4 Extending the Functionality of the Connector
After you deploy the connector, you must configure it to meet your requirements.
This chapter discusses the following connector configuration procedures:
Note:
From Oracle Identity Manager Release 11.1.2 onward, lookup queries are not supported. See Managing Lookups in Oracle Fusion Middleware Administering Oracle Identity Manager guide for information about managing lookups by using the Form Designer in the Oracle Identity Manager System Administration console.
4.1 Configuring the Connector for a New Target System
You can configure the connector to support an additional flavor of UNIX.
Note:
Perform this procedure only if you want to configure the connector for an additional flavor of UNIX other than the target systems listed in Certified Components.
By default, the connector uses pre-configured scripts to support Linux, Solaris, AIX, and HP-UX.
The scripts are available in the connector bundle JAR file. You can download the bundle from Oracle Identity Governance database using the DownloadJars utility in OIM_HOME/ bin directory or from the installation media. If you are using Connector Server, then you can copy the bundle from CONNECTOR_SERVER_HOME/ bundles directory.
You can add similar scripts with similar directory structure to support an additional flavor of UNIX. For example, you can add connector support for a target system with BSD/OS flavor of UNIX. To do so:
4.2 Configuring the Connector for Multiple Instances and Multiple Versions of the Target System
Note:
Perform this procedure only if you want to configure the connector for multiple installations of the target system.
The following example illustrates this requirement:
The Tokyo, London, and New York offices of Example Multinational Inc. have their own installations of the target system. The company has recently installed Oracle Identity Manager, and they want to configure Oracle Identity Manager to link all the installations of the target system.
To meet the requirement posed by such a scenario, you must configure the connector for multiple installations of the target system.
To configure the connector for multiple installations of the target system:
When you use the Administrative and User Console to perform provisioning, you can specify the IT resource corresponding to the target system installation to which you want to provision the user.
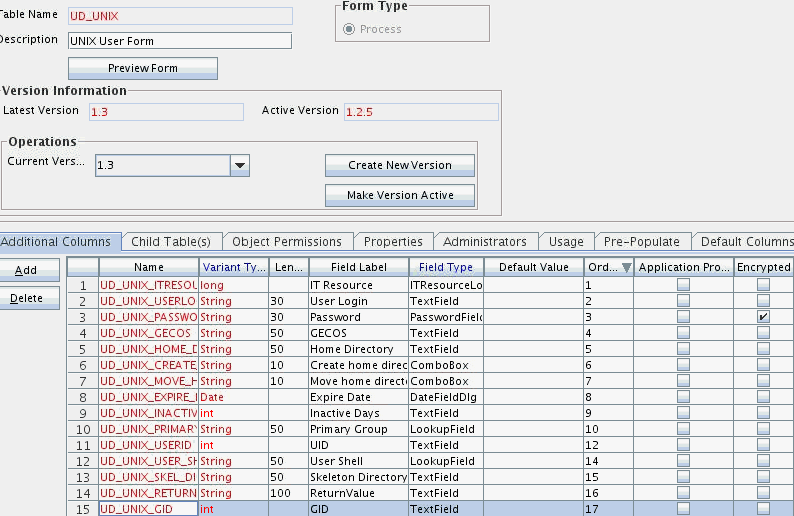
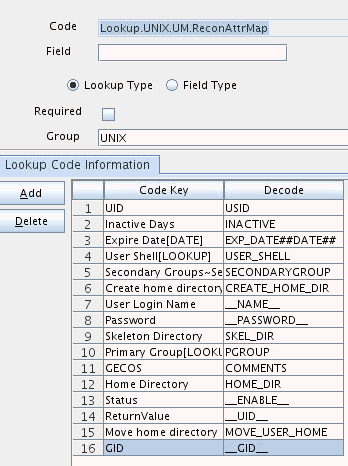
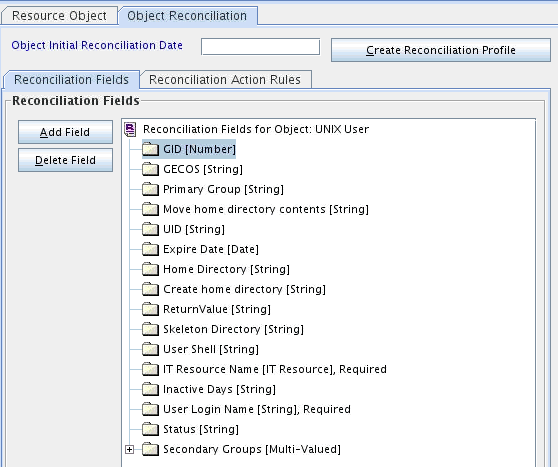
4.3 Adding Custom Attributes for Target Resource Reconciliation
The connector provides a default set of attribute mappings for reconciliation between Oracle Identity Manager and the target system. If required, you can add new user or group attributes for reconciliation.
Note:
In this section, the term "attribute" refers to the identity data fields that store user data.
By default, the attributes listed in User Attributes for Target Resource Reconciliation and Provisioning are mapped for reconciliation between Oracle Identity Manager and the target system. If required, you can map additional attributes for reconciliation as follows:
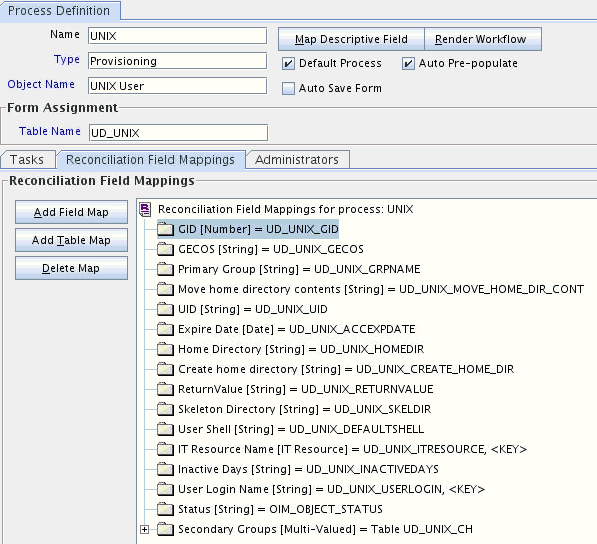
4.4 Adding Custom Attributes for Provisioning
The connector provides a default set of attribute mappings for provisioning between Oracle Identity Manager and the target system. If required, you can add new user or group attributes for provisioning.
Note:
In this section, the term "attribute" refers to the identity data fields that store user data.
By default, the attributes listed in User Attributes for Target Resource Reconciliation and Provisioning are mapped for provisioning between Oracle Identity Manager and the target system. If required, you can map additional attributes for provisioning as follows:
4.5 Configuring Validation of Data During Reconciliation and Provisioning
You can configure validation of reconciled and provisioned single-valued data according to your requirements.
The Lookup.UNIX.UM.ProvValidation and Lookup.UNIX.UM.ReconValidation lookup definitions hold single-valued data to be validated during provisioning and reconciliation operations, respectively.
For example, you can validate data fetched from the First Name attribute to ensure that it does not contain the number sign (#). In addition, you can validate data entered in the First Name field on the process form so that the number sign (#) is not sent to the target system during provisioning operations.
Note:
The Lookup.UNIX.UM.ProvValidation and Lookup.UNIX.UM.ReconValidation lookup definitions are optional and do not exist by default.
You must add these lookups as decode values to the Lookup.UNIX.UM.Configuration lookup definition to enable exclusions during provisioning and reconciliation operations. See Lookup.UNIX.UM.Configuration for more information.
To configure validation of data:
4.6 Configuring Transformation of Data During User Reconciliation
You can configure transformation of reconciled data according to your requirements.
The Lookup.UNIX.UM.ReconTransformation lookup definition holds single-valued user data to be transformed during reconciliation operations. For example, you can use First Name and Last Name values to create a value for the Full Name field in Oracle Identity Manager.
Note:
The Lookup.UNIX.UM.ReconTransformation lookup definition is optional and does not exist by default.
You must add this lookup as decode value to the Lookup.UNIX.UM.Configuration lookup definition to enable exclusions during provisioning and reconciliation operations. See Lookup.UNIX.UM.Configuration for more information.
To configure transformation of single-valued user data fetched during reconciliation:
4.7 Configuring Resource Exclusion Lists
The Lookup.UNIX.UM.ProvExclusionList and Lookup.UNIX.UM.ReconExclusionList lookup definitions hold user IDs of target system accounts for which you do not want to perform provisioning and reconciliation operations, respectively.
Note:
The Lookup.UNIX.UM.ProvExclusionList and Lookup.UNIX.UM.ReconExclusionList lookup definitions are optional and do not exist by default.
You must add these lookups as decode values to the Lookup.UNIX.UM.Configuration lookup definition to enable exclusions during provisioning and reconciliation operations. See Lookup.UNIX.UM.Configuration for more information.
The following is the format of the values stored in these lookups:
| Code Key | Decode | Sample Values |
|---|---|---|
|
User Login resource object field name |
User ID of a user |
Code Key: User Login Decode: User001 |
|
User Login resource object field name with the [PATTERN] suffix |
A regular expression supported by the representation in the |
Code Key: User Login[PATTERN] To exclude users matching any of the user ID 's User001, User002, User088, then: Decode: User001|User002|User088 To exclude users whose user ID 's start with 00012, then: Decode: 00012* See Also: For information about the supported patterns, visit |
To add entries in the lookup for exclusions during provisioning operations: