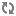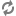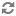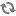By default, the
enecerts utility produces the
eneCert.pem certificate (used by all clients and
servers to specify their identity when using SSL) and the
eneCA.pem Certificate Authority (CA) certificate
(used by all clients and servers that wish to authenticate the other endpoint
of a communication channel).
If you have your own CA certificate and private-key files, you can use
the
--CAkey and
--CAcert
flags to generate the
eneCert.pem certificate. The private-key file
(.key extension) is used to digitally sign the public key that is generated by
the
enecerts utility. Both flags must be used for this
operation.
The syntax for the
--CAkey flag is:
--CAkey private-key
where private-key is your own .key file with the private key for the CA that should be used to sign the generated certificate.
The syntax for the
--CAcert flag is:
--CAcert cert-pem
where
cert-pem is your CA certificate (.pem extension).
This file is the same type of file as the default
eneCA.pem CA certificate.
For example, the following Windows command creates a signed certificate file using your own CA certificate and private-key files:
enecerts --CAkey myCA.key --CAcert myCA.pem
You would then use the resulting
eneCert.pem certificate and your CA file
(myCA.pem in the example) to configure SSL for your Guided
Search components. If you have multiple machines in your deployment, you must
also copy these files to the other machines.