Overview of Bridged Networks
Bridges connect various nodes in the network into a single network. The network segments share a single broadcast network and communicate as if they were a single network segment when connected. As a result, each node can reach the other nodes by using network protocols such as IP rather than using routers to forward traffic across network segments. If you do not use a bridge, you must configure IP routing to permit the forwarding of IP traffic between nodes.
Although you can use both bridging and routing to distribute information about the locations of resources on the network, they differ in several ways. Routing is implemented at the IP layer (L3) and uses routing protocols. No routing protocols are used on the datalink layer.
Bridging is used to distribute information about the locations of resources on the network. In a bridged network, the destinations of forwarded packets are determined by examining the network traffic that is received on the links that are attached to the bridge. A bridged network uses protocols, such as Spanning Tree Protocol (STP) and Transparent Interconnection of Lots of Links (TRILL). For more information, see Bridging Protocols.
 | Caution - Do not set the local-mac-address? property to false by using the eeprom command on SPARC® based systems that use bridging. Doing so causes these systems to incorrectly use the same MAC address on multiple ports and on the same network. |
Simple Bridged Network
The following figure shows a simple bridged network configuration.
Figure 13 Simple Bridged Network
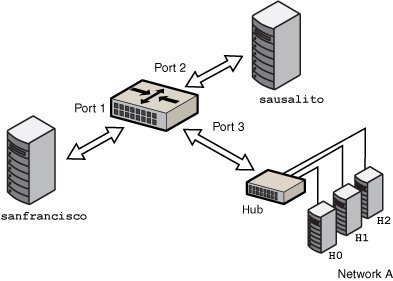
The bridge, goldengate, is an Oracle Solaris system that has bridging configured. The systems sanfrancisco and sausalito are physically connected to the bridge. Network A uses a hub that is physically connected to the bridge on one side and to three computer systems on the other side. The bridge ports are the links net0, net1, and net2.
How Oracle Solaris Bridges Are Implemented in the Network Stack
In Oracle Solaris, you can configure bridges on the datalink layer of the same network stack implementation, as shown in the following figure.
Figure 14 Bridges in the Network Stack for Oracle Solaris
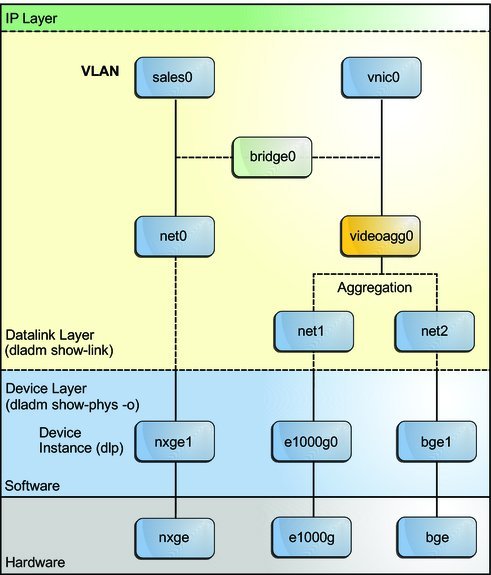
Two interfaces, net0 and videoagg0, are configured as a bridge, bridge0. Packets that are received on one interface are forwarded to the other interface. After the bridge configuration, both interfaces can still be used to configure VLANs and IP interfaces.
Bridged Network Ring
Bridged networks can be formed into rings that physically connect several bridges together. The following figure shows a bridged network ring configuration.
Figure 15 Bridged Network Ring
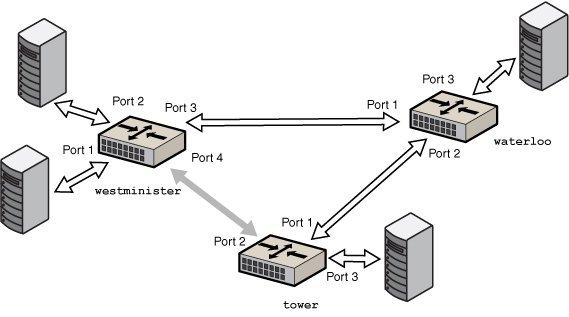
The figure shows a bridged network that is configured in a ring. The configuration shows three bridges. Two systems are physically connected to the westminister bridge. One system is physically connected to the waterloo bridge and one system is physically connected to the tower bridge. The bridges are physically connected to each other through the bridge ports.
This type of configuration can cause problems with old packets saturating the network links by endlessly looping around the ring. To protect against such looping conditions, Oracle Solaris bridges implement both the STP and TRILL protocols. Note that most hardware bridges also implement STP loop protection.
How a Bridged Network Works
When a packet is received by the bridge, its source address is examined. The source address of the packet associates the node from which the packet was sent with the link on which it is received. Thereafter, when a received packet uses that same address as the destination address, the bridge forwards the packet over the link to that address.
The link that is associated with a source address might be an intermediate link that is connected to another bridge in the bridged network. Over time, all of the bridges within the bridged network "learn" which of the links sends a packet toward a given node. Therefore, destination address of the packet is used to direct the packet to its final destination by means of hop-by-hop bridging.
A local "link-down" notification indicates that all nodes on a given link are no longer reachable. In this situation, packet forwarding to the link is halted and all forwarding entries over the link are flushed. Older forwarding entries are also flushed over time. When a link is restored, packets that are received over the link are treated as new. The learning process begins again, based on the source address of a packet. This process enables the bridge to properly forward packets over that link when the address is used as the destination address.
Bridging Protocols
Bridged networks use the following protocols:
-
STP is the default protocol that is used by the bridged networks. Bridging uses the STP mechanism to prevent network loops that potentially render the subnetworks unusable. To forward packets to their destinations, bridges must listen in promiscuous mode on every link that is attached to the bridge. Listening in promiscuous mode causes bridges to become vulnerable to the occurrences of forwarding loops, in which packets infinitely circle at full-line rate.

Caution - Do not configure a link into a bridge when the highest possible levels of performance are required. Bridging requires the underlying interfaces to be in promiscuous mode, which disables a number of important optimizations that are in the hardware (NIC), driver, and other layers of the system. The disabling of these performance enhancements is an unavoidable consequence of the bridging mechanism. These performance issues only affect links that are configured to be part of a bridge. You can use a bridge on a system where some of the links of the system are not bridged and are hence not subject to those constraints.
-
Transparent Interconnection of Lots of Links (TRILL)
Oracle Solaris supports the TRILL protection enhancement, which avoids loops without disabling links. TRILL helps to load-balance the traffic between several paths to the destination.
When STP is used for loop protection, the physical loop is mitigated by preventing one of the connections in the loop from forwarding packets. Bridged Network Ring shows that the physical link between the westminster and tower bridges is not used to forward packets.
Unlike STP, TRILL does not shut down physical links to prevent loops. Instead, TRILL computes the shortest-path information for each TRILL node in the network and uses that information to forward packets to individual destinations.
You can use TRILL by specifying the –P trill option in the dladm create-bridge or dladm modify-bridge commands. For more information, see Creating a Bridge and Modifying the Protection Type for a Bridge.
For information about STP, see IEEE 802.1D-1998. For information about TRILL, see the Internet Engineering Task Force (IETF) TRILL draft documents (http://tools.ietf.org/wg/trill).
STP Daemon
Each bridge that you create by using the dladm create-bridge command is represented as an identically named Service Management Facility (SMF) instance of svc:/network/bridge. Each instance runs a copy of the /usr/lib/bridged daemon, which implements the STP.
For example, the following command creates a bridge called pontevecchio:
# dladm create-bridge pontevecchio
The system creates an SMF service instance called svc:/network/bridge:pontevecchio and an observability node called /dev/net/pontevecchio0. The observability node is intended for use with the snoop command and the wireshark packet analyzer. You can use the dlstat command to obtain the run time statistics of the bridge.
For safety purposes, all ports run standard STP by default. A bridge that does not run some form of bridging protocol, such as STP, can form long-lasting forwarding loops in the network. Because Ethernet has no hop-count or time-to-live (TTL) on packets, any such loops are fatal to the network.
-
To handle any new ports that are added
-
To implement BPDU guarding
-
To enable or disable forwarding on the ports, as necessary
When a particular port is not connected to another bridge (for example, because the port has a direct point-to-point connection to a system), you can administratively disable STP for that port. Even if all ports on a bridge have STP disabled, the STP daemon still runs for the following reasons:
When a port has STP disabled, the bridged daemon continues to listen for BPDUs (BPDU guarding). The daemon uses syslog to flag any errors and disables forwarding on the port to indicate a serious network misconfiguration. The link is re-enabled when the link goes down and comes up again, or when you manually remove the link and add it again.
If you disable the SMF service instance for a bridge, the bridge stops on those ports as the STP daemon is stopped. If the instance is restarted, STP starts from its initial state.
TRILL Daemon
Each bridge that you create by using the dladm create-bridge -P trill command is represented by an identically named SMF instance of svc:/network/bridge and svc:/network/routing/trill. Each instance of svc:/network/routing/trill runs a copy of the /usr/lib/trilld daemon, which implements the TRILL protocol.
For example, the following command creates a bridge called bridgeofsighs:
# dladm create-bridge -P trill bridgeofsighs
The system creates two SMF services called svc:/network/bridge:bridgeofsighs and svc:/network/routing/trill:bridgeofsighs. In addition, the system creates an observability node called /dev/net/bridgeofsighs0.