Overview of Private VLANs
Private VLAN (PVLAN) technology enables you to divide a VLAN into sub-VLANs to isolate network traffic. A regular VLAN is a single broadcast domain. When you configure a PVLAN, the single broadcast domain is partitioned into smaller subdomains. The standard (IEEE 802.1Q) VLAN is called the primary VLAN and the sub-VLANs are called the secondary VLANs when you configure a PVLAN. The secondary VLANs can be either isolated VLANs or community VLANs.
-
The ports that are associated with an isolated VLAN can communicate only with the primary VLAN and not with any other secondary VLAN. You can create only one isolated VLAN within a primary VLAN domain.
-
The ports associated with community VLAN can communicate with the primary VLAN and the other ports that are in the same community VLAN. You can create multiple community VLANs within a primary VLAN domain.
In Oracle VM Server for SPARC, you can configure a PVLAN. This PVLAN enables you to divide a regular VLAN into sub-VLANs to isolate network traffic. The inter-vnet-links feature supports the communication restrictions of isolated and community PVLANs. Inter-vnet-links are disabled for isolated PVLANs and are enabled only for virtual networks that are in the same community for community PVLANs. Direct traffic from other virtual networks outside of the community is not permitted. For more information, see Using Private VLANs in Oracle VM Server for SPARC 3.3 Administration Guide.
For information about the regular VLANs, see Configuring Virtual Networks by Using Virtual Local Area Networks.
The following figure shows a simple PVLAN configuration with two PVLANs configured on a switch that supports PVLAN.
Figure 11 Private VLAN
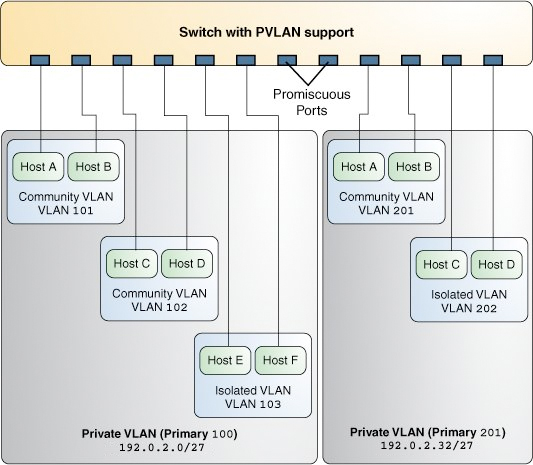
In the figure, the private VLAN with the primary VLAN ID 100 has three secondary VLANs with secondary VLAN IDs 101, 102, and 103. Two of the secondary VLANs are community VLANs with the hosts Host A and Host B and Host C and Host D, and the other is an isolated VLAN with the hosts Host E and Host F.
The ports associated with the community VLANs 101 and 102 can communicate with the primary VLAN 100 and also can communicate with each other, that is, Host A can communicate with Host B and Host C can communicate with Host D. However, Host A and Host B in community VLAN 101 cannot communicate with Host C and Host D in community VLAN 102. The ports associated with the isolated VLAN can communicate only with the primary VLAN and not with each other.
For more information, see Configuring a Private VLAN.
Advantages of Using PVLANs
Using PVLAN provides the following advantages:
-
Conserves IP addresses because multiple VLANs can be created per IP subnet.
-
Increases scalability because PVLANs provide a greater number of L2 isolation networks than regular VLANs. This increase helps to overcome the limitation of VLANs, which enables you to create a maximum of 4094 isolated networks.
-
Provides better isolation compared to regular VLANs.
PVLAN Ports
PVLANs can span multiple switches similar to regular VLANs. A trunk port carries frames either from a primary VLAN or a secondary VLAN. The two different types of ports associated with the PVLAN are promiscuous trunk ports and secondary trunk ports.
-
Promiscuous trunk port – All the frames going out from the promiscuous trunk port are tagged with the primary VLAN ID. This port is configured on the top-level switch uplink port. The switch maps the primary VLAN ID and the secondary VLAN ID.
-
PVLAN secondary trunk port – All the frames going out from PVLAN secondary trunk port are tagged with the secondary VLAN ID.
Note - Even though the PVLAN ports are isolated at layer 2, the ports can still communicate with each other at layer 3 as long as the external policy gateway allows the communication.
Tagging the Outgoing Traffic
In Oracle Solaris, you must set the tag mode property for a PVLAN depending on whether the promiscuous trunk port is on the system or the switch. Therefore, you need to identify whether the PVLAN is configured on the switch and the secondary ports are configured on Oracle Solaris or the PVLAN is configured only on the system and not on the switch.
To send out the packets with the primary VLAN ID, you must set the tag mode to primary. To send out packets with the secondary VLAN ID, you must set the tag mode to secondary. The switch converts the secondary VLAN ID to the primary VLAN ID. By default, the packets are sent out with the primary VLAN ID.
You can tag the outgoing traffic with a primary VLAN ID or a secondary VLAN ID by configuring the tagmode property. The default value of this property is primary. If there are multiple PVLAN switches and you want a PVLAN to span these multiple switches, you must set the property tagmode to secondary by using the dladm set-linkprop command.
Example 22 Setting the Tag Mode for a PVLANThe following example shows how you can change the tag mode on a datalink.
# dladm set-linkprop -p pvlan-tagmode=secondary net0
# dladm show-linkprop -p pvlan-tagmode net0
LINK PROPERTY PERM VALUE EFFECTIVE DEFAULT POSSIBLE
net0 pvlan-tagmode rw secondary secondary primary secondary,
primary
Note - The value of tagmode depends on whether the switch supports PVLANs.
PVLAN Configuration Requirements
When configuring a PVLAN, note the following restrictions:
-
The primary VLAN ID and secondary VLAN ID for community VLANs must be unique.
For example, if you have a community VLAN with a primary VLAN ID of 3 and a secondary VLAN ID of 100, you cannot create another community VLAN that uses either 3 or 100 as the secondary VLAN ID. That is, any combination containing the ID pair such as 4, 100 or 4, 3 is invalid.
-
You can reuse the secondary VLAN ID of an isolated VLAN.
For example, if you have an isolated VLAN with a primary VLAN ID of 3 and a secondary VLAN ID of 100, you can reuse the VLAN ID 100 as the primary VLAN ID or the community secondary VLAN ID.
PVLANs With Zones
You can configure multiple private virtual networks within a single network unit such as a switch by combining VLANs and Oracle Solaris zones. With PVLAN you can provide network isolation between zones which are in the same VLAN without introducing any additional VLANs. The following figure shows a system with two physical NICs and two PVLANs are configured over them.
Figure 12 PVLAN With Zones
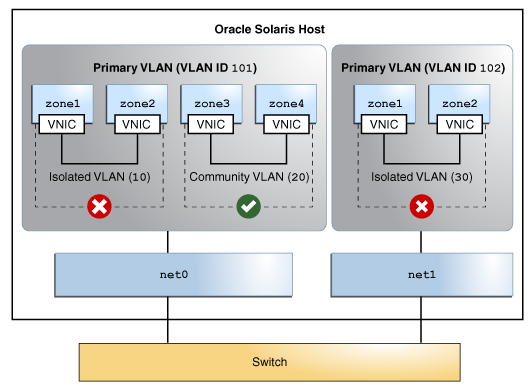
The figure shows two PVLANs with VLAN IDs 101 and 102. An isolated and a community VLAN are configured on Primary VLAN 101. Only one isolated VLAN is configured on primary VLAN 102. The zones in the isolated VLAN and the community VLAN on the Primary VLAN 101 cannot communicate with each other. However, the hosts within the community VLAN can communicate with each other.
For information about how to assign PVLAN to a zone, see Assigning a PVLAN to a Zone.