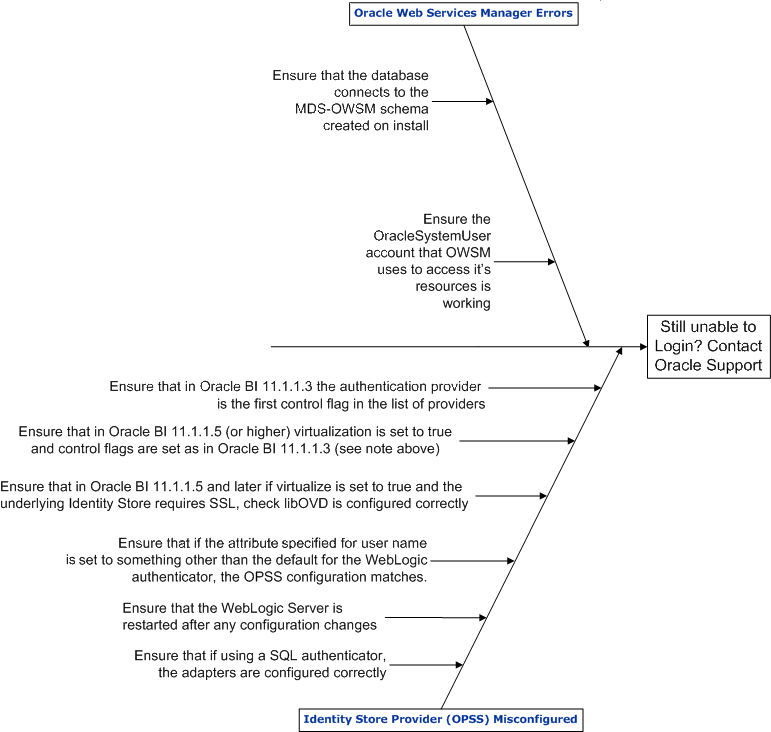
The following diagram shows: Causes of User Login Failure — Part 2
The above diagram helps you identify alternative causes of login failure if you cannot identify them using the first diagram. However, if you still cannot identify the causes of login failure after using the above diagram, contact Oracle Support at:
The description for the above diagram is as follows:
-
Identity store provider (OPSS) misconfigured.
-
Ensure that if using a SQL authenticator, the adapters are configured correctly.
-
Ensure that if the attribute specified for username is set to something other than the default value for the WebLogic authenticator, the OPSS configuration matches.
-
Ensure that in Oracle Business Intelligence Release 11.1.1.5 (or higher):
-
Virtualization is set to true.
-
Control flags are set as in Oracle Business Intelligence Release 11.1.1.3 (see following bullet).
-
-
Ensure that in Oracle Business Intelligence Release 11.1.1.3 the authentication provider (which refers to the user population with the BI System User), is the first control flag in the list of providers.
-
Ensure that the WebLogic Server is re-started after any configuration changes.
-
Ensure that in Oracle Business Intelligence Release 11.1.1.5 (or higher), if virtualization is set to true and the identity store requires SSL, virtualization must be configured correctly. See Configuring SSL when Using Multiple Authenticators.
-
-
Oracle Web Services Manager errors.
-
Ensure the database connects to the MDS-OWSM schema created on install.
-
Ensure the OracleSystemUser account that OWSM uses to access its resources is working.
-
Resolving User Login Authentication Failures
This section explains user login authentication failures, describes how to resolve them, and contains the following topics:
Single User Cannot Log in to Oracle Business Intelligence
This section contains the following topics:
Is Login Failure the Result of User Error?
The first check is whether the user cannot log in to Oracle Business Intelligence due to a simple error for example, did the user enter the wrong password?
If other users can log in to Oracle Business Intelligence, but one user cannot, check that user's credentials, see Is User Account Locked?.
Is User Account Locked?
Many LDAP authenticators lock a user account when attempts to log in exceed a specified threshold. For example, an account may be locked after more than three failed login attempts to defeat a potential automated attack.
Refer to the documentation for your chosen identity store to discover how to unlock user accounts. For example, to unlock a locked user account when using WebLogic Server embedded LDAP, see Unlock user accounts in Oracle WebLogic Server Administration Console Online Help.
Users Cannot Log in to Oracle Business Intelligence Due to Misconfigured Authenticators
The most common cause of authentication failure is misconfiguration of authenticators in WebLogic Server as follows:
Note:
Make sure you have read, and are familiar with the steps and concepts identified in Using Alternative Authentication Providers.
Have You Specified the Correct Authenticator for the Identity Store or LDAP Server?
WebLogic Server uses a variety of server-specific authenticators in addition to the embedded LDAP authenticator.
However, the embedded LDAP authenticator might not be able to query against some LDAP server products because they do not appear to be generic LDAP servers. For example, the generic LDAP server does not work with Active Directory (AD), even though AD does apparently fully implement LDAP and successfully presents itself as an LDAP server to many LDAP query tools. Configure the appropriate authenticator based on the LDAP server that the system uses.
Is the Authenticator for the LDAP Server Configured Correctly?
If the configuration settings for the LDAP server used as the primary identity store are incorrectly configured, then users cannot be correctly authenticated. Some common things to check include:
-
Account used for LDAP connection.
In the LDAP Authenticator provider-specific configuration, you must specify the DN of a principal that is used to connect to the LDAP server. This account must exist and have sufficient privileges to be able to run queries to retrieve the user or group population from the trees specified in the User or Group Base DNs. In a restricted LDAP environment, this may require elevated privileges beyond those granted to ordinary user accounts.
-
Ensure user and group Base DNs are correct.
Search for groups and users in the tree specified by the user or group Base DN, and ensure that the tree specified actually contains your user or group population.
-
Ensure 'from Name Filter' queries are correct.
Search for groups and users in the trees specified in the base DN by using the query specified in 'User from name filter' and 'Group from Name filter'. %u is a placeholder for the user id used for querying a specific user (including during authentication), and %g is a placeholder for the group name used for querying a specific group. Check that queries are syntactically and logically correct for your directory, and that you can run them (and return expected results) from an LDAP browser, using the credentials specified in the authenticator configuration.
-
Ensure the attributes specified match what is in your LDAP store.
The attributes and object classes for users and groups, are specified in the Authenticator configuration. You should not necessarily use an authenticator's pre-configured default values. For example, you should ensure that the value specified in User Name Attribute exists, and is being used for the users' names in the LDAP server on your site.
-
WebLogic Server administrator user moved to LDAP and cannot boot WebLogic Server.
If you move the WebLogic Server administrator user from the embedded LDAP server to another LDAP server, and also remove the DefaultAuthenticator from the embedded LDAP Server, you are relying only on LDAP to authenticate the administrator user. If you have misconfigured the LDAP authenticator, WebLogic Server does not start.
-
Ensure users can log in to Oracle WebLogic Server Administration Console.
If you can log in to Oracle WebLogic Server Administration Console using the credentials you used to start WebLogic Server, you can check whether other LDAP users can log in to Oracle WebLogic Server Administration Console as follows:
Grant the WebLogic Server global Admin role to an LDAP user, and if they can log in to theOracle WebLogic Server Administration Console using the URL
http://<biserver>:9501/console, the LDAP authenticator configuration is correct.Note:
If you temporarily grant the WebLogic Server global Admin role to a user to test this scenario, you must remove the grant when testing is complete to ensure the user does not have privileges to which they are not entitled.
If the LDAP user cannot log in to Oracle Business Intelligence:
-
Check that the identity store containing your users is exposed as an identity store to OPSS - check the authenticator ordering and control flags section, see Are the Control Flags for Your Authenticators Set Correctly and Ordered Correctly?.
-
Are the Control Flags for Your Authenticators Set Correctly and Ordered Correctly?
The primary identity store must be set as the first one in the list of authenticators (note that this restriction is lifted from Oracle Business Intelligence Release 11.1.1.5 (or higher) when virtualization is set to true).
Oracle Business Intelligence uses the user role Application Programming Interface (API) from OPSS which only picks up the first identity store from the list of authenticators for example, when looking up users, profile information, roles. This situation enables a user to log in to Oracle WebLogic Server Administration Console (showing that authentication has succeeded), but prevents the user logging in to Oracle Business Intelligence (because the identity store containing the user is not first in the list).
Where more than one authenticator is configured, in the general case the control flags should all be set to SUFFICIENT. This enables each one to be tried in turn until authentication succeeds. If authentication is successful, no further authenticators are tried. If none of the authenticators can authenticate the supplied credentials, the overall authentication process fails.
Note:
During install, the DefaultAuthenticator is set to REQUIRED; if you configure another authenticator, the DefaultAuthenticator must be set to SUFFICIENT or OPTIONAL, if it is being retained. SUFFICIENT is the recommended setting.
Users Cannot Log in to Oracle Business Intelligence When Oracle Web Services Manager is not Working
Oracle Web Services Manager (OWSM) secures the BI Security Service, so if OWSM is not working, then nothing can call the BI Security Service, and authentication cannot succeed until this issue is resolved.
Common causes of OWSM failure are:
-
Database Issues - OWSM Cannot Retrieve Policies
Issues connecting to the MDS-OWSM schema created on install.
-
OracleSystemUser Issues - OWSM Cannot Retrieve Policies
Issues with the OracleSystemUser account that OWSM uses to access it's resources.
Database Issues - OWSM Cannot Retrieve Policies
Oracle Web Services Manager (OWSM ) stores its metadata, including its policy definitions, in an OWSM subsection of the MDS schema. It accesses this metadata using a connection pool created on install, named mds-owsm. If there is a problem accessing the schema (for example, if the database is not available, there are incorrect credentials, or the database account is locked), then Oracle Business Intelligence authentication fails.
You see an error message like the following one in the Managed Server diagnostic log:
[2011-06-28T14:59:27.903+01:00] [bi_server1] [ERROR] [] [oracle.wsm.policymanager.bean.util.PolicySetBuilder] [tid: RTD_Worker_2] [userId: <anonymous>] [ecid: de7dd0dc53f3d0ed:11d7f503:130d6771345:-8000-0000000000000003,0] [APP: OracleRTD#11.1.1] The policy referenced by URI "oracle/wss_username_token_client_policy" could not be retrieved as connection to Policy Manager cannot be established at "t3://biserver:7001,biserver:9704" due to invalid configuration or inactive state.
In addition, you see multiple errors related to a failure to establish or create the connection pool for the data source in the Administration Server logs.
To correct this issue, you must check the following:
-
Is the database schema you specified for the MDS-OWSM data source available?
-
Did you specify the correct credentials?
-
Can you access the schema using standard database tools (for example, SQL Plus, Jdeveloper DB tools) using those credentials?
-
Is the mds-owsm data source configured correctly?
Use these steps to test the MDS-OWSM data source.
-
Log in to Oracle WebLogic Server Administration Console.
-
Click Services in the left hand pane and click Data Sources.
-
Display the Configuration page and click mds-owsm.
-
Select the Monitoring tab and display the Testing page.
-
Select a server and click Test Data Source.
Use these steps to configure the MDS-OWSM data source.
- Log in to Oracle WebLogic Server Administration Console, and click Lock & Edit in the Change Center.
- Click Services in the left hand pane and click Data Sources.
- Display the Configuration page and click mds-owsm.
- Select the Configuration tab and display the Connection Pool page.
- Configure appropriate changes.
- Click Save to save your changes.
- In the Change Center, click Activate Changes.
- Restart WebLogic Server and Oracle Business Intelligence components.
OracleSystemUser Issues - OWSM Cannot Retrieve Policies
By default, Oracle Web Services Manager (OWSM) uses the OracleSystemUser account to retrieve policies. If the account is missing, and cannot be authenticated or does not have the correct WebLogic Server global role assignments, this causes failures.
You see a log message like the following one in the Managed server diagnostic logs:
[2011-06-28T14:59:27.903+01:00] [bi_server1] [ERROR] [] [oracle.wsm.policymanager.bean.util.PolicySetBuilder] [tid: RTD_Worker_2] [userId: <anonymous>] [ecid: de7dd0dc53f3d0ed:11d7f503:130d6771345:-8000-0000000000000003,0] [APP: OracleRTD#11.1.1] The policy referenced by URI "oracle/wss_username_token_client_policy" could not be retrieved as connection to Policy Manager cannot be established at "t3://biserver:7001,biserver:9704" due to invalid configuration or inactive state.[[
After this entry, if the problem is that OWSM is not in the OracleSystemRole WebLogic Server global role, you see the following log entry:
java.rmi.AccessException: [EJB:010160]Security Violation: User: 'OracleSystemUser' has insufficient permission to access EJB: type=<ejb>, application=wsm-pm, module=wsm-pmserver-wls.jar, ejb=DocumentManager, method=retrieveDocuments, methodInterface=Remote, signature={java.lang.String,java.util.Map}.
You must ensure that the OracleSystemUser is a member of the OracleSystemGroup group in your identity store and that the group has the WebLogic Server global role OracleSystemRole assigned to it. See Steps 3-6 in Configuring Oracle Internet Directory LDAP Authentication as the Only Authenticator, these steps still apply for other LDAP servers.
If the problem is that the OracleSystemUser account cannot be authenticated or does not exist, for example, because you migrated to an LDAP identity store and removed DefaultAuthenticator without creating a new OracleSystemUser account in your new identity store, you see a log entry like this:
Caused by: javax.security.auth.login.FailedLoginException: [Security:090304]Authentication Failed: User OracleSystemUser javax.security.auth.login.FailedLoginException: [Security:090302]Authentication Failed: User OracleSystemUser denied
at weblogic.security.providers.authentication.LDAPAtnLoginModuleImpl.login(LDAPAtnLoginModuleImpl.java:261)
This error message can be caused by several different issues:
-
You have removed the DefaultAuthenticator and not created an account named OracleSystemUser in the new identity store you are using instead.
-
You have misconfigured the authenticator for your new identity store such that the OracleSystemUser account cannot be found.
-
The OracleSystemUser account has been locked or disabled in some way on your LDAP server.
Check the system for each of the possible causes, reconfigure and restart the system if needed, before retrying.
Users Cannot Log in to Oracle Business Intelligence - Is the External Identity Store Configured Correctly?
If you have configured an external identity store as your primary user population, check the following aspects of the provider configuration:
-
The authentication provider which refers to the primary user population must be set first in the order of providers (unless you are using Release 11.1.1.5 or higher, and virtualization is set to true).
-
If the DefaultAuthenticator is still enabled, ensure that both it and the authentication provider referring to the primary user population are set to 'SUFFICIENT'.
-
If you set the username attribute to something other than the default, you need to follow the instructions in Configuring User and Group Name Attributes in the Identity Store. For example, the OID authentication provider defaults to expecting the UserName attribute to be "cn", but many organizations actually use the attribute "uid" instead. In this instance, follow the instructions to set both username.attr and user.login.attr to uid in the identity store configuration in Fusion Middleware Control.
Users Can Log in With Any or No Password
In Oracle Business Intelligence Release 10g, authentication is managed through the Metadata Repository, and users wanting to authenticate against external database tables can do so using initialization block settings. The facility still exists in Oracle Business Intelligence 11g, and 12c and unfortunately it is possible to configure these blocks such that the query issued does not check the password of the user.
For example, the query:
SELECT USER_ID FROM USERS WHERE USER_ID = ':USER'
only checks the user id and not whether the password is correct. In a scenario where such an initialization block is configured, it can lead to users being able to log in with any (or no) password.
This scenario also leads to some apparently inconsistent behavior. For example, if user A and B exist in the primary identity store (Oracle Internet Directory), but user B also exists in a database which is referenced by the initialization block described in this section. When user A and user B try to log in using the wrong password they both fail authentication against OID. However, the BI Server will also attempt to run the initialization block for each user. User A fails, but user B logs in successfully because its user name is in the USER_ID column of the USERS table, and the initialization block query succeeds, despite not checking the user's password. This kind of scenario must be avoided, so if you find an authentication initialization block that behaves in this way you must remove, or alter it.
Have Removed Default Authenticator and Cannot Start WebLogic Server
WebLogic Server must be started using administrator user credentials which are associated with the WebLogic Server (not Oracle Business Intelligence) global Admin role.
When you install Oracle Business Intelligence the installer prompts for administrator user name and password, which are created in the embedded LDAP, and accessed through the DefaultAuthenticator. When you want to move from using the embedded LDAP to using an external LDAP identity store, you create a new WebLogic Server administrator user in the external store, ensure it has the WebLogic Server global Admin role, and remove the DefaultAuthenticator.
However, if you have performed these steps and have not correctly configured the authenticator configuration for the identity store that now contains the user that you want to use to start the WebLogic Server with, then you cannot start the server. The work around is to revert to the configuration settings that existed before you removed the DefaultAuthenticator.
The domain home for your WebLogic BI Domain (unless you specifically requested otherwise on install), is located in:
ORACLE_HOME/user_projects/domains/bi/
This directory contains a configuration directory with the configuration file for the overall domain, including any authenticators. When you update the configuration settings, a backup of the main configuration file, config.xml, is created, starting with backup_config.xml and then numbered versions (for example, backup_config7.xml) for each subsequent revision.
Make sure you copy the current config.xml and the most recent backup_config xml file in case you run into problems. To restore your configuration, replace the current config.xml file with the most recent backup_config xml file, and restart WebLogic Server and all Oracle Business Intelligence components. When WebLogic Server restarts, the DefaultAuthenticator will be restored.