1 About the CA Top Secret Advanced Connector
The CA Top Secret Advanced connector integrates Oracle Identity Manager with a CA Top Secret target system. This connector lets you use CA Top Secret as a managed (target) resource of identity data for Oracle Identity Manager.
This chapter contains the following topics:
Introduction to the Connector
In the account management (target resource) mode of the connector, information about users (ACIDs) created or modified directly on the target system can be reconciled into Oracle Identity Manager. In addition, you can use Oracle Identity Manager to perform provisioning operations on the target system.
Certified Components
These are the software components and their versions required for installing and using the connector.
Table 1-1 Certified Components
| Item | Requirement |
|---|---|
|
Oracle Identity Manager or Oracle Identity Governance |
You can use one of the following releases of Oracle Identity Manager or Oracle Identity Governance:
|
|
JDK |
The JDK version can be one of the following:
|
|
Target systems |
CA Top Secret R15 or R16 running on IBM z/OS version 2.2, 2.3, 2.4, or 2.5 |
|
Infrastructure requirement for the message transport layer between Oracle Identity Manager and the mainframe environment |
TCP/IP |
|
Target system user account for reconciliation and provisioning operations |
CA Top Secret authorized user account with System Administrators privileges During installation of the mainframe agents, the <HLQ>.JCLLIB.TOPSDEF job automatically creates user accounts (ACIDs) with System Administrators privileges. |
|
Pioneer and Voyager |
Pioneer and Voyager are written in single thread LE Cobol. They were developed to run above the 16M line. Options that can adversely affect these STCs are LE run options: ALL31(OFF) instead of ON STACK(,,,BELOW,,) instead of STACK(,,,ANYWHERE,,) |
|
LDAP Gateway |
The computer hosting the LDAP Gateway must run the following software:
|
Certified Languages
The connector supports the following languages:
-
Arabic
-
Chinese (Simplified)
-
Chinese (Traditional)
-
Danish
-
English
-
French
-
German
-
Italian
-
Japanese
-
Korean
-
Portuguese (Brazilian)
-
Spanish
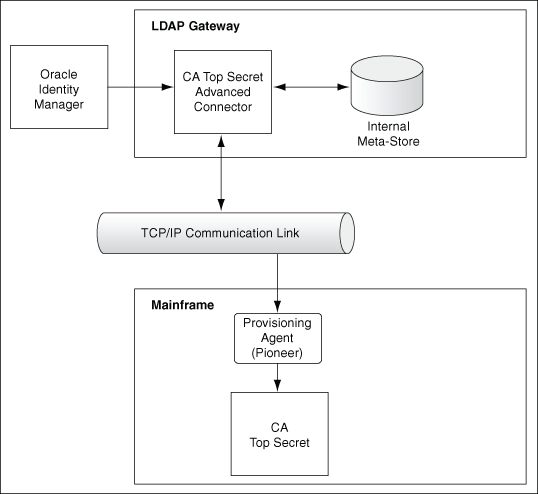
Connector Architecture
Connectors require certain architecture consisting of Gateways and Provisioning Agent.
This section contains the following topics:
About the Connector Components
The CA Top Secret Advanced connector contains the following components:
-
LDAP Gateway: The LDAP Gateway receives instructions from Oracle Identity Manager in the same way as any LDAP version 3 identity store. These LDAP commands are then converted into native commands for CA Top Secret and sent to the Provisioning Agent. The response, which is also native to CA Top Secret, is parsed into an LDAP-format response and returned to Oracle Identity Manager.
During reconciliation, the LDAP Gateway receives event notification, converts the events to LDAP format, and then forwards them to Oracle Identity Manager, or events can be stored in the LDAP Gateway internal store and pulled into Oracle Identity Manager by a scheduled task.
-
Provisioning Agent (Pioneer): The Pioneer Provisioning Agent is a mainframe component. It receives native mainframe CA Top Secret identity and authorization change events from the LDAP Gateway. These events are processed against the CA Top Secret authentication repository, in which all provisioning updates from the LDAP Gateway are stored. The response is parsed and returned to the LDAP Gateway.
Note:
At some places in this guide, the Provisioning Agent is referred to as Pioneer.
-
Reconciliation Agent (Voyager): The Reconciliation Agent captures mainframe events by using a Top Secret exit, which is a program run after events in CA Top Secret are processed. These events include the ones generated at TSO logins, the command prompt, batch jobs, and other native events. These events are stored in the subpool cache area that is established by a supplied, standard z/OS procedure (STARTUP). The Reconciliation Agent captures these events, transforms them into LDAPv3 protocol notification messages, and then sends them to Oracle Identity Manager through the LDAP Gateway.
Note:
At some places in this guide, the Reconciliation Agent is referred to as Voyager.
-
Message Transport Layer: This connector supports a message transport layer by using the TCP/IP protocol, which is functionally similar to proprietary message transport layer protocols. In addition, the connector provides AES encryption for messages sent and received through the transport layer.
The AES encryption is performed using 128-bit cryptographic keys. In addition, Encryption and Decryption programs are supplied in the Distribution Load Library. The encryption or decryption does not require any network software or hardware.
Connector Operations
This section provides an overview of the following processes involving the CA Top Secret Connector.
This section contains these topics:
Full Reconciliation Process
Full reconciliation involves fetching existing user data from the mainframe to Oracle Identity Manager. This user data is converted into accounts or resources for OIM Users.
Figure 1-1 shows the flow of data during full reconciliation.
Figure 1-1 Full Reconciliation Process for CA Top Secret Connector
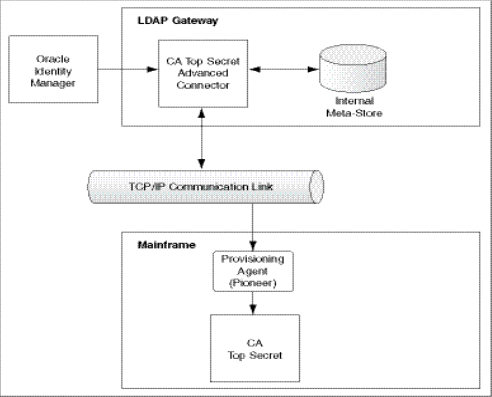
Description of "Figure 1-1 Full Reconciliation Process for CA Top Secret Connector"
The following is a summary of the full reconciliation process:
Note:
The detailed procedure is explained later in this guide.
-
Set values for the attributes of the Reconcile All Users scheduled task and run it. The task sends a search request to the LDAP Gateway.
-
The LDAP Gateway encrypts the search request and then sends it to the Provisioning Agent on the mainframe.
-
The Provisioning Agent encrypts user profile data received from CA Top Secret and then passes this data to the LDAP Gateway.
-
The LDAP Gateway decrypts the user profile data. If the user profile data does not include any changes when compared to the OIM user's existing resource data, then the event is ignored and reconciliation continues with the next user on the target system. If the user profile data includes a change, then the LDAP Gateway passes the data on to Oracle Identity Manager.
-
This user profile data is converted into accounts or resources for OIM Users.
CFILE Reconciliation Process
CFILE reconciliation involves fetching existing user data in the form of a TSSCFILE extract from the mainframe to Oracle Identity Manager. This user data is converted into accounts or resources for OIM Users.
Instead of reconciling directly from the target system to OIM (which can be slow on large systems), the LDAP gateway offers an internal LDAP store that can be populated with target system users by using a single transaction to the mainframe. Oracle Identity Manager then reconciles user data from the LDAP store instead of the target system.
Reconciling user, profile, and facility data from an extract file requires the following procedure:
Note:
The detailed procedure is explained later in this guide.
-
Generate an extract file of the user data by executing the TSSCFILE job on the CA Top Secret system.
Note that the TSSCFILE job is supplied as part of <hlq>.JCLLIB in the connector installation package.
-
Set values for the attributes of the Top Secret Reconcile Users to Internal LDAP scheduled task and run it. The task sends a request to the LDAP gateway to retrieve the extract file from Pioneer.
-
The Provisioning Agent receives the request from LDAP Gateway and reads the data from the extract dataset.
-
The Provisioning Agent encrypts the user data and passes it to the LDAP Gateway.
-
The LDAP Gateway decrypts the user profile data. The data is stored in the LDAP Gateway's internal data-store.
-
Set values for the attributes defined in the TSS Reconcile LDAP Users to OIM scheduled task.
-
Run the scheduled task. The next step depends on the setting in the IT resource as mentioned below:
-
If you set the "Last Modified Time Stamp" property to 0, then all the user profile data is retrieved from the LDAP internal store.
-
If you configure the "Last Modified Time Stamp" property with a timestamp, then only the user profile data updated since the timestamp is retrieved from the LDAP internal store.
-
-
The next step depends on the user data as mentioned below:
-
If the user profile data does not include any changes when compared to the OIM user's existing resource data, then the event is ignored and reconciliation continues with the next retrieved user.
-
If the user profile data includes a change, then the LDAP Gateway passes the data on to Oracle Identity Manager. The user profile data is converted into accounts or resources for OIM Users.
-
Incremental (Real-Time) Reconciliation Process
Incremental or real-time reconciliation is initiated by the exit that works in conjunction with the Reconciliation Agent. Figure 1-2 shows the flow of data during this form of reconciliation.
Figure 1-2 Reconciliation Process for CA Top Secret Connector
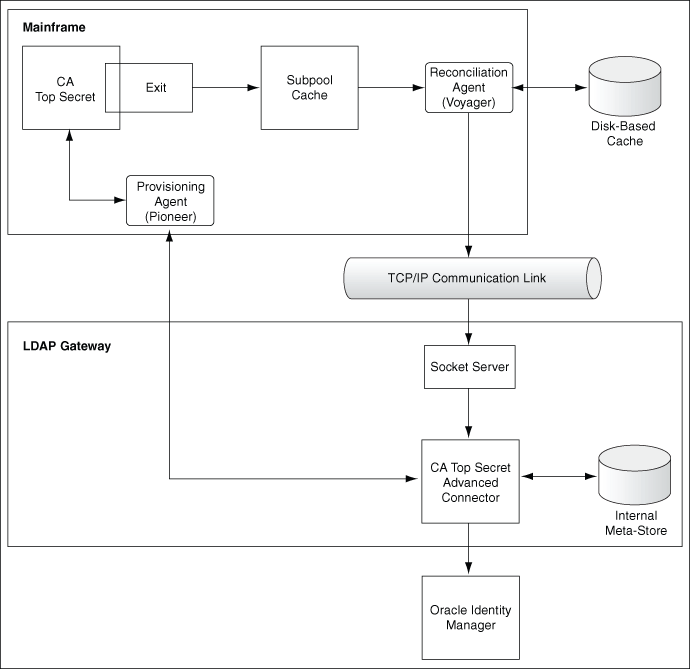
Description of "Figure 1-2 Reconciliation Process for CA Top Secret Connector"
Performing (Real-Time) Reconciliation
If you want to perform a (Real Time) reconciliation the following is a summary of this process:
-
Incremental reconciliation begins when a user is created or, updated on CA Top Secret. This event might take place either directly on the mainframe or in response to a provisioning operation on Oracle Identity Manager.
-
TSSINSTX is a standard CA Top Secret exit. This exit is used in conjunction with the Reconciliation Agent. The exit detects the event and sends a message containing user data to Subpool 231 (cache).
-
The Reconciliation Agent polls Subpool 231. When it finds the message in the subpool, it reads the message into its buffer. This frees up the subpool.
-
The Reconciliation Agent opens up a connection with the LDAP Gateway, and then sends the message to the gateway over TCP/IP.
Note:
Messages sent to the LDAP Gateway are encrypted using AES-128 encryption.
-
The LDAP Gateway decrypts the user profile data. If the user profile data does not include any changes when compared to the OIM user's existing resource data, then the event is ignored and reconciliation continues with the next user on the target system. If the user profile data includes a change, then the LDAP Gateway can store the data internally for use by a scheduled task, or it can pass the data on to Oracle Identity Manager.
-
Oracle Identity Manager processes the message and creates or updates either the corresponding CA Top Secret resource or the OIM User.
Provisioning Process
Figure 1-3 shows the flow of data during provisioning.
The following is a summary of the provisioning process:
-
Provisioning data submitted from Oracle Identity Self Service is sent to the LDAP Gateway.
-
The LDAP Gateway converts the provisioning data into mainframe commands, encrypts the commands, and converts the message from ASCII to EBCDIC.
-
The Provisioning Agent executes the commands and runs them on the mainframe and within the Pioneer STC (Started Task) using the RACF API (IRRSEQ00).
-
The Provisioning Agent converts the RACF API output to ASCII and encrypts the message prior to sending it back to the LDAP Gateway.
-
The outcome of the operation on the mainframe is displayed on Identity Self Service. A more detailed message is recorded in the connector log file.
Connector Features
The features of the connector include support for full and incremental reconciliation, encrypted communication, and high availability.
The following are the features of the connector:
Support for Target Resource Reconciliation
You can configure the connector as a target resource of Oracle Identity Manager.
Full and Incremental Reconciliation
After you deploy the connector, you can perform full reconciliation to bring all existing user data from the target system to Oracle Identity Manager. After the first full reconciliation run, change-based or incremental reconciliation is automatically enabled and active. Incremental reconciliation is a real-time process.
User changes on the target system are directly sent to Oracle Identity Manager or stored in the LDAP Gateway internal store.
You can perform a full reconciliation run at any time. See Performing Full Reconciliation for more information.
Encrypted Communication Between the Target System and Oracle Identity Manager
AES-128 encryption is used to encrypt data that is exchanged between the LDAP Gateway, and the Reconciliation and Provisioning Agents on the Mainframe. This encryption is taken care by the Mainframe agents.
High Availability Feature of the Connector
The following are component-failure scenarios and the response of the connector to each scenario.
-
Scenario 1: The Reconciliation Agent is running and the LDAP Gateway stops responding
-
The Reconciliation Agent stops sending messages (event data) to the LDAP Gateway.
-
Messages that are not sent are stored in the subpool cache.
-
When the LDAP Gateway is brought back online, the Reconciliation Agent reads data from the subpool cache and then sends messages to the LDAP Gateway.
-
-
Scenario 2: The LDAP Gateway is running and the Reconciliation Agent stops responding
-
Event data is sent to the subpool cache.
-
When the Reconciliation Agent is brought back online, it reads data from the subpool cache and then sends messages to the LDAP Gateway.
Note:
During SHUTDOWN, there is a possibility that events that had been sent to the LDAP might be saved and re-sent again once the Agent is brought back online. This is to ensure no data lose and this process will re-list the event data to provide the most current view.
-
-
Scenario 3: The LDAP Gateway is running and the mainframe stops responding
-
Messages that are in the subpool cache are written to disk.
-
When the mainframe is brought back online, event data written to disk is again stored in the subpool cache.
-
The Reconciliation Agent reads data from the subpool cache and then sends messages to the LDAP Gateway.
Note:
During SHUTDOWN, there is a possibility that events that had been sent to the LDAP might be saved and re-sent again once the Agent is brought back online. This is to ensure no data lose and this process will re-list the event data to provide the most current view.
-
-
Scenario 4: The LDAP Gateway is running and the Provisioning Agent or mainframe stops responding
The process task that sends provisioning data to the LDAP Gateway retries the task.
-
Scenario 5: The subpool is stopped by an administrator
If the subpool is stopped by an administrator, then it shuts down the Reconciliation Agent, thereby destroying any messages that are not transmitted. However, the messages in the AES-encrypted file are not affected and can be recovered.
Connector Objects Used During Reconciliation and Provisioning
These are the connector objects that used during reconciliation and provisioning operations.
Supported Functions for Target Resource Reconciliation
The connector supports reconciliation of user data from these events.
-
Create user
-
Modify user
-
Password Interval changes
-
Change password
-
Reset password
-
Disable user
-
Delete user
-
Enable user
-
Group Membership Changes
-
Create group data
-
Modify group data
-
Delete groups
-
Audit information
Supported Functions for Provisioning
These are the provisioning functions that the connector supports.
Table 1-2 Supported Functions for Provisioning
| Function | Description |
|---|---|
|
Create user |
Adds new users in CA Top Secret |
|
Modify user |
Modifies user information in CA Top Secret |
|
Change password |
Changes user passwords in CA Top Secret in response to password changes made in Oracle Identity Manager through user self-service |
|
Reset password |
Resets user passwords in CA Top Secret The passwords are reset by the administrator. |
|
Disable user |
Disables users in CA Top Secret |
|
Enable user |
Enables users in CA Top Secret |
|
Delete users |
Removes users from CA Top Secret |
|
Authenticate users |
Validates user's LoginId and Password |
|
Create profiles |
Adds new profiles to CA Top Secret |
|
Modify profiles |
Modifies profiles information in CA Top Secret |
|
Delete profiles |
Removes profiles from CA-Top Secret |
|
Define resources |
Define new resources to CA Top Secret |
|
Alter resources |
Modify resources in CA Top Secret |
| Delete resources |
Remove resources from CA Top Secret |
| Search All Users | Retrieves all users with current data from CA-Top Secret |
| Search All Profiles | Retrieves all profiles with current data from CA-Top Secret |
| Search All Departments | Retrieves all departments with current data from CA-Top Secret |
| Search All Resources | Retrieves all resources with current data from CA-Top Secret |
| Search All Datasets | Retrieves all datasets with current data from CA-Top Secret |
|
Grant users access to data sets and general resources |
Permits users access to a CA Top Secret dataset or resource |
|
Grant users access to privileges (TSO) |
Provides TSO login access to users or other privileges |
| Assign profile membership | Add or remove user from profiles in CA Top Secret |
|
Grant user TSO attributes |
Provides TSO information |
|
Grant User NETVIEW attributes |
Provides NETVIEW information |
|
Grant User CICS attributes |
Provides CICS information |
|
Grant User Custom Segment attributes |
Provides custom segment support for user-defined information |
|
Grant User OMVS attributes |
Provides OMVS information |
User Attributes for Target Resource Reconciliation and Provisioning
The CA Top Secret connector uses three categories of attributes: mapped, unmapped, and custom.
Mapped and unmapped attributes are supported in the LDAP Gateway, but unmapped attributes are not shipped with preconfigured OIM metadata such as form fields, process tasks, or reconciliation mappings.
Custom attributes require additional configuration steps in the LDAP Gateway. See Adding Custom Fields for Target Resource Reconciliation through Adding Custom Fields for Provisioning for more information.
Table 1-3 lists the major differences between attribute types.
Table 1-3 Attribute Characteristics of CA Top Secret Connector
| Attribute Type | Out-of-the-box OIM Metadata Support | Out-of-the-box LDAP Support | Additional LDAP Configuration Required |
|---|---|---|---|
|
Mapped |
Yes |
Yes |
No |
|
Unmapped |
No |
Yes |
No |
|
Custom |
No |
No |
Yes |
Table 1-4 lists mapped attribute mappings between CA Top Secret and Oracle Identity Manager. The OnBoardUser and ModifyTopsUser adapters are used for Create User and Modify User provisioning operations, respectively.
Table 1-4 Mapped User Attributes for Target Resource Reconciliation and Provisioning of CA Top Secret Connector
| Process Form Field | CA Top Secret Attribute Display Name | Description |
|---|---|---|
|
USER_ID |
USER |
Login ID of the user |
|
FULL_NAME |
NAME |
Full name of the user |
|
Password |
PASSWORD |
Password |
|
department |
DEPARTMENT |
Default department of the user Note: Provisioning is done using "department" attribute but reconciliation brings department's full name in "department" attribute and the acid value is brought in DEPTACID. |
|
deptacid |
DEPARTMENT |
Default department of the user Note: Provisioning is done using "department" attribute but reconciliation brings department's full name in "department" attribute and the acid value is brought in DEPTACID. |
|
instdata |
DATA |
Installation-defined data of the user |
|
createdate |
CREATED |
Date user was created |
|
passwordExpire |
EXPIRES |
Expire the user's password |
|
passwordExpireInterval |
INTERVAL |
Number of days the user's password remains valid |
|
suspendUntilDate |
SUSPENDED DATE |
Future date on which the user will be prevented from accessing the system |
|
divacid |
DIVISION |
Default division for the user Note: Provisioning is done using "division" attribute but reconciliation brings division's full name in "division" attribute and the acid value is brought in "divacid." |
|
division |
DIVISION |
Default division for the user Note: Provisioning is done using "division" attribute but reconciliation brings division's full name in "division" attribute and the acid value is brought in "divacid." |
|
lastmodificationdate |
LAST MOD |
Last time the user connected |
|
tsocommand |
COMMAND |
Command to be run during TSO/E logon |
|
tsodest |
DEST |
Default SYSOUT destination |
|
tsounit |
UNIT |
Default unit name for allocations |
|
tsoudata |
USERDATA |
Site-defined data field for a TSO user |
|
tsolacct |
ACCTNUM |
Default TSO account number on the TSO/E logon panel |
|
tsohclass |
HOLDCLASS |
Default hold class |
|
tsojclass |
JOBCLASS |
Default job class |
|
tsomsize |
MAXSIZE |
Maximum region size the user can request at logon |
|
tsomclass |
MSGCLASS |
Default message class |
|
tsolproc |
PROC |
Default logon procedure on the TSO/E logon panel |
|
tsolsize |
SIZE |
Minimum region size if not requested at logon |
|
tsoopt |
OPT |
TSO options, such as MAIL and NOTICES |
|
tsosclass |
SYSOUTCLASS |
Default SYSOUT class |
|
zone |
ZONE |
Display name of default zone for the user |
|
zoneAcid |
ZONE ACID |
Default zone for the user |
| PASSPHRASE | PASSPHRASE |
Password phrase |
|
PHRASEONLY |
PHRASEONLY |
Valid values are The LDAP gateway and Mainframe TOPS Pioneer agent will allow provisioning and reconcile of the PHRASEONLY attribute |
| PHRASE_EXPIRE | PHRASEEXPIRE |
Number of days before a password phrase expires |
| PHRASE_EXPIRE_INTERVAL | PHRASE EXPIRE INTERVAL |
Passphrase expiration interval |
The Top Secret connector supports provisioning and reconciliation of additional attributes that are not included on the main process form or preconfigured with process tasks and reconciliation mappings.
Table 1-5 lists unmapped the attribute mappings between CA Top Secret and Oracle Identity Manager. The adpModifyTopsUser adapter is used for Modify User provisioning operations, respectively.
Table 1-5 Unmapped User Attributes for Target Resource Reconciliation and Provisioning of CA Top Secret Connector
| LDAP Gateway Name | CA Top Secret Attribute | Description | Supported Operations |
|---|---|---|---|
|
lu62#appl |
#APPL |
LU 6.2 #APPL |
Both |
|
lu62#entity |
#ENTITY |
LU 6.2 #ENTITY |
Both |
|
lu62bc1chain |
BC1CHAIN |
LU 6.2 BC1CHAIN |
Both |
|
lu62bc2chain |
BC2CHAIN |
LU 6.2 BC2CHAIN |
Both |
|
lu62set1disp |
SET1DISP |
LU 6.2 SET1DISP |
Both |
|
lu62set2disp |
SET2DISP |
LU 6.2 SET2DISP |
Both |
|
waaccnt |
WAACCNT |
APPC SYSOUT ACCT NUMBER |
Both |
|
waaddr1 |
WAADDR1 |
APPC SYSOUT ADDRESS 1 |
Both |
|
waaddr2 |
WAADDR2 |
APPC SYSOUT ADDRESS 2 |
Both |
|
waaddr3 |
WAADDR3 |
APPC SYSOUT ADDRESS 3 |
Both |
|
waaddr4 |
WAADDR4 |
APPC SYSOUT ADDRESS 4 |
Both |
|
wabldg |
WABLDG |
APPC SYSOUT BUILDING |
Both |
|
wadept |
WADEPT |
APPC SYSOUT DEPARTMENT |
Both |
|
waname |
WANAME |
APPC SYSOUT NAME |
Both |
|
waroom |
WAROOM |
APPC SYSOUT ROOM |
Both |
|
tsodefprfg |
TSODEFPRFG |
DEFAULT PERFORMANCE GROUP |
Both |
|
tsompw |
TSOMPW |
MULTIPLE PASSWORDS |
Both NOTE: In reconciliation, the attribute is stored as "attributes" with value of "TSOMPW". |
|
tsoacct |
TSOACCT |
SECURE TSO LOGON ACCOUNT CODES |
Provisioning Only |
|
tsoauth |
TSOAUTH |
SECURE TSO USER ATTRIBUTES |
Provisioning Only |
|
tsoprfg |
TSOPRFG |
SECURE TSO PERFORMANCE GROUPS |
Provisioning Only |
|
tsoproc |
TSOPROC |
SECURE TSOP LOGON PROCS |
Provisioning Only |
|
defaultGroup |
DFLTGRP |
OMVS DEFAULT GROUP |
Both |
|
omvsProgram |
OMVSPGM |
OMVS PROGRAM |
Both |
|
omvsUid |
UID |
OMVS USER ID |
Both |
|
omvsHome |
HOME |
OMVS HOME SUBDIRECTORY |
Both |
|
omvsGid |
GID |
OMVS GROUP ID |
Both |
|
omvsAssize |
ASSIZE |
OMVS MAX ADDRESS SPACE SIZE |
Both |
|
omvsMmaparea |
MMAPAREA |
OMVS MAX DATASPACE PAGES |
Both |
|
omvsOecputm |
OECPUTM |
OMVS MAX CPU TIME |
Both |
|
omvsoeflep |
OEFILEP |
OMVS MAX FILES PER PROCESS |
Reconciliation Only |
|
omvsProcuser |
PROCUSER |
OMVS MAX PROCESSES |
Both |
|
omvsThreads |
THREADS |
OMVS MAX PTHREADS CREATED |
Both |
|
netviewMsgrecvr |
MSGRECVR |
NETVIEW RECEIVE UNSOLICITED MESSAGES |
Both |
|
netviewInitcmd |
IC |
NETVIEW INITIAL COMMAND |
Both |
|
netviewControl |
CTL |
NETVIEW SECURITY CHECK TYPE |
Both |
|
netviewOpclass |
OPCLASS |
NETVIEW SCOPE CLASS |
Both |
|
netviewDomains |
DOMAINS |
NETVIEW CROSS-DOMAIN SESSIONS |
Both |
|
netviewNgmfadmn |
NGMFADMN |
NETVIEW GRAPHICAL DISPLAY ADMIN |
Both |
|
netviewConsName |
CONSNAME |
NETVIEW EXTENDED CONSOLE NAME |
Both |
|
cicsOpclass |
OPCLASS |
CICS OPERATOR CLASSES |
Both |
|
cicsOpident |
OPIDENT |
CICS OPERATOR IDENTIFICATION VALUE |
Both |
|
cicsOpprty |
OPPRTY |
CICS OPERATOR PRIORITY |
Both |
|
cicsSctykey |
SCTYKEY |
CICS SECURITY KEYS |
Both |
|
cicsSitran |
SITRAN |
CICS TRANSACTION FOLLOWING FACILITY SIGN-IN |
Both Note: To provision cicsSitran, you must map the process task to the adpModifySitranTopsUser adapter instead of adpModifyTopsUs. |
|
cicsSitranFacility |
SITRAN FACILITY |
CICS FACILITY ASSOCIATED WITH TRANSACTION |
Both Note: To provision cicsSitranFacility, you must map the process task to the adpModifySitranTopsUser adapter instead of adpModifyTopsUser. |
|
misc1 |
MISC1 |
ADMIN MISC |
Reconciliation Only |
|
misc2 |
MISC2 |
ADMIN MISC |
Reconciliation Only |
|
misc3 |
MISC3 |
ADMIN MISC |
Reconciliation Only |
|
misc4 |
MISC4 |
ADMIN MISC |
Reconciliation Only |
|
misc5 |
MISC5 |
ADMIN MISC |
Reconciliation Only |
|
misc7 |
MISC7 |
ADMIN MISC |
Reconciliation Only |
|
misc8 |
MISC8 |
ADMIN MISC |
Reconciliation Only |
|
misc9 |
MISC9 |
ADMIN MISC |
Reconciliation Only |
PROFILE Attributes for Target Resource Reconciliation and Provisioning
The connector supports reconciliation and provisioning of the PROFILE multivalued attribute. For any particular user, a child form is used to hold values of the PROFILE attributes listed in the table.
The AddUserToProfile and RemoveUserFromProfile adapters are used for PROFILE provisioning operations. Table 1-6 lists PROFILE attribute mappings between CA Top Secret and Oracle Identity Manager.
Table 1-6 PROFILE Attribute Mappings for CA Top Secret Connector
| Child Form Field | CA Top Secret Attribute | Description |
|---|---|---|
|
UD_TSSPROF_ID |
PROFILE |
Profile ID |
GROUP Attributes for Target Resource Reconciliation and Provisioning
The connector supports reconciliation and provisioning of the GROUP multivalued attribute. For any particular user, a child form is used to hold values of the GROUP attributes listed in the table.
The AddUserToGroup and RemoveUserFromGroup adapters are used for GROUP provisioning operations.
Table 1-7 lists GROUP attribute mappings between CA Top Secret and Oracle Identity Manager.
Table 1-7 GROUP Attribute Mappings for CA Top Secret Connector
| Child Form Field | CA Top Secret Attribute | Description |
|---|---|---|
|
UD_TSSGROUP_ID |
GROUP |
Group ID |
SOURCE Attributes for Provisioning
The connector supports provisioning of the SOURCE multivalued attribute. For any particular user, a child form is used to hold values of the SOURCE attributes listed in the table.
The AddUserToSource and RemoveUserFromSource adapters are used for SOURCE provisioning operations. Table 1-8 lists SOURCE attribute mappings between CA Top Secret and Oracle Identity Manager.
Table 1-8 SOURCE Attribute Mappings for CA Top Secret Connector
| Child Form Field | CA Top Secret Attribute | Description |
|---|---|---|
|
UD_TSSSOURC_ID |
SOURCE |
Source ID |
FACILITY Attributes for Target Resource Reconciliation and Provisioning
The connector supports reconciliation and provisioning of the FACILITY multivalued attribute. For any particular user, a child form is used to hold values of the FACILITY attributes listed in the table.
The AddUserToFacility and RemoveUserFromFacility adapters are used for FACILITY provisioning operations. Table 1-9 lists FACILITY attribute mappings between CA Top Secret and Oracle Identity Manager.
Table 1-9 FACILITY Attribute Mappings for CA Top Secret Connector
| Child Form Field | CA Top Secret Attribute | Description |
|---|---|---|
|
UD_TSSFAC_ID |
FACILITY |
Facility ID |
DATASET Attributes for Provisioning
The connector supports provisioning of the DATASET multivalued attribute. For any particular user, a child form is used to hold values of the DATASET attributes listed in the table.
The AddUserToDataset and RemoveUserFromDataset adapters are used for DATASET provisioning operations. Table 1-10 lists DATASET attribute mappings between CA Top Secret and Oracle Identity Manager.
Table 1-10 DATASET Attribute Mappings for CA Top Secret Connector
| Child Form Field | CA Top Secret Attribute | Description |
|---|---|---|
|
DATASET_ID |
DATASET |
Dataset ID |
|
DATASET_ACCESS |
ACCESS |
Users level of access to the dataset |
Provisioning GENCERT Operations
The connector supports provisioning operations for the TSS GENCERT command, however a pre-configured child form, process task, and adapter are not included in with the release. To provision GENCERT actions, the OIM administrator will need to create an adapter and map it to the GenerateCertificate function in the topsecret-provisioning-adapter.jar file.
The following is the function header for GenerateCertificate:
public String generateCertificate(String idfUserId, String digicert, String dcdsn, String keysize, String keyusage,String nbdate, String nbtime, String nadate, String natime, String lablcert, String altname, String subjects, String signwith, String icsf, String dsa, String pcicc)
For boolean attributes such as ICSF or DSA, the administrator should map these values as literal String values equal to either true or false.
Provisioning GENREQ Operations
The connector supports provisioning operations for the TSS GENREQ command, however a preconfigured child form, process task, and adapter are not included in with the release. To provision GENREQ actions, the OIM administrator will need to create an adapter and map it to the GenerateCertificateRequest function in the topsecret-provisioning-adapter.jar file.
The following is the function header for GenerateCertificateRequest:
public String generateCertificateRequest(String idfUserId, String digicert, String dcdsn, String lablcert)
Reconciliation Rules
During target resource reconciliation, Oracle Identity Manager tries to match each user fetched from CA Top Secret with existing CA Top Secret resources provisioned to OIM Users. This is known as process matching. A reconciliation rule is applied for process matching.
If a process match is found, then changes made to the user on the target system are copied to the resource on Oracle Identity Manager. If no match is found, then Oracle Identity Manager tries to match the user against existing OIM Users. This is known as entity matching. The reconciliation rule is applied during this process. If an entity match is found, then a CA Top Secret resource is provisioned to the OIM User. Data for the newly provisioned resource is copied from the user.
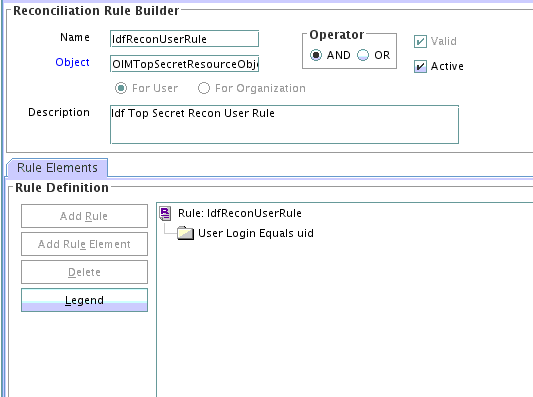
Rule name: IdfReconUserRule
Rule element: User Login Equals uid
In this rule element:
-
User Login is the User ID field on the process form and the OIM User form.
-
uid is the USER attribute on CA Top Secret.
Viewing the Reconciliation Rule
You can view the reconciliation rule for this connector from Development Tools in Oracle Identity Manager Design Console.
After you deploy the connector, you can view this reconciliation rule by performing the following steps:
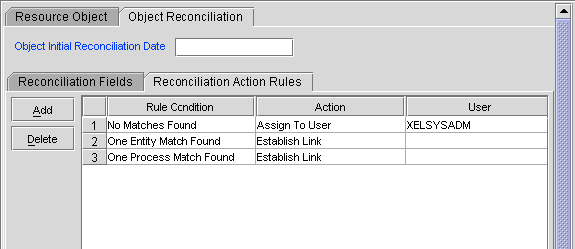
Reconciliation Action Rules
Reconciliation action rules specify actions that must be taken depending on whether or not matching CA Top Secret resources or OIM Users are found when the reconciliation rule is applied.
Table 1-11 lists the reconciliation action rules.
Table 1-11 Reconciliation Action Rules for CA Top Secret Connector
| Rule Condition | Action |
|---|---|
|
No Matches Found |
None |
|
One Entity Match Found |
Establish Link |
|
One Process Match Found |
Establish Link |