1 About the Connector
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. This guide discusses the connector that enables you to integrate Oracle Identity Manager with UNIX-based target systems using SSH or Telnet protocol. This connector enables you to use the target system as a managed (target) resource or as an authoritative (trusted) source of identity data for Oracle Identity Manager.
In the account management (target resource) mode of the connector, information about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
In the identity reconciliation (trusted source) configuration of the connector, users are created or modified only on the target system and information about these users is reconciled into Oracle Identity Manage
This chapter contains the following sections:
Note:
In this guide, the term Oracle Identity Manager server refers to the computer on which Oracle Identity Manager is installed.
1.1 Certified Components
These are the software components and their versions required for installing and using the connector.
Table 1-1 lists the certified components for this connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
Oracle Identity Governance or Oracle Identity Manager |
You can use one of the following releases of Oracle Identity Manager:
|
|
Target systems |
The target system can be any one of the following operating systems:
Note: You can also configure and use the connector on any other UNIX-based operating system that supports SSH and Telnet protocols. See Configuring the Connector for a New Target System for more information. |
|
Connector Server |
11.1.2.1.0 |
|
Connector Server JDK |
JDK 1.6 Update 24 or later, or JRockit JDK 1.6 Update 24 or later |
|
External code |
Expect4j (expect4j-1.0.jar) is a third-party API used to connect and run commands or scripts on the target systems. It is included with the connector installation bundle, along with the following dependent libraries:
|
|
Other systems |
OpenSSH, OpenSSL, operating system patches (HP-UX), and SUDO software (only if the SUDO Admin mode is required) |
|
Target system user account |
Depending on the target system that you are using, the target system user account can be one of the following:
You provide the credentials of this user account while configuring the IT resource. |
|
Character encoding supported by the target system |
The target system must support the default C (POSIX) locale. Use the following command to check the locale that the target system supports:
|
Note:
The connector requires sh shell on the target system to run the scripts. Therefore, the connector switches to sh before running the commands.
If the user account indicated in the loginUser basic configuration parameter has access to sh and the user account can switch to sh, then there is no restriction on the original login shell.
1.2 Usage Recommendation for the UNIX Connector
Depending on the Oracle Identity Manager version that you are using, you must deploy and use one of the following connectors:
-
If you are using an Oracle Identity Manager release 9.1.0.1 or later and earlier than Oracle Identity Manager 11g Release 1 BP02 (11.1.1.5.2), then use the 9.0.4 version of this connector.
-
If you are using Oracle Identity Manager 11g Release 1 BP02 (11.1.1.5.2) or later, Oracle Identity Manager 11g Release 2 BP04 (11.1.2.0.4) or later, or Oracle Identity Manager 11g Release 2 PS3 (11.1.2.3.0), then use the latest 11.1.1.x version of this connector.
1.3 Certified Languages for the UNIX Connector
These are the languages that the connector supports.
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Czech
-
Danish
-
Dutch
-
English
-
Finnish
-
French
-
German
-
Greek
-
Hebrew
-
Hungarian
-
Italian
-
Japanese
-
Korean
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazilian)
-
Romanian
-
Russian
-
Slovak
-
Spanish
-
Swedish
-
Thai
-
Turkish
Note:
However, the connector does not support the entry of multibyte characters in some of the fields.
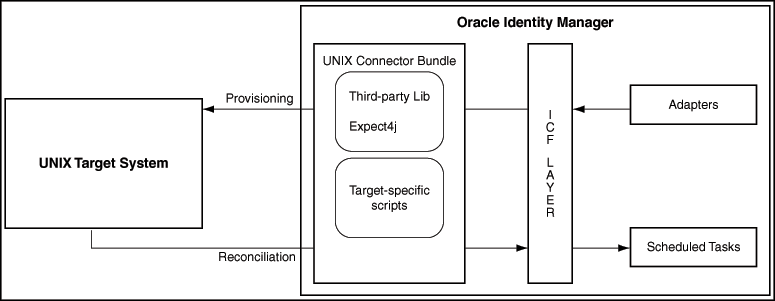
1.4 Architecture of the UNIX Connector
The UNIX connector is implemented by using the Identity Connector Framework (ICF).
This connector enables management of target system accounts through Oracle Identity Manager. Figure 1-1 shows the architecture of the connector.
The architecture of the connector can be explained in terms of the connector operations it supports:
1.4.1 Reconciliation Process for the UNIX Connector
This connector can be configured to perform either trusted source reconciliation or target resource reconciliation.
When you configure the target system as a target resource, the connector enables you to create and manage target accounts for OIM Users through provisioning. In addition, data related to newly created and modified target system accounts can be reconciled and linked with existing OIM Users and provisioned resources.
When you configure the target system as a trusted source, the connector fetches into Oracle Identity Manager, data about newly created or modified target system accounts. This data is used to create or update OIM Users.
See Also:
Reconciliation Based on the Object Being Reconciled in Oracle Fusion Middleware Administering Oracle Identity Manager for conceptual information about target resource reconciliation and trusted source reconciliation.
The following is an overview of the steps involved in reconciliation:
-
The scheduled task is run at the time or frequency that you specify. This scheduled task contains details of the mode of reconciliation (trusted source or target resource) that you want to perform.
-
The scheduled task establishes a connection with the target system by using the Expect4j third-party library.
-
The scheduled task performs the following tasks:
-
Reads the values that you set for the task attributes.
-
Reads the differences in the /etc/passwd, /etc/shadow and their corresponding mirror files to determine user records to be fetched into Oracle Identity Manager.
-
Fetches user records into Oracle Identity Manager.
-
-
If you have configured your target system as a trusted source, then:
-
Each user record fetched from the target system is compared with existing OIM Users. The reconciliation rule is applied during the comparison process. See Reconciliation Rule for Trusted Source Reconciliation for information about the reconciliation rule.
-
If a match is found between the target system record and the OIM User, then the OIM User attributes are updated with changes made to the target system record.
-
If no match is found between the target system record and the OIM User, then the target system record is used to create an OIM User.
-
-
If you have configured your target system as a target resource, then:
-
Each user record fetched from the target system is compared with existing target system resources assigned to OIM Users. The reconciliation rule is applied during the comparison process. See Reconciliation Rule for Target Resource Reconciliation for information about the reconciliation rule.
-
If a match is found between the target system record and a resource provisioned to an OIM User, then the database user resource is updated with changes made to the target system record.
-
If no match is found between the target system record and a resource provisioned to an OIM User, then the target system user record is compared with existing OIM Users. The next step depends on the outcome of the matching operation:
If a match is found, then the target system record is used to provision a resource for the OIM User.
If no match is found, then the status of the reconciliation event is set to No Match Found.
-
1.4.2 Provisioning Process for the UNIX Connector
Provisioning involves creating and managing user accounts. When you allocate (or provision) a UNIX resource to an OIM User, the operation results in the creation of an account on the target system for that user. Similarly, when you update the resource on Oracle Identity Manager, the same update is made to the account on the target system.
The provisioning process can be started through one of the following events:
-
Direct provisioning
The Oracle Identity Manager administrator uses the Administrative and User Console to create a target system account for a user.
-
Provisioning triggered by access policy changes
An access policy related to accounts on the target system is modified. When an access policy is modified, it is reevaluated for all users to which it applies.
-
Request-based provisioning
In request-based provisioning, an individual creates a request for a target system account. The provisioning process is completed when an OIM User with the required privileges approves the request and provisions the target system account to the requester.
During provisioning operations, adapters carry provisioning data submitted through the process form to the Expect4j third-party library, which in turn submits the provisioning data to the target system. The user account maintenance commands accept provisioning data from the adapters, carry out the required operation on the target system, and return the response from the target system to the adapters. The adapters return the response to Oracle Identity Manager.
1.4.3 Provisioning Functions of the UNIX Connector
This section lists provisioning functions supported by the connector
Table 1-2 lists the provisioning functions and the Adapter column gives the name of the adapter that is used when the function is performed.
Table 1-2 Provisioning Functions
| Function | Adapter |
|---|---|
|
Create User |
UNIXCreateUser |
|
Delete User |
UNIXDeleteUser |
|
Disable User |
UNIXDisableUser |
|
Enable User |
UNIXEnableUser |
|
Expire Date Updated |
UNIXUpdateUser |
|
GECOS Updated |
UNIXUpdateUser |
|
Home Directory Updated |
UNIXUpdateUser |
|
Inactive Days Updated |
UNIXUpdateUser |
|
Password Updated |
UNIXUpdateUser |
|
Primary Group Updated |
UNIXUpdateUser |
|
Secondary Group Delete |
UNIXUpdateChildTableValues |
|
Secondary Group Insert |
UNIXUpdateChildTableValues |
|
Secondary Group Update |
UNIXUpdateChildTableValues |
|
UID Updated |
UNIXUpdateUser |
|
User Login Updated |
UNIXUpdateUser |
|
User Shell Updated |
UNIXUpdateUser |
1.5 Features of the UNIX Connector
The features of the connector include support for connector server, full reconciliation, and limited reconciliation.
The following are the features of this connector:
-
Support for Configuring the Connector for a New Target System
-
Support for Multiple Instances and Multiple Versions of UNIX
-
Support for Both Target Resource and Trusted Source Reconciliation
-
Support for Reconciliation of User Status from the Target System
-
Support for Adding Custom Attributes for Reconciliation and Provisioning
1.5.1 Support for Switching Between SSH and Telnet Protocols
You can switch between SSH and Telnet protocols to connect to UNIX-based target systems. You can specify the connection type by using the connectionType parameter of the IT Resource.
The connector supports the following connection types:
-
SSH - This is the default connection. Used for SSH with password-based authentication.
-
SSHPUBKEY - Used for SSH with key-based authentication.
-
TELNET - Used for Telnet connection.
See Configuring the IT Resource for the Target System for related information.
1.5.2 Support for Running Custom Scripts
You can run scripts on a computer where the UNIX connector is deployed. You can configure custom scripts to support additional flavors of UNIX.
You can configure the scripts to run before or after the create, update, or delete an account provisioning operations. For example, you could configure a script to run before a user is created by the connector. See Configuring Action Scripts for more information.
1.5.3 Support for Configuring the Connector for a New Target System
You can configure the connector to support an additional flavor of UNIX by using custom scripts.
You can configure the connector to support an additional flavor of UNIX by using custom scripts.
By default, the connector uses pre-configured scripts to support AIX, HP-UX, Linux, and Solaris. You can customize these scripts to support an additional flavor of UNIX. See Configuring the Connector for a New Target System for more information.
1.5.4 Support for Multiple Instances and Multiple Versions of UNIX
The connector supports multiple instances and multiple versions of UNIX.
You can deploy a single connector bundle on Oracle Identity Manager and create multiple instances and multiple versions of UNIX. Then, you can use Oracle Identity Manager to manage accounts on these target systems. See Configuring the Connector for Multiple Instances and Multiple Versions of the Target System for more information.
1.5.5 Support for Both Target Resource and Trusted Source Reconciliation
You can use the connector to configure the target system as either a target resource or trusted source of Oracle Identity Manager.
See Configuring Reconciliation for more information.
1.5.6 Support for Both Full and Incremental Reconciliation
After you deploy the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, incremental reconciliation is automatically enabled from the next run of the user reconciliation.
You can perform a full reconciliation run at any time. See Full Reconciliation for more information.
1.5.7 Support for Limited Reconciliation
You can set a reconciliation filter as the value of the Filter attribute of the scheduled tasks. This filter specifies the subset of newly added and modified target system records that must be reconciled.
See Limited Reconciliation for more information.
1.5.8 Support for Batched Reconciliation
You can break down a reconciliation run into batches by specifying the number of records that must be included in each batch.
See Batched Reconciliation for more information.
1.5.9 Support for Reconciliation of User Status from the Target System
From this release onward, the connector can reconcile user account status information from the target system.
1.5.10 Support for Adding Custom Attributes for Reconciliation and Provisioning
If you want to add custom attributes for reconciliation and provisioning, then perform the procedures described in Adding Custom Attributes for Target Resource Reconciliation and Adding Custom Attributes for Provisioning.
1.5.11 Transformation of Data
You can configure transformation of data that is brought into Oracle Identity Manager during reconciliation.
See Configuring Transformation of Data During User Reconciliation for more information.
1.5.12 Support for Resource Exclusion Lists
You can specify a list of accounts that must be excluded from reconciliation and provisioning operations.
Accounts whose user IDs you specify in the exclusion list are not affected by reconciliation and provisioning operations.
Configuring Resource Exclusion Lists describes the procedure to add entries in these lookup definitions.
1.6 User Attributes for Target Resource Reconciliation and Provisioning
The connector provides a default set of attribute mappings for reconciliation between Oracle Identity Manager and the target system. If required, you can add new user or group attributes for reconciliation.
Table 1-3 provides information about user attribute mappings for target resource reconciliation and provisioning.
Table 1-3 User Attributes for Target Resource Reconciliation and Provisioning
| Process Form Field | Target System Field | Description |
|---|---|---|
|
User Login |
User Login |
New login name, specified as a string of printable characters |
|
Password |
passwd |
Password The length of the password field must be 32 characters. The supported special characters for password during provisioning are:
|
|
Secondary Group Names |
supplementary groups |
List of supplementary groups, of which the user is also a member |
|
User UID |
uid |
Numeric value of the user ID Note: It is recommended that you leave this entry blank. The target system will automatically assign a UID. |
|
Primary Group Name |
initial group |
The group name or number of the user's initial login group Note: Primary Group cannot be updated to null. |
|
Default Shell |
shell |
User's login shell |
|
GECOS |
comment |
Generally, a short description of the login It is used as the field for the user's full name. This information is stored in the user's /etc/passwd file entry. Note: The entry of multibyte characters is supported for this attribute. |
|
Home Directory |
home directory |
Login directory of the new user The final home directory name is obtained by appending the login name to the home directory value provided in this field. For example, if the login name is jdoe and the actual home directory desired on the target is |
|
Expire Date |
expire date |
Date on which the user account is disabled Note: For AIX, this field is not reconciled. |
|
Skeleton Directory |
skeleton directory |
Specifies the skeleton directory that contains information that can be copied to the new login's home directory An existing directory must be specified. The system provides a skeleton directory, /etc/skel, that can be used for this purpose. |
|
Inactive Days |
inactive days |
Number of days after a password has expired before the account is disabled Note: For AIX, this field is neither provisioned nor reconciled. |
1.7 User Attributes for Trusted Source Reconciliation
The connector provides a default set of attribute mappings for reconciliation between Oracle Identity Manager and the target system.
Table 1-4 lists user attributes for trusted source reconciliation.
Table 1-4 User Attributes for Trusted Source Reconciliation
| OIM User Form Field | Target System Attribute | Description |
|---|---|---|
|
User ID |
UserLogin |
UserLogin |
|
Last Name |
UserLogin |
Last name |
|
Employee Type |
NA |
Default value: |
|
User Type |
NA |
Default value: |
|
Organization |
NA |
Default value: |
|
TrustedStatus[TRUSTED] |
Flag (Lock/Unlock) |
User status |
1.8 Roadmap for Deploying and Using the Connector
The following is the organization of information in the rest of this guide:
- Deploying the Connector describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
- Using the Connector describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
- Extending the Functionality of the Connector describes procedures that you can perform if you want to extend the functionality of the connector.
- Testing and Troubleshooting describes the procedure to use the connector testing utility for testing the connector.
- Known Issues lists known issues associated with this release of the connector.
- Privileges Required for Performing Provisioning and Reconciliation provides information about privileges required for successful provisioning operations and reconciliation runs.
- Sample Scripts for Updating Default Attributes for Reconciliation provides sample scripts for the procedure described in Adding Custom Attributes for Target Resource Reconciliation.
- Sample Scripts for Updating Default Attributes for Provisioning provides sample scripts for the procedure described in Adding Custom Attributes for Provisioning.