Using the JRockit Memory Leak Detector
|
|
Using the Memory Leak Detector
Now you understand how a flow of events for memory leak detection works and the basic functions of the user interface, it is time to get to know how powerful the Memory Leak Detector actually is in action. This part of the user guide describes the different tabs of the interface in detail and how the Memory Leak Detector works when monitoring a Java application with a real memory leak. Each tab of the interface will be explained in detail in this section.
The following topics will be covered in this section:
- Analyzing the Application
- Investigating a Suspicious Object Type
- Investigating an Object Instance
- Viewing Allocation Stack Traces
Analyzing the Application
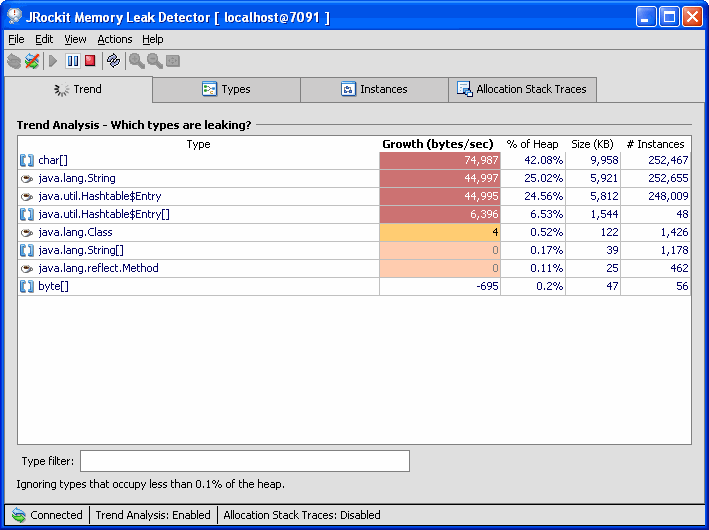
From the Trend tab (see Figure 3-1), you start the analysis of your applications. The object types with the highest growth in bytes/sec are marked red (darkest) in the Trend Analysis table and they are listed at the top of the table. For each update, the list can change and the type that was the highest move down the list. The object types listed in Figure 3-1 are fetched from an example application, where you can suspect a memory leak at the objects marked red.
Figure 3-1 Memory Leak Analysis
Table 3-1 explains what each column in the Trend tab displays.
To Start Analyzing Your Application
- Make sure the Memory Leak Detector is connected to JRockit and that your JRockit application is running with the
-Xmanagementoption turned on. - Click the Start button to start the trend analysis. If you have an application with a memory leak, the trend analysis can look something like Figure 3-1.
To Pause Analysis of Your Application
To Stop Analysis of Your Application
To Start the Investigation
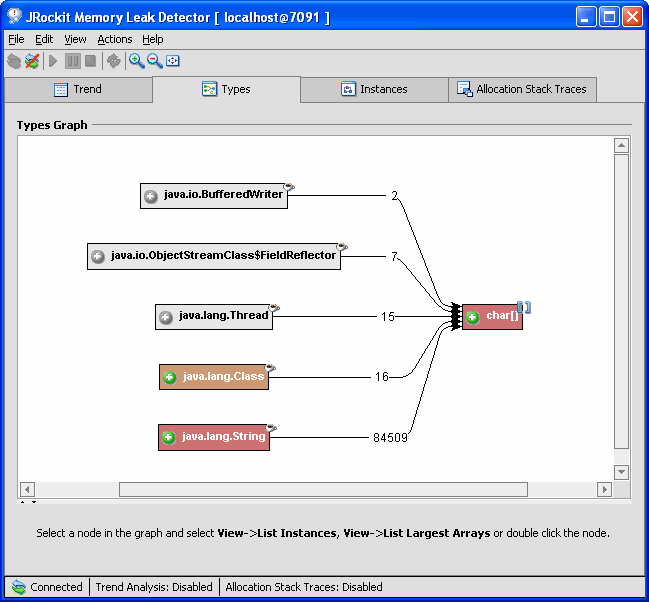
The Types tab appears (see Figure 3-2). For instructions on how to investigate further, see To Get Closer to the Memory Leaking Object.
Investigating a Suspicious Object Type
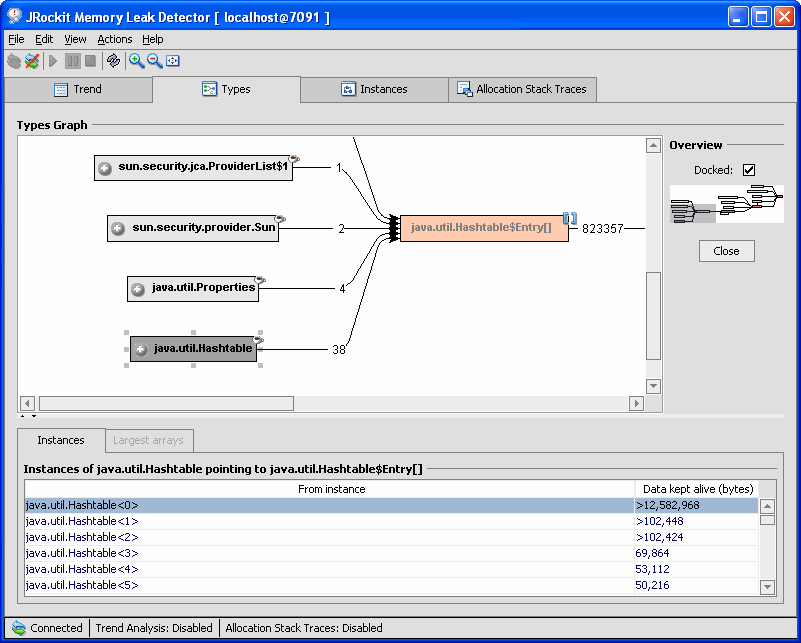
Once you have found a suspected memory leak (a type that is high in growth and is colored red), you investigate the suspected leak further in the Types tab, see Figure 3-2. Before anything is displayed in this tab, you need to start the investigation by selecting a type from the Trend tab, see To Start the Investigation.
The Types tab offers a view of the relationships between all the types pointing to the type you are investigating. For each type you also see a number, which is the number of instances that point to that type.
The color red (dark) means that the type has a high growth rate (which may or may not be related to a memory leak).
To Get Closer to the Memory Leaking Object
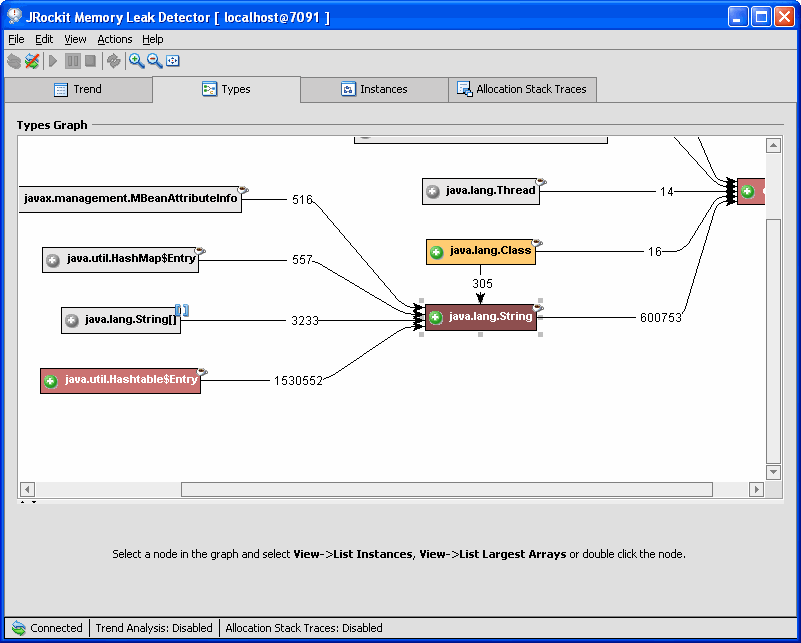
The type expands further (see Figure 3-3).
Figure 3-3 Type Graph Expanded
- Keep clicking the type with the darkest color red, until you get down to a "natural end" where you think you can pinpoint the memory leak.
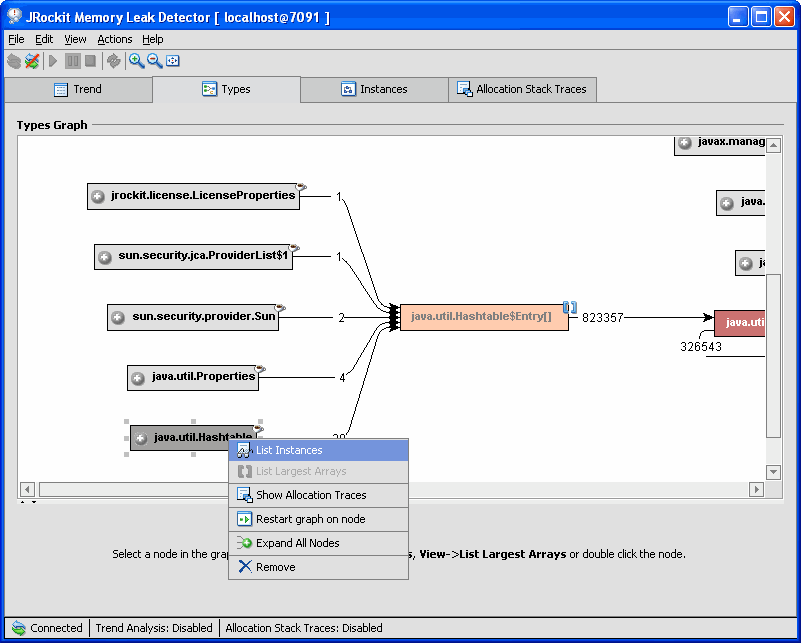
- Right-click the type where you suspect a leak (see Figure 3-4).
The Instances part of the Types tab opens.
List instances shows you instances of the selected type. The instances shown will only be those that have references to the type indicated by the arrow from the selected type in the above type graph.
Figure 3-5 List of Instances in Types Tab
The lower half of the tab lists all instances of type A pointing to type B if the instance list is not too large (see Figure 3-5). If the list is too large, the Memory Leak Detector might time out when trying to display the list. You can change the time out setting under File > Preferences.
The column Data kept alive (bytes) shows how much data a certain instance keeps alive. That data cannot be garbage collected.
Have the Overview part of the window open to see where you are in the graph (see To Get an Overview of the Graph for how to turn on the overview). You can also zoom in/out or re-center the view (see Table 2-2 for an explanation of the zooming tools).
Figure 3-4 Type Graph with Memory Leak Pinpointed
To Get an Overview of the Graph
To Investigate an Instance of a Type
The Instances tab appears (see Figure 3-6).
Investigating an Object Instance
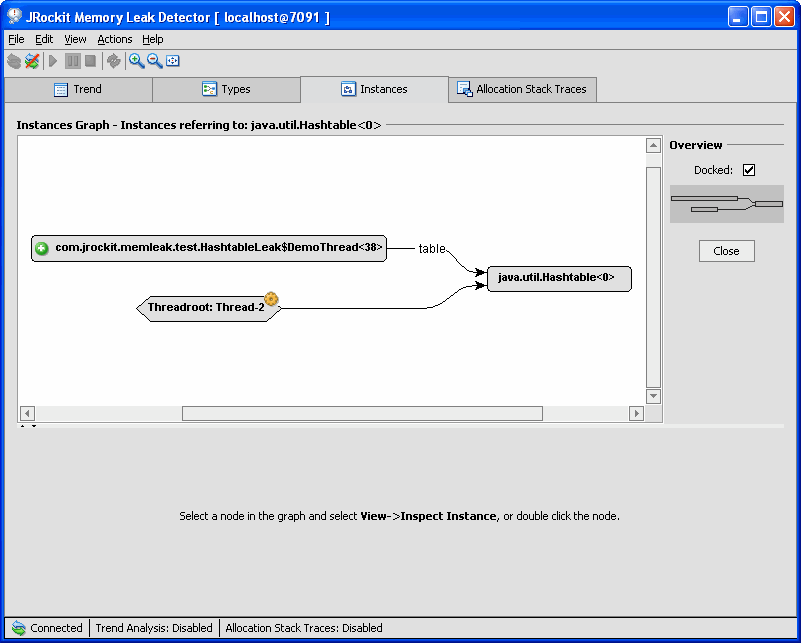
In the Instance tab, see Figure 3-6, you view the instances of the type that you suspect is leaking memory. You can also see the name of the specific field by looking at the arrow that is referring. Right-click an instance to get a popup menu with the Inspect Instance option. When inspecting an instance you will see all instance variables that the object contains. This information will help you pinpoint where in your application the leaking object is located.
Figure 3-6 Referring Instances Tab
Table 3-2 explains what you will be able to view in the Instances tab.
Viewing Allocation Stack Traces
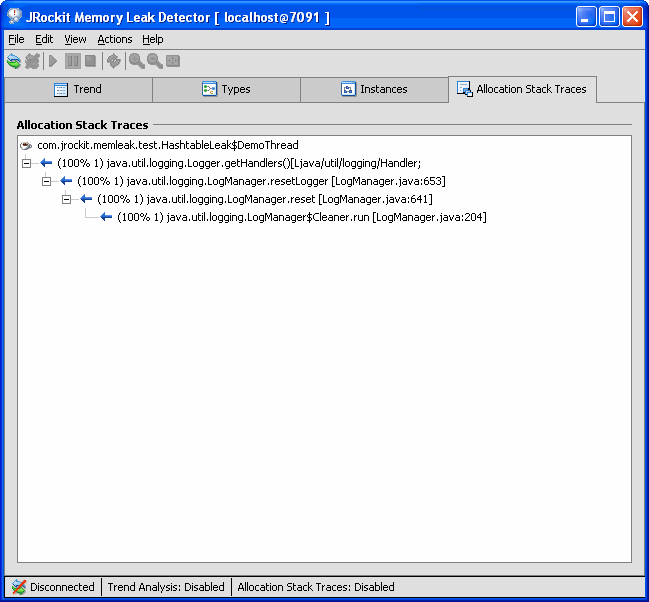
In the Allocation Stack Traces tab, see Figure 3-7, you can check for where in the code allocations of a certain type are done. Enabling allocation stack traces may deteriorate the performance of JRockit. Collecting information about all the allocation points might take a while.
Figure 3-7 Allocation Stack Traces Tab
Customizing Settings
The Memory Leak Detector can be customized in many different ways. Figure 3-8 through Figure 3-13 explains the different settings you can make.
To Open the Preferences Window
- Click File > Preferences.
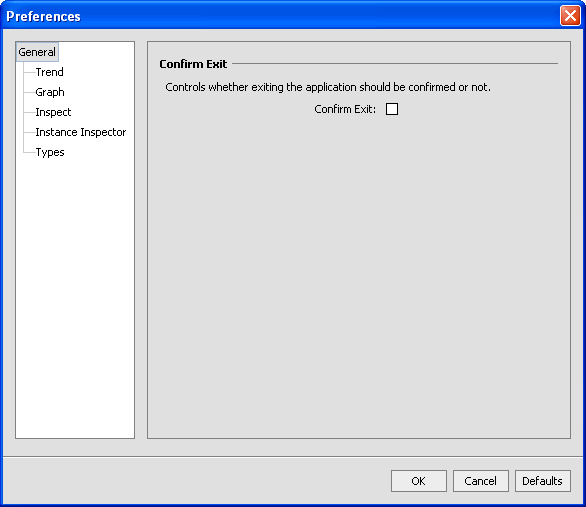
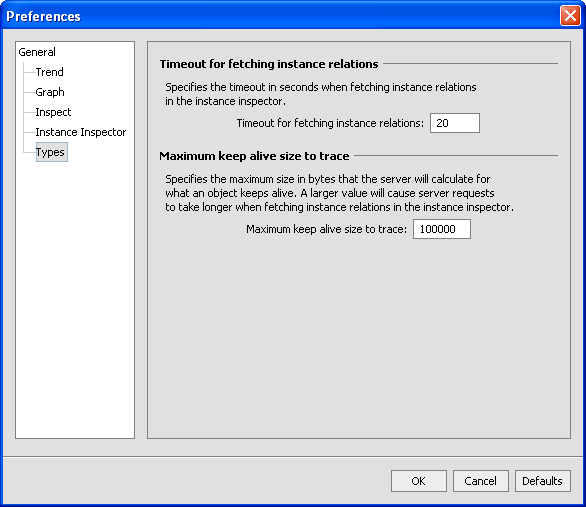
The Preferences window opens (see Figure 3-8).
When you have set your preferences, click OK for them to take effect.
To Reset Preferences to Default Values
Select the Confirm Exit option if you want to get a confirmation message when you are closing the Memory Leak Detector.
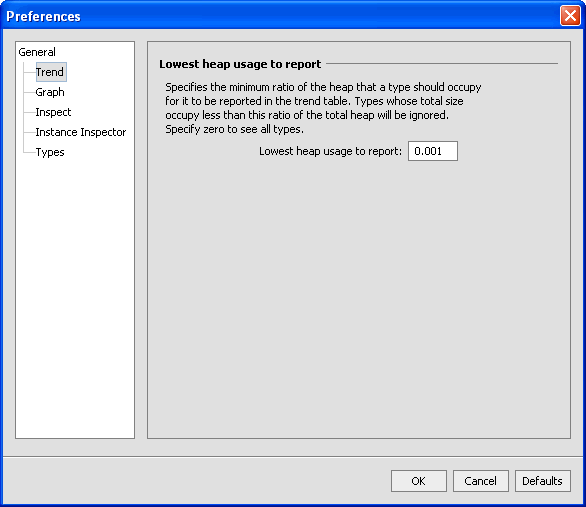
Figure 3-9 Display of Heap Usage
Here you set the ratio of the Java heap that you want displayed. Those types that are smaller than the set ratio are not displayed. If you want to display all types, set the ratio to 0 (zero).
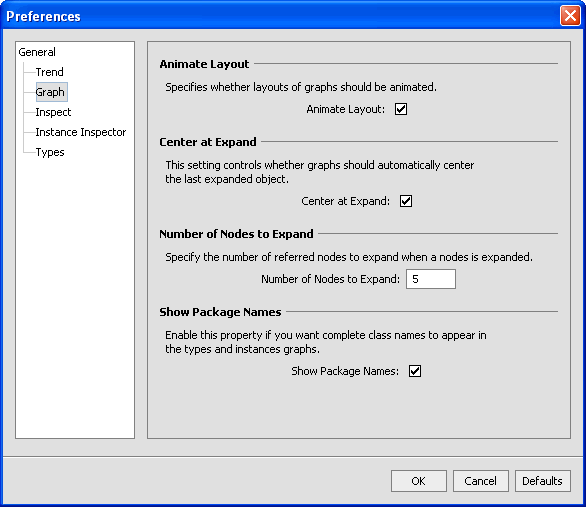
- Select Animate Layout if you want the types graph in the Types tab and the Instances tab to be animated when you expand a node on the type.
- Select Center at Expand if you want the graphs in the Types tab and Instances tab to be centered in the viewing area when you expand a node on the type or instance.
- Specify the value for Number of Nodes to Expand to control how many nodes you want to be displayed in the Types tab and Instances tab. If you specify a very high number, the view can become cluttered.
- Select Show Package Names if you want the complete class name displayed.
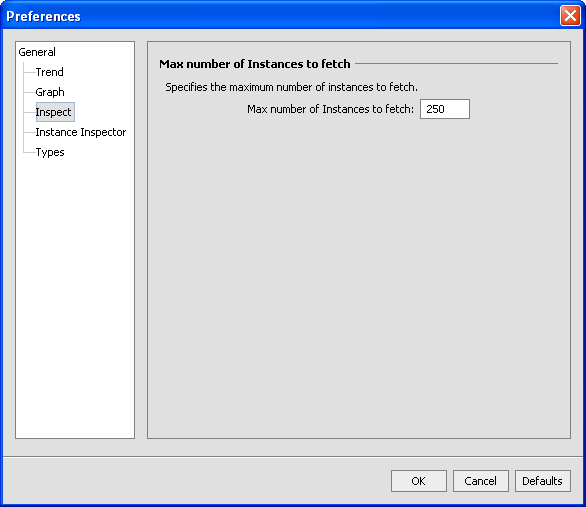
Figure 3-11 Number of Instances that are Fetched
Here you set the number of instances you want to list when doing List instances of a type. The list is shown in the Types tab under Instances.
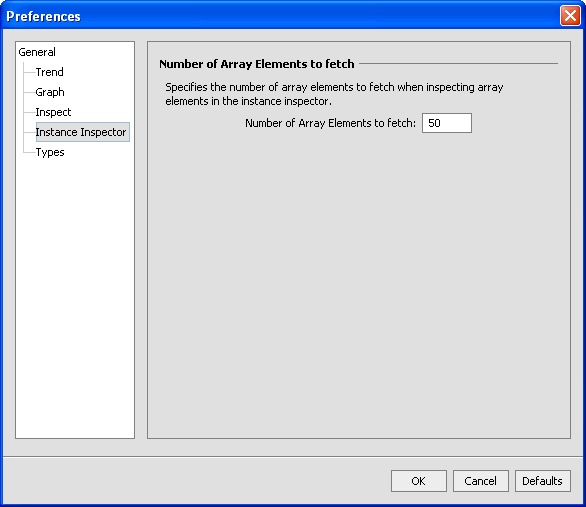
Figure 3-12 Number of Array Elements that are Fetched
Specify the value for the Max number of Array Elements to fetch. These elements are displayed in the Types tab when you have selected List Largest Arrays.
- Set a number for Timeout for fetching instance relations. This number is measured in seconds. The instance relation is showed in the Instances tab. The time out error can be caused by too many instances that need to be fetched.
- Set a value, in bytes, for the Maximum keep alive size to trace. When the Memory Leak Detector looks at an object until it reaches this value.