2 Deploying the Connector
Deploying the connector involves the following steps:
Note:
Some of the procedures described in this chapter must be performed on the target system. To perform these procedures, you must use an SAP administrator account to which the SAP_ALL and SAP_NEW profiles have been assigned.2.1 Preinstallation
Preinstallation information is divided across the following sections:
2.1.1 Preinstallation on Oracle Identity Manager
This section contains the following topics:
2.1.1.1 Files and Directories on the Installation Media
Table 2-1 lists the files and directories that are bundled in the deployment package on the installation media.
Table 2-1 Files and Directories on the Installation Media
| File in the Installation Media Directory | Description |
|---|---|
| configuration/SAPHRMS-CI.xml | This XML file contains configuration information that is used during connector installation. |
| lib/Common.jar | This JAR file contains the class files that are common to all connectors. During connector deployment, this file is copied to the Oracle Identity Manager database of Oracle Identity Manager release 11.1.x. |
| lib/SAPCommon.jar | This JAR file contains the class files that are common to all SAP connectors. During connector deployment, this file is copied to the Oracle Identity Manager database of Oracle Identity Manager release 11.1.x. |
| lib/SAPER.jar | This JAR file contains the class files that are specific to the SAP Employee Reconciliation connector. During connector deployment, this file is copied to the Oracle Identity Manager database of Oracle Identity Manager release 11.1.x. |
| Files in the resources directory |
Each of these resource bundles contains language-specific information that is used by the connector. During connector deployment, this file is copied to the Oracle Identity Manager database of Oracle Identity Manager release 11.1.x. Note: A resource bundle is a file containing localized versions of the text strings that include GUI element labels and messages. |
| xml/SAPHRMS-ConnectorConfig.xml |
This XML file contains definitions for the connector components. These components include the following:
|
Note:
If you are using Oracle Identity Manager 12cPS4 (12.2.1.4.0) or later with the SAP Employee Reconciliation 9.1.2.x connector, you must create the ServiceAccount.API.EncryptedParamsValue system property. This property is not available out of the box and must be created from the Configuration Property option in Oracle Identity System Administration console. This system property is used to control the functionality of the tcITResourceInstanceOperationsBean.getITResourceInstanceParameters(long plITResourceInstanceKey) API.
By default, this API masks the value of encrypted fields making your deployment more secure.
Oracle recommends creating this property only if a legacy connector or an old custom code requires the legacy behavior of the above API.
When the value is set to False, the encrypted parameter values are masked. When the value is set to True, the encrypted parameter values are returned by the above API.
2.1.1.2 Creating a Backup of the Existing Common.jar File
The Common.jar file is in the deployment package of each release 9.1.x connector. With each new release, code corresponding to that particular release is added to the existing code in this file. For example, the Common.jar file shipped with Connector Y on 12-July contains:
- Code specific to Connector Y
- Code included in the Common.jar files shipped with all other release 9.1.x connectors that were released before 12-July.
If you have already installed a release 9.1.x connector that was released after current release of the SAP Employee Reconciliation connector, back up the existing Common.jar file, install the SAP Employee Reconciliation connector, and then restore the Common.jar file. The steps to perform this procedure are as follows:
Caution:
If you do not perform this procedure, then your release 9.1.x connectors might not work.2.1.2 Preinstallation on the Target System
Preinstallation on the target system involves performing the following procedures:
2.1.2.1 Creating a Target System User Account for Connector Operations
The connector uses a target system account to connect to the target system during reconciliation. This target system account must be a CPIC user to whom you assign a customized role with the S_IDOC_ALL profile, S_RFC authorization object, and PLOG authorization object.
Note:
You must configure the PLOG authorization object so that the values assigned to this object match the ones shown in Step 2 through 6. Only the Plan Version (PLVAR) object can be set according to your requirements.2.1.2.2 Downloading and Installing the SAP JCo
Note:
To download files from the SAP Web site, you must have access to the SAP service marketplace with Software Download authorization.
In an Oracle Identity Manager cluster, copy the JAR files and the contents of the connectorResources directory to the corresponding directories on each node of the cluster.
To download and copy the external code files to the required locations:
2.2 Installation
Note:
In this guide, the term Connector Installer has been used to refer to the Connector Installer feature of the Oracle Identity Manager Administrative and User Console.Installing the connector involves running the connector installer, see Running the Connector Installer.
2.2.1 Running the Connector Installer
To run the Connector Installer for Oracle Identity Manager 11.1.x:
When you run the Connector Installer, it copies the connector files and external code files to destination directories on the Oracle Identity Manager host computer. These files are listed in Table 2-1.
Installing the Connector in an Oracle Identity Manager Cluster
While installing Oracle Identity Manager in a cluster, copy all the JAR files and the contents of the connectorResources directory into the corresponding directories on each node of the cluster. Then, restart each node. See Files and Directories on the Installation Media for information about the files that you must copy and their destination locations on the Oracle Identity Manager server.
Restoring the Common.jar File
If required, restore the Common.jar file that you had backed up by following the procedure described in Creating a Backup of the Existing Common.jar File
2.3 Postinstallation
Postinstallation steps are divided across the following sections:
- Setting Up the Lookup.SAP.HRMS.Configuration Lookup Definition in Oracle Identity Manager
- Verifying Segment Details in Lookup Definitions
- Configuring Reconciliation of Manager ID Attribute Values
- Configuring the Target System for Generation of IDocs
- Changing to the Required Input Locale on Oracle Identity Manager
- Clearing Content Related to Connector Resource Bundles from the Server Cache
- Copying Resource Bundle Entries for UDFs
- Managing Logging
- Configuring Reconciliation of Effective-Dated Target System Events
- Recovering from Failed Communication Between the Target System and Oracle Identity Manager
- Configuring SNC to Secure Communication Between Oracle Identity Manager and the Target System
- Specifying Values for the Connection Properties (IT Resource Configuration)
- Creating an Authorization Policy
- Displaying UDFs in Oracle Identity Manager 11.1.2 or Later
2.3.1 Setting Up the Lookup.SAP.HRMS.Configuration Lookup Definition in Oracle Identity Manager
The Lookup.SAP.HRMS.Configuration lookup definition is used to capture information about the following items:
- Message type and IDoc type used for communication between the target system and Oracle Identity Manager
- Connector components used during reconciliation
Table 2-2 lists the entries in this lookup definition. The procedure to set or modify a Decode value is given after this table.
Table 2-2 Entries in the Lookup.SAP.HRMS.Configuration Lookup Definition
| Code Key | Description | Decode |
|---|---|---|
| Message Type |
Message type to be used for person record Note: You must not change the Decode value. |
HRMD_A |
| Class Name |
Name of the parser class Note: If you develop your own parser, then you can replace the default value of the Class Name entry with the name of your custom parser class. |
oracle.iam.connectors.sap.common.parser.HRMDAParser |
| IDoc Type |
IDoc type that you want to use You can specify either a predefined IDoc type or the name of a custom IDoc type. |
HRMD_A05 |
| IDoc Type Extension | If you have extended a predefined IDoc type, then enter the name of the IDoc type extension. | NONE |
| Sub Type Field |
Stores the sub-type information You can specify a maximum length of 4 characters. |
000076,000079 |
| Begin Date Field |
Stores the start date information You can specify a maximum length of 8 characters. |
000091,000098 |
Note:
The entries listed in the remaining rows of this table must be changed only if you use a custom IDoc type. The default Decode values are correct for all predefined HRMD_A* IDoc types.| Code Key | Description | Decode |
|---|---|---|
| Root Segment |
Root segment in IDoc, which will be used to identify new employees Note: You must not change the Decode value. |
E2PLOGI001 |
| Segment Name Length | Number of characters in the file that denotes the segment name | 30 |
| Object Type |
Segment details of object type The Decode value is used to filter person records. |
E2PLOGI001;OTYPE;66;67;P |
| User ID | Object ID that indicates the personnel number in a person record | E2PLOGI001;OBJID;68;75 |
| Delete Indicator | Segment details of the indicator that identifies whether or not the employee is deleted | E2PLOGI001;OPERA;77;77;D |
| Event Begin Date | Segment details for the begin date of events (hire, terminate, and other events) | E2P0000001;BEGDA;91;98 |
| Event End Date | Segment details for the end date of events (hire, terminate, and other events) | E2P0000001;ENDDA;83;90 |
| Actions Event | Segment to indicate actions | E2P0000001 |
| Event | Segment details for event | E2P0000001;MASSN;138;139 |
| Group | Segment details for employee group | E2P0001001;PERSG;146;146 |
| Sub Group | Segment details for employee subgroup | E2P0001001;PERSK;147;148 |
| Group Segment | Infotype containing Employee Group and Employee Subgroup attributes | E2P0001001 |
Information about connector components
| Code Key | Description | Decode |
|---|---|---|
| Employee Type Lookup | Name of the lookup definition that is used to map combinations of Employee Group and Employee Subgroup of the target system with the employee type in Oracle Identity Manager | Lookup.SAP.HRMS.EmployeeType |
| Hire Events Lookup |
Name of the lookup definition that is used to store the list of all Hire events For example, name of the lookup definition that stores event IDs corresponding to employees joining the company for the first time. |
Lookup.SAP.HRMS.HireEvents |
| Terminate Events Lookup |
Name of the lookup definition that is used to store the list of all Terminate events For example, name of the lookup definition that stores events IDs corresponding to employees on long leave or terminated employees. |
Lookup.SAP.HRMS.TerminateEvents |
| Rehire Events Lookup |
Name of the lookup definition that is used to store the list of all Rehire events For example, name of the lookup definition that stores events IDs corresponding to employees who re-join the company. |
Lookup.SAP.HRMS.RehireEvents |
| Transform Lookup For Recon | Name of the lookup definition that is used to configure transformation of user attribute values fetched from the target system during reconciliation | Lookup.SAP.HRMS.ReconTransformation |
| Validation Lookup For Recon | Name of the lookup definition that is used to configure validation of user attribute values fetched from the target system during reconciliation | Lookup.SAP.HRMS.ReconValidation |
| Organization | Default organization in Oracle Identity Manager | Xellerate Users |
| Employee Type |
Default employee type in Oracle Identity Manager Note: The Decode value is used as the default user type in the Lookup.SAP.HRMS.EmployeeType lookup definition. |
Full-time |
| User Type |
Enter the role that must be set for OIM Users created through reconciliation. You must select one of the following values:
Default value: |
End-User |
| IT Resource Mapping | Name of the lookup definition that holds mappings between the connection properties accepted by the SAP JCo API and the names of IT resource parameters | Lookup.SAP.HRMS.ITResourceMapping |
Miscellaneous Variables
| Code Key | Description | Decode |
|---|---|---|
| Batch Size | Enter the number of lines that you want the parser to process at a time from the flat file containing IDocs. This flat file is generated when you perform the procedure described in the Performing Full Reconciliation. | 5 |
| Remove Leading Zero from Personnel Number | Enter yes if you want leading zeros to be removed from personnel numbers fetched from the target system. Enter no if you do not want leading zeros to be removed. |
no |
| Reconcile First Time Disabled Users | Enter yes to specify that you want to reconcile records that are currently in the Disabled state and that have not been reconciled earlier. Otherwise, enter no. |
yes |
| Constants Lookup | Name of the lookup definition that holds constants | Lookup.SAP.HRMS.Constants |
| Manager Lookup Name | Name of the lookup definition in which manager IDs of managers of the various target system organizations must be populated | Lookup.SAP.HRMS.OrgManager |
| Create deferred event for future dated hire |
Enter Enter |
No |
| Create deferred event for terminate event |
Enter Note: If you set the value of this entry to Yes, then the OIM start date field and OIM end date field entries (which are described later in this table) must contain the values Start date and End date, respectively. |
No |
| OIM start date field | Enter Start Date if you want to reconcile the start date value from the target system into the Start date process form field in Oracle Identity Manager. Otherwise, enter None. |
Start Date |
| OIM end date field | Enter End Date if you want to reconcile the end date value from the target system into the End date process form field in Oracle Identity Manager. Otherwise, enter None |
End date |
| Use Validation For Recon | Enter Yes if you want to configure validation of user attributes that are brought into Oracle Identity Manager during reconciliation. Otherwise, enter No.
See Configuring Validation of Data During Reconciliation for more information about this feature. |
No |
| Use Transformation For Recon | Enter Yes if you want to configure transformation of user attributes that are brought into Oracle Identity Manager during reconciliation. Otherwise, enter No.
See Configuring Transformation of Data During User Reconciliation for more information about this feature. |
No |
| Organization Hierarchy Lookup Name | Name of the lookup definition containing details of organization hierarchies on the target system | Lookup.SAP.HRMS.OrgHierarchy |
| Get Manager ID During Recon | Enter Yes if you want to reconcile the Manager ID attribute values along with other user records. Otherwise, enter No. |
No |
| Is Future Dated Event Handling Enabled | Enter Yes if you want the connector to handle future dated events as current dated events. Otherwise, enter No. |
Yes |
| Is IDOC File Format in XML | Enter Yes if you want to parse the XML format IDOC. Otherwise, enter No. |
No |
| Recon Rule Attribute Lookup | This entry will be used only to customize the reconciliation Rule. We must add an entry in the Lookup.SAP.HRMS.ReconRuleAttrMap.
Field_Label as code key and UserForm_Field_Name in the decode. Example: Decode: Note: Any updates done to Reconciliation Rules requires the 'Create Reconciliation Profile' option in Resource Object to be run once for the rule to take effect. |
Lookup.SAP.HRMS.ReconRuleAttrMap |
Depending on the OIM version, do the following to set or modify a Decode value in the lookup definition:
For Oracle Identity Manager prior to 11.1.2.1.0:
- On the Design Console, expand Administration, and then double-click Lookup Definition.
- Search for and open the Lookup.SAP.HRMS.Configuration lookup definition.
- In the Decode column for the Code Key, enter a value.
- Click the Save icon.
For Oracle Identity Manager 11.1.2.1.0 or later:
- Log in to Oracle Identity System Administration.
- In the left pane, under System Configuration, click Lookups.
- Search for and open the Lookup.SAP.HRMS.Configuration lookup definition.
- Click Edit Lookup Type.
- In the Meaning column for the Code Key, enter a value.
- Click the Save icon.
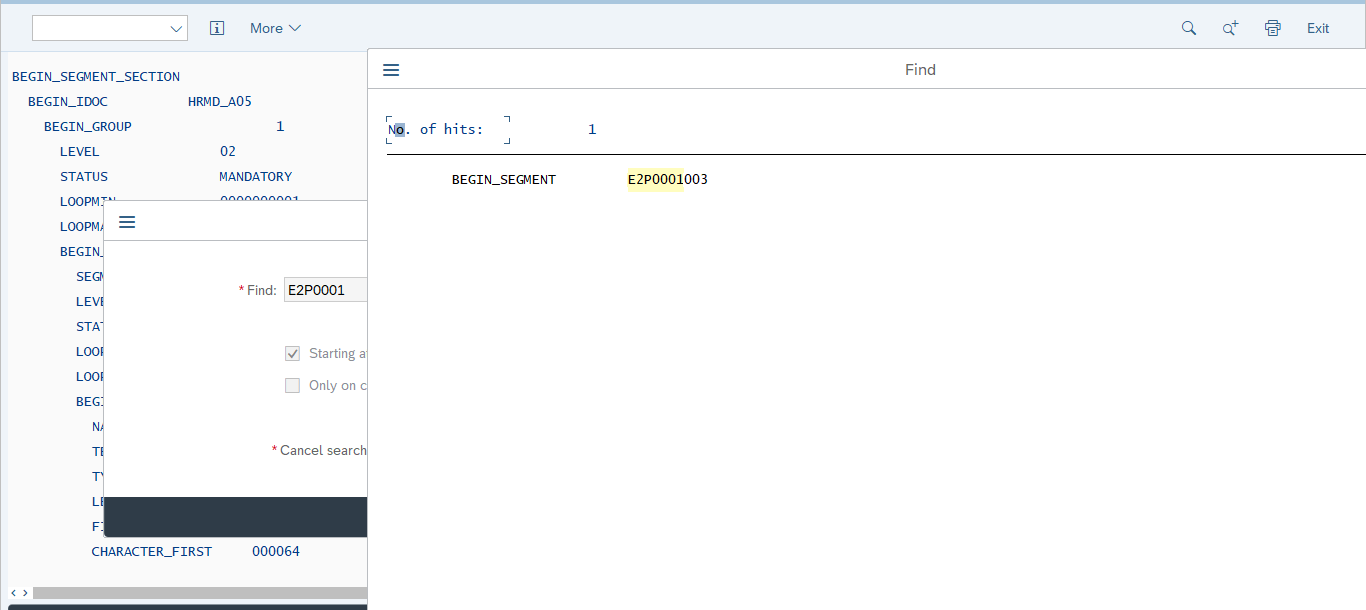
2.3.2 Verifying Segment Details in Lookup Definitions
The Lookup.SAP.HRMS.Configuration and Lookup.SAP.HRMS.AttributeMapping lookup definitions hold segment details of target system attributes. Segment details are in the following format:
E2P<INFO_TYPE><SEGMENT_VERSION>
For example, in the E2P0000001 segment, 0000 is the infotype and 001 is the version of the segment.
See Also:
Structure of a Sample IDocThe segment version is different for different versions of the target system. For the HRMD_A05 IDoc type, E2P0001001 is the segment name in SAP R/3 4.7 and E2P0001002 is the segment name in ECC 6.0.
You must verify and, if required, correct segment details in the Lookup.SAP.HRMS.Configuration and Lookup.SAP.HRMS.AttributeMapping lookup definitions.
To determine and if required change the segment version:
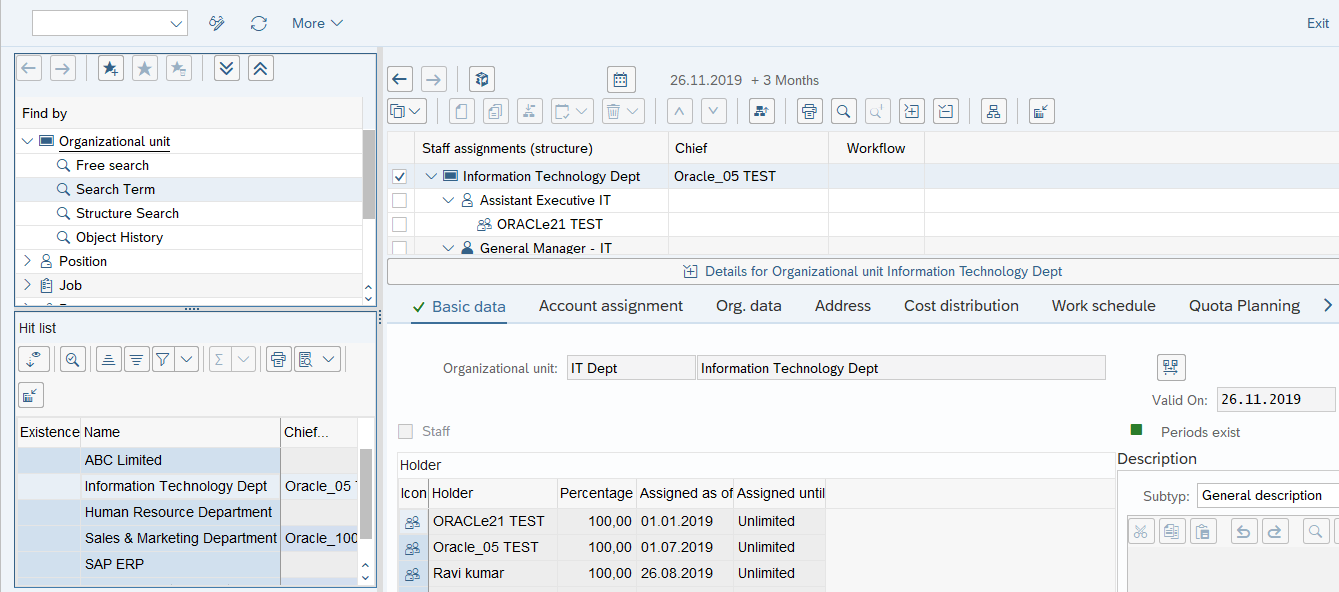
2.3.3 Configuring Reconciliation of Manager ID Attribute Values
See Also:
Reconciliation of the Manager ID Attribute for information about the sequence of steps involved in this process.To configure reconciliation of manager ID attribute values:
2.3.4 Configuring the Target System for Generation of IDocs
User data is moved from the target system to Oracle Identity Manager through "push" technology. The Application Link Enabling (ALE) feature of SAP is the foundation of this mode of data transfer.
This section describes procedures involved in configuring the target system. You may need the assistance of an SAP Basis administrator to perform some of these procedures.
The following link describes procedures to create the ALE components that are used during generation of IDocs:
- Checking Whether a Sender Logical System Already Exists
- Defining the Sending and Receiver Logical Systems
- Assigning a Client to the Sender Logical System
- Defining the Distribution Model
- Creating the File Port
- Defining the Partner Profile
- Registering the Listener with the SAP Gateway (tRFC)
- Creating the tRFC Port
- Activating Change Pointers
- Configuring Segment Filtering
- Configuring SAP Ports for Communication with Oracle Identity Manager
For more information on procedures to create ALE components, see the following link: https://wiki.scn.sap.com/wiki/display/ABAP/7+Steps+For+ALE+Configuration
Note:
- Select either the Transfer IDocs immediately or the Collect IDocs.
- For incremental reconciliation, select Transfer IDocs immediately Instead, the job that you schedule on the target system will be used to transfer IDocs in flat-file format to the port.
- For full reconciliation, select the Collect IDocs option. By selecting this option, you specify that IDocs must not be transferred to the port as and when they are created.
- While performing the procedure described in Configuring the IT Resource , you specify the same program ID as the value of the Program ID parameter of the IT resource.
2.3.4.1 Checking Whether a Sender Logical System Already Exists
You must create a sender logical system to represent SAP and a receiver logical system to represent Oracle Identity Manager.
If there is an existing sender logical system to represent SAP, then you need not define another sender logical system. Similarly, if a client is assigned to the existing sender logical system, then you need not assign another client.
To check if the sender logical system has been defined and if a client has been associated with it:
2.3.4.2 Defining the Sending and Receiver Logical Systems
You must create a sender logical system to represent SAP and a receiver logical system to represent Oracle Identity Manager
If there is an existing sender logical system to represent SAP, then you need not define another sender logical system. Similarly, if a client is assigned to the existing sender logical system, then you need not assign another client.
If you determined that a sender logical system does not exist, then you must create the sender logical system. In addition, you must create the receiver logical system.
To create the sending or receiver logical system:
2.3.4.3 Assigning a Client to the Sender Logical System
The sender logical system must have a client associated with it. If there is an existing client associated with the sender logical system, then you need not associate another client.
Note:
A logical system can have only one client associated with it.To associate a client with the sender logical system:
2.3.4.4 Defining the Distribution Model
The distribution model holds information about the sending and receiver logical systems that you define and the message type that flows between them.
To define the distribution model:
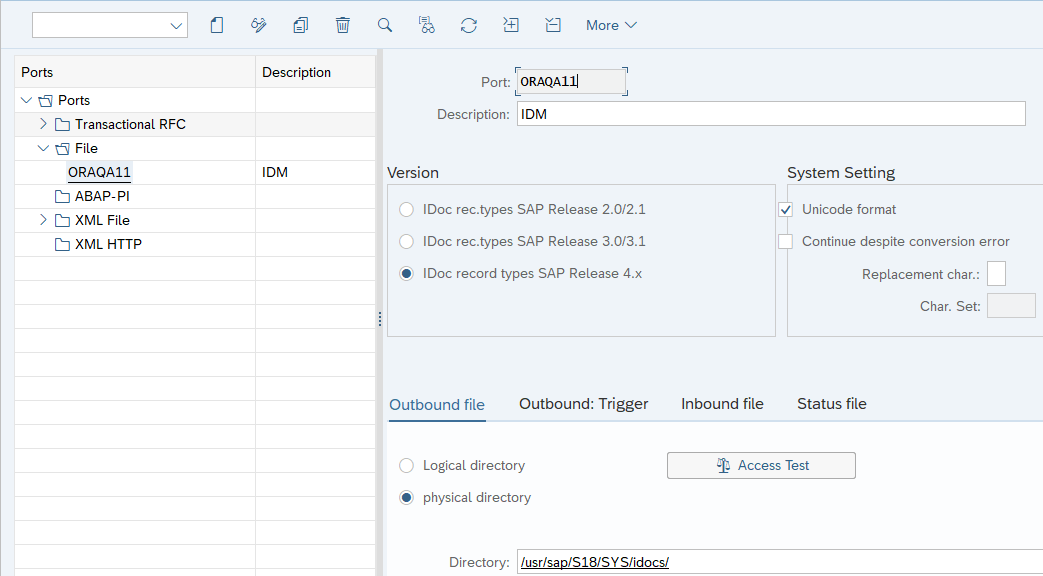
2.3.4.5 Creating the File Port
The file port is a definition of the directory location and name of the file in which IDocs are recorded. In full reconciliation, IDocs for all existing target system users is generated and written to flat files. The file port holds the directory location and name of these flat files.
To create the file port:
2.3.4.6 Defining the Partner Profile
A partner profile is a mapping of the receiver logical system, ports used by the receiver logical system, and IDoc collection mode.
Note:
When you start using the connector to reconcile user data from the target system, you use the partner profile to switch between full and incremental reconciliation. When you switch to full reconciliation, the scheduled task for incremental recon continues to run. However, IDocs are not sent to Oracle Identity Manager.To define the partner profile:
2.3.4.7 Registering the Listener with the SAP Gateway (tRFC)
To register the listener with the SAP gateway, create an RFC destination as follows:
2.3.4.8 Creating the tRFC Port
Transactional RFC (tRFC) on SAP is a variant of the Remote Function Call feature. The tRFC port on SAP is used by the listener, which is a scheduled task running on Oracle Identity Manager. The listener picks up IDocs delivered at the tRFC port. These IDocs are in the form of Java objects; there is no exchange of physical files at the tRFC port.
2.3.4.9 Activating Change Pointers
Change pointers are used to record updates to user data on the target system. These records are stored in special tables, and they are called change docs.
Note:
During incremental reconciliation, a change doc contains only data from attributes of infotypes in which at least one attribute has been modified. For example, consider the 0001 infotype. This infotype holds the MSTBR attribute and some other attributes. If this attribute is modified, then during the next incremental reconciliation run, all the attributes of the 0001 infotype are copied into the change doc that is created to track the change in the MSTBR attribute.To activate change pointers:
2.3.4.10 Configuring Segment Filtering
Note:
The procedure described in this section is optional. Segment filtering is not a requirement for using the ALE feature.On the target system, multiple attributes of the same type are grouped under an infotype. Multiple infotypes are grouped under a segment. There are more than 100 predefined segments on the target system.
The Lookup.SAP.HRMS.AttributeMapping lookup definition maps attributes of the target system with OIM User fields. Only data from mapped attributes is reconciled into Oracle Identity Manager, regardless of the segments (that is, attributes) in the IDocs received by Oracle Identity Manager. This is illustrated by the following example:
Suppose there are 14 attribute mappings in the Lookup.SAP.HRMS.AttributeMapping lookup definition. If the IDocs contain data for 30 attributes, then only data from the 14 mapped attributes is reconciled into Oracle Identity Manager. Data for the remaining 16 attributes is not used at all.
The segment filtering feature of the target system enables you to specify the segments that must not be included in IDocs. By configuring segment filtering, you ensure that attribute data that is not required in Oracle Identity Manager is not brought to Oracle Identity Manager.
Segment filtering is applied at the IDoc creation stage. Change docs are created for a change in any attribute of infotypes in any segment.
Note:
When you configure segment filtering, you must ensure that the E1P0000, E1P0001, E1P0002, E1P0006 and E1P0105 segments are always included. Some attributes from infotypes in these segments are configured as predefined attributes that are mapped to OIM User attributes. See Structure of a Sample IDoc for information about the structure of a sample IDoc.
You can configure and then reconfigure segment filtering at any time after deployment. While configuring segment filtering, you must ensure that mandatory attributes defined in the target system and Oracle Identity Manager are always included.
To configure segment filtering:
2.3.4.11 Configuring SAP Ports for Communication with Oracle Identity Manager
To enable communication between the target system and Oracle Identity Manager, you must ensure that the ports listed in Table 2-4 are open.
Table 2-4 Ports for SAP Services
| Service Port Number | Format Default Port |
|---|---|
| Dispatcher 32SYSTEM_NUMBER | 3200 |
| Gateway (for non-SNC communication) 33SYSTEM_NUMBER | 3300 |
| Gateway (for SNC communication) 48SYSTEM_NUMBER | 4800 |
| Message server 36SYSTEM_NUMBER | 3600 |
To check if these ports are open, you can, for example, try to establish a Telnetconnection from Oracle Identity Manager to these ports.
2.3.5 Changing to the Required Input Locale on Oracle Identity Manager
Changing to the required input locale (language and country setting) involves installing the required fonts and setting the required input locale.
You may require the assistance of the system administrator to change to the required input locale.
2.3.6 Clearing Content Related to Connector Resource Bundles from the Server Cache
Note:
In an Oracle Identity Manager cluster, you must perform this step on each node of the cluster. Then, restart each node.
To clear content related to connector resource bundles from the server cache:
2.3.7 Copying Resource Bundle Entries for UDFs
If you are using a non-English locale, then copy entries for the UDFs from the connector resource bundle to the customResources_LOCALE.properties file.
The following example illustrates this procedure:
Suppose you are using the French locale. When you install Oracle Identity Manager, the customResources_fr.properties file is copied into the Oracle Identity Manager database for Oracle Identity Manager release 11.1.x.
2.3.8 Managing Logging
If you are using Oracle Identity Manager release 11.1.x, perform the instructions in the following sections:
2.3.8.1 Understanding Log Levels
When you enable logging, Oracle Identity Governance automatically stores in a log file information about events that occur during the course of provisioning and reconciliation operations.
Note:
In an Oracle Identity Manager cluster, perform this procedure on each node of the cluster. Then, restart each node.Oracle Identity Manager release 11.1.x uses Oracle Java Diagnostic Logging (OJDL) for logging. OJDL is based on java.util.logger. To specify the type of event for which you want logging to take place, you can set the log level to one of the following:
-
SEVERE.intValue()+100
This level enables logging of information about fatal errors.
-
SEVERE
This level enables logging of information about errors that might allow Oracle Identity Governance to continue running.
-
WARNING
This level enables logging of information about potentially harmful situations.
-
INFO
This level enables logging of messages that highlight the progress of the application.
-
CONFIG
This level enables logging of information about fine-grained events that are useful for debugging.
-
FINE, FINER, FINEST
These levels enable logging of information about fine-grained events, where FINEST logs information about all events.
These message types are mapped to ODL message type and level combinations as shown in Table 2-5.
Table 2-5 Log Levels and ODL Message Type:Level Combinations
| Java Level | ODL Message Type:Level |
|---|---|
|
SEVERE.intValue()+100 |
INCIDENT_ERROR:1 |
|
SEVERE |
ERROR:1 |
|
WARNING |
WARNING:1 |
|
INFO |
NOTIFICATION:1 |
|
CONFIG |
NOTIFICATION:16 |
|
FINE |
TRACE:1 |
|
FINER |
TRACE:16 |
|
FINEST |
TRACE:32 |
The configuration file for OJDL is logging.xml, which is located at the following path:
DOMAIN_HOME/config/fmwconfig/servers/OIM_SERVER/logging.xml
Here, DOMAIN_HOME and OIM_SEVER are the domain name and server name specified during the installation of Oracle Identity Governance.
2.3.8.2 Enabling Logging
To enable logging in Oracle WebLogic Server:
-
Edit the logging.xml file as follows:
-
Add the following blocks in the file:
<log_handler name='sap-er-handler' level='[LOG_LEVEL]' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='[FILE_NAME]'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="OIMCP.SAPH" level="[LOG_LEVEL]" useParentHandlers="false"> <handler name="sap-er-handler"/> <handler name="console-handler"/> </logger> -
Replace both occurrences of [LOG_LEVEL] with the ODL message type and level combination that you require. Table 2-5 lists the supported message type and level combinations.
Similarly, replace [FILE_NAME] with the full path and name of the log file in which you want log messages to be recorded.
The following blocks show sample values for [LOG_LEVEL] and [FILE_NAME]:
<log_handler name='sap-er-handler' level='NOTIFICATION:1' class='oracle.core.ojdl.logging.ODLHandlerFactory'> <property name='logreader:' value='off'/> <property name='path' value='F:\MyMachine\middleware\user_projects\domains\base_domain1\servers\oim_server1\logs\oim_server1-diagnostic-1.log'/> <property name='format' value='ODL-Text'/> <property name='useThreadName' value='true'/> <property name='locale' value='en'/> <property name='maxFileSize' value='5242880'/> <property name='maxLogSize' value='52428800'/> <property name='encoding' value='UTF-8'/> </log_handler>
<logger name="OIMCP.SAPH" level="NOTIFICATION:1" useParentHandlers="false"> <handler name="sap-er-handler"/> <handler name="console-handler"/> </logger>With these sample values, when you use Oracle Identity Manager, all messages generated for this connector that are of a log level equal to or higher than the NOTIFICATION:1 level are recorded in the specified file.
-
-
Save and close the file.
-
Set the following environment variable to redirect the server logs to a file:
For Microsoft Windows:
set WLS_REDIRECT_LOG=FILENAMEFor UNIX:
export WLS_REDIRECT_LOG=FILENAMEReplace FILENAME with the location and name of the file to which you want to redirect the output.
-
Restart the application server.
2.3.9 Configuring Reconciliation of Effective-Dated Target System Events
Note:
If you do not perform the procedure described in this section, then support for effective-dated events is disabled. In other words, an event is brought to Oracle Identity Manager, regardless of the effective date of the infotype. See Reconciliation of Effective-Dated Lifecycle Events for information about how future-dated events are processed.On the target system, events IDs are assigned to all employee lifecycle events. The connector can distinguish between current-dated and future-dated lifecycle events related to hiring employees and terminating the services of employees.
To enable this feature of the connector, define the event IDs as follows:
2.3.10 Recovering from Failed Communication Between the Target System and Oracle Identity Manager
What Happens When the Listener Becomes Unavailable
When an IDoc is sent to the listener running on Oracle Identity Manager during incremental reconciliation, the status of the IDoc on the target system is changed to "Transferred to Destination." This status change takes place regardless of whether or not the listener is available.
If you determine that the listener was unavailable for some time, then you can reset the status of the IDocs on the target system and then resend them to Oracle Identity Manager.
What Happens When the Target System Becomes Unavailable
The listener receives an exception, which is recorded in the log file. When the target system becomes available again, the listener starts receiving IDocs again.
2.3.11 Configuring SNC to Secure Communication Between Oracle Identity Manager and the Target System
Oracle Identity Manager uses a Java application server. To connect to the SAP system application server, this Java application server uses the SAP Java connector (JCo). If required, you can use Secure Network Communication (SNC) to secure communication between Oracle Identity Manager and the SAP system.
This section discusses the following topics:
2.3.11.1 Prerequisites for Configuring the Connector to Use SNC
The following are prerequisites for configuring the connector to use SNC:
- SNC must be activated on the SAP application server.
- You must be familiar with the SNC infrastructure. You must know which Personal Security Environment (PSE) the application server uses for SNC.
2.3.11.2 Installing the Security Package
To install the security package on the Java application server used by Oracle Identity Manager:
2.3.11.3 Configuring SNC
To configure SNC:
-
Either create a PSE or copy the SNC PSE of the SAP application server to the SECUDIR directory. To create the SNC PSE for the Java application server, use the sapgenpse.exe command-line tool as follows:
-
To determine the location of the SECUDIR directory, run the
sapgenpsecommand without specifying any command options. The program displays information such as the library version and the location of the SECUDIR directory. -
Enter a command similar to the following to create the PSE:
sapgenpse get_pse -p PSE_Name -x PIN Distinguished_Name
The following is a sample distinguished name:
CN=SAPJ2EE, O=MyCompany, C=US
The
sapgenpsecommand creates a PSE in the SECUDIR directory.
-
-
Create credentials for the Java application server.
The Java application server must have active credentials at run time to be able to access its PSE. To check whether or not this condition is met, enter the following command in the parent directory of the SECUDIR directory:
Sapgenpse seclogin
Then, enter the following command to open the PSE of the server and create the credentials.sapgenpse file:
seclogin -p PSE_Name -x PIN -O [NT_Domain\]user_ID
The
user_IDthat you specify must have administrator rights.PSE_NAMEis the name of the PSE file.The credentials file, cred_v2, for the user specified with the
-Ooption is created in the SECUDIR directory. -
Exchange the public key certificates of the two servers as follows:
Note:
If you are using individual PSEs for each certificate of the SAP server, then you must perform this procedure once for each SAP server certificate. This means that the number of times you must perform this procedure is equal to the number of PSEs.
-
Export the Oracle Identity Manager certificate by entering the following command:
sapgenpse export_own_cert -o filename.crt -p PSE_Name -x PIN
-
Import the Oracle Identity Manager certificate into the SAP application server. You may require the SAP administrator's assistance to perform this step.
-
Export the certificate of the SAP application server. You may require the SAP administrator's assistance to perform this step.
-
Import the SAP application server certificate into Oracle Identity Governance by entering the following command:
sapgenpse maintain_pk -a serverCertificatefile.crt -p PSE_Name -x PIN
-
-
Configure the following parameters in the SAP HRMS IT Resource object:
-
SAP lib
-
SAP mode
-
SAP myname
-
SAP partnername
-
SAP qop
-
2.3.12 Specifying Values for the Connection Properties (IT Resource Configuration)
The IT resource holds connection properties that are used by SAP JCo. These connection properties are the ones accepted by the SAP JCo. The Lookup.SAP.HRMS.ITResourceMapping lookup definition holds mappings between the connection properties accepted by the SAP JCo API and the names of IT resource parameters.
Note:
The IT resource is used only during incremental reconciliation. In full reconciliation, you manually copy th e flat file containing user data to the Oracle Identity Manager host computer. See the Javadocs shipped with SAP JCo 3.0.8 for detailed information about connection properties used by the target system.This section discusses the following topics:
-
To meet the requirements of your operating environment, you might need to add connection properties to this default set of properties. For example, if the target system is behind a firewall, then you must also provide a value for the jco.client.saprouter connection property. To add a connection property, see the Mapping New Connection Properties.
-
For instructions on specifying values for the IT resource parameters, see the Configuring the IT Resource.
-
If your target system is a group of SAP instances that provide a load-balancing connection to applications such as Oracle Identity Manager, then perform the procedure described in the Parameters for Enabling the Use of a Logon Group.
2.3.12.2 Configuring the IT Resource
You must specify values for the parameters of the SAP HRMS IT resource as follows:
2.3.12.3 Parameters for Enabling the Use of a Logon Group
In SAP, a logon group is used as a load-sharing mechanism. When a user logs in to a logon group, the system internally routes the connection request to the logon group member with the least load.
The following parameters of the IT resource are used to enable this feature. These parameters are explained in Table 2-6.
- Group name
- Message server
- R3 name
In addition, perform the following procedure on the Oracle Identity Manager host computer to enable SAP JCo connectivity:
- Open the following file in a text editor:
For Microsoft Windows:
C:\WINDOWS\system32\drivers\etc\services
For Solaris or Linux, open the following file:
/etc/services
- Add an entry in the following format:
Note:
Ensure that you add the entry in the correct ascending order of the port number as shown in the example.sapmsSYSTEM_ID 36SYSTEM_NUMBER/tcp
For example:. . . ipx 213/udp #IPX over IP sapmsE60 3600/tcp ldap 389/tcp #Lightweight Directory Access Protocol . . .
- Save and close the file.
- Create the sapmsg.ini file and add the following lines in the file:
[Message Server] o01=oss001.wdf.sap-ag.de SYSTEM_ID=HOST_NAME
For example:[Message Server] o01=oss001.wdf.sap-ag.de E60=mysap08.corp.example.com
- Save and close the file.
- On the Oracle Identity Manager host computer, copy the file into the C:\Windows directory or the root directory (depending on the operating system running on the host).
2.3.13 Creating an Authorization Policy
The procedure described in this section is applicable only if you are using Oracle Identity Manager release 11.1.x.
On Oracle Identity Manager release 11.1.x, to create an authorization policy, see the instructions given in Managing Authorization Policies of Oracle Fusion Middleware Performing Self Service Tasks with Oracle Identity Manager. The following instructions are specific to individual steps of the procedure described in the "Creating an Authorization Policy for User Management" section of that chapter:
- When you reach Step 3, in the Policy Name field, enter a name for the policy. For example:
Personnel Number Authorization Policy - When you reach Step 4, in the Description field, enter a description for the policy. For example:
Personnel Number Authorization Policy - When you reach Step 7:
In the Permissions table, select the following check boxes in the Enable column:
- Modify User Profile
- Search User
- View User Details
Click Edit Attributes.
On the Attribute Settings page, clear all the check boxes, select Personnel Number, User created from HRMS, and Manager. Then, click Save.
2.3.14 Displaying UDFs in Oracle Identity Manager 11.1.2 or Later
In Oracle Identity Manager release 11.1.2 or later, some of the user attributes (UDFs) such as City, Cost Center, Department, District, Group, Job Position, Org Unit, Personnel Number, Manager, SAP Linked User ID, Sub Group, User Created from HRMS are not displayed after running the SAP HRMS User Recon.
If you want to display these attributes as form fields in the Oracle Identity Manager user interface, you must customize the associated pages on the interface to add custom form fields. To do so, perform the following procedure:
- Log in to Oracle Identity System Administration.
- Create and activate a sandbox.
- From the Identity System Administration Console, in the Upgrade region, click Upgrade User Form. All the UDFs are listed.
- Click Upgrade.
- Publish the sandbox.
2.4 Upgrading the Connector
You can upgrade the SAP ER connector while in production, and with no downtime. Your customizations remain intact and the upgrade will be transparent to your users. All form field names are preserved from the legacy connector.
To upgrade the SAP ER connector, perform the procedures described in the following sections:
Note:
-
Before you perform the upgrade procedure, it is strongly recommended that you create a backup of the Oracle Identity Manager database. Refer to MoS: OIM 11gR2: Schema Backup and Restoration using Data Pump Client Utility (Doc ID 1492129.1) from OIM perspective.
-
As a best practice, first perform the upgrade procedure in a test environment.
See Also:
Upgrading Connectors in Oracle Fusion Middleware Administering Oracle Identity Manager for detailed information on these steps
2.4.1 Prerequisites for Upgrading the Connector
Before you perform an upgrade operation or any of the upgrade procedures, you must perform the following actions:
-
Perform a reconciliation run to fetch all latest updates to Oracle Identity Manager.
-
Define the source connector (an earlier release of the connector that must be upgraded) in Oracle Identity Manager. You define the source connector to update the Deployment Manager XML file with all customization changes made to the connector.
-
Run the Oracle Identity Manager Delete JARs utility to delete the old connector bundle to the Oracle Identity Manager database.
See Also:
Delete JAR Utility in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance for detailed information about the Delete JARs utility2.4.2 Upgrading the Connector
This is a summary of the procedure to upgrade the connector for both staging and production environments.
Depending on the environment in which you are upgrading the connector, perform one of the following steps:
-
Staging Environment
Perform the upgrade procedure by using the wizard mode.
-
Production Environment
Perform the upgrade procedure by using the silent mode.
See Also:
Managing Connector Lifecycle of Oracle Fusion Middleware Administering Oracle Identity Governance for detailed information about the wizard and silent modes2.4.3 Performing the Postupgrade Steps
Perform the procedure described in this section to complete the steps that are required to post-upgrade.
- Run the Oracle Identity Manager Upload JARs utility to post the new connector bundle to the Oracle Identity Manager database.
- From the Advanced menu, select Configuration and then select IT Resource and configure the IT resources created as part of this connector.
- From the Sysadmin console menu, select Management and then select Scheduled Job and configure the jobs that are already created for the connector.
- From the field name reference in the lookup definition (if any duplicates), processed task literals and adapters must be updated according to the old form names.
See Also:
Upload JAR Utility in Oracle Fusion Middleware Developing and Customizing Applications for Oracle Identity Governance for detailed information about the Upload JARs utility - Upgrading the connector will generate duplicate entries in Lookups, you must manually delete these duplicate entries. Perform the postupgrade procedure documented in Managing Connector Lifecycle of Oracle Fusion Middleware Administering Oracle Identity Manager.