Release 2 (8.1.6)
A76989-01
Library |
Product |
Contents |
Index |
| Oracle8i SQL Reference Release 2 (8.1.6) A76989-01 |
|
SQL Statements (continued), 3 of 8
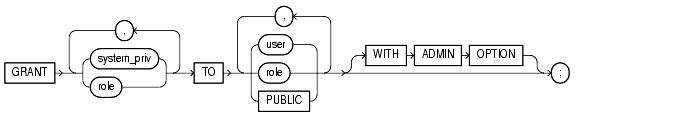
To grant system privileges and roles to users and roles. Both privileges and roles are either local, global, or external (see "CREATE USER" and "CREATE ROLE" for definitions).
You can authorize database users to use roles through means other than the database and the GRANT statement. For example, some operating systems have facilities that grant operating system privileges to operating system users. You can use such facilities to grant roles to Oracle users with the initialization parameter OS_ROLES. If you choose to grant roles to users through operating system facilities, you cannot also grant roles to users with the GRANT statement, although you can use the GRANT statement to grant system privileges to users and system privileges and roles to other roles. For information about other authorization methods, see Oracle8i Administrator's Guide.
For information on granting object privileges, see "GRANT object_privileges".
To grant a system privilege, you must either have been granted the system privilege with the ADMIN OPTION or have been granted the GRANT ANY PRIVILEGE system privilege.
To grant a role, you must either have been granted the role with the ADMIN OPTION or have been granted the GRANT ANY ROLE system privilege, or you must have created the role.
|
system_priv |
is a system privilege to be granted. Table 7-5 lists the system privileges (organized by the database object operated upon). |
|
|
|
|
|
|
|
Oracle provides a shortcut for specifying all system privileges at once: |
|
|
|
ALL PRIVILEGES |
is equivalent to specifying all the system privileges listed in Table 7-5, " System Privileges". |
|
|
Restrictions:
|
|
|
role |
is a role to be granted. You can grant an Oracle predefined role or a user-defined role. Table 7-6 lists the predefined roles. For information on creating a user-defined role, see "CREATE ROLE". |
|
|
|
|
|
|
|
identifies users or roles to which system privileges and roles are granted.
Restriction: A user, role, or |
|
|
|
grants system privileges or roles to all users. |
|
|
|
enables the grantee to |
|
|
|
If you grant a system privilege or role to a user without specifying To revoke the admin option on a system privilege or role from a user, you must revoke the privilege or role from the user altogether and then grant the privilege or role to the user without the admin option. |
|
| Predefined Role | Purpose |
|---|---|
|
|
These roles are provided for compatibility with previous versions of Oracle. You can determine the privileges encompassed by these roles by querying the |
|
|
Note: Oracle Corporation recommends that you design your own roles for database security rather than relying on these roles. These roles may not be created automatically by future versions of Oracle. |
|
|
These roles are provided for accessing data dictionary views and packages. See Also: Oracle8i Administrator's Guide for more information on these roles. |
|
|
These roles are provided for convenience in using the Import and Export utilities. See Also: Oracle8i Utilities for more information on these roles. |
|
|
You need these roles to use Oracle's Advanced Queuing functionality. See Also: Oracle8i Application Developer's Guide - Advanced Queuing for more information on these roles. |
|
|
|
|
|
You need this role to create a user who owns a recovery catalog. See Also: Oracle8i Backup and Recovery Guide for more information on recovery catalogs. |
|
|
A DBA using Oracle's heterogeneous services feature needs this role to access appropriate tables in the data dictionary and to manipulate them with the DBMS_HS package. See Also: Oracle8i Distributed Database Systems and Oracle8i Supplied PL/SQL Packages Reference for more information. |
|
Oracle also creates other roles that authorize you to administer the database. On many operating systems, these roles are called |
|
To grant the CREATE SESSION system privilege to RICHARD, allowing RICHARD to log on to Oracle, issue the following statement:
GRANT CREATE SESSIONTO richard;
To grant the CREATE TABLE system privilege to the role TRAVEL_AGENT, issue the following statement:
GRANT CREATE TABLETO travel_agent;
TRAVEL_AGENT's privilege domain now contains the CREATE TABLE system privilege.
The following statement grants the TRAVEL_AGENT role to the EXECUTIVE role:
GRANT travel_agentTO executive;
TRAVEL_AGENT is now granted to EXECUTIVE. EXECUTIVE's privilege domain contains the CREATE TABLE system privilege.
To grant the EXECUTIVE role with the ADMIN OPTION to THOMAS, issue the following statement:
GRANT executiveTO thomas WITH ADMIN OPTION;
THOMAS can now perform the following operations with the EXECUTIVE role:
|
|
 Copyright © 1999 Oracle Corporation. All Rights Reserved. |
|